A robot from Lego managed to trick algorithms that recognize the user by gestures
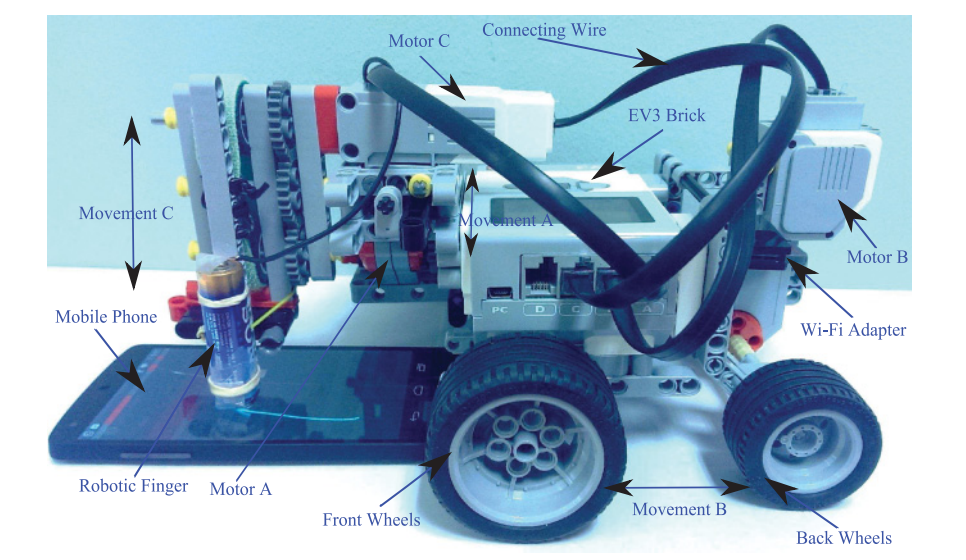
A team of computer security specialists with financial support from DARPA (United States Defense Advanced Research Projects Agency) in a new research paper draws attention to the unreliability of user identification methods based on their touch screen profile. The team built a robot based on Lego Mindstorms has managed to force various authentication systems on the smartphone to believe that the phone is being used by its owner.
Recently, the development of user authentication systems based on the analysis of gestures is gaining popularity. The idea is to collect the use of the touch screen by the user, and then on this basis to build a profile of the user's movements and constantly compare it with those movements that are used when working with a smartphone. It is believed that the set of movement data (the beginning and end of the swipe, the duration, etc.) is unique for each person.
The authors of the study note that such a system should be used only as an auxiliary one - they showed that the two existing ways to circumvent it are implemented using an uncomplicated robot. The first is the processing of statistics on the use of devices by different users in order to build some kind of universal average profile of using the touch screen. The second involves a hacker stealing information about the use of a smartphone by a specific user, in order to impersonate him.
')
In a paper entitled “robotic robbery on a touch screen,” researchers studied both of these methods. To automate the process, they built a robot from Lego Mindstorms, on the manipulator of which a finger model was made, made from an analogue of Play-Doh plasticine.
Data on gestures were collected from 41 people who participated in the experience, who, on the instructions of the testers, performed several actions natural for the Android system, accumulating a base of gestures (each of them reproduced 28 different movements).
The researchers then tested the described approaches on seven different user recognition algorithms through gestures. The first approach, using averaged gestures, managed to deceive the least reliable algorithm in 70 percent of cases - in these cases, the algorithm mistakenly determined that the device was used by the person who owns the smartphone.
When in the second phase of the experiment, scientists used data obtained from a specific user, the robot, which is not surprising, managed to deceive recognition algorithms in 90% of cases.
The authors of the study concluded that, since attacks of this kind are easy to carry out using freely available equipment, protection companies need not only to include tests with such robots in the security verification procedure, but also to work on improving the defense as a whole.
Source: https://habr.com/ru/post/394039/
All Articles