What is actually happening with MAC address randomization in iOS 8
Usually, when you roam with a WiFi device that is not connected to a network, it broadcasts requests to try to find known networks. These requests are sent using the MAC address of your phone's WiFi adapter, which is unique and usually permanent. This means that anyone who monitors these requests, for example, in a department store, for example, can constantly monitor you in the store and after several visits. This information is not tied to your personal data, but analyst companies can learn a lot of information about your buying habits from it, and some users are not thrilled with it.
How it should work
Starting with iOS 8, Apple devices must randomly change their MAC address by sending out these WiFi requests. The OS is responsible for creating random, locally managed MAC addresses. It is hoped that as long as you are not connected to wireless access points, your device can no longer be used to track you. Since these are WiFi requests, their distance is limited. Those who want to track the presence and movement of your device should be relatively close. One of the places where we have seen this is in department stores to monitor customer buying habits. With the new MAC address periodically generated for your device, there will no longer be a permanent marker for passive surveillance.
')
How does this seem to work?
Unfortunately, it seems that Apple's changes in the behavior of these requests are not exactly what we hoped for. A couple of weeks ago, a representative of GISi Indoors, a company engaged in indoor navigation and location analytics, turned to us, saying that they were testing changes in functionality in iOS 8 beta and saw how it works. We launched Wireshark to take a look.
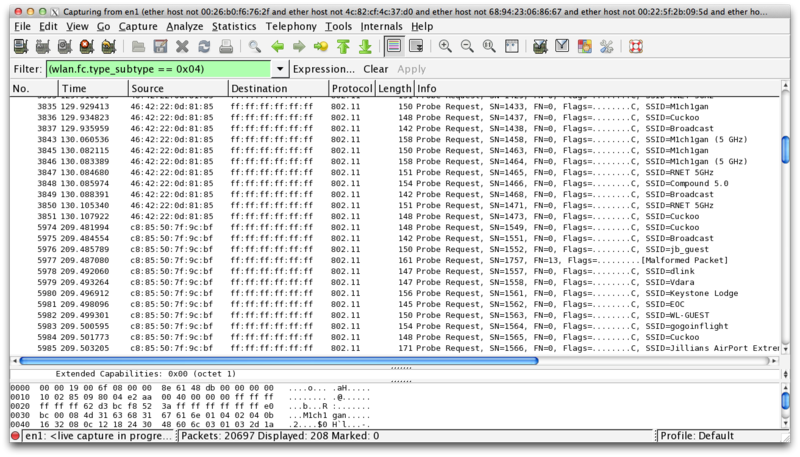
Of course, we saw that our device happily sends out WiFi requests using its real MAC address, and we were not alone in that. Security researcher Hubert Seiwert, the creator of the iSniff utility, saw the same behavior. At first, MAC randomization did not seem to work at all, and it was strange, because Apple focused on this possibility when publishing.
After long digging and many sleepless nights of monitoring traffic at Wireshark, it became clear that Apple seems to have done this function, as stated, but not quite as expected. At the WWDC conference in the session on user privacy, the slide said: "The MAC address used for WiFi scanning will not always be the real (universal) address." They did not say that he would never be a real MAC, only that he could not always be him.
Last week, analyst firm AirTight published extremely detailed reports on testing MAC randomization in iOS 8 and obtaining similar results. If you have not read them, I strongly recommend to look. Their testing seems to be very extensive, although their results do not fully coincide with ours.
In our testing, we found that in order for the randomization functionality to work, the devices supported by iOS 8 must meet two criteria. First, the device should not be connected to WiFi, which makes sense. Secondly, the device must be in sleep mode. AirTight concluded that location services (Location Services) and cellular service also need to be disabled, but if you look closely, I don’t think so.
On iPhone 6 running iOS 8.0.2, I had the opportunity to watch WiFi requests sent with a randomized MAC address with location services and cellular service enabled. The problem is that if you have a cellular connection, your phone usually doesn’t go to sleep for a long time. Even if the screen has fallen asleep, the phone can remain active, for example, receiving a new push notification email. Even if you turn off alerts, the phone wakes up when this email arrives, despite the fact that the screen remains off.
Unfortunately, the requirement for the phone to be in sleep mode makes this feature almost useless, although it coincides with the description of Apple at WWDC. In order to use random MAC addresses, I had to turn off alerts for several applications, disable push for email and stay awake for the night to have a greater chance for the phone to fall asleep without interrupting for more than a minute or two. Even under these circumstances, I was able to see only one or two rounds of requests (which seem to be sent every couple of minutes) with random MAC addresses before the phone issues a packet of requests with a real MAC. I think this could be due to some kind of push-notification process that awakened the phone. With the cellular connection turned on, I only saw about 50% of requests coming from randomly assigned MAC addresses.
This feature seems even more useless because, although requests come with a random MAC, they contain 5 SSIDs of networks to which the phone was previously connected. This means that even when the MAC is random, the sent SSIDs can serve as a fingerprint of my phone. The MAC address may be random every time, but if each request sends the same set of 5 network names every few minutes, it is still possible to track my device.
Should we worry?
Ultimately, this feature is not what Apple should have done; this is what they decided to do to help user privacy. In theory, it was a great idea, but the performance seems to have nothing really useful. Users are no worse off than iOS 7, and this information is still not tied directly to a person, but it gives companies (and individuals) the ability to track anonymous people without their consent. This is primarily useful for stores, marketers and analytical companies to analyze consumer trends and habits, but ideally this is something that users should have some control over. This data is almost equal to the information about us, and we must have the final say in who can use this data. Hopefully Apple can make adjustments to the MAC randomization process.
translation: www.imore.com/closer-look-ios-8s-mac-randomization
How it should work
Starting with iOS 8, Apple devices must randomly change their MAC address by sending out these WiFi requests. The OS is responsible for creating random, locally managed MAC addresses. It is hoped that as long as you are not connected to wireless access points, your device can no longer be used to track you. Since these are WiFi requests, their distance is limited. Those who want to track the presence and movement of your device should be relatively close. One of the places where we have seen this is in department stores to monitor customer buying habits. With the new MAC address periodically generated for your device, there will no longer be a permanent marker for passive surveillance.
')
How does this seem to work?
Unfortunately, it seems that Apple's changes in the behavior of these requests are not exactly what we hoped for. A couple of weeks ago, a representative of GISi Indoors, a company engaged in indoor navigation and location analytics, turned to us, saying that they were testing changes in functionality in iOS 8 beta and saw how it works. We launched Wireshark to take a look.

Of course, we saw that our device happily sends out WiFi requests using its real MAC address, and we were not alone in that. Security researcher Hubert Seiwert, the creator of the iSniff utility, saw the same behavior. At first, MAC randomization did not seem to work at all, and it was strange, because Apple focused on this possibility when publishing.
After long digging and many sleepless nights of monitoring traffic at Wireshark, it became clear that Apple seems to have done this function, as stated, but not quite as expected. At the WWDC conference in the session on user privacy, the slide said: "The MAC address used for WiFi scanning will not always be the real (universal) address." They did not say that he would never be a real MAC, only that he could not always be him.
Last week, analyst firm AirTight published extremely detailed reports on testing MAC randomization in iOS 8 and obtaining similar results. If you have not read them, I strongly recommend to look. Their testing seems to be very extensive, although their results do not fully coincide with ours.
In our testing, we found that in order for the randomization functionality to work, the devices supported by iOS 8 must meet two criteria. First, the device should not be connected to WiFi, which makes sense. Secondly, the device must be in sleep mode. AirTight concluded that location services (Location Services) and cellular service also need to be disabled, but if you look closely, I don’t think so.
On iPhone 6 running iOS 8.0.2, I had the opportunity to watch WiFi requests sent with a randomized MAC address with location services and cellular service enabled. The problem is that if you have a cellular connection, your phone usually doesn’t go to sleep for a long time. Even if the screen has fallen asleep, the phone can remain active, for example, receiving a new push notification email. Even if you turn off alerts, the phone wakes up when this email arrives, despite the fact that the screen remains off.
Unfortunately, the requirement for the phone to be in sleep mode makes this feature almost useless, although it coincides with the description of Apple at WWDC. In order to use random MAC addresses, I had to turn off alerts for several applications, disable push for email and stay awake for the night to have a greater chance for the phone to fall asleep without interrupting for more than a minute or two. Even under these circumstances, I was able to see only one or two rounds of requests (which seem to be sent every couple of minutes) with random MAC addresses before the phone issues a packet of requests with a real MAC. I think this could be due to some kind of push-notification process that awakened the phone. With the cellular connection turned on, I only saw about 50% of requests coming from randomly assigned MAC addresses.
This feature seems even more useless because, although requests come with a random MAC, they contain 5 SSIDs of networks to which the phone was previously connected. This means that even when the MAC is random, the sent SSIDs can serve as a fingerprint of my phone. The MAC address may be random every time, but if each request sends the same set of 5 network names every few minutes, it is still possible to track my device.
Should we worry?
Ultimately, this feature is not what Apple should have done; this is what they decided to do to help user privacy. In theory, it was a great idea, but the performance seems to have nothing really useful. Users are no worse off than iOS 7, and this information is still not tied directly to a person, but it gives companies (and individuals) the ability to track anonymous people without their consent. This is primarily useful for stores, marketers and analytical companies to analyze consumer trends and habits, but ideally this is something that users should have some control over. This data is almost equal to the information about us, and we must have the final say in who can use this data. Hopefully Apple can make adjustments to the MAC randomization process.
translation: www.imore.com/closer-look-ios-8s-mac-randomization
Source: https://habr.com/ru/post/375057/
All Articles