Facebook API allows you to access any sent links via Facebook Messenger
This week, security experts from Checkpoint found a vulnerability that allows you to modify messages and links sent via the Facebook messenger. Facebook quickly fixed this bug, but users managed to find a new vulnerability that allows access to all links ever sent through the social network messenger.
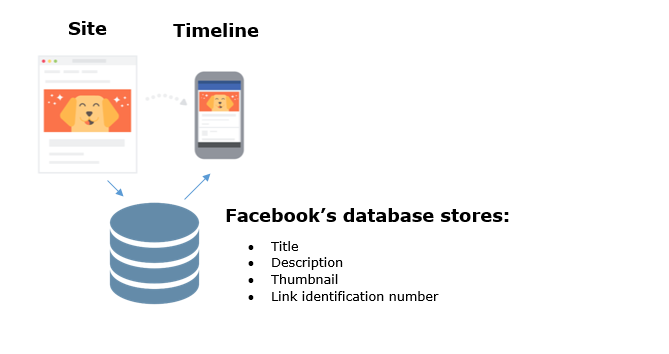
At the heart of the vulnerability is the principle of Facebook with links. When you first send a link, Facebook collects all the information from the page - from the title to the image on the preview, and then saves it in the database under unique identification numbers. This method does not allow links to be linked with the account from which they were sent, but with due patience and a large amount of data collected, it is theoretically possible to compare shared links with specific accounts.
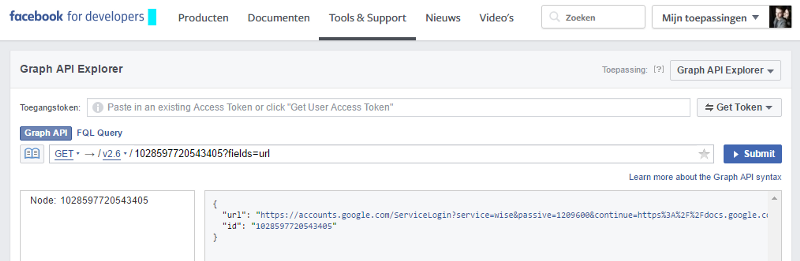
Medium blog user Inti de Seukeleire notes that all links receive unique numbers, but are not encrypted, it allows you to access absolutely any links that are stored in the Facebook database. To test his theory, he used a link to a file in Google Docs, which he sent to a friend.
')
After sending the link in the social network messenger, he received a unique number for this link in the Facebook debugger (a tool that allows you to find errors in the collected information from the page) and was able to get the link from the database through the Facebook API. It is noteworthy that Facebook stores links in its database only after clicking on them - without this, they are not registered in the database.
Using a simple script, Inti de Seukeleire made a parser with a unique identifier generator that allows you to find links stored in your Facebook database, sent in personal messages in Facebook Messenger. If Facebook used any cryptographically strong hashing to generate such identifiers, it would be almost impossible to select them. By itself, the ability to pick up an ID does little, but the fact that among objects you can identify links and retrieve them from the database, regardless of affiliation and privacy settings, is much more serious.
Most users will not suffer from such a vulnerability, but those who share confidential information via Facebook should once again think about changing the messenger.

After a brief analysis of vulnerabilities, Inti de Seukeleire was able to obtain the following information:
- Names;
- The location of the sent links;
- Attached files that need to be closed within Facebook privacy settings;
- Application data: the level of friends, their nicknames, and much more;
- Links to confidential documents and other content of this type.
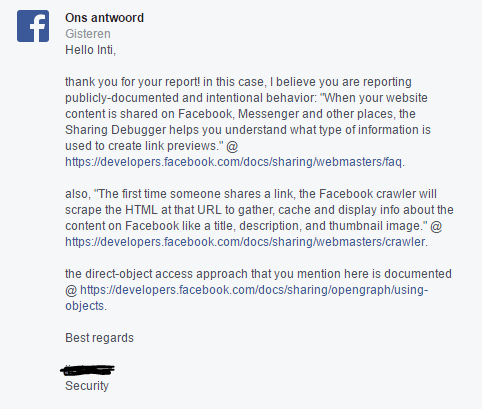
In response to a request to correct this vulnerability, Facebook representatives replied that all actions were carried out within the framework of the existing social network policy and do not contradict it.
In May, users filed a lawsuit against Facebook, in which they accused the social network of scanning personal messages. Scanning is necessary to ensure the security of themselves - for example, filtering links to malicious files, but some fear that Facebook used such tools for marketing purposes.
Source: https://habr.com/ru/post/394953/
All Articles