Intel Software Guard Technology Extensions in Pictures
Last year, we have already published an Intel blog post about Intel Software Guard Extensions (Intel SGX) technology, the support of which was implemented in the sixth generation Intel Core processors. Then it was mainly about ideological issues; I think it's time to tell how it works. In this post there will be a lot of illustrations from the detailed (over 200 slides) presentation from Intel on this technology. It, of course, says much more than here, so you now know where you can continue to study the issue.

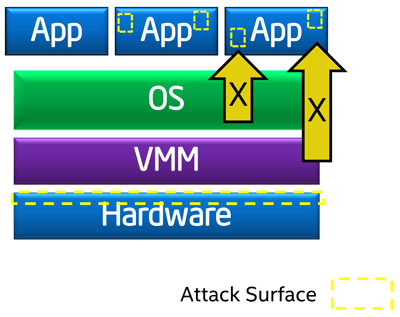
Protected mode rings share privileged kernel code and application code, and also separate applications from each other. However, applications are not protected from attacks by privileged code. A malicious application can penetrate it with the help of an exploit and then infiltrate a defenseless victim. At the same time, the site for attack is very wide: you can attack both the OS components, the application itself, and even the hardware subsystem.
')
The meaning of SGX is to narrow the perimeter of protection by placing all critical data in separate areas-enclaves that are inaccessible even from the kernel code. At the same time, however, the development process and the environment where the application is executed should not be radically changed.
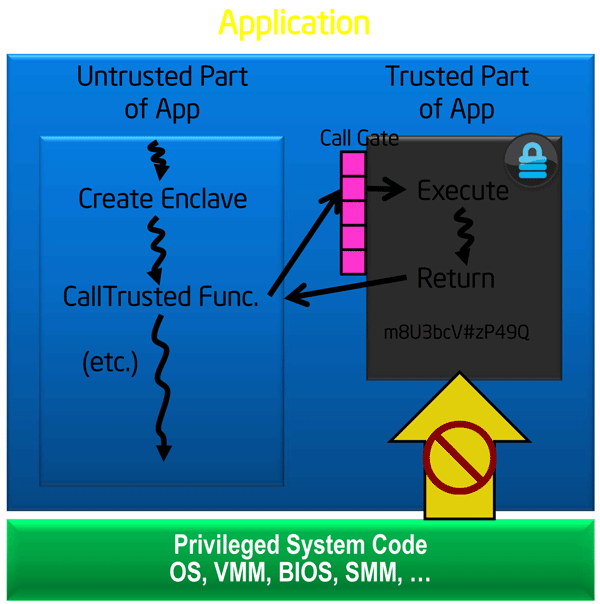
The application consists of two parts: trusted and common. When launched, it creates an enclave in a protected part of memory, consisting of 4 KB pages. When you call a trusted function, it sees the data of the enclave, any other external access (including from the OS) is prohibited. After the function ends, the enclave remains in a protected area.
The secure execution environment is built into the user process, it has its own code and data. It provides security, data integrity, control of input points, supports multithreading.
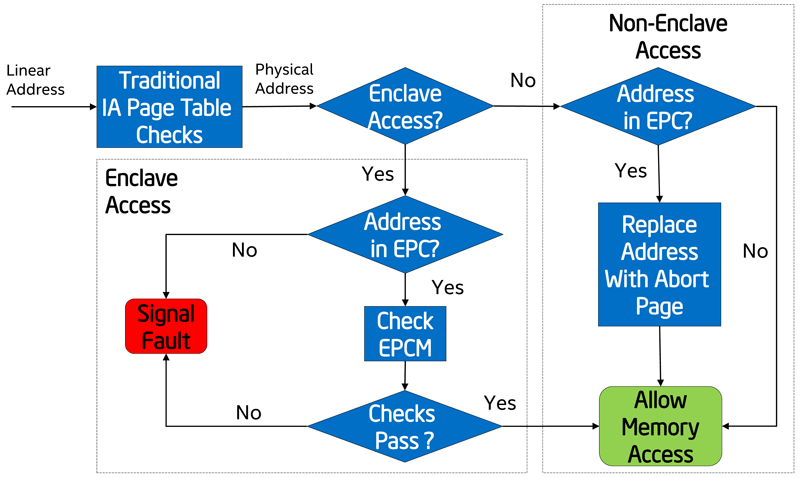
When attempting to access the enclave, it is checked whether the data of the calling process (EPC, Enclave Page Cache) is located at this address. The authorizations of the function (EPCM, Enclave Page Cache Metadata) are then monitored, and then the required access is granted.
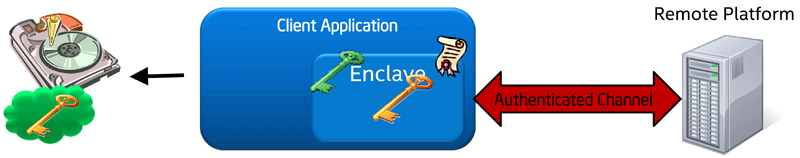
Certification is as follows. The enclave requests a hardware-signed report containing, including information about the integrity of the enclave. This report is sent to the evaluating server, where it is verified. The application key (public key part) is sent to the enclave, where a signing (private) key is generated, depending on the enclave and the platform. The application key is encrypted with the signing key and saved for future use.
The functionality of Intel Software Guard Extensions is implemented using a combination of SGX instructions that support local certification and the attestation enclosure provided by Intel to support remote certification.
SGX developers have provided protection against various kinds of attacks on data and code: threats from user and system software, as well as the loader. Note that using SGX means it is impossible to protect against side-channel vulnerabilities, when attackers collect CPU usage statistics to determine the characteristics of the code executed on it. To solve this kind of problems, tools for dynamic analysis of programs are used, such as, for example, Pin .
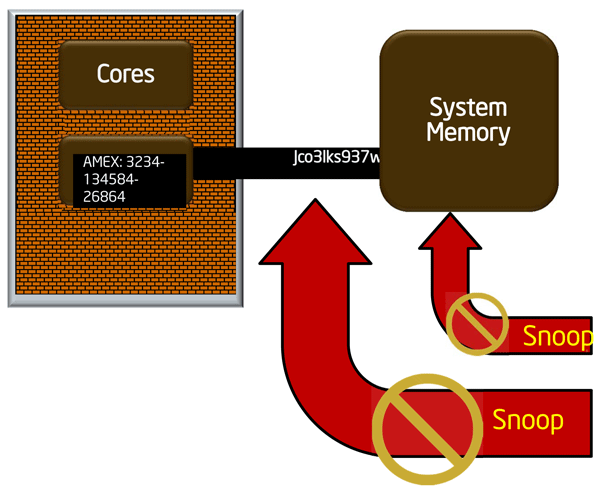
To prevent data interception during the exchange between the processor and memory, the Memory Encryption Engine (MEE) is used, which acts as an extension of the memory controller and supports SGX technology. For certain areas of memory encrypted data is transmitted over the bus. MEE uses special combinations of cryptographic primitives for efficient encryption with very strict delay requirements.
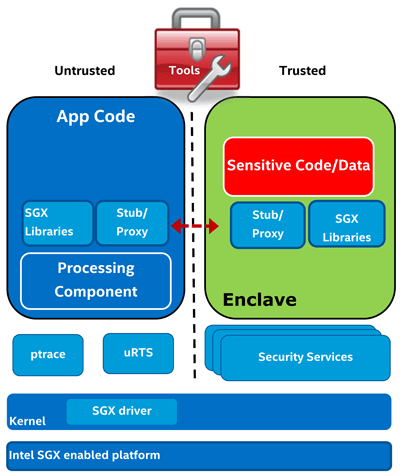
What is the development of applications that support SGX? Sensitive code and data fragments are placed in a separate shared object (.so). Next, the enclave interface is defined and stubs are generated. The SGX libraries interact with the code through the API, and the usual for the developer toolchains are used for development. To facilitate processing, the Intel SGX SDK is already available.
What does Intel SGX technology promise us? First of all, the requirements for the technical skills of a user working with confidential information can be greatly reduced. She no longer afraid of viruses, trojans and strange programs that may be on his computer. Further, confidence in cloud platforms will increase - they will be able to trust their applications, since they will be protected from any host code. Of course, the whole thing is quite a distant future, because the Skylake processors have just appeared. But you can use SGX now. We are ready to delve into this topic and answer any questions related to it.

Protected mode rings share privileged kernel code and application code, and also separate applications from each other. However, applications are not protected from attacks by privileged code. A malicious application can penetrate it with the help of an exploit and then infiltrate a defenseless victim. At the same time, the site for attack is very wide: you can attack both the OS components, the application itself, and even the hardware subsystem.

')
The meaning of SGX is to narrow the perimeter of protection by placing all critical data in separate areas-enclaves that are inaccessible even from the kernel code. At the same time, however, the development process and the environment where the application is executed should not be radically changed.

The application consists of two parts: trusted and common. When launched, it creates an enclave in a protected part of memory, consisting of 4 KB pages. When you call a trusted function, it sees the data of the enclave, any other external access (including from the OS) is prohibited. After the function ends, the enclave remains in a protected area.
The secure execution environment is built into the user process, it has its own code and data. It provides security, data integrity, control of input points, supports multithreading.

When attempting to access the enclave, it is checked whether the data of the calling process (EPC, Enclave Page Cache) is located at this address. The authorizations of the function (EPCM, Enclave Page Cache Metadata) are then monitored, and then the required access is granted.

Certification is as follows. The enclave requests a hardware-signed report containing, including information about the integrity of the enclave. This report is sent to the evaluating server, where it is verified. The application key (public key part) is sent to the enclave, where a signing (private) key is generated, depending on the enclave and the platform. The application key is encrypted with the signing key and saved for future use.
The functionality of Intel Software Guard Extensions is implemented using a combination of SGX instructions that support local certification and the attestation enclosure provided by Intel to support remote certification.
SGX developers have provided protection against various kinds of attacks on data and code: threats from user and system software, as well as the loader. Note that using SGX means it is impossible to protect against side-channel vulnerabilities, when attackers collect CPU usage statistics to determine the characteristics of the code executed on it. To solve this kind of problems, tools for dynamic analysis of programs are used, such as, for example, Pin .

To prevent data interception during the exchange between the processor and memory, the Memory Encryption Engine (MEE) is used, which acts as an extension of the memory controller and supports SGX technology. For certain areas of memory encrypted data is transmitted over the bus. MEE uses special combinations of cryptographic primitives for efficient encryption with very strict delay requirements.

What is the development of applications that support SGX? Sensitive code and data fragments are placed in a separate shared object (.so). Next, the enclave interface is defined and stubs are generated. The SGX libraries interact with the code through the API, and the usual for the developer toolchains are used for development. To facilitate processing, the Intel SGX SDK is already available.
What does Intel SGX technology promise us? First of all, the requirements for the technical skills of a user working with confidential information can be greatly reduced. She no longer afraid of viruses, trojans and strange programs that may be on his computer. Further, confidence in cloud platforms will increase - they will be able to trust their applications, since they will be protected from any host code. Of course, the whole thing is quite a distant future, because the Skylake processors have just appeared. But you can use SGX now. We are ready to delve into this topic and answer any questions related to it.
Source: https://habr.com/ru/post/392789/
All Articles