Free PassPass Password Manager works on a clean function.
Storing unique passwords for all sites and applications is an art. It is impossible to remember a hundred long passwords with high entropy. Maybe there are a dozen highly developed autists in the world who are capable of it, no more. The rest of the people have to use technical tricks. The most common option is to write all the passwords into one file, which is protected by a master password. By this principle, most password managers work.
This method has many advantages, but there are two main disadvantages: 1) it is difficult to synchronize passwords between devices; 2) you must always have at your disposal the password file itself. That is, lost the password file - and goodbye.
The new open source password manager of LessPass is devoid of these shortcomings, because it works on a pure deterministic function . He has other drawbacks, of course. About this below. First, the merits.
')
Concept
The concept of LessPass is that one-time passwords are regenerated on the fly using a pure function that returns deterministic values each time a unique password is calculated.
The input of the function is four arguments:
- master password
- login on the site
- Website address
- password generation options
At any time on any computer, you can re-launch the function - and calculate your unique password for a specific site.
What it looks like.
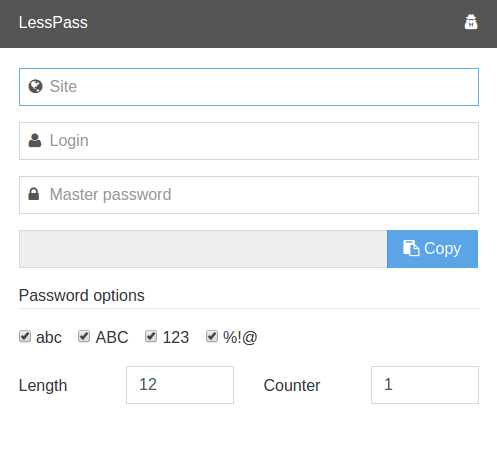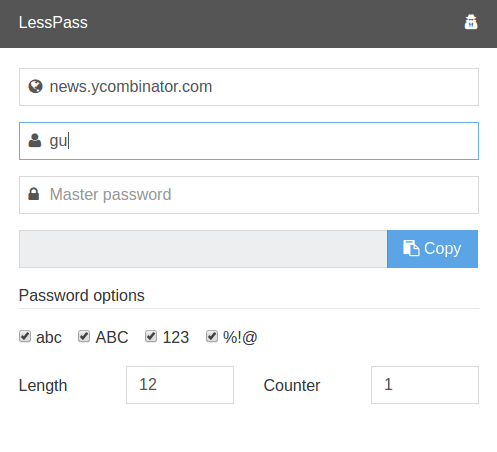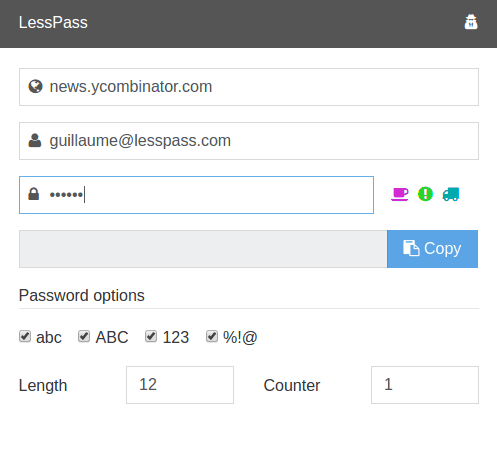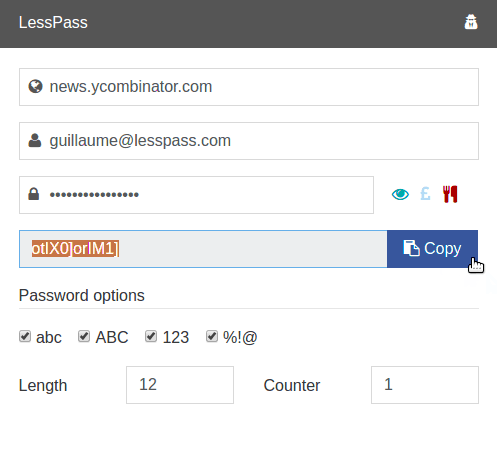
From this concept, the main advantage of this approach is immediately clear - you do n’t have a password file at all, as in other password managers. What is not - it is impossible to lose. Now, instead of extracting a unique password from the encrypted storage, we re-generate this password every time. Due to the determinism of the function and the immutability of the input parameters, the same unique passwords for all sites are always generated.
Program developer Guillaume Vincent (Guillaume Vincent) tried to implement security, as far as he understands it. What security is needed for deterministic function? First of all, so that by the result of its work it was impossible to determine all its arguments, especially since some of the arguments are already known to the attacker, just like the function itself.
Simply put, if the attacker knows two or three of the four arguments, as well as the result of the function, he does not need to know the fourth argument — the master password.
To protect the master password from bruteforce, the unique passwords calculation LessPass runs 8192 iterations of the PBKDF2 function with the SHA-256 hash function.

The hash generated by the first function is processed to match the pattern set by the third and fourth parameters (the set of characters used, the password length).
Now, in order to “remember” a unique password for a specific site, simply launch the LessPass program. This tiny program consists of only 109 lines .
Program code
import crypto from 'crypto'; module.exports = { encryptLogin: _encryptLogin, renderPassword: _renderPassword, createFingerprint: createFingerprint, _deriveEncryptedLogin, _getPasswordTemplate, _prettyPrint, _string2charCodes, _getCharType, _getPasswordChar, _createHmac }; function _encryptLogin(login, masterPassword, {iterations = 8192, keylen = 32}={}) { return new Promise((resolve, reject) => { if (!login || !masterPassword) { reject('login and master password parameters could not be empty'); } crypto.pbkdf2(masterPassword, login, iterations, keylen, 'sha256', (error, key) => { if (error) { reject('error in pbkdf2'); } else { resolve(key.toString('hex')); } }); }) } function _renderPassword(encryptedLogin, site, passwordOptions) { return _deriveEncryptedLogin(encryptedLogin, site, passwordOptions).then(function (derivedEncryptedLogin) { const template = passwordOptions.template || _getPasswordTemplate(passwordOptions); return _prettyPrint(derivedEncryptedLogin, template); }); } function _createHmac(encryptedLogin, salt) { return new Promise(resolve => { resolve(crypto.createHmac('sha256', encryptedLogin).update(salt).digest('hex')); }); } function _deriveEncryptedLogin(encryptedLogin, site, passwordOptions = {length: 12, counter: 1}) { const salt = site + passwordOptions.counter.toString(); return _createHmac(encryptedLogin, salt).then(derivedHash => { return derivedHash.substring(0, passwordOptions.length); }); } function _getPasswordTemplate(passwordTypes) { const templates = { lowercase: 'vc', uppercase: 'VC', numbers: 'n', symbols: 's', }; let template = ''; for (let templateKey in templates) { if (passwordTypes.hasOwnProperty(templateKey) && passwordTypes[templateKey]) { template += templates[templateKey] } } return template; } function _prettyPrint(hash, template) { let password = ''; _string2charCodes(hash).forEach((charCode, index) => { const charType = _getCharType(template, index); password += _getPasswordChar(charType, charCode); }); return password; } function _string2charCodes(text) { const charCodes = []; for (let i = 0; i < text.length; i++) { charCodes.push(text.charCodeAt(i)); } return charCodes; } function _getCharType(template, index) { return template[index % template.length]; } function _getPasswordChar(charType, index) { const passwordsChars = { V: 'AEIOUY', C: 'BCDFGHJKLMNPQRSTVWXZ', v: 'aeiouy', c: 'bcdfghjklmnpqrstvwxz', A: 'AEIOUYBCDFGHJKLMNPQRSTVWXZ', a: 'AEIOUYaeiouyBCDFGHJKLMNPQRSTVWXZbcdfghjklmnpqrstvwxz', n: '0123456789', s: '@&%?,=[]_:-+*$#!\'^~;()/.', x: 'AEIOUYaeiouyBCDFGHJKLMNPQRSTVWXZbcdfghjklmnpqrstvwxz0123456789@&%?,=[]_:-+*$#!\'^~;()/.' }; const passwordChar = passwordsChars[charType]; return passwordChar[index % passwordChar.length]; } function createFingerprint(str) { return new Promise(resolve => { resolve(crypto.createHmac('sha256', str).digest('hex')) }); } Password generation works as a script on the LessPass website , or on a client computer. Relevant extensions for Chrome and Firefox have been released . The generator script can be run in the local cloud. For example, using the local cloud Cozy .
Thus, when using such a password manager, it is impossible to lose the password file, because such a file does not exist. No problem entering a unique password from any device. It is only necessary to regenerate it.
The drawbacks of LessPass are obvious and stem from its merits. Most importantly, with the compromise of the master password, all tens or hundreds of derivatives of unique passwords for all sites can be considered lost at once.
The second drawback is that you cannot normally and conveniently change the password for a particular site. To do this, you have to change one of the password generation parameters ( Counter ). Subsequently, you have to remember which parameter was used for each site. Where one, where two, where three, and so on. In addition, you need to remember the unique password requirements of each site. For example, some banking applications may limit the password only to numbers and six digits in length. To solve this problem, LessPass implemented profiles for sites. The profile stores all the information needed to generate a password, except for the master password.
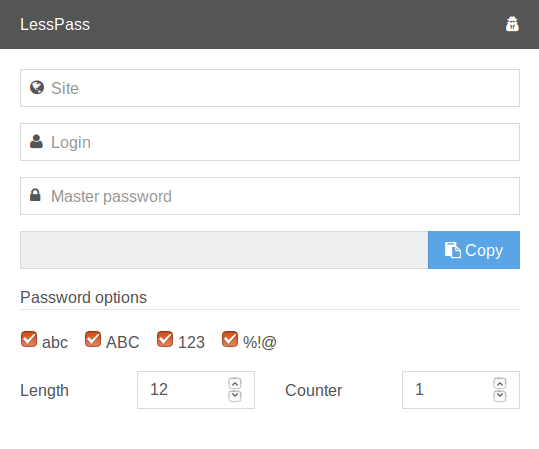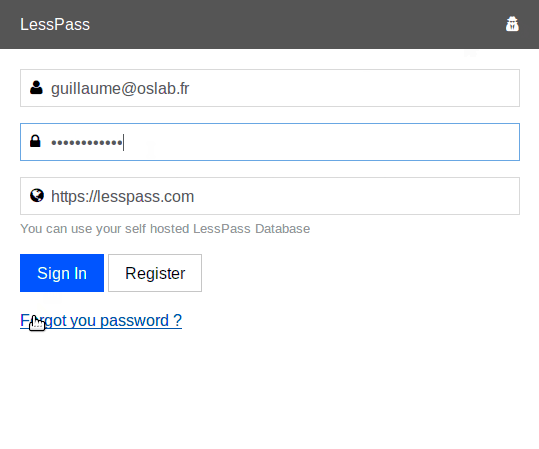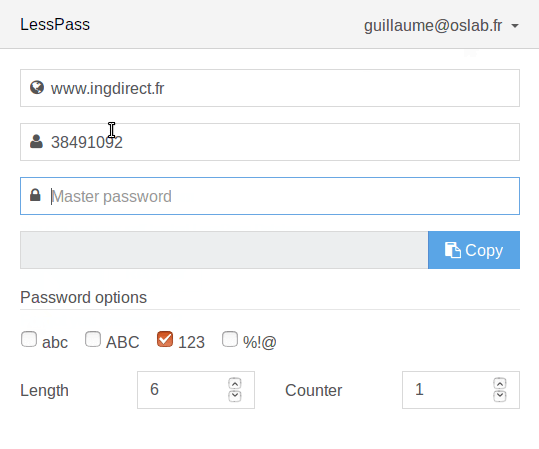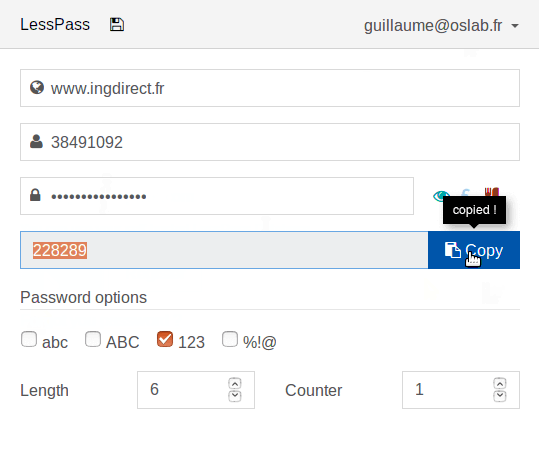
Profiles in LessPass
The third drawback is that the attacker does not need physical access to the user's computer to brute force the password. It does not need your file with encrypted passwords. Purely theoretically, it simplifies his actions. The user will not notice at all that he is attacking.
The situation is worsened by the fact that in this particular implementation, LessPass uses only 8192 iterations of PBKDF2-SHA256. According to experts , this is not enough for reliable protection against brute force on the GPU. A few years ago, at least 100,000 iterations were recommended, and the computing power of bruthos roughly doubles every year. So we will assume that the current implementation of LessPass is just a demo version, proof of the concept's performance.
LessPass is not the only deterministic password manager running on a clean function. There are other similar programs, including the Master Password App and Forgiva . All these programs have the same drawbacks mentioned above. In addition, they can not import their old passwords, so that when migrating to such a program, you will have to regenerate all passwords.
Despite all the shortcomings, the generator of deterministic passwords on a pure function is an interesting concept. Perhaps someone just such a password manager will seem the most convenient.
Source: https://habr.com/ru/post/372847/
All Articles