Petya cryptographer will not receive money: we generate the hard drive unlock key ourselves

On April 3, information on the detection of a new cryptographer appeared on Habrahabr, which encrypts not the individual files, but the entire disk partition (volume). The program is called Petya, and its purpose is the NTFS file allocation table. Ransomware runs low on the disk, with total loss of access to the volume files for the user.
Petya also found a special masking scheme to hide the activity. Initially, the cryptographer requests the user to activate UAC, masquerading as legitimate applications. As soon as extended privileges are obtained, malicious software begins to operate. As soon as the volume is encrypted, the cryptographer begins to demand money from the user, and a certain period is given for the payment of "redemption". If the user does not pay the funds during this time, the amount is doubled. "Field of Miracles", and only.
')
But the cryptographer turned out to be not very well protected by himself. Twitter user nickname leostone has developed a key generator for Petya, which allows you to unlock disk encryption. The key is individual, and the selection takes about 7 seconds.
The same user has created a website that generates keys for users whose PCs have suffered because of Petya. To obtain the key, you must provide information from the infected disk.
What do we have to do?
Infected media needs to be inserted into another PC and to extract certain data from certain sectors of the infected hard disk. This data must then be run through the Base64 decoder and sent to the site for processing.
Of course, this is not the easiest way, and for many users it may not be feasible at all. But there is a way out. Another user, Fabian Wosar , created a special tool that does everything on its own. For it to work, you need to rearrange the infected disk to another PC with Windows OS. Once this is done, download Petya Sector Extractor and save it to your desktop. Then we execute PetyaExtractor.exe. This software scans all drives for Petya search. As soon as an infected disk is detected, the program starts the second stage of work.
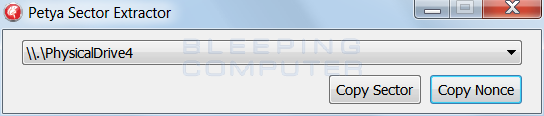
The extracted information must be uploaded to the site indicated above. There will be two text fields, titled as Base64 encoded 512 bytes verification data and Base64 encoded 8 bytes nonce. In order to get the key, you need to enter the data extracted by the program in these two fields.
To do this, press the Copy Sector button in the program, and paste the copied data into the field of the Base64 encoded 512 site bytes verification data.
Then in the program, select the Copy Nonce button, and paste the copied data into the Base64 encoded 8 bytes nonce on the site.
If everything is done correctly, this window should appear:
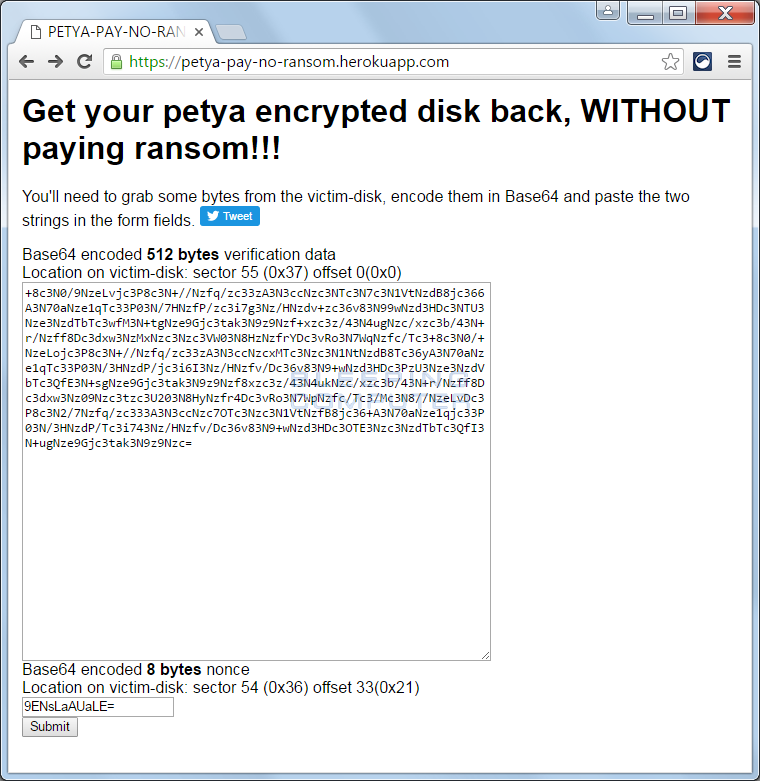
To get the decryption password, click the Submit button. A password will be generated for about a minute.

Write the password, and connect the infected disk back. As soon as the virus window appears, enter your password.
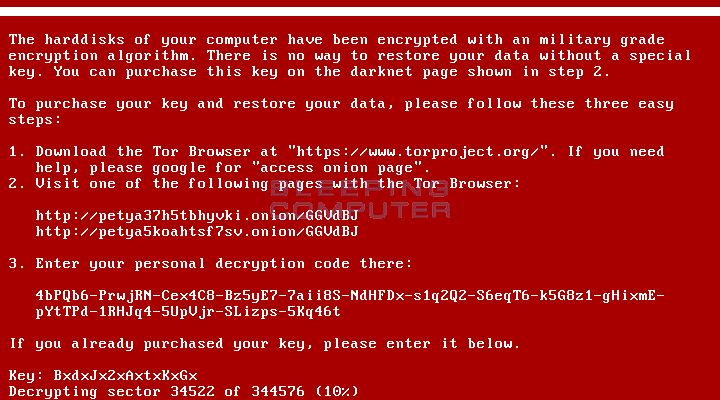
Petya begins decrypting the volume, and everything starts working when the process is complete.
Source: https://habr.com/ru/post/392727/
All Articles