Authorizer: emcSSL decentralized authorization will work with oAuth 2.0
News about regular hacking databases and stealing passwords or hashes appear with frightening regularity, even from such giants as VC and Yahoo. But Facebook and Google users can not be sure of their security, because the essence of the problem is not in hacking as such, but in the centralized storage of user data, including passwords or password hashes, which can be successfully restored.
Last year, we already wrote about the world's first decentralized digital key management system based on the Emercoin blockchain: emcSSL . Its authentication architecture does not reveal the user's secret in the authentication process to the server and uses decentralized storage of accounts.

')
In theory, this is a great way to secure the credentials of users of any service, but in practice the implementation of emcSSL requires the participation of a qualified programmer and contains a number of inconveniences from the user's point of view. Therefore, our today's announcement can be considered a New Year's gift of HashCoins to the whole world: we have almost finished work on the Authorizer service, which allows you to connect emcSSL via oAuth 2.0 .
Unfortunately, emcSSL integration is not the easiest thing:
In order to simplify the life of webmasters, HashCoins decided to take on this problem by combining emcSSL with oAuth 2.0: now it’s enough just to insert the code of the conditional login button, the user clicks the button, goes to the Avtoiser website, or sees our pop-up window (from the user's point of view) will look the same as authorization via Facebook, for example) and comes back with an authorization token.
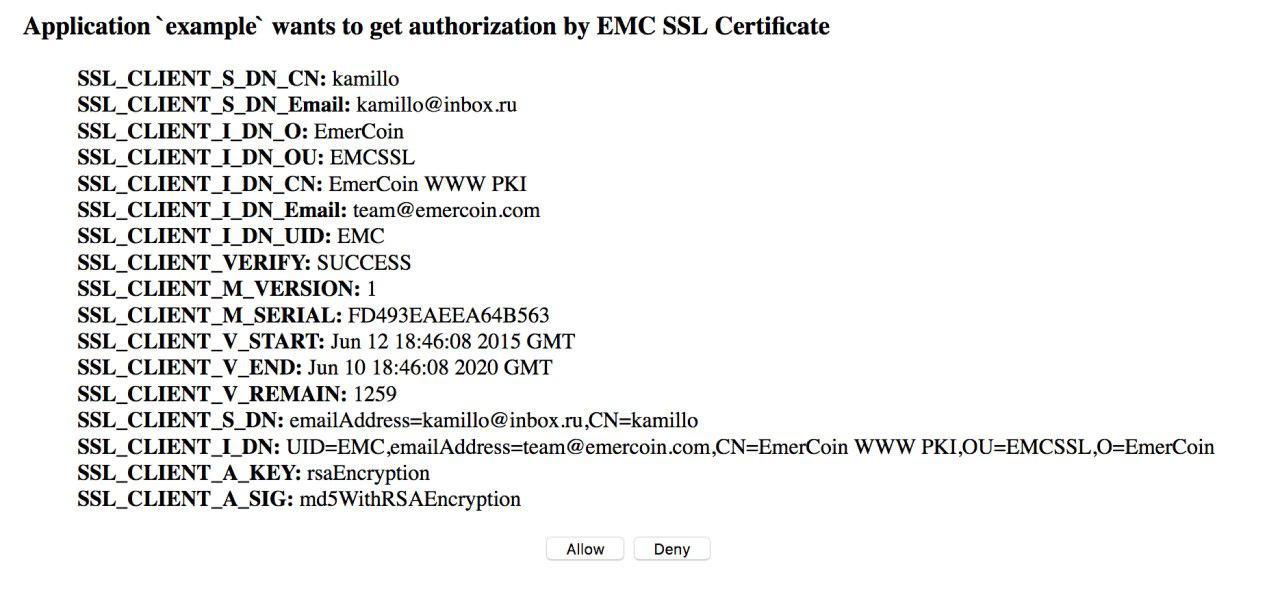
To configure, the webmaster must specify the data of our Autorzier oAuth Provider. This is set up in two orders of magnitude simpler than installing emcSSL and does not frighten visitors with certificate requirements. This functionality is already ready.
In addition to authorization per se, Authorizer can be used to transfer other user information — for example, a postal address, etc. The idea is the same: centralized storage of personal data on someone's servers is evil, because if they are compromised, personal, payment, medical and other information may be lost. When using emcSSL, this information is contained in a special info card stored in the Emercoin blockchain in an encrypted form, and various services get to it only temporary access during authorization and only with the user's permission. This can be useful, for example, online stores, concerned about the speeding up of the number of user actions that precede the purchase directly. When using authorization through Authorizer, the store receives data for delivery directly upon authorization of the user using emcSSL.
Thanks to emcSSL, the authorizer does just that with an info card. At the first authorization through the "Autorizer" we will ask the user to fill out the info card or take the data from the user Emercoin card, if the user is one. In the future, when entering a site, the Authorizer will ask the user if he wants to show his data, for example, to an online store.
In the case of a positive response, the "Autorizer" will transmit data from the info card - for example, the delivery address to the store. After making a purchase, the server “forgets” its contents - until the next user login. As a result, only the UserID can be stored in the account on the server, and nothing else. No password, no personal user data. And if there is nothing to take from the server, they will most likely not try to hack it.
After connecting emcSSL with oAuth2, the most difficult thing will not be the introduction of technology, but a change in user habits. Because the principle of the passwords, with all their shortcomings, even your grandmother understands. Password-free authorization, although as old as the web, remains new and incomprehensible to most users. We have simplified emcSSL integration, but for technology to become truly massive, you need to be understood by ordinary users. Therefore, here are a couple of words about how it works - a small educational program that you can share with less advanced acquaintances, so as not to tell everything from scratch.
All the user needs is his electronic key to all doors: a certificate. There are several ways to create it: either through the site “Autorizer” (we’ll give it to him after the official release), or at emcssl.org , or in the Emercoin web wallet , or in the most reliable way: self-generation using scripts . It sounds, of course, is not very usable from the point of view of the mass user, but we are working to expand and simplify the receipt of the certificate. However, in the first release of the "Autorizer" you will need to create it yourself.
Having created it, you can add it to all browsers and devices you use. When you create a certificate, you also create a password, which you will need to enter only one into each new browser - it is necessary for your protection in case of certificate theft.
Then everything is simple: when you go to the site with the support of Authorizer, you see a certificate authorization button and choose a certificate on your device and enjoy a secure connection.

Authorizer saves you from the risk of compromising your personal data when hacking the servers of the next services, but increases the requirements for you as a guarantor of your own network security: you have to take care of creating a certificate and prevent the password from being stored in clear text anywhere. So we can say that in its current form, Authorizer is suitable for services designed for an average and higher technical literacy audience - for those for whom a couple of extra gestures are fully justified by the increased level of protection. Say, this method of authorization as one of the alternatives would have been great for Habra, do not you think?
Release Authorizer is scheduled for the end of January. In the meantime, we are happy to hear your feedback, questions and suggestions on our technology.

Last year, we already wrote about the world's first decentralized digital key management system based on the Emercoin blockchain: emcSSL . Its authentication architecture does not reveal the user's secret in the authentication process to the server and uses decentralized storage of accounts.

')
In theory, this is a great way to secure the credentials of users of any service, but in practice the implementation of emcSSL requires the participation of a qualified programmer and contains a number of inconveniences from the user's point of view. Therefore, our today's announcement can be considered a New Year's gift of HashCoins to the whole world: we have almost finished work on the Authorizer service, which allows you to connect emcSSL via oAuth 2.0 .
How emcSSL works
There is no certificate authority in the emcSSL system, and the users themselves issue certificates. Accordingly, the certificate certificate is free by definition. The Blockchain EmerCoin acts only as a public trusted repository of SSL certificate hashes and ensures the uniqueness of Serial, which is a unique UserID.
Thus, in the emcSSL system, both problems were successfully solved - both non-disclosure of the secret (a) and decentralization (b), which allows the system to be scaled to the global level. The user of the emcSSL system receives a kind of “pass-all-terrain vehicle”, which does not depend on anyone except the user. Not from the “site on the Internet,” not from the certifier, or from anyone else. Accordingly, the system does not allow attacks of the type discussed above, which lead to a massive compromise of accounts, because private keys are generated by users and never leave their computers, and there simply is no such central place that can be compromised.
In particularly important cases, it is advisable to use emSSL with a password in the framework of two-factor authentication. In this case, emcSSL authorizes the device and provides a secure channel of communication with the server, and the password authorizes the operator.
It is also worth mentioning that the emcSSL blockchain architecture effectively and safely solves the problem of revoking a compromised certificate and its quick replacement, which compares favorably with CRL and OCSP protocol, which is vulnerable to the MItM attack.
In general, emcSSL is cool and safe, but without a convenient method of implementation, it is all but useless. It requires a wallet "Emercoin" on the server, it is impossible to use a CDN, because An enetrprise account is required to place the Emercoin certificate; thirdly, when authorizing via emcSSL, a certificate is required, which can frighten unprepared users.
Unfortunately, emcSSL integration is not the easiest thing:
In order to simplify the life of webmasters, HashCoins decided to take on this problem by combining emcSSL with oAuth 2.0: now it’s enough just to insert the code of the conditional login button, the user clicks the button, goes to the Avtoiser website, or sees our pop-up window (from the user's point of view) will look the same as authorization via Facebook, for example) and comes back with an authorization token.

To configure, the webmaster must specify the data of our Autorzier oAuth Provider. This is set up in two orders of magnitude simpler than installing emcSSL and does not frighten visitors with certificate requirements. This functionality is already ready.
Info cards
In addition to authorization per se, Authorizer can be used to transfer other user information — for example, a postal address, etc. The idea is the same: centralized storage of personal data on someone's servers is evil, because if they are compromised, personal, payment, medical and other information may be lost. When using emcSSL, this information is contained in a special info card stored in the Emercoin blockchain in an encrypted form, and various services get to it only temporary access during authorization and only with the user's permission. This can be useful, for example, online stores, concerned about the speeding up of the number of user actions that precede the purchase directly. When using authorization through Authorizer, the store receives data for delivery directly upon authorization of the user using emcSSL.
An ideal user accounting system on the server side should have information about it when this information is required (say, at the time of the purchase), and not contain it when an attacker trying to merge the information to the merge does.
Thanks to emcSSL, the authorizer does just that with an info card. At the first authorization through the "Autorizer" we will ask the user to fill out the info card or take the data from the user Emercoin card, if the user is one. In the future, when entering a site, the Authorizer will ask the user if he wants to show his data, for example, to an online store.
In the case of a positive response, the "Autorizer" will transmit data from the info card - for example, the delivery address to the store. After making a purchase, the server “forgets” its contents - until the next user login. As a result, only the UserID can be stored in the account on the server, and nothing else. No password, no personal user data. And if there is nothing to take from the server, they will most likely not try to hack it.
Getting used to passwordless authorization
After connecting emcSSL with oAuth2, the most difficult thing will not be the introduction of technology, but a change in user habits. Because the principle of the passwords, with all their shortcomings, even your grandmother understands. Password-free authorization, although as old as the web, remains new and incomprehensible to most users. We have simplified emcSSL integration, but for technology to become truly massive, you need to be understood by ordinary users. Therefore, here are a couple of words about how it works - a small educational program that you can share with less advanced acquaintances, so as not to tell everything from scratch.
All the user needs is his electronic key to all doors: a certificate. There are several ways to create it: either through the site “Autorizer” (we’ll give it to him after the official release), or at emcssl.org , or in the Emercoin web wallet , or in the most reliable way: self-generation using scripts . It sounds, of course, is not very usable from the point of view of the mass user, but we are working to expand and simplify the receipt of the certificate. However, in the first release of the "Autorizer" you will need to create it yourself.
Having created it, you can add it to all browsers and devices you use. When you create a certificate, you also create a password, which you will need to enter only one into each new browser - it is necessary for your protection in case of certificate theft.
Then everything is simple: when you go to the site with the support of Authorizer, you see a certificate authorization button and choose a certificate on your device and enjoy a secure connection.

Authorizer saves you from the risk of compromising your personal data when hacking the servers of the next services, but increases the requirements for you as a guarantor of your own network security: you have to take care of creating a certificate and prevent the password from being stored in clear text anywhere. So we can say that in its current form, Authorizer is suitable for services designed for an average and higher technical literacy audience - for those for whom a couple of extra gestures are fully justified by the increased level of protection. Say, this method of authorization as one of the alternatives would have been great for Habra, do not you think?
Release Authorizer is scheduled for the end of January. In the meantime, we are happy to hear your feedback, questions and suggestions on our technology.

Source: https://habr.com/ru/post/373025/
All Articles