Confidential documents from Office365 users are searchable at Docs.com
Docs.com with the new Doxs.com logo. Rebranding offer from Kevin Beaumont. Illustration: Kevin Beaumont
Docs.com is a public document hosting service for Office365 users. Not all Microsoft users are literate professionals. Some do not understand what they are doing. For some unknown reason, people publish their confidential documents on Docs.com public hosting, including password lists, social security numbers, SWIFT code details, bank accounts, investment portfolios, divorce agreements, work invitations and much more.
According to the caustic remark of one of the specialists, after such a story with massive “self-coking” it is appropriate to rename Docs.com to Doxs.com. He even painted a new logo (see above).
Through the search line on the site files with user passwords are available. This was first noticed by the British security systems architect Kevin Beaumont. On March 25, 2017, he wrote about this on his Twitter account - and the information went to the masses. People began to search for open documents on Docs.com for different keywords, not just passwords.
')
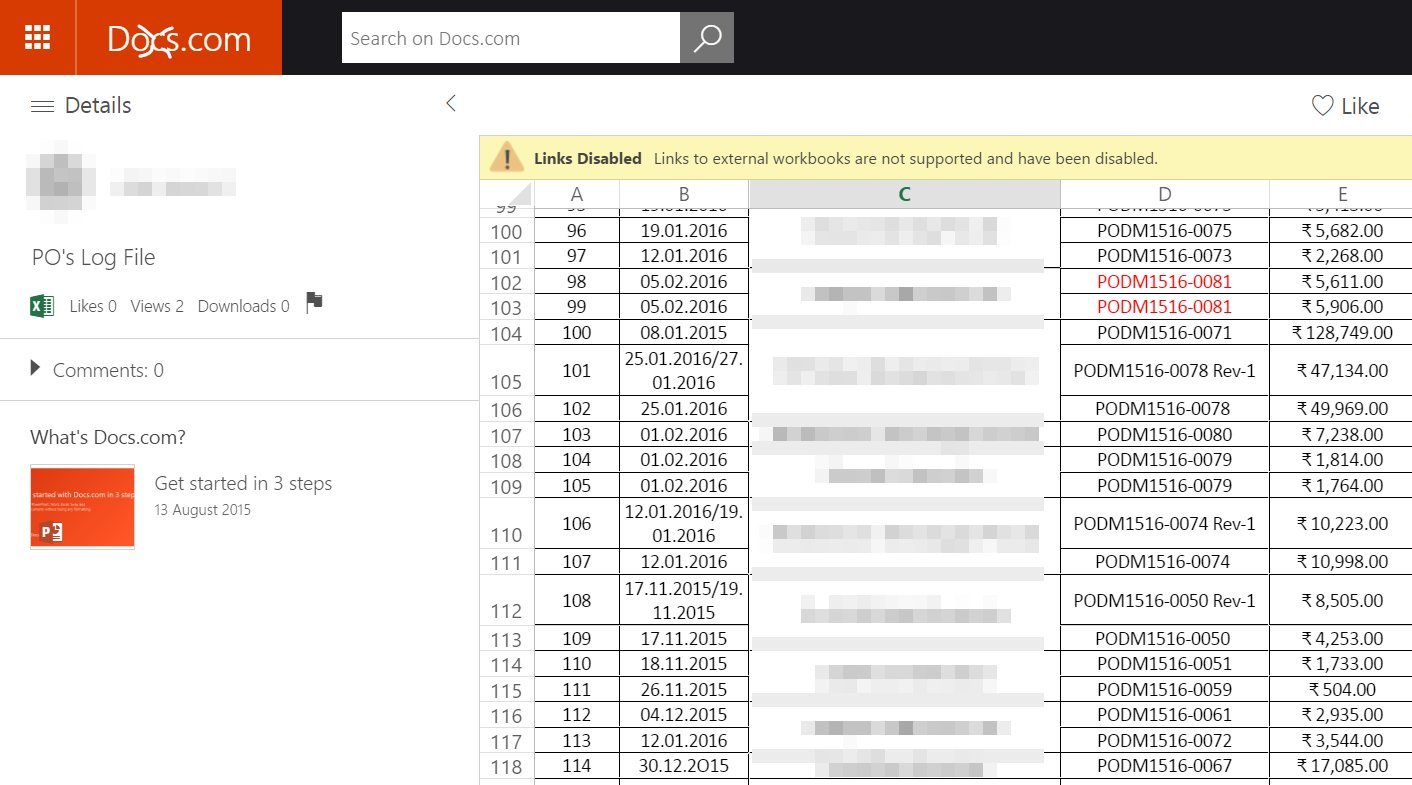
Fragments of some confidential documents that are found on Docs.com
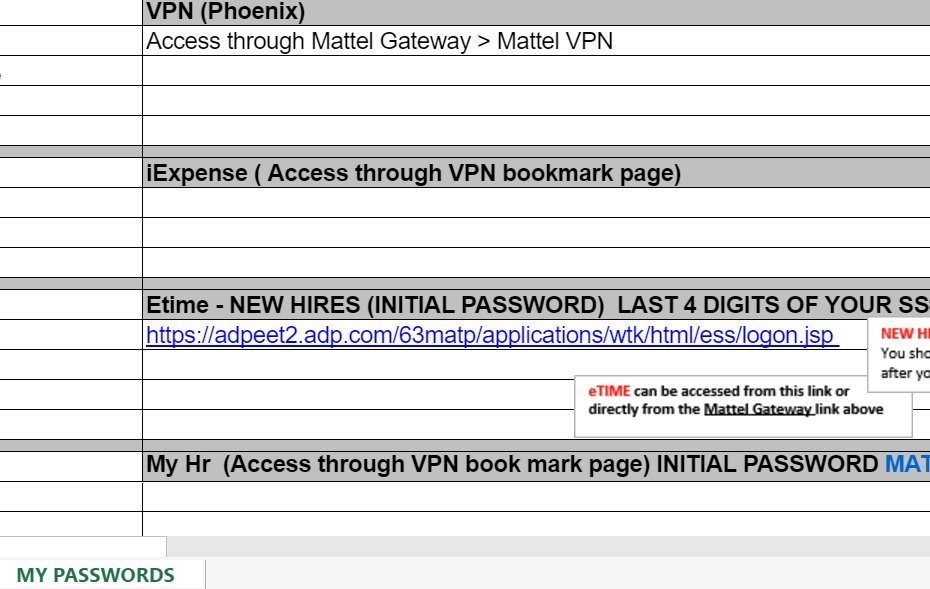
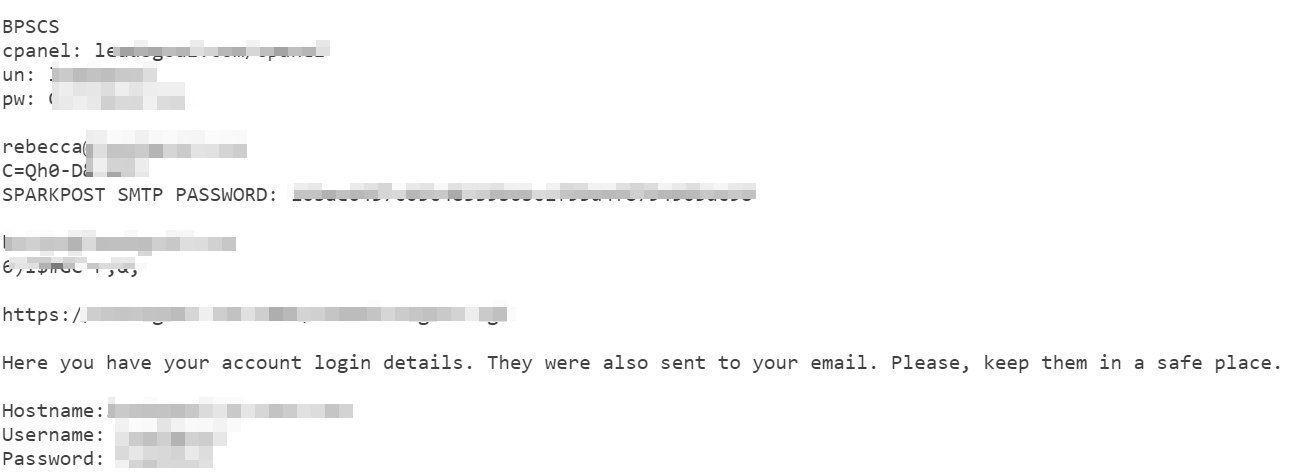
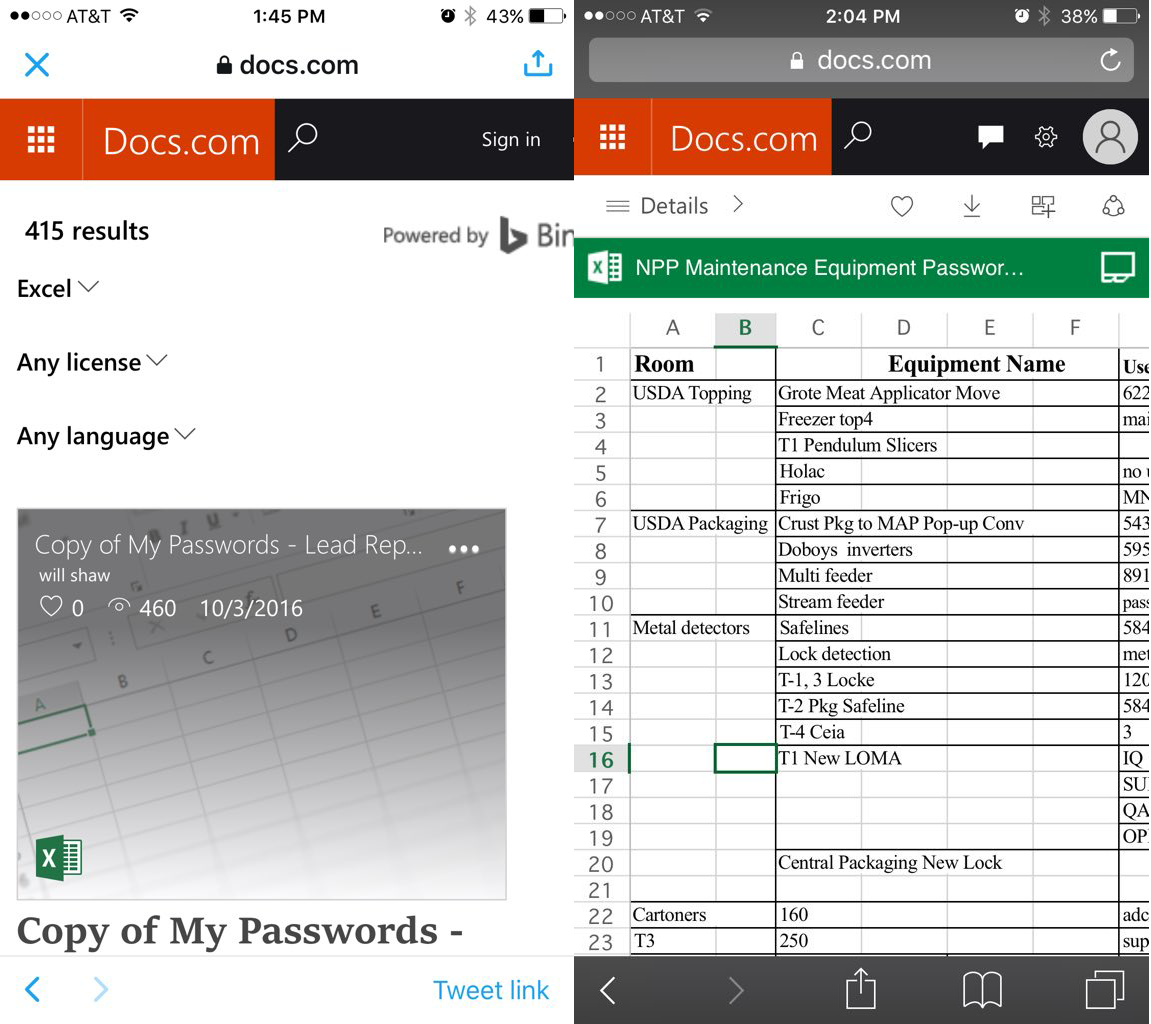
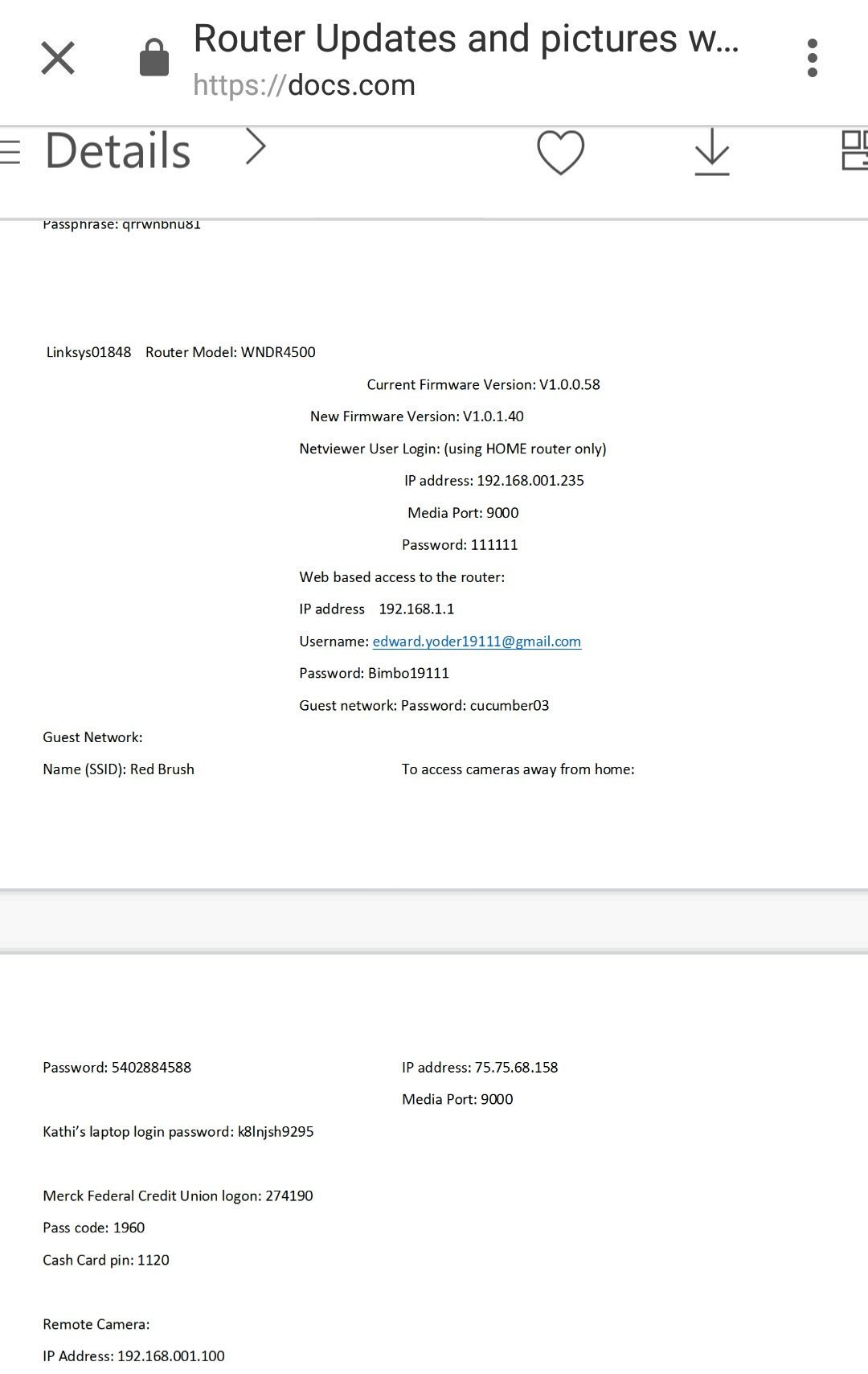
On March 26, about this case of mass self-docking, when hundreds or thousands of users voluntarily self-compromise themselves by laying out their documents, wrote the ZDNet publication.
Microsoft responded quickly: it removed the search string from Docs.com. At the same time, a number of incoming links and referrals to Google search were blocked and access to public documents was blocked. But confidential information fell into the index of all search engines, and the documents still remained searchable. This is exactly the situation when Bing comes to the rescue.
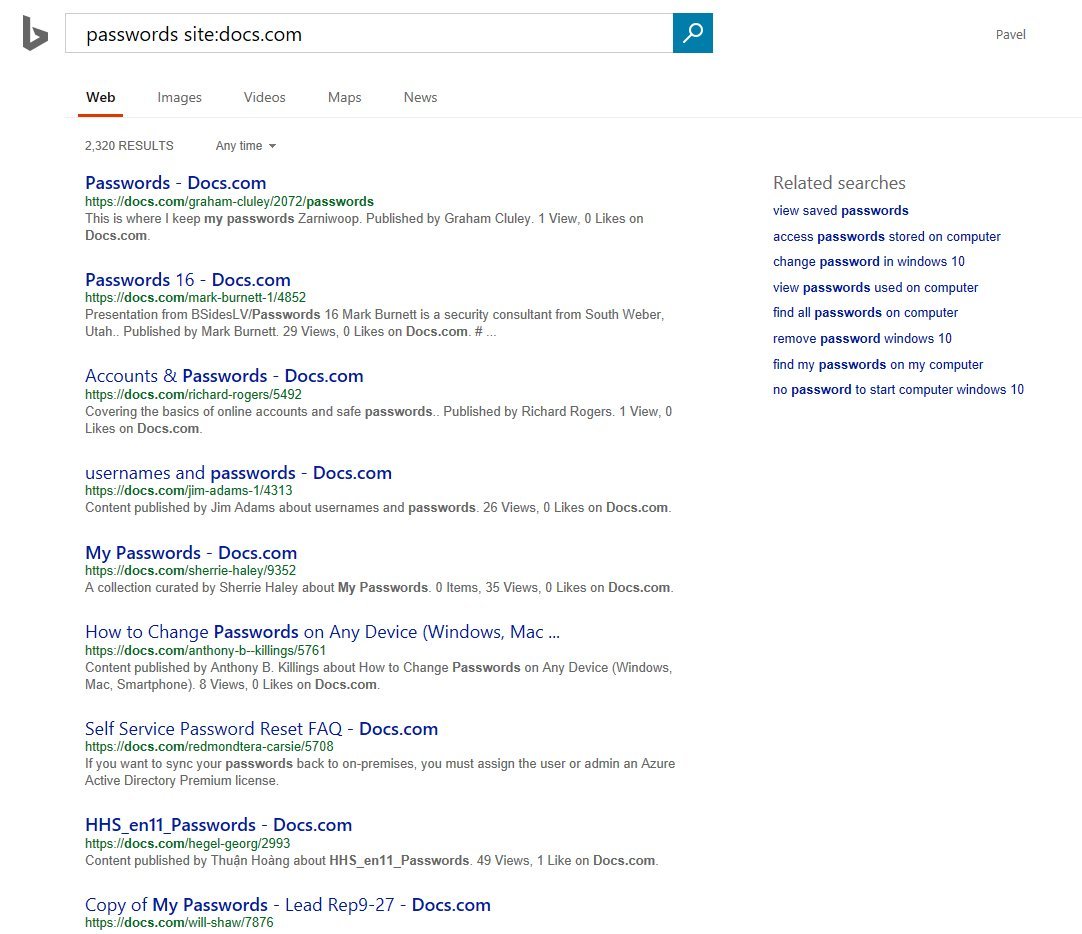
In addition, Microsoft has blocked far from all confidential information. For example, various personal medical records remain publicly available.
Obviously, some users of Office365 and Docs.com accidentally posted their documents in open access. It seems that this is quite a typical situation for many, because a lot of documents have been published. Maybe someone wanted to pass the document to a colleague or relative, not suspecting that all information is indexed by search engines.
Among the most unusual documents found in the early days of mass doxing is a list of logins and passwords for a variety of devices, including metal detectors and other devices. Names, addresses, social security numbers, bank account numbers, postal addresses, and phone numbers of people who are transferred to a collection agency for recovering debts. The medical data, including the therapist's records, along with photographs of the patient, and here the credentials for entering the medical records system. A document for registering a new employee with instructions on how to log into the local local network for the first time (with a username and default password). Real logins and passwords received by email from the administrator and saved as Word documents.
It was a real storehouse of personal information. They say that these data have been open for years. The site constantly appears "fresh" from new users. People still continue to inadvertently post information to the public. To fight inadvertent self-doxing, Microsoft previously published a security patch to help system administrators make it difficult for ordinary users to integrate Office365 and Docs.com. But users still persistently make their way and publish their secrets for all to see.
By lunchtime on March 28, Microsoft returned the search box back. Now she works there again. Immediately after this, the company gave a comment to the press: “Docs.com allows users to submit their documents and share them with the world. As part of our commitment to protecting users, we take steps to help those who inadvertently publish confidential information documents. Users can review and update their settings by logging into an account at www.docs.com . ”
Microsoft acknowledged that many of its users set incorrect settings for accessing confidential information. The company has closed access to those documents that the attackers will most obviously look for.
In general, such leaks of information can be prevented. If you are afraid that some sensitive information about you or your company will accidentally get on the Internet, you can create a Google Alert informer in advance, who will immediately send you a notification email that the specified keyword has been indexed and encountered in such a document. At the very least, you’ll be the first to know about a leak right away as soon as it’s available to Google and search queries. After receiving operational information, you can take some measures. For example, change passwords or fire someone.
Source: https://habr.com/ru/post/373307/
All Articles