Risk management on IT projects: what has changed in recent years
The dilemma of risk management is very simple: either you reassure yourself and put all the threats in the budget of a project that will rise to the skies, or you will miss some of the risks and then get a chance to screw up nicely.
In the first case, there will be no profit from the company and your premium, and in the second, something more terrible will happen. But the second case is the Russian roulette, it may be lucky. In practice, risk management is always a delicate balance between “reasonable” and “sufficient”.
Therefore, let's talk a little more about some of the risks of projects that have increased in recent years. Some of them are not new. Some in the realities of the current IT market have acquired new shapes, colors and monstrous features.
There was a need to launch larger-scale integration and product projects in order to gain a tangible competitive advantage in the market. Since the basic “bricks” of the projects have already been written, we are talking about large implementations, where the first place is not the code itself, but performance indicators.
')
Previously, CIO was engaged in automating the company's business processes and ensuring the stable operation of its zoo systems. Now the stage of automation of classic business functions comes to an end: ERP, CRM, BI and other business management tools have already been digitized. Just having automation is no longer a competitive advantage. More important is Time-to-value, Time-to-market, ROE, continuity and cybersecurity. The speed of product launch to the market, ensuring uninterrupted access to services and their security - the main focus is now there.
IT becomes not a service unit, but the core of a business. Any large-scale IT project now involves many processes, and, accordingly, requires the participation of an increasing number of services and top managers. That is why the role of the CIO and its division has grown over the past years. IT literacy requirements for technical unit employees also grew.
Now it is impossible to successfully implement the project without understanding the industry specifics and nuances in the customer's business processes, that is, the work of integrators has become more complicated. The service work model comes to the fore. A large sale is increasingly taking shape almost as a cooperation agreement, but without revenue sharing, although there are such examples in my practice. Projects more and more often begin to develop the “beginning and end” model and turn into a continuous process of development of previously implemented projects. The integrator begins to be perceived as a partner, ready to share responsibility not only for the successful implementation of the project, but also for the business result for which it was launched.
As an example, I can give projects on photo and video recording of violations of traffic rules when the project is implemented at the expense of the executor, and the executor gets the profit from the proceeds generated by the fixing system itself in the form of fines! That is, the system was built poorly or missed with the calculation of the return on investment - get a loss in the project.
Now the phase of automation of the channels of interaction of companies with the surrounding business environment has begun: customers, partners, regulators, and so on. In fact, business is opening itself up in the cyberspace of a new digital market - creating a digital ecosystem around itself. This task is new to the market and carries with it a standard set of risks - financial, investment, operational.
This is mainly due to the lack of accumulated experience and developed standards, guaranteed mechanisms to protect processes and data in cyberspace.
From the point of view of the CIO, the integration of IT and the company's main business continues, respectively, and the growing influence of the IT service on the company's risk management system.
What does this mean in terms of changing the work of the CIO and its subordinates? From the point of view of team leaders?
Now KPI CIO can not be limited to indicators of continuity and cost of ownership of IT. As a key element of any modern company, business indicators are coming to the forefront of IT departments! CIO and its team need to dive even more into the details of the organization’s business, go beyond IT competencies, and even lose them, since most of the IT resources begin to be delivered through the service model. The increased responsibility for the result of the implementation of strategic initiatives makes us pay special attention to risk management in projects. Some of them become an insurmountable barrier for the project team on the path to successful implementation.
In a short time, you need to have time to make a “minimally viable product” for its entry into production, otherwise competitors will do the same. All other improvements later, in the process of testing custom hypotheses. It is important to "stake out the clearing" first. This circumstance forces customers and project teams to change their usual classical implementation models, creating new problems and risks.
The real challenge for the project team is to manage the requirements and expectations of the customer. What is the main difficulty here? Projects are increasingly starting with a minimum set of requirements that are continuously refined and supplemented throughout the project. It often happens that by the end of the project the set of requirements is absolutely “perpendicular” to what was at the start. I have often observed how the customer only by the middle of the project, and sometimes by its end, finally (!) Realized, and what he really wants.
An iterative approach usually helps here - dividing into small sprints and deep customer involvement in the implementation process. And the more such uncertainty, the closer should be the interaction. To create the necessary conditions for effective collaboration, we often land key people from Technoserv on the customer’s site. This greatly improves communication, reduces reaction time, creates the necessary conditions for the integration of project teams, and, accordingly, reduces the amount of work "in the basket."
About expectations - a separate story. On the one hand, it is difficult to manage the expectations of the customer, who himself does not clearly understand what he wants to get at the end of the project. On the other hand, as I wrote earlier, projects are increasingly affecting almost all the functional units of the customer. And each of them is a source of requirements and a participant in the coordination of the final result. KPI of these units is different, and therefore, the conflict of interest can not be avoided! If you can not find a compromise and make friends of the conflicting parties, outright sabotage by the individual participants is provided to you.
In one of our large projects, the problem of sabotage, as agreed with the IT curator, had to be included in the register of key risks and submitted to the management committee of the customer. There was another project when we were building a credit line for one large bank of the top 10. In the working group from the customer were IT, risk takers, security guards, product specialists, lawyers, etc. Each of them solved their tasks, fought for their KPIs, and in order to solve many key issues, they had to involve the top managers of the bank. Fortunately, the project was initiated by the first person of the bank and he was very interested in it. Largely due to this, the system was able to be implemented in the shortest possible time. Probably, we would have done the project, only it would take much more time.
The trust of the top managers to the project manager is usually based on two things: the professionalism of the PM and the quick victories of the team. If trust has not appeared in a short time, then it can be extremely difficult to restore it. For PMA and the team, it is important to understand not only the specifics of the customer’s industry, its problems, but also to know the KPI of each key participant in this project. If you contribute to their achievement - you are well done, your allies are provided.
The world is becoming digital, so the need for IT specialists has increased dramatically in recent years. We need people who are already trained and do work with good quality and predictable results. There is no time for the buildup, and customers no longer want to experiment on themselves. Increasingly, customers are looking for ready-made teams with ready-made practices and proven in practice business cases. The qualification requirements of such teams are quite high, and in the market, when it comes to innovative solutions, there are not so many of them. The outdated classical training model is simply unable to meet growing resource demand — you can see for yourself if you are interviewing, for example, in development teams. The market is experiencing a huge shortage of highly qualified personnel.
Moreover, the risks are caused not only by the shortage itself, but also by the fact that in response to the growing demand, the market was filled with low-skilled surrogate teams, which gained accelerated knowledge and lacked sufficient practical experience. It can be difficult to recognize them in the project bustle, because they usually have professional people on the front.
From the point of view of implementation, the situation looks like this: it’s good if you have enough resources necessary for the project implementation. It is bad when you have to look for a partner and work with an unfamiliar team.
At such times two important things usually save:
Modern IT transformation projects imply not only the digitization of existing business processes of the company, but also a global review of the functioning of the entire organization - access to a fundamentally new level of work. Everything changes as soon as the market moves from mass enthusiasm to new technologies to attempts at real implementations. Many customers are simply not ready to make global changes to their business model. As a result, everything is limited by superficial optimization of cumbersome and inefficient business processes that have been formed over many years. We translated the as-is processes into a figure and continue to work as well as we have worked before, without noticing the obvious opportunities to increase efficiency. The main reasons are inertia of thinking and fear of change. And the older the company, the brighter they appear. The implementation of such projects turns into a protracted positional struggle with the customer’s stereotypes for the team - “we have always worked this way, and everything was fine ...”, “we ourselves know better”, “no, you are not bureaucratic, this is regulation of fundamental aspects of work so there are so many levels of negotiation ", etc.
In one of the consulting projects for an interview, a customer representative spoke about the business processes in which he participates. My question is, what exactly will your unit agree on in this thread? What is the importance of your participation? The customer could not articulate clearly, saying that if they implemented it this way, it means it is important and necessary!
Oddly enough, but often the essence itself, the goal of the project becomes an insurmountable barrier to its implementation. And if the tops of the company are not adherents of global change, only a small part of such projects will live to “combat” exploitation. Tested in practice!
If you look at the reports of leading analytical agencies, you will see that only 15% of modern innovative IT projects are recognized as successful! Why it happens?
Increasingly, projects on the side of customers are initiated under the influence of marketing pressure by vendors, as well as in pursuit of notorious competitors who have already implemented something new and hurried to inform the market about this in countless press releases. At all conferences and forums we hear: “BigData is a must have”, “blockchain is our everything”, “IOT is in every home” and a lot more ...
Without proper IT maturity and experience in implementing such solutions, customers often start a project either with high expectations or without proper goal setting. As a result, we see the following picture: the customer has implemented BigData and uses it to get simple analytics, which can be obtained in cheaper ways. Either he gets a high-quality, multifaceted analytics, but he doesn’t understand at all how to use it in his work. Either understand how to use, but internal processes and IT do not allow it. As a result, the customer is disappointed both in the decision itself and in the performer. Well, who else do we blame?
Awareness comes to the market through trial and error, products go through a so-called self-identification: the terms acquire their true meaning, more user experience and successful implementations appear. To understand how this works, just look at the Gartner HYIP-cycles and see what is now at the peak of “advertising hype”. Here is one of them for 2017.
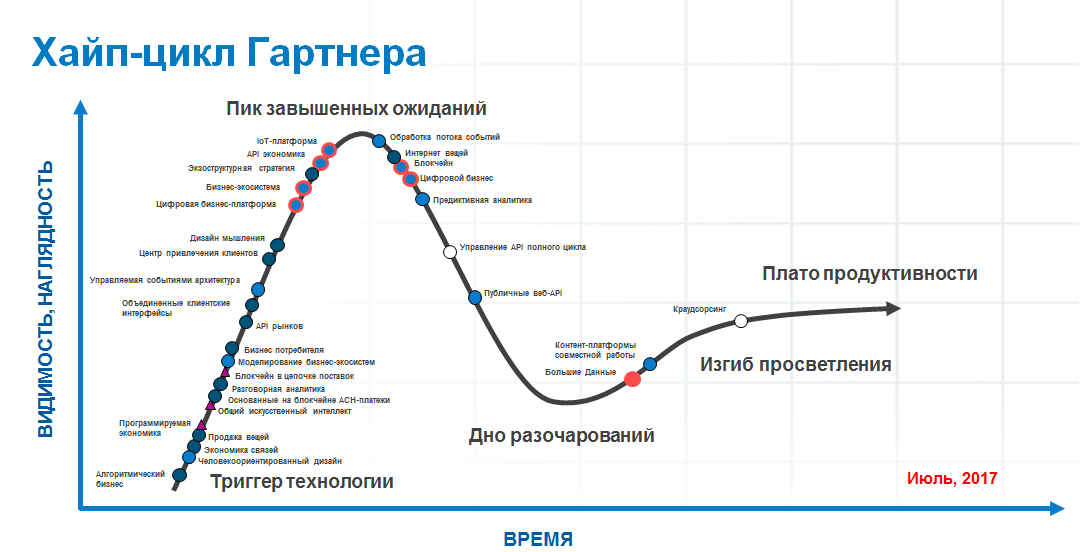
Take, for example, BigData and look at the chart (marked by a red dot). Only now, after almost a decade since the appearance of the first products and solutions that relate exclusively and directly to the problem of processing big data, this technology has passed its “bottom of frustrations” and is beginning to “reach the plateau of productivity”. With other technologies, just about everything is the same.
Often, the voiced problem is clearly visible in the transitions to the cloud: for example, my colleague’s material on what myths are , but the history of exploitation of how the old architecture is transferred to a new platform without understanding its essence .
Usually, this term is understood as the legal aspects of interaction with regulatory bodies. The regulatory framework is a separate headache in the way of modern “digital” projects, especially for the public sector. The fact is that many SNIPs, GOSTs, regulations and decrees, according to which the controlling bodies now work, were written still “with the king of the peas”, when there were no technologies like that. A large number of them are currently simply not applicable. This is really a serious problem that the state itself is aware of. And this is taken into account in the program "Digital Economy", which was approved by the Russian government last year. There was a case in my practice when virtualization did not fit into the security requirements for a large state-owned bank: the standards by which the design was carried out, many years ago were written “with iron”. Then the customer had to turn to the regulators, one of which was FSTEC, to refine the regulatory framework and requirements for the protection of virtual environments. As you know, it was not at all fast! Other technologies are now experiencing similar problems.
Whatever these standards may be - engineering, payment and others - you will have to figure it out yourself, attracting the right people, like a lawyer. Why the most, because the main skill PMA - is to understand how you can implement the project. Most often, your consultants will find a million reasons for why it’s impossible, and not just one opportunity as much as possible.
A striking example is PCI DSS certification .
Or another example - the definition of what is personal data for you .
Let's remember how budgeting takes place at the majority of customers (we remember the states separately and in bright colors). The budget is formed at the beginning of the year, is defended by the Criminal Code (or in other instances) and is often not even revised. When we proceed to the implementation, there will be a major dilemma - which payment scheme to choose. The “fix scope - fix price” work scheme, it is also called “Fixed Fee”, is not very suitable for the contractor, since the requirements are vague, the variability is large, and the budget is fixed. There are huge risks to miss with the budget.
The “Time & Material” scheme is often even unacceptable for the customer. On the one hand, it is impossible to talk about financial planning if you don’t know the cost of implementation (procedural constraints inside), and on the other hand, the customer often doesn’t have enough experience to otrulivaniya such a scheme. And if there is no experience, and even confidence in the contractor, it is almost impossible to convince the customer of its application. For the public sector, this scheme is in general a misfortune: overspending is bad, underdevelopment is doubly bad. I remember a fun project for one of the state services for the development and modernization of their main information system. The customer decided to contract using the “T & M” scheme. This was his first experience. I put money into the budget for the whole year, formed the main directions of development. Further by the contract it was assumed that individual orders would be received by the contractor in the form of private TK, preliminarily evaluated and paid according to the T & M model. First of all, the customer fixed the accumulated bugs - it did not take much time and, accordingly, the budget. And then ... the ideas are over! The field staff simply did not know where to further develop their own system. The project team was only partially able to help, since the task was relatively new, and the team was insufficiently staffed by industry experts and analysts. Realizing that time is ticking and the money is “burning down”, the customer started generating tasks from the category “not really necessary, but suddenly it will come in handy.” Dynamics has increased dramatically, development, too. But when really bright ideas appeared at the customer by the end of the project, the project budget was already over! The customer did not use such a scheme anymore!
The rapid development of innovative technologies opens up new horizons in business development and gaining competitive advantages. At the same time, it generates new risks and threats both for the implementation itself and for the future work of the customer. For example, every year the issue of information security is becoming more acute, and absolutely at all levels. And the whole difficulty lies in the fact that for searching for vulnerabilities and cyber attacks all the same modern technologies BigData, artificial intelligence, etc. are used - but this is a conversation for a whole separate article.
There are many other risks that can suddenly put an end to your project. Previously, they were not so relevant for us. Recently, these risks are often generated by the geopolitical situation in the world. This currency risks (when the dollar rose sharply and iron became "golden"), and the introduction of sanctions, when suddenly in the middle of the project the vendor told you that he could not bring the necessary equipment, and now you have to buy what is in stock supplier, at a price 2 times more expensive ...
If it is interesting, then later I can tell about each area - where there are pitfalls, which my colleagues and I have repeatedly attacked.
In the first case, there will be no profit from the company and your premium, and in the second, something more terrible will happen. But the second case is the Russian roulette, it may be lucky. In practice, risk management is always a delicate balance between “reasonable” and “sufficient”.
Therefore, let's talk a little more about some of the risks of projects that have increased in recent years. Some of them are not new. Some in the realities of the current IT market have acquired new shapes, colors and monstrous features.
What has changed in the last 10 years in IT projects?
There was a need to launch larger-scale integration and product projects in order to gain a tangible competitive advantage in the market. Since the basic “bricks” of the projects have already been written, we are talking about large implementations, where the first place is not the code itself, but performance indicators.
')
Previously, CIO was engaged in automating the company's business processes and ensuring the stable operation of its zoo systems. Now the stage of automation of classic business functions comes to an end: ERP, CRM, BI and other business management tools have already been digitized. Just having automation is no longer a competitive advantage. More important is Time-to-value, Time-to-market, ROE, continuity and cybersecurity. The speed of product launch to the market, ensuring uninterrupted access to services and their security - the main focus is now there.
IT becomes not a service unit, but the core of a business. Any large-scale IT project now involves many processes, and, accordingly, requires the participation of an increasing number of services and top managers. That is why the role of the CIO and its division has grown over the past years. IT literacy requirements for technical unit employees also grew.
Now it is impossible to successfully implement the project without understanding the industry specifics and nuances in the customer's business processes, that is, the work of integrators has become more complicated. The service work model comes to the fore. A large sale is increasingly taking shape almost as a cooperation agreement, but without revenue sharing, although there are such examples in my practice. Projects more and more often begin to develop the “beginning and end” model and turn into a continuous process of development of previously implemented projects. The integrator begins to be perceived as a partner, ready to share responsibility not only for the successful implementation of the project, but also for the business result for which it was launched.
As an example, I can give projects on photo and video recording of violations of traffic rules when the project is implemented at the expense of the executor, and the executor gets the profit from the proceeds generated by the fixing system itself in the form of fines! That is, the system was built poorly or missed with the calculation of the return on investment - get a loss in the project.
Now the phase of automation of the channels of interaction of companies with the surrounding business environment has begun: customers, partners, regulators, and so on. In fact, business is opening itself up in the cyberspace of a new digital market - creating a digital ecosystem around itself. This task is new to the market and carries with it a standard set of risks - financial, investment, operational.
This is mainly due to the lack of accumulated experience and developed standards, guaranteed mechanisms to protect processes and data in cyberspace.
From the point of view of the CIO, the integration of IT and the company's main business continues, respectively, and the growing influence of the IT service on the company's risk management system.
What does this mean in terms of changing the work of the CIO and its subordinates? From the point of view of team leaders?
Now KPI CIO can not be limited to indicators of continuity and cost of ownership of IT. As a key element of any modern company, business indicators are coming to the forefront of IT departments! CIO and its team need to dive even more into the details of the organization’s business, go beyond IT competencies, and even lose them, since most of the IT resources begin to be delivered through the service model. The increased responsibility for the result of the implementation of strategic initiatives makes us pay special attention to risk management in projects. Some of them become an insurmountable barrier for the project team on the path to successful implementation.
... Project implementation deadlines decrease, and the pace grows
In a short time, you need to have time to make a “minimally viable product” for its entry into production, otherwise competitors will do the same. All other improvements later, in the process of testing custom hypotheses. It is important to "stake out the clearing" first. This circumstance forces customers and project teams to change their usual classical implementation models, creating new problems and risks.
The real challenge for the project team is to manage the requirements and expectations of the customer. What is the main difficulty here? Projects are increasingly starting with a minimum set of requirements that are continuously refined and supplemented throughout the project. It often happens that by the end of the project the set of requirements is absolutely “perpendicular” to what was at the start. I have often observed how the customer only by the middle of the project, and sometimes by its end, finally (!) Realized, and what he really wants.
An iterative approach usually helps here - dividing into small sprints and deep customer involvement in the implementation process. And the more such uncertainty, the closer should be the interaction. To create the necessary conditions for effective collaboration, we often land key people from Technoserv on the customer’s site. This greatly improves communication, reduces reaction time, creates the necessary conditions for the integration of project teams, and, accordingly, reduces the amount of work "in the basket."
About expectations - a separate story. On the one hand, it is difficult to manage the expectations of the customer, who himself does not clearly understand what he wants to get at the end of the project. On the other hand, as I wrote earlier, projects are increasingly affecting almost all the functional units of the customer. And each of them is a source of requirements and a participant in the coordination of the final result. KPI of these units is different, and therefore, the conflict of interest can not be avoided! If you can not find a compromise and make friends of the conflicting parties, outright sabotage by the individual participants is provided to you.
In one of our large projects, the problem of sabotage, as agreed with the IT curator, had to be included in the register of key risks and submitted to the management committee of the customer. There was another project when we were building a credit line for one large bank of the top 10. In the working group from the customer were IT, risk takers, security guards, product specialists, lawyers, etc. Each of them solved their tasks, fought for their KPIs, and in order to solve many key issues, they had to involve the top managers of the bank. Fortunately, the project was initiated by the first person of the bank and he was very interested in it. Largely due to this, the system was able to be implemented in the shortest possible time. Probably, we would have done the project, only it would take much more time.
The trust of the top managers to the project manager is usually based on two things: the professionalism of the PM and the quick victories of the team. If trust has not appeared in a short time, then it can be extremely difficult to restore it. For PMA and the team, it is important to understand not only the specifics of the customer’s industry, its problems, but also to know the KPI of each key participant in this project. If you contribute to their achievement - you are well done, your allies are provided.
Personnel as a baseline risk
The world is becoming digital, so the need for IT specialists has increased dramatically in recent years. We need people who are already trained and do work with good quality and predictable results. There is no time for the buildup, and customers no longer want to experiment on themselves. Increasingly, customers are looking for ready-made teams with ready-made practices and proven in practice business cases. The qualification requirements of such teams are quite high, and in the market, when it comes to innovative solutions, there are not so many of them. The outdated classical training model is simply unable to meet growing resource demand — you can see for yourself if you are interviewing, for example, in development teams. The market is experiencing a huge shortage of highly qualified personnel.
Moreover, the risks are caused not only by the shortage itself, but also by the fact that in response to the growing demand, the market was filled with low-skilled surrogate teams, which gained accelerated knowledge and lacked sufficient practical experience. It can be difficult to recognize them in the project bustle, because they usually have professional people on the front.
From the point of view of implementation, the situation looks like this: it’s good if you have enough resources necessary for the project implementation. It is bad when you have to look for a partner and work with an unfamiliar team.
At such times two important things usually save:
- Availability of a list of reliable, proven partners in key deficient areas. Such contacts often help out when their resources are insufficient for large-scale implementation. In terms of burning deadlines, this is always extremely useful and often without damage to the budget. It is worth noting that such partners are not quickly developed, and the interaction is largely based on trust from both sides. The result obtained, as a rule, justifies the effort invested in it.
- Development of your team. That is, constantly learn yourself and teach your people. Conferences, hackathons, courses, trainings - all this works perfectly in a rapidly changing market. Allows you to be at the forefront of technology and motivate the team. Here we work closely with key vendors and partners.
Conservatism of the customer
Modern IT transformation projects imply not only the digitization of existing business processes of the company, but also a global review of the functioning of the entire organization - access to a fundamentally new level of work. Everything changes as soon as the market moves from mass enthusiasm to new technologies to attempts at real implementations. Many customers are simply not ready to make global changes to their business model. As a result, everything is limited by superficial optimization of cumbersome and inefficient business processes that have been formed over many years. We translated the as-is processes into a figure and continue to work as well as we have worked before, without noticing the obvious opportunities to increase efficiency. The main reasons are inertia of thinking and fear of change. And the older the company, the brighter they appear. The implementation of such projects turns into a protracted positional struggle with the customer’s stereotypes for the team - “we have always worked this way, and everything was fine ...”, “we ourselves know better”, “no, you are not bureaucratic, this is regulation of fundamental aspects of work so there are so many levels of negotiation ", etc.
In one of the consulting projects for an interview, a customer representative spoke about the business processes in which he participates. My question is, what exactly will your unit agree on in this thread? What is the importance of your participation? The customer could not articulate clearly, saying that if they implemented it this way, it means it is important and necessary!
Oddly enough, but often the essence itself, the goal of the project becomes an insurmountable barrier to its implementation. And if the tops of the company are not adherents of global change, only a small part of such projects will live to “combat” exploitation. Tested in practice!
Product self-identification of the market
If you look at the reports of leading analytical agencies, you will see that only 15% of modern innovative IT projects are recognized as successful! Why it happens?
Increasingly, projects on the side of customers are initiated under the influence of marketing pressure by vendors, as well as in pursuit of notorious competitors who have already implemented something new and hurried to inform the market about this in countless press releases. At all conferences and forums we hear: “BigData is a must have”, “blockchain is our everything”, “IOT is in every home” and a lot more ...
Without proper IT maturity and experience in implementing such solutions, customers often start a project either with high expectations or without proper goal setting. As a result, we see the following picture: the customer has implemented BigData and uses it to get simple analytics, which can be obtained in cheaper ways. Either he gets a high-quality, multifaceted analytics, but he doesn’t understand at all how to use it in his work. Either understand how to use, but internal processes and IT do not allow it. As a result, the customer is disappointed both in the decision itself and in the performer. Well, who else do we blame?
Awareness comes to the market through trial and error, products go through a so-called self-identification: the terms acquire their true meaning, more user experience and successful implementations appear. To understand how this works, just look at the Gartner HYIP-cycles and see what is now at the peak of “advertising hype”. Here is one of them for 2017.

Take, for example, BigData and look at the chart (marked by a red dot). Only now, after almost a decade since the appearance of the first products and solutions that relate exclusively and directly to the problem of processing big data, this technology has passed its “bottom of frustrations” and is beginning to “reach the plateau of productivity”. With other technologies, just about everything is the same.
Often, the voiced problem is clearly visible in the transitions to the cloud: for example, my colleague’s material on what myths are , but the history of exploitation of how the old architecture is transferred to a new platform without understanding its essence .
Regulator
Usually, this term is understood as the legal aspects of interaction with regulatory bodies. The regulatory framework is a separate headache in the way of modern “digital” projects, especially for the public sector. The fact is that many SNIPs, GOSTs, regulations and decrees, according to which the controlling bodies now work, were written still “with the king of the peas”, when there were no technologies like that. A large number of them are currently simply not applicable. This is really a serious problem that the state itself is aware of. And this is taken into account in the program "Digital Economy", which was approved by the Russian government last year. There was a case in my practice when virtualization did not fit into the security requirements for a large state-owned bank: the standards by which the design was carried out, many years ago were written “with iron”. Then the customer had to turn to the regulators, one of which was FSTEC, to refine the regulatory framework and requirements for the protection of virtual environments. As you know, it was not at all fast! Other technologies are now experiencing similar problems.
Whatever these standards may be - engineering, payment and others - you will have to figure it out yourself, attracting the right people, like a lawyer. Why the most, because the main skill PMA - is to understand how you can implement the project. Most often, your consultants will find a million reasons for why it’s impossible, and not just one opportunity as much as possible.
A striking example is PCI DSS certification .
Or another example - the definition of what is personal data for you .
Classic project budgeting
Let's remember how budgeting takes place at the majority of customers (we remember the states separately and in bright colors). The budget is formed at the beginning of the year, is defended by the Criminal Code (or in other instances) and is often not even revised. When we proceed to the implementation, there will be a major dilemma - which payment scheme to choose. The “fix scope - fix price” work scheme, it is also called “Fixed Fee”, is not very suitable for the contractor, since the requirements are vague, the variability is large, and the budget is fixed. There are huge risks to miss with the budget.
The “Time & Material” scheme is often even unacceptable for the customer. On the one hand, it is impossible to talk about financial planning if you don’t know the cost of implementation (procedural constraints inside), and on the other hand, the customer often doesn’t have enough experience to otrulivaniya such a scheme. And if there is no experience, and even confidence in the contractor, it is almost impossible to convince the customer of its application. For the public sector, this scheme is in general a misfortune: overspending is bad, underdevelopment is doubly bad. I remember a fun project for one of the state services for the development and modernization of their main information system. The customer decided to contract using the “T & M” scheme. This was his first experience. I put money into the budget for the whole year, formed the main directions of development. Further by the contract it was assumed that individual orders would be received by the contractor in the form of private TK, preliminarily evaluated and paid according to the T & M model. First of all, the customer fixed the accumulated bugs - it did not take much time and, accordingly, the budget. And then ... the ideas are over! The field staff simply did not know where to further develop their own system. The project team was only partially able to help, since the task was relatively new, and the team was insufficiently staffed by industry experts and analysts. Realizing that time is ticking and the money is “burning down”, the customer started generating tasks from the category “not really necessary, but suddenly it will come in handy.” Dynamics has increased dramatically, development, too. But when really bright ideas appeared at the customer by the end of the project, the project budget was already over! The customer did not use such a scheme anymore!
The future is no longer the same
The rapid development of innovative technologies opens up new horizons in business development and gaining competitive advantages. At the same time, it generates new risks and threats both for the implementation itself and for the future work of the customer. For example, every year the issue of information security is becoming more acute, and absolutely at all levels. And the whole difficulty lies in the fact that for searching for vulnerabilities and cyber attacks all the same modern technologies BigData, artificial intelligence, etc. are used - but this is a conversation for a whole separate article.
There are many other risks that can suddenly put an end to your project. Previously, they were not so relevant for us. Recently, these risks are often generated by the geopolitical situation in the world. This currency risks (when the dollar rose sharply and iron became "golden"), and the introduction of sanctions, when suddenly in the middle of the project the vendor told you that he could not bring the necessary equipment, and now you have to buy what is in stock supplier, at a price 2 times more expensive ...
If it is interesting, then later I can tell about each area - where there are pitfalls, which my colleagues and I have repeatedly attacked.
Source: https://habr.com/ru/post/374671/
All Articles