Jigsaw cryptographer plays with the user, like the character of the movie "Saw" (+ neutralization instructions)
The malware deletes files once an hour and when trying to restart the PC
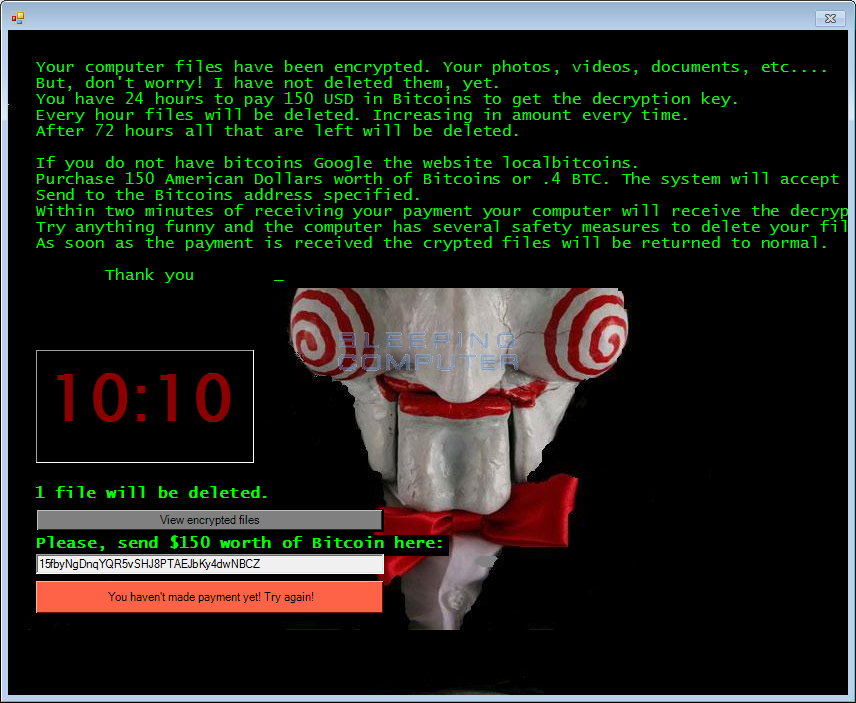
Malicious programs that threaten the safety of user data is becoming more and more. We did not have time to solve the problem with the Petya cryptographer, which encrypts the user's hard disk instead of individual files, as another ransomware appeared - the Jigsaw cryptographer. This software does not just encrypt user files and requires a ransom for their decryption. Every 60 minutes, one user file is deleted, and the data is also deleted by the extortioner when attempting to restart the PC. After some time, the hourly "execution" affects not one, but more files. When restarting, not one or two files are deleted, but just a thousand.
')
All this has a very strong effect on the user, and he, in most cases, prefers to pay. In this case, the screen gives instructions on how much to pay (Bitcoin equivalent of $ 150) and where you can get Bitcoins to pay for the “buy-out”. Already scary? In general, all this may also have an effect on a technically trained user ... But there is a way out - as was the case with Petya, there were users who learned how to neutralize ransomware. Now these users share their experiences with others.
What to do?
Thanks to the analysis carried out by Twitter users MalwareHunterTeam , DemonSlay335 , and BleepinComputer , a method has been found to neutralize the software. A decryptor has been released that can decrypt files affected by Jigsaw.
Initially, you need to terminate the firefox.exe and drpbx.exe processes in the task manager. This will avoid deleting files. Then we start MSConfig and stop the process firefox.exe, which is located in% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe. Next, we decrypt the files using this program .
It's pretty simple:
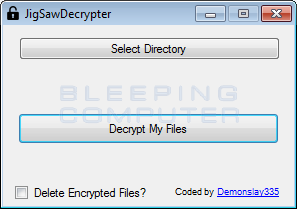
If you need to decrypt all the files on the disk, choose not the folder, but the root of the disk, and click on "Decrypt my files".
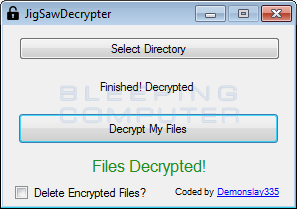
And then - then we run antivirus software with new databases, and check the PC.

Jigsaw Technical Details
After the malware gets to the user's computer, it starts searching for files with a certain extension, and encrypts them with AES encryption. Native extensions are replaced with .FUN, .KKK, or .BTC.
Their list is located in% UserProfile% \ AppData \ Roaming \ System32Work \ EncryptedFileList.txt. The bitcoin address is stored in the% UserProfile% \ AppData \ Roaming \ System32Work \ Address.txt file.
Files associated with this malware:
% UserProfile% \ AppData \ Roaming \ Frfx \
% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe
% UserProfile% \ AppData \ Local \ Drpbx \
% UserProfile% \ AppData \ Local \ Drpbx \ drpbx.exe
% UserProfile% \ AppData \ Roaming \ System32Work \
% UserProfile% \ AppData \ Roaming \ System32Work \ Address.txt
% UserProfile% \ AppData \ Roaming \ System32Work \ dr
% UserProfile% \ AppData \ Roaming \ System32Work \ EncryptedFileList.txt
Finally, registry entries:
HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \ firefox.exe% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe
As we see, the cryptographer is not the most dangerous, but the idea, of course, is strong. If future versions of the cryptographer will be better protected, it will be much more difficult to cope with Jigsaw.

Malicious programs that threaten the safety of user data is becoming more and more. We did not have time to solve the problem with the Petya cryptographer, which encrypts the user's hard disk instead of individual files, as another ransomware appeared - the Jigsaw cryptographer. This software does not just encrypt user files and requires a ransom for their decryption. Every 60 minutes, one user file is deleted, and the data is also deleted by the extortioner when attempting to restart the PC. After some time, the hourly "execution" affects not one, but more files. When restarting, not one or two files are deleted, but just a thousand.
')
All this has a very strong effect on the user, and he, in most cases, prefers to pay. In this case, the screen gives instructions on how much to pay (Bitcoin equivalent of $ 150) and where you can get Bitcoins to pay for the “buy-out”. Already scary? In general, all this may also have an effect on a technically trained user ... But there is a way out - as was the case with Petya, there were users who learned how to neutralize ransomware. Now these users share their experiences with others.
What to do?
Thanks to the analysis carried out by Twitter users MalwareHunterTeam , DemonSlay335 , and BleepinComputer , a method has been found to neutralize the software. A decryptor has been released that can decrypt files affected by Jigsaw.
Initially, you need to terminate the firefox.exe and drpbx.exe processes in the task manager. This will avoid deleting files. Then we start MSConfig and stop the process firefox.exe, which is located in% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe. Next, we decrypt the files using this program .
It's pretty simple:

If you need to decrypt all the files on the disk, choose not the folder, but the root of the disk, and click on "Decrypt my files".

And then - then we run antivirus software with new databases, and check the PC.

Jigsaw Technical Details
After the malware gets to the user's computer, it starts searching for files with a certain extension, and encrypts them with AES encryption. Native extensions are replaced with .FUN, .KKK, or .BTC.
These files are encrypted:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf , .c, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb,. prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps,. pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv , .efx, .sdf, .vcf, .xml, .ses, .Qbw, .QBB, .QBM, .QBI, .QBR, .Cnt, .Des, .v30, .Qbo, .Ini, .Lgb,. Qwc, .Qbp, .Aif, .Qba, .Tlg, .Qbx, .Qby, .1pa, .Qpd, .Txt, .Set, .Iif, .Nd, .Rtp, .Tlg, .Wav, .Qsm, .Qss, .Qst, .Fx0, .Fx1, .Mx0, .FPx, .Fxr, .Fim, .ptb, .Ai, .Pfb, .Cgn, .Vsd, .Cdr, .Cmx, .Cpt, .Csl, .Cur, .Des, .Dsf, .Ds4 ,, .Drw, .Dwg .Eps, .Ps, .Prn, .Gif, .Pcd, .Pct, .Pcx , .Plt, .Rif, .Svg, .Swf, .Tga, .Tiff, .Psp, .Ttf, .Wpd, .Wpg, .Wi, .Raw, .Wmf, .Txt, .Cal, .Cpx,. Shw, .Clk, .Cdx, .Cdt, .Fpx, .Fmv, .Img, .Gem, .Xcf, .Pic, .Mac, .Met, .PP4, .Pp5, .Ppf, .Xls, .Xlsx, .Xlsm, .Ppt, .Nap, .Pat, .Ps, .Prn, .Sct, .Vsd, .wk3, .wk4, .XPM, .zip, .rar
Their list is located in% UserProfile% \ AppData \ Roaming \ System32Work \ EncryptedFileList.txt. The bitcoin address is stored in the% UserProfile% \ AppData \ Roaming \ System32Work \ Address.txt file.
Files associated with this malware:
% UserProfile% \ AppData \ Roaming \ Frfx \
% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe
% UserProfile% \ AppData \ Local \ Drpbx \
% UserProfile% \ AppData \ Local \ Drpbx \ drpbx.exe
% UserProfile% \ AppData \ Roaming \ System32Work \
% UserProfile% \ AppData \ Roaming \ System32Work \ Address.txt
% UserProfile% \ AppData \ Roaming \ System32Work \ dr
% UserProfile% \ AppData \ Roaming \ System32Work \ EncryptedFileList.txt
Finally, registry entries:
HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \ firefox.exe% UserProfile% \ AppData \ Roaming \ Frfx \ firefox.exe
As we see, the cryptographer is not the most dangerous, but the idea, of course, is strong. If future versions of the cryptographer will be better protected, it will be much more difficult to cope with Jigsaw.
Source: https://habr.com/ru/post/392975/
All Articles