Apple wants to know how the FBI hacked the phone
Recently it became known that the FBI has withdrawn its demand for Apple to decipher data from the phone seized from the shooter from San Bernardino, due to the fact that the agency with the help of unnamed third parties has coped with this task on its own. However, now Apple has questions to the Bureau - the company's specialists need to know about the found vulnerability.
It is clear that the FBI, which demanded civic awareness from Apple and help in deciphering data from a terrorist’s phone, now, in theory, should demonstrate it by example, and share information about hacking methods. Then Apple will be able to successfully continue enhancing the security of its users, improving encryption.
But it’s just as clear that the FBI is not going to divulge the secrets they received - because once the technology has worked it can be used many more times to uncover other, possibly not so loud, cases. And if the FBI had to put pressure on Apple through court, then Apple generally has virtually no leverage over the federal bureau of investigation.
')
Governments and their agencies often acquire information from third parties about vulnerabilities in products of various companies, and they do not consider it their duty to inform these companies themselves - which ultimately harms, naturally, ordinary citizens. For example, recently it became known that the FBI used the services of third-party specialists who managed to break the Tor network and calculate the real ip-addresses of its participants as part of the operation against the darknet network .
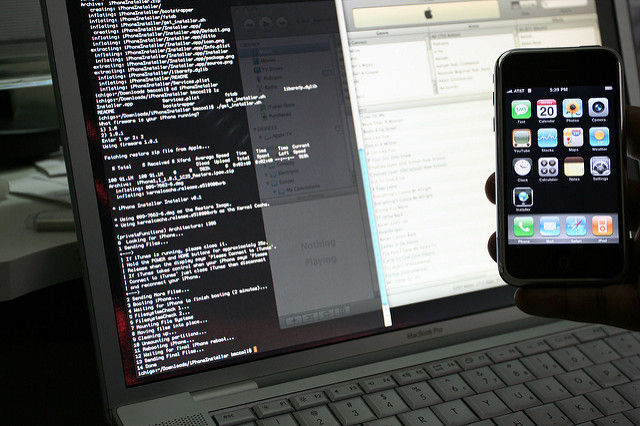
Of course, if you used hardware technologies like NAND mirroring chips for this , there is little that can be done. This technology involves the creation of multiple copies of the chip in order to circumvent the limit on the number of attempts to enter the code and the delay between attempts.
Demonstration of the concept of NAND-copying using jailbroken phone
However, it is possible that another hacker was able to detect the zero-day vulnerability, due to which pin-code selection can be made possible. Such cases have already happened - for the 8th version of iOS, they used both a special IP-BOX device , breaking the contacts of the battery, and software solutions . These problems are already taken into account by Apple companies in new versions of the OS, but no one guarantees the appearance of new vulnerabilities in them.
Now Apple, trying to demonstrate its concern for users, is trying to find out about the methods used to open the phone. Apple's well-paid lawyers are looking for legal pressure on the FBI to uncover the exact technology for hacking the phone.
Some experts believe that the best tactics for the company will be declaring the need to disclose vulnerabilities in encryption necessary for national security - because if this information remains undisclosed and measures are not taken for vulnerability, this potentially endangers the security of many phone users.
Source: https://habr.com/ru/post/392367/
All Articles