Cryptominer viruses form botnets earning hundreds of thousands of dollars for their owners.

Monero and Dash are especially popular with intruders
Over time, miner viruses are becoming increasingly popular. They appeared many years ago (a post about one such was published on Habré back in 2011), now such malware has become very common. The attackers, hoping to get a cryptocurrency, the rate of which is now constantly growing, infect more and more computers. Through the protection of PCs and networks, malware penetrates in the usual way - either through vulnerabilities in the OS, or with the help of the user himself who can thoughtlessly open the application in an e-mail message with a title like “Hi, I'm Christina, here are my photos. There are, of course, other ways, but social engineering has not been canceled.
By itself, the crypto-miner virus does not do anything wrong with the victim's computer, because the creators of such applications themselves are interested in making the machine work well. Experts say that in the last month alone, several large botnets have been identified that are aimed at making a profit from mining.
The problem for the victim is that her computer infected with a crypto-miner runs much slower than usual, because the system’s resources are mining. This is bad if we are talking about a single user, and even worse if the network of the whole enterprise is infected. In this case, workflows begin to slip, and the reason why computers started to work slowly is not always and immediately detected.
')
The network intruders attack the network by exploiting a vulnerability like EternalBlue . The most interesting thing is that the cryptomineer collector is sold, it is offered, for example, in Telegram.
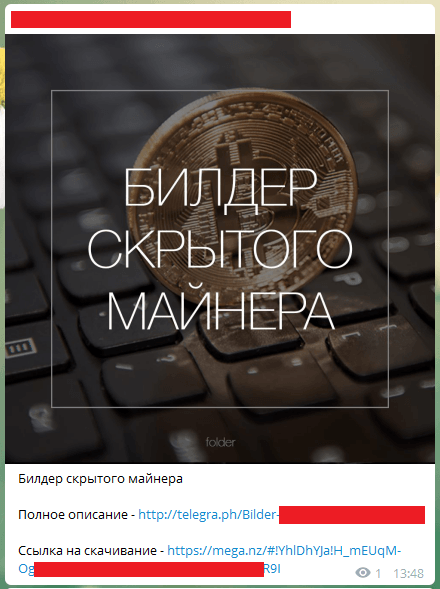
This collector gives you the opportunity to test the performance of the demo version of the virus. Well, after the approbation of the demo, you can easily buy the full version of those who distribute such ads.
There are a lot of miners, and the difficulty of detecting them is that mining itself is a standard process. These are not attempts to erase or modify files, change the contents of the boot sector of a hard disk, etc. No, mining in the usual case will not be determined by antivirus. Therefore, antivirus developers have to look for new ways to determine the presence of such programs on victims' computers.
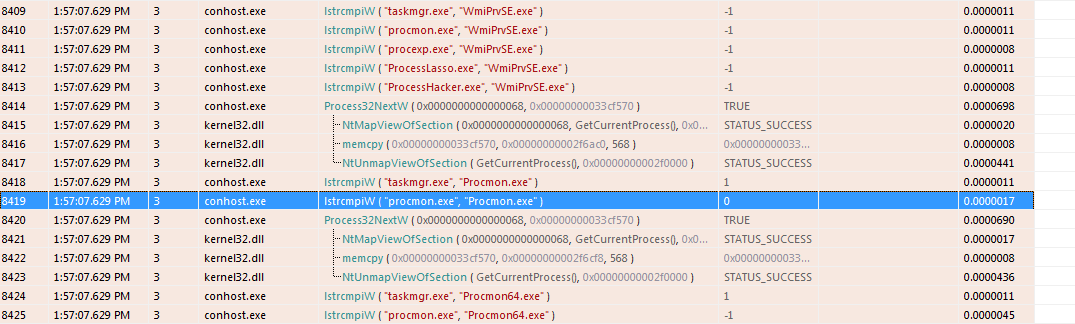
Victims may not even be aware of the presence of a malware on a PC, because advanced malware stops working during the launch of “heavy” applications like PCs on a PC. As a result, the user does not feel the effect of the virus, and he quietly mines the cryptocurrency.
A few days ago an article was published on the Securelist resource, which refers to the discovery of a fairly large “cryptobotnet”, which includes more than 5,000 different computers with the Minergate miner installed . And this, by the way, is quite a “white” miner, which the attackers secretly installed on the computers of the victims.
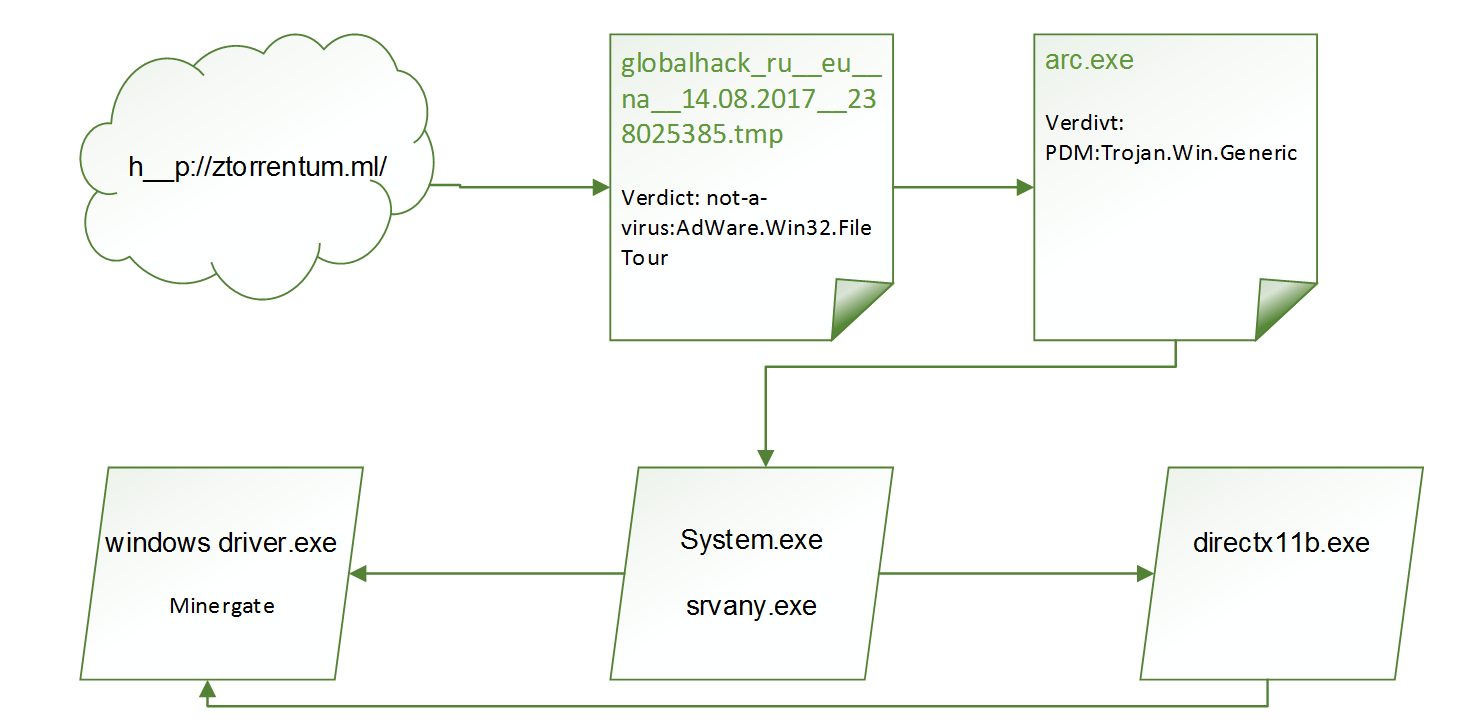
The installer of the program was downloaded by victims from file hosting sites as either keys for unlocking trial versions of programs, or as any other “white and fluffy” software. Once the program is loaded and running, the installer starts downloading the dropper miner. That, in turn, writes down Minergate and loads a number of tools which ensure continuous work of the miner as a system process.
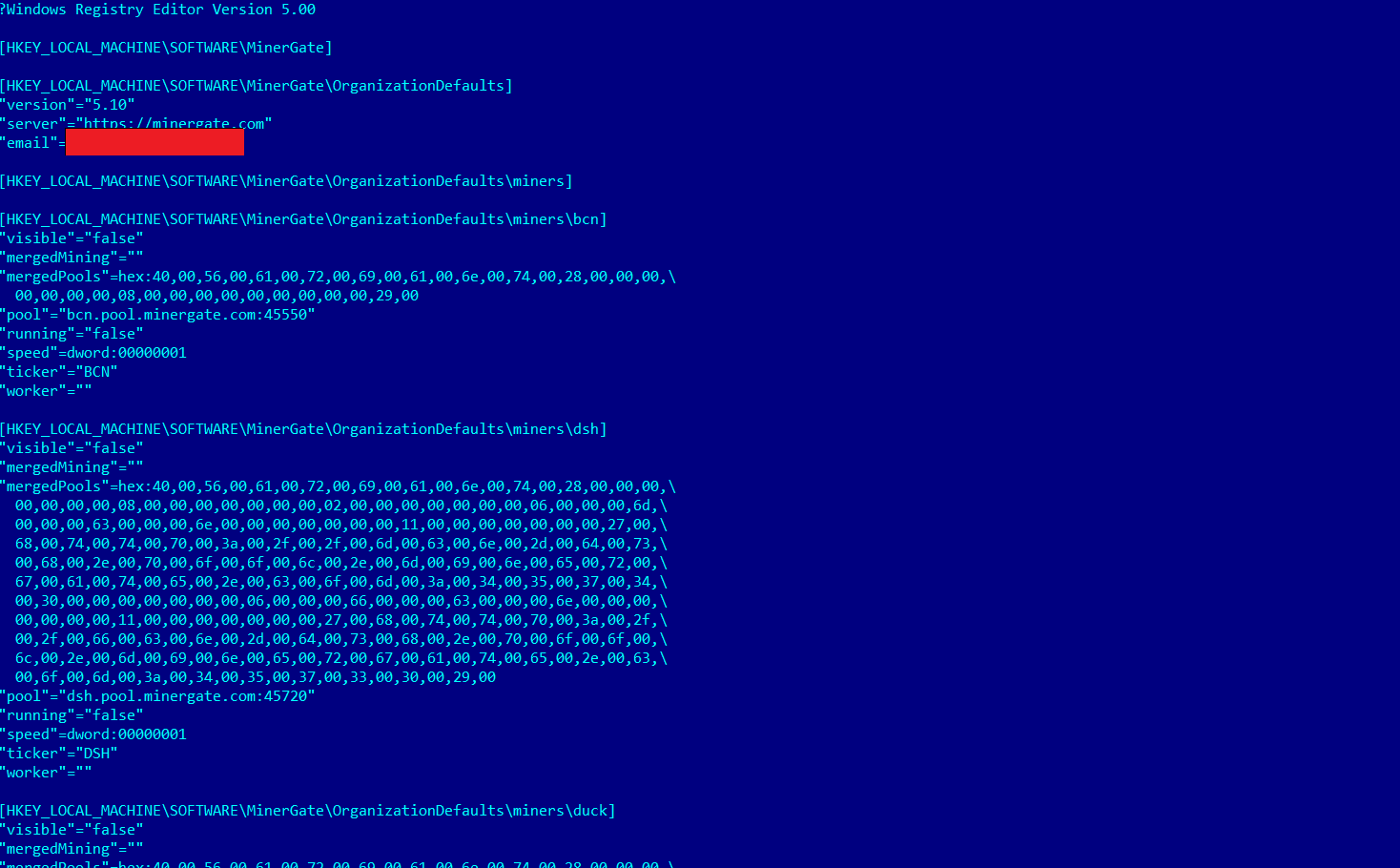
Now, in contrast to the same in 2011, malefactors with the help of miners receive not Bitcoin or air, but Monero and Zcash. This choice is due to the fact that both coins provide for almost complete anonymity - it is difficult to track them.
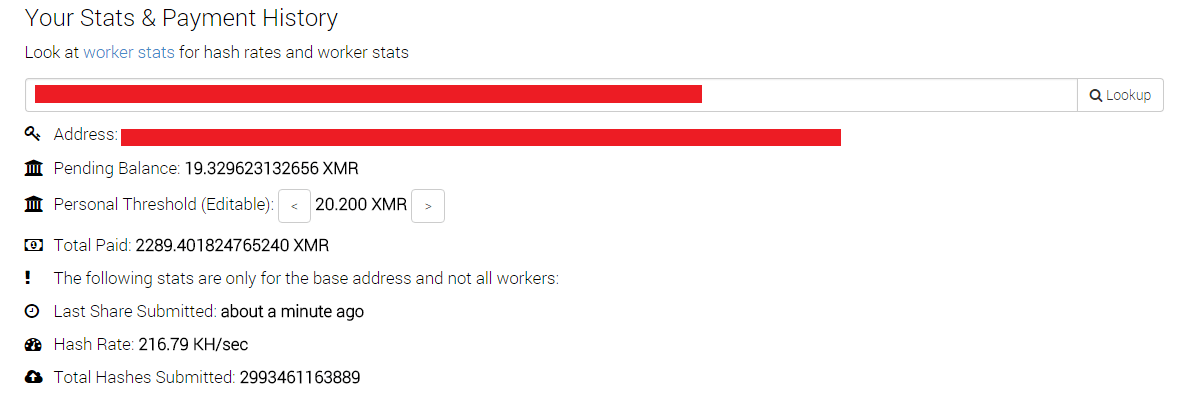
Earnings of this kind are quite high. The illustration above shows the total withdrawal of funds from the intruders' wallet. At the current exchange rate, Monero (XMR) is over $ 200,000.
According to representatives of Kaspersky Lab, at the moment two botnets with cryptomines are found. In each - a few thousand "bots", as mentioned above. So far, there are no particularly reliable ways to combat this kind of malware, but a number of companies that produce anti-virus products are making efforts to create a sufficiently effective tool to combat such software.
Source: https://habr.com/ru/post/373785/
All Articles