Mining browser cryptocurrency unexpectedly rose from the dead
It was believed that the mining of the crypt in the browser is dead, but now it unexpectedly returns to haunt the websites and their visitors again

Over the past few months of 2017, mining cryptocurrency has experienced explosive growth. After many years of deathly silence, the catalyst for this, apparently, was the launch in September of a new mining service in the Coinhive browser. The service delivers a neat software package for website owners, and gave birth to a new idea, which has long been considered dead.
Tried, checked and buried
Mining in the browser, as the name implies, is a method of mining cryptocurrency that occurs inside the browser using a scripting language. It differs from the more well-known cryptocurrency mining system when the user downloads and runs a special executable file.
For the first time, mining in the browser appeared in May 2011 , when the first launch of the innovative service BitcoinPlus.com took place - when Bitcoin was cheap and the mining was simple (do not confuse with another cryptocurrency known as Bitcoin Plus (XBC)). This service was in many ways surprisingly similar to the modern reincarnation, Coinhive. He used JavaScript code for mining, and website owners could subscribe to this service and insert scripts into web pages so that visitors could mine a crypt for them. The big difference was that in 2011, as is clear from the name BitcoinPlus.com, the site mine Bitcoins (BTC), and today's browser miners, like Coinhive, mine Monero (XMR) - a new cryptocurrency focused on privacy. In 2011, before the mining appeared at ASIC (in 2013), Bitcoin was in its infancy, the complexity of mining was small, and the cost of cryptocurrency was even lower. It was almost realistic to figure out the currency with a home computer.
')
And although at that time it was possible to mine Bitcoins via BitcoinPlus.com, in practice this exercise was by and large useless. The rewards were miniscule compared to the required power and electricity. Of course, that was before the price of bitcoins soared - in June 2011, the cost of bitcoins rose to the then maximum of $ 30.

Due to the fundamental problem with profits from browser mining, the service soon disappeared. However, the idea was again restored in December 2013 by a group of students from MIT, in the form of the Tidbit project, allegedly advertised as an alternative way for site owners to earn money. And again, this project did not last long, because soon after its launch, a branch of the US Consumer Protection Agency, located in New Jersey, launched an investigation into a new company on charges of illegally using users ’computer power. The result was a lengthy trial, fully completed only in 2015 .
The prospect of browser mining was very modest. The growing problem of profitability worsened due to an increase in the number of miners at ASIC. This process took Bitcoin mining away from home users and transferred it to an industrial area dominated by massive mining farms that are more familiar to us today. After the disappearance of Tidbit, the idea of browser mining of a crypt based on JavaScript has by and large died again.
But despite all these problems, key lessons have been learned. The purpose of a service like Tidbit has never been the use of separate servers or powerful computers involved in mining. The true power of this service is to scale and use the potentially huge combined power of a large number of visitors to sites with medium hardware. Increasing traffic means increasing profits, and, sooner or later, someone should have come up with an improved way to make browser mining work on end-user computers more efficiently.
Dawn of the dead
Fast forward to September 2017, when the position of cryptocurrency compared with 2013 greatly changed. In April 2013, there were very few types of crypts on the market, and its total capitalization was estimated at only $ 1.5 billion. The crypt market was limited and illiquid, which meant that even if you earn something, it is very difficult to turn it into fiat money and spend. This contrasts strongly with September 2017 , when the market capitalization reached $ 166 billion, distributed over more than a thousand different cryptocurrencies.
In addition to the variety of coins, a variety of reward mechanisms for working with them also appeared. Some, like Bitcoins, can be mined through proof of work [proof-of-work, PoW], using power-hungry ASICs - although there have been attempts to change this with the help of various branches of the project, for example, Bitcoin Gold (BTG) and Bitcoin Diamond (BCD ), designed for mining through the GPU. Other cryptocurrencies like Monero, Ethereum (ETH), Ethereum Classic (ETC) and Dash (DASH) can be mined using GPUs available in stores, which can be found in many computers. There are currencies that are more suitable for mining on the CPU - Monero and Verium Reserve (VRM). The trading environment has also changed - it is now much easier to make exchanges of fiat money and a crypt, which makes the latter more useful and valuable.
It is against this background that the Coinhive service released its scripts capable of mining Monero, which brings the idea of browser mining to life.
News spreads quickly
Coinhive is advertised as an alternative to browser advertising. The motivation is simple: users pay for content indirectly, by mining, when visiting the site, and site owners do not have to bother users with ads, trackers and other common accessories. Users end up with cleaner, faster, and potentially less dangerous sites, and everyone is happy. What could go wrong?
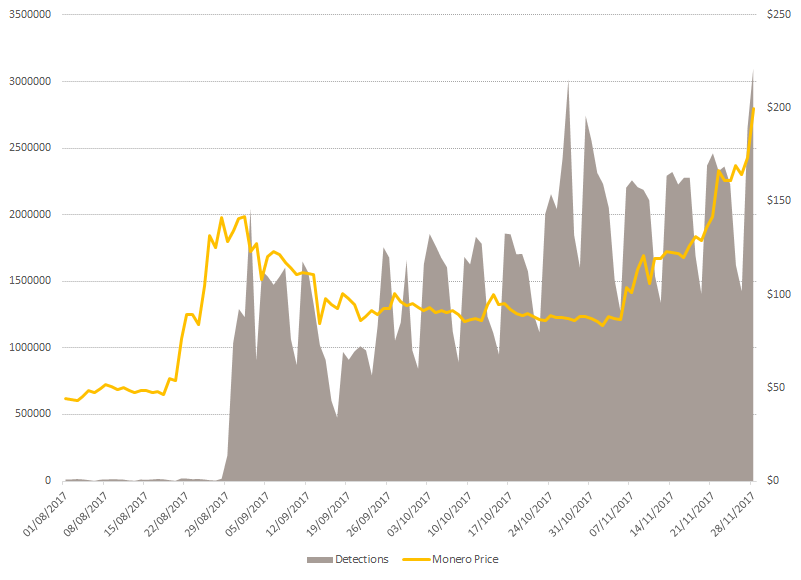
Soon after the release of the service, hash counting speeds began to grow rapidly. The hash rate is the number of hashes calculated by all miners in total, measured as the number of hashes per second. Usually this indicator is measured in millions (MH / s). Hashing is a calculation of cryptographic parameters used to process transactions. Miners participating in the general calculations of the fund receive their share of the income generated by the entire fund.
According to the Coinhive blog, hash counting speed jumped from 0 MH / s to 3 MH / s in a couple of days, and then increased to 13.5 MH / s over the course of a week. To make it clear, the total speed of hash calculation for the entire network (the total amount of mining power of all computers involved in this) at Monero on September 20, 2017 was within 260 MH / s. The total capacity of the Coinhive pool has reached 5% of this figure, which is pretty good for such a short period.

Monero can be mined both on the CPU and on the GPU, but the mining service in the Coinhive browser only works with the CPU, and this restriction seriously reduces potential earnings.
To maximize profits, the script is best placed on websites with high traffic, as well as on sites where the user stays on the page for a long time. According to one of the first users, the profit from mining on his website turned out to be much smaller than the profit from advertising.
To its credit, Coinhive should say that the project recommends transparency with the site visitors and notifying users about what is happening mining, and even better, suggest ways for users to participate in it. Unfortunately, despite good intentions, unprincipled operators quickly adopted the idea of secret mining in the hope that users would not notice anything.
The beginning of the stream
The first popular site to start using Coinhive was The Pirate Bay torrent tracker. The history of this site is not smooth, and since it is very popular ( taking 161 places in the global ranking of sites with 290 million visitors over the past six months), it is constantly looking for alternative ways to monetize its traffic volume. His initial mining attempts were quickly noticed by users who didn’t like it very much. At least in this case, the decision to use Coinhive was taken by the site owners.
Another popular project soon followed The Pirate Bay - this time the Coinhive miner was discovered on two Showtime sites . One of the participating sites provided streaming video, it had a lot of traffic and users stayed on the page for a long time while the video was being transmitted to the browser. Showtime is a paid service, so it is rather strange that users were forced to pay for content twice. The scripts were quickly deleted after detection, which suggests that they could be placed there with malicious intent.
Soon followed by reports of many other sites where Coinhive mining scripts were discovered. During the Thanksgiving Day holiday in the USA, the Coinhive miner was discovered in the LiveHelpNow widget used on many different sites and offering chat with customer support. The reason for this was that one of the CDN servers used by LiveHelpNow was compromised. As in the case of Showtime, LiveHelpNow is a legitimate and profitable business, so it’s not clear why he had to risk user confidence in order to earn a few extra dollars. So, the most likely option is when a server was compromised by a third party, possibly working in a company.
Mining in the browser periodically appears in other places:
- These scripts have been seen already in several extensions and browser plugins.
- Fake support pages build miners to earn even more. The load on the CPU caused by mining can help convince the user of the problems and increase the chances of getting caught.
- People even try to practice mining on reserved domains, such as where you rarely find yourself, mistaking the name of the site.
Why is browser mining gaining momentum?
The reasons for the return of mining in the browser a lot. Unlike previous unsuccessful attempts, recent developments in the field of cryptocurrency made this occupation more profitable. Consider some of the factors in more detail.
The emergence of cryptocurrency concentrating on privacy
Privacy is important if you want to secretly mine coins so that other people cannot trace them to you. Monero, which appeared on the market in 2014, offers a high level of transaction privacy. Unlike other crypts using public transparent block chains, where transaction addresses are available for viewing by any person, Monero works differently. By default, everything is hidden in it, including the amount of the transfer, the sender and the recipient. There is an option in which wallet owners can selectively disclose information using the “ key viewer ”, but cybercriminals are unlikely to use this feature.
Ease of use
As mentioned, Coinhive provides a convenient and easy-to-use software package for people who want to participate in the mining of Monero. All you need to do is add a few lines of code to the code for the website. No need to force visitors to download and install executable files.

The mining process can start quickly and without unnecessary noise, unless the processor is very overloaded, which makes mining easy to detect.
Mining profitability on ordinary computers on a large scale
The cost of Monero has recently surpassed the $ 300 mark, and the total computing power of the network reaches 300 MH / s, so profitable mining is a large-scale game that requires careful cost estimation.
In the case of mining in the browser, its cost is borne mainly by visitors, due to the wear of iron and waste of energy. The scale is achieved when using sites with high traffic and long presence on the pages.
Now Coinhive pays out 0.000104 XMR ($ 0.025) per million hashes . If you take a PC user with an average Intel i7-7700K processor capable of processing 300 H / s, then he will need to spend 3333 seconds on the site, or 55 minutes to calculate a million hashes. But if you can force 3333 users to spend one second on the site, the result will be the same.
Even under optimal conditions, the number of hashes produced in each case will be small, but with distributed computer power everything depends on the scale, and the world is going to go down the line.
Cryptocurrency growth factor
As we have already noted, the value of rewards for mining is small, at least for the first time. To better understand the situation, you need to look at the profitability of this occupation in the long term and take into account the macroeconomic component. The cost of cryptocurrency type Monero is growing at an impressive pace. In 2017, the cost increased from $ 13 to $ 300. Under such conditions, when the cost of Monero can grow strongly in dollars in a relatively short time, mining Monero can become attractive. A small amount of coins mined today will be able to cost a lot of money in just a few months (or be very cheap, depending on the crypto economy).
Reflecting the increase in interest in the crypt and its cost, in recent months there has been a big jump in the number of miners we found, based on both executable files and browsers.
Minim on the go
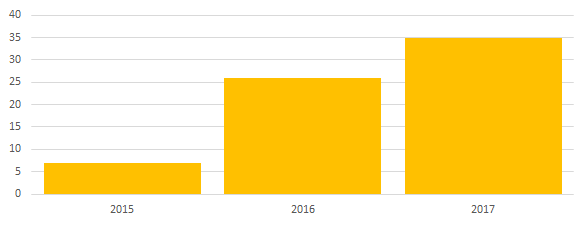
Hidden mining is not limited to desktop computers and servers. Internet-connected mobile devices are increasingly becoming its target. In recent years, we are witnessing an increase in mining on mobile phones. In 2016, we found 26 different Android applications involved in mining cryptocurrency. In 2017, we have already found 35 - 34% more.
The power of modern mobile phone processors can be comparable to the power of lower- or middle-class desktop computers, which helps increase the value of mobile mining. But this process is always energy-intensive, which is why the greatest problem of mobile mining will be the rapid consumption of battery power, because battery manufacturing technology lags behind the growth of computing power. Mobile mining will inevitably be noticed due to excessive heat and a rapid drawdown of the battery, not to mention the problems with the speed of work that may arise from the device.
What awaits us in the future?
If we look at the cryptocurrency market as a whole, we can see that along with a multiple increase in the cost of cryptocurrency, interest in malicious mining, both on the basis of browsers and executable files, also increases.
And with increasing interest in activity, more and more people are connecting, both miners and tool makers. Coinhive, albeit the most famous project, does not own the entire market. Similar projects appear, for example, Crypto Loot , or JSEcoin , which has been in beta testing since August 2017, which are also trying to grow.
Symantec has been witnessing a significant jump in mining in recent months, which is reflected in the number of detections of harmful applications. Despite the sincere desire of most of the mining projects in the browser to offer a real and potentially better alternative to the traditional ways of making money, the sad reality is that this method can be misused, which is actually happening.
Increasing user awareness and detection of this activity by security companies will launch a new arms race between cybercriminals and defenders. Recent innovations in the malicious use of browser scripts for mining, such as hidden pop-up windows, in which the miner runs, are signs of the presence of this process. A wide range of malware distribution channels and detection avoidance technologies can be expected to help spread and extend the mining process to maximize profits. As long as current factors work in favor of mining, we can expect to maintain or even increase interest in mining in browsers in the short and medium term.
How Symantec helps prevent browning mining
Symantec carefully monitors the growing mining trend in browsers. If necessary, we make changes to prevent the work of unwanted miners cryptocurrency and theft of your computer resources in order to enrich third parties.
Site owners need to follow the injection of mining scripts into the code of their site. Our network solutions can help to notice this activity in network traffic when your server communicates with visitors. In addition, the file system scan can show all files that may be associated with mining in the browser, which will help you detect and delete this unwanted content.
Symantec helps prevent theft of computer resources by protecting your computer at various stages of an attack.
Blocking network traffic associated with mining in the browser
Any software for mining, whether it is based on files or on a browser, should be able to communicate either with a network of cryptocurrencies or with a pool of miners for data exchange - that is, for proving that work has been completed. Without such a connection, it cannot get the data needed to generate hashes, and it becomes useless. You can also immediately block downloading scripts for mining. Our network protection works on end devices as well as gateways and in the cloud. All these solutions help to create reliable protection against unwanted mining.
Here are some of the network protection signatures aimed at detecting mining in a browser:
Web Attack: PUA.JSCoinminer Download
Web Attack: JSCoinminer Download
Web Attack: JSCoinminer Download 6
Web Attack: JSCoinminer Download 7
Web Attack: JSCoinminer Download 8
Web Attack: JSCoinminer Download 10
Web Attack: JSCoinminer Download 12
Web Attack: JSCoinminer Download 13
Web Attack: JSCoinminer Download 14
Audit: JSCoinminer Download 3
Block mining on end devices
Our solutions for end devices are able to recognize and block all types of mining, based on both executable files and browsers. These solutions can prevent the installation and launching of mining programs. Browser mining scripts are recognized as PUA.JScoinminer .
Source: https://habr.com/ru/post/374131/
All Articles