Hacker hacked 150 thousand printers available on the web

The printout found in the printer tray may be a big surprise.
Computer security specialist with the nickname Stackoverflowin spoke about hacking more than 150 thousand printers that are available from the global network. In an interview with the publication Bleeping Computer, he said that the purpose of hacking is not to cause harm to anyone or to gain benefits, but to draw attention to the problem of information security. According to the hacker, now users, both ordinary and corporate, do not pay attention to protecting their printers, opening access to them from the outside without the use of firewalls or other network protection methods.
Stackoverflowin created a script that searches for available and open network printer ports, sending a print task to vulnerable printers. The script does not do any harm, just the user's printer starts printing a page with certain text, a warning about the need to close the port and protect its connection.
stackoverflowin the hacker god has returned, your printer is part of a flaming botnet, operating on putin's forehead utilising BTI's (break the internet) complex infrastructure.
[ASCII ART HERE]
For the love of God, please close this port, skid.
-------
Questions?
Twitter: https://twitter.com/lmaostack
-------The first version of the appeal to the owners of vulnerable printers contained an ASCII image of the robot and an e-mail cracker. If desired, the user could write to this address, having received information on how to protect themselves. The second version of the text also contains an ASCII image, with the image of a computer and a printer next to it. Above the picture is information about the need to protect the printer, which has become part of the botnet (in fact, there is no botnet).
')
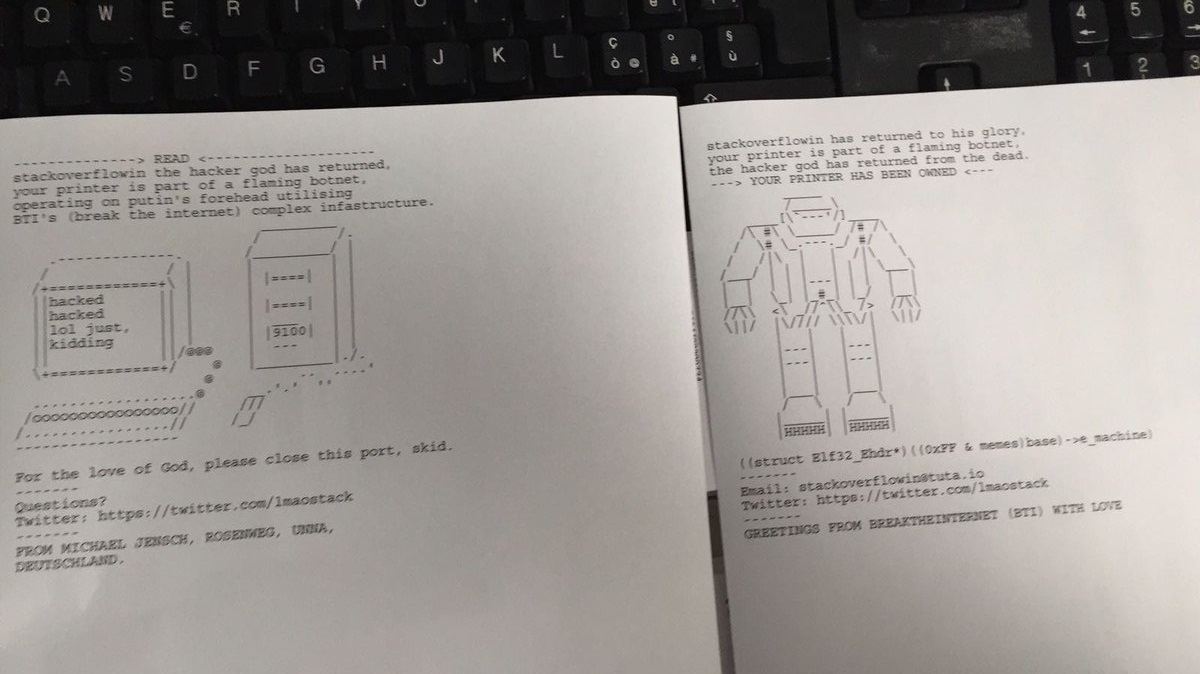
The first and second versions of messages sent by hacker Stackoverflowin to owners of hacked printers
Many models of printers from various manufacturers were subject to hacking. Among other companies about which printers it became known are Afico, Brother, Canon, Epson, HP, Lexmark, Konica Minolta, Oki, Samsung. The script looks for devices that open IPP ports (Internet Printing Protocol), LPD (Line Printer Daemon) plus port 9100.
Part of the script is an exploit where a remote code execution vulnerability is used. This exploit is designed for Dell Xeon line printers. “It allows me to do PostScript injections and get the printer to do the tasks,” says Stackoverflowin.
There is no doubt that the hacker script was effective. Online photos of printed pages are massively laid out by the owners of hacked printers. Here are some of these messages.
As you can see, not only ordinary printers are cracked, but also receipt printers.
Repetition of the material covered
In the script itself and its work there is nothing particularly difficult, as discussed, for example, at Habrahabr . That is why the search for printers available on the network with sending third-party tasks to the print queue is a very popular task for various hackers and the script kiddie .
Probably, cracking printers much more often than this becomes known. The media usually covers cases where printers are forced to print something unusual. For example, the massive hacking of printers, carried out last year by Andrew Oernheimer, became very famous. He timed his event to the birthday of Hitler and sent to print many leaflets with anti-Semitic text and protests against migrants.
Then it became known that at least 6 large universities had printers involved. First, the attacker collected the IP connected to the network devices from North America and Australia with an open port 9100. It was very easy to do this using the services of Shodan or masscan . After that a simple script of the following content was used:
#!/bin/bash for i in `cat printers` do cat payload.ps |netcat -q 0 $i 9100 done Plus the string “while true; do killall --older-than 1m netcat; sleep 1; done "in order to remove" hung "connections. The hacker also learned about the success of the whole event from social networks, in particular, Twitter.
To protect against this is quite simple. You should not assign public IP addresses unnecessarily to your printers; the company needs to check whether such addresses are assigned to printers. If assigned, but for work it is not necessary, it is better to correct the situation in advance. In addition, you can use one of the paid or free firewalls. HP has already published its own solution to the problem.
Source: https://habr.com/ru/post/373139/
All Articles