Money WannaCry brought in untraceable Monero cryptocurrency
On August 3, the owners of WannaCry wallets withdrew money from them, transferring them in small installments of 7-10 BTC. According to the testimony of the bot @actual_ransom , the contents of the purses changed as follows:
August 3rd
52.19666422 BTC ($ 142,361.51) - 338 payments, 0 withdrawals
withdrawal 7.34128314 BTC ($ 20,055.52 USD)
withdrawal 8.73261636 BTC ($ 23,856.48 USD)
9.67641378 BTC withdrawal ($ 26,434.83 USD)
Withdrawal of 7.06939288 BTC ($ 19,318.06 USD)
Withdrawal 10.06868926 BTC ($ 27,514.04 USD)
Withdrawal 9.03851401 BTC ($ 24,698.95 USD)
9.67641378 BTC withdrawal ($ 26,508.37 USD)
August 4
0 BTC ($ 0) - 345 payments, 7 withdrawals
')
Obviously, the owners of the cryptographer should have tried to anonymize money. They could use the service of washing , but still such services operate within the pseudo-anonymous system Bitcoin, that is, the traces still remain in the blockchain. Therefore, the attackers chose a more reliable option.
According to the Italian company Neutrino, which specializes in information security, the owners of a cryptographer have withdrawn funds in a completely anonymous and untraceable digital currency XMR ( Monero ), writes Ars Technica .
Like other cryptocurrencies, Monero is based on the blockchain, but it uses a cryptographic scheme like “ring signatures” (ring signatures) to ensure anonymity.
Ring signatures - a simplified version of group signatures, designed for those cases where the participants of the scheme do not want to cooperate with each other, and the scheme does not provide for a manager (as opposed to group signatures). Ring signatures were developed by the authors of the RSA algorithm Rivest and Shamir, in collaboration with Tauman.
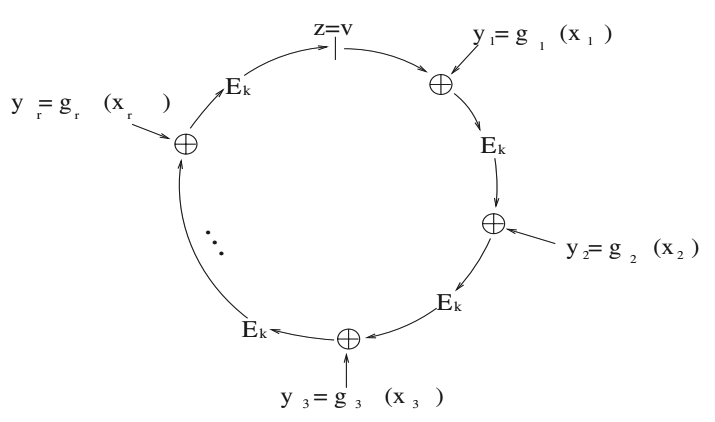
Ring Signatures
The peculiarity of ring signatures is that the one who signs the transaction sets an arbitrary set of possible signers, including himself, and calculates the signature exclusively independently using his secret key and the public keys of other users. In such a system, other participants may not even know that their public keys are used by an unknown person to sign some document that they have never seen. However, such a scheme is very effective and ensures the anonymity of transactions, because when examining the blockchain, an external observer cannot say which parties were involved in the transaction.
The payment system Monero recently attracted attention when its support was announced by the hacker group Shadowbrokers (it announced that it would accept XMR as payment for its Monthly Dump Service monthly payment service). Interestingly, it is this hacker group that stole from the NSA and published the ETERNALBLUE and DOUBLEPULSAR exploits with 0day vulnerability in SMB. They were used by cryptographer. However, there is no evidence of a link between Shadowbrokers and WannaCry.
But it is known that another malware began to spread before WannaCry, which used the same exploits and vulnerabilities. He had exactly the same distribution mechanism: port scanning, using the ETERNALBLUE exploit, and then using the DOUBLEPULSAR exploit. This malware was Adylkuzz crypto miner, which mine is ... right, Monero cryptocurrency. The Adylkuzz epidemic did not attract much attention, also because the malware did not cause any harm to the infected systems: the computers just started to work a little slower.
It should be noted that the owners of WannaCry have chosen not the best time for the withdrawal of bitcoins: right after this, the BTC jumped in price (on August 3, the exchange rate was $ 2814, and now $ 3239).
And another fact related to WannaCry: just a few days ago, after the hacker conference DEF CON, 23-year-old British information security expert Marcus Hutchins, better known by his nickname MalwareTech, was detained. It was this guy who accidentally stopped the spread of WannaCry infection by registering a stop domain for himself.

The Englishman has already admitted that he wrote part of the Kronos banking trojan code. Together with accomplices, they sold at least one copy of the Trojan for $ 2,000, and personally Hutchins is accused of retailing the program for another $ 7,000. On Friday, August 4, Marcus was released on bail of $ 30 thousand, but he was forbidden to fly home. He must be in the United States and wear a GPS tracker.
August 3rd
52.19666422 BTC ($ 142,361.51) - 338 payments, 0 withdrawals
withdrawal 7.34128314 BTC ($ 20,055.52 USD)
withdrawal 8.73261636 BTC ($ 23,856.48 USD)
9.67641378 BTC withdrawal ($ 26,434.83 USD)
Withdrawal of 7.06939288 BTC ($ 19,318.06 USD)
Withdrawal 10.06868926 BTC ($ 27,514.04 USD)
Withdrawal 9.03851401 BTC ($ 24,698.95 USD)
9.67641378 BTC withdrawal ($ 26,508.37 USD)
August 4
0 BTC ($ 0) - 345 payments, 7 withdrawals
')
Obviously, the owners of the cryptographer should have tried to anonymize money. They could use the service of washing , but still such services operate within the pseudo-anonymous system Bitcoin, that is, the traces still remain in the blockchain. Therefore, the attackers chose a more reliable option.
According to the Italian company Neutrino, which specializes in information security, the owners of a cryptographer have withdrawn funds in a completely anonymous and untraceable digital currency XMR ( Monero ), writes Ars Technica .
Like other cryptocurrencies, Monero is based on the blockchain, but it uses a cryptographic scheme like “ring signatures” (ring signatures) to ensure anonymity.
Ring signatures - a simplified version of group signatures, designed for those cases where the participants of the scheme do not want to cooperate with each other, and the scheme does not provide for a manager (as opposed to group signatures). Ring signatures were developed by the authors of the RSA algorithm Rivest and Shamir, in collaboration with Tauman.

Ring Signatures
The peculiarity of ring signatures is that the one who signs the transaction sets an arbitrary set of possible signers, including himself, and calculates the signature exclusively independently using his secret key and the public keys of other users. In such a system, other participants may not even know that their public keys are used by an unknown person to sign some document that they have never seen. However, such a scheme is very effective and ensures the anonymity of transactions, because when examining the blockchain, an external observer cannot say which parties were involved in the transaction.
The payment system Monero recently attracted attention when its support was announced by the hacker group Shadowbrokers (it announced that it would accept XMR as payment for its Monthly Dump Service monthly payment service). Interestingly, it is this hacker group that stole from the NSA and published the ETERNALBLUE and DOUBLEPULSAR exploits with 0day vulnerability in SMB. They were used by cryptographer. However, there is no evidence of a link between Shadowbrokers and WannaCry.
But it is known that another malware began to spread before WannaCry, which used the same exploits and vulnerabilities. He had exactly the same distribution mechanism: port scanning, using the ETERNALBLUE exploit, and then using the DOUBLEPULSAR exploit. This malware was Adylkuzz crypto miner, which mine is ... right, Monero cryptocurrency. The Adylkuzz epidemic did not attract much attention, also because the malware did not cause any harm to the infected systems: the computers just started to work a little slower.
It should be noted that the owners of WannaCry have chosen not the best time for the withdrawal of bitcoins: right after this, the BTC jumped in price (on August 3, the exchange rate was $ 2814, and now $ 3239).
And another fact related to WannaCry: just a few days ago, after the hacker conference DEF CON, 23-year-old British information security expert Marcus Hutchins, better known by his nickname MalwareTech, was detained. It was this guy who accidentally stopped the spread of WannaCry infection by registering a stop domain for himself.

The Englishman has already admitted that he wrote part of the Kronos banking trojan code. Together with accomplices, they sold at least one copy of the Trojan for $ 2,000, and personally Hutchins is accused of retailing the program for another $ 7,000. On Friday, August 4, Marcus was released on bail of $ 30 thousand, but he was forbidden to fly home. He must be in the United States and wear a GPS tracker.
Source: https://habr.com/ru/post/373697/
All Articles