The extortioner malware “Petya” encrypts the entire hard disk and requires money
Welcome to the pages of the blog iCover ! Perhaps the online exposition of the The Malware Museum virus museum, which contains unusual and memorable malware users, will soon be replenished with another interesting exhibit. The creators of the Petya Trojan (Petya) operate according to the classical scheme: they encrypt user data and require a ransom for the key to unlock. But, it has “Win32.Trojan-Ransom.Petya.A Trojan” and something that fundamentally distinguishes it from the average extortionists-cryptographers - Locky, CryptoWall, TeslaCrypt ..., its authors did not limit themselves to coding individual categories of files - documents, photo or video archives, the malware encrypts the data disk completely.
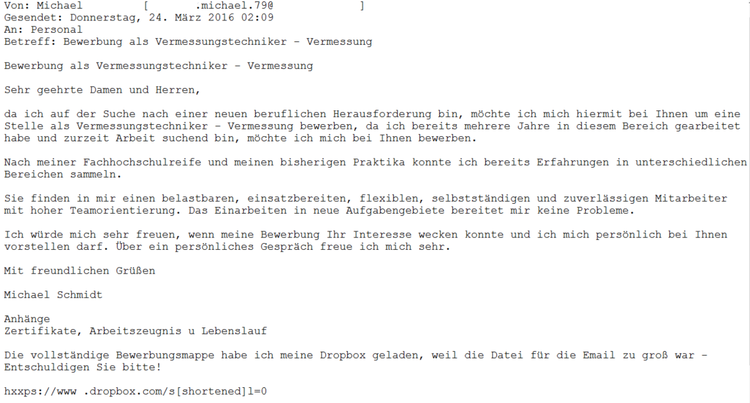
The first step towards establishing a close contact “attacker-user” is to receive the last letter, which does not look any different from the hundreds sent daily. Here we have to pay tribute to a fairly good knowledge of the psychology of its compilers. A letter was sent allegedly by mistake by the job seeker referring to the personnel department of the company-employer. The archive is attached to the letter - a portfolio of works stored in the cloud service Dropbox.
')
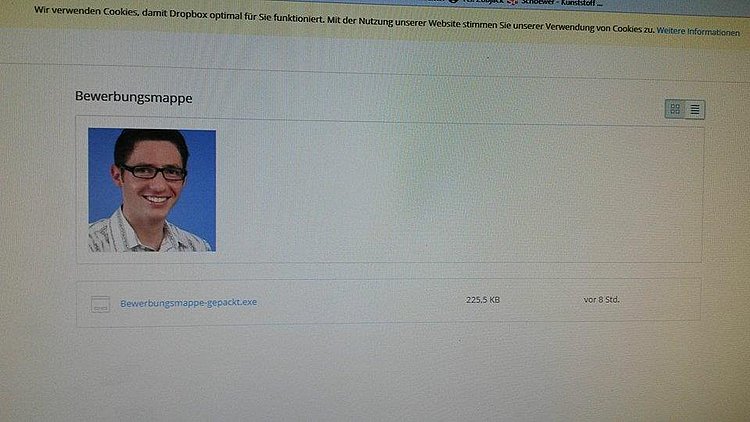
Although outwardly, everything looks quite harmless, as it probably already became clear to our readers, the archive contains an executable file containing malicious software. Upon clicking on the link, the boot record on the system drive is modified, the computer shuts down in emergency mode.
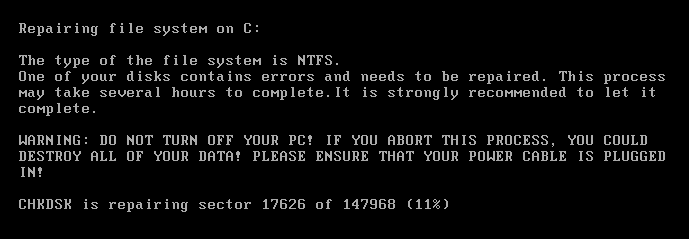
After restarting the computer, the user sees a system message notifying that the disk is damaged and needs to be corrected. The check may take several hours, and in order to prevent complete loss of information, the computer should not be turned off during the entire testing phase. In fact, during all this time, the user's drive data is encrypted.
When Petya finishes his dirty deed and the access to the disk data is encrypted, the user who rebooted the system will be asked to purchase the key through the Tor browser.
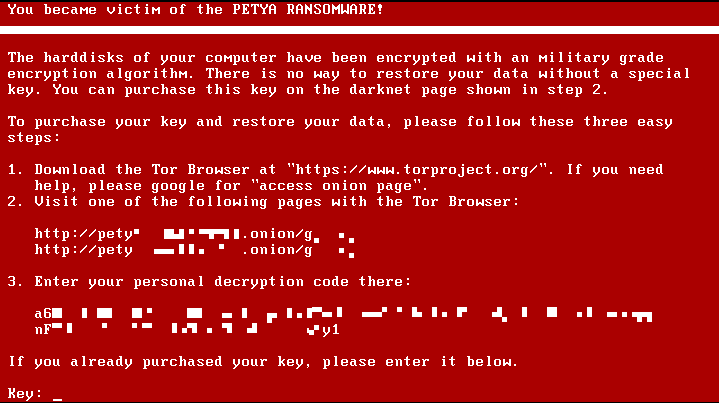
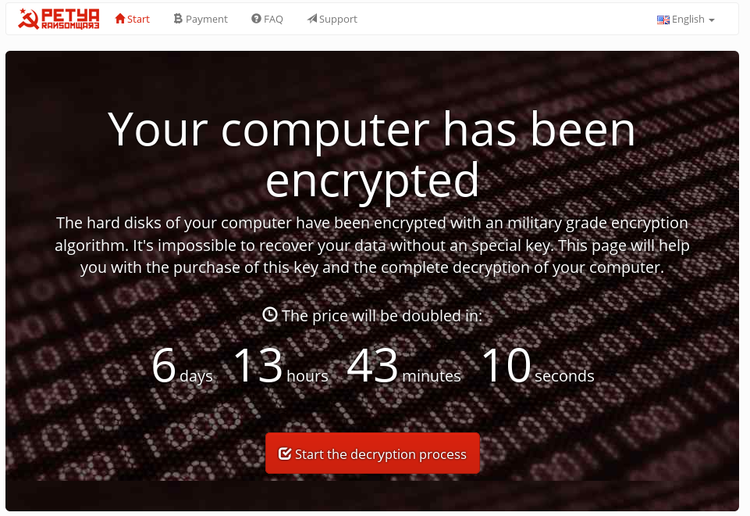
At this stage, extortionists resort to another attempt at psychological pressure: to encourage the victim to pay, Petya displays a message with a timer, according to which in 7 days the cost of the key will double.

Virus analysis is now carried out in the laboratory by security experts G DATA SecurityLabs . They hope that Petya still encrypts only file access, but not the drive data itself. The answer to the question: is it possible to recover disk data in case of infection at the moment no.
In order for Petya not to become a part of our nightmare, SecurityLabs experts, in the absence of a clear understanding of the malware code at the moment, recommend sticking to two standard tips:
• Regularly create archival copies of important data.
• Show increased attention when downloading executable files.
If the system is already infected, it is necessary to disconnect the computer from the network despite the strong recommendations on the screen. Laboratory specialists do not recommend paying for services to the creators of the malware.
Information about whether to restore access to the data and the data itself is not yet available. In this regard, experts of the laboratory note, it should be understood that the moment before downloading and opening the malicious file is a point of no return, that last chance, when the threat and the problems accompanying it can still be prevented.
A source
G DATA SecurityLabs laboratory promises to publish updated information on the results of virus testing on the blog page in real time.
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review materials and other publications, and we will try to do everything possible so that the time spent with us will be useful for you. And, of course, do not forget to subscribe to our headings .
Our other articles and events

The first step towards establishing a close contact “attacker-user” is to receive the last letter, which does not look any different from the hundreds sent daily. Here we have to pay tribute to a fairly good knowledge of the psychology of its compilers. A letter was sent allegedly by mistake by the job seeker referring to the personnel department of the company-employer. The archive is attached to the letter - a portfolio of works stored in the cloud service Dropbox.

')
Although outwardly, everything looks quite harmless, as it probably already became clear to our readers, the archive contains an executable file containing malicious software. Upon clicking on the link, the boot record on the system drive is modified, the computer shuts down in emergency mode.

After restarting the computer, the user sees a system message notifying that the disk is damaged and needs to be corrected. The check may take several hours, and in order to prevent complete loss of information, the computer should not be turned off during the entire testing phase. In fact, during all this time, the user's drive data is encrypted.

When Petya finishes his dirty deed and the access to the disk data is encrypted, the user who rebooted the system will be asked to purchase the key through the Tor browser.

At this stage, extortionists resort to another attempt at psychological pressure: to encourage the victim to pay, Petya displays a message with a timer, according to which in 7 days the cost of the key will double.

Virus analysis is now carried out in the laboratory by security experts G DATA SecurityLabs . They hope that Petya still encrypts only file access, but not the drive data itself. The answer to the question: is it possible to recover disk data in case of infection at the moment no.
How to protect against malware
In order for Petya not to become a part of our nightmare, SecurityLabs experts, in the absence of a clear understanding of the malware code at the moment, recommend sticking to two standard tips:
• Regularly create archival copies of important data.
• Show increased attention when downloading executable files.
If the system is already infected, it is necessary to disconnect the computer from the network despite the strong recommendations on the screen. Laboratory specialists do not recommend paying for services to the creators of the malware.
Information about whether to restore access to the data and the data itself is not yet available. In this regard, experts of the laboratory note, it should be understood that the moment before downloading and opening the malicious file is a point of no return, that last chance, when the threat and the problems accompanying it can still be prevented.
A source
G DATA SecurityLabs laboratory promises to publish updated information on the results of virus testing on the blog page in real time.
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review materials and other publications, and we will try to do everything possible so that the time spent with us will be useful for you. And, of course, do not forget to subscribe to our headings .
Our other articles and events
- Gator Caref Watch. Caring for your child
- Spring discounts from KitchenAid
- Sale of useful gadgets and interesting pieces
- Jawbone UP3 vs. Xiaomi Mi Band 1S Pulse - the battle for our hearts!
- A selection of smart watches today. What changed?
- Top 10 most popular gadgets in iCover
- How the case did not save my iPhone. Choose right
Source: https://habr.com/ru/post/392395/
All Articles