Third-party developers add “silly” features to the Mirai source code.

In October of this year, one Anna-senpai published the source code of the Mirai software, which allows you to turn unprotected IoT devices into a botnet. With the help of Mirai, malefactors organized large DDoS attacks, disabling the infrastructure of large sites with millions of visitors for several hours.
The problem of the vulnerability of the Internet of Things is more relevant than ever. Network-connected systems are becoming more and more (smart TVs, cameras, security systems, thermostats), but developers forget to update device software. As a result, the firmware contains vulnerabilities or weak passwords, sometimes set to "iron".
This and took advantage of the authors Mirai. With the help of the army of “zombie devices”, the attackers were able to organize a powerful DDoS attack on the site of information security specialist Brian Krebs. After this, a similar attack was carried out on the European hosting provider OVH. The total power of this attack was 1 Tb / s.
')
In all these cases, a botnet from webcams and DVRs infected with Mirai was used. The botnet that launched the attack consisted of more than 152,000 IoT devices. The management software constantly scans the entire range of IP addresses on the network to look for devices that can be compromised. As soon as the device is hacked, it sends a message to the central server, from which the DDoS attacks are carried out.
After the malicious code became available, it was used by both experienced and novice hackers, as well as information security specialists. Some users try to add new features and capabilities to the code. Employees of Arbor Networks, an information security company, found that some hackers "customize and improve the attack capabilities of the original botnet code," then using the modified software for their own purposes.
The modified copy of the Mirai software code now contains a backdoor that listens on port 103. As soon as a command arrives at this port, Mirai begins to execute it. According to experts, there is no such function in the original botnet code, it was added later.
Normally, when Mirai infects a device, the software disables the Telnet protocol, so that no one else can connect to the infected device.
The original malware infects those devices that use the Telnet protocol and standard access passwords ("0000", "password", and the like). New features recently added by third-party developers allow attackers who have launched Mirai on the network to retain control of the device, even when their main server is down. True, information security experts consider this a useless and even stupid function.
“This is a stupid opportunity,” says Darren Martyn, a hacker working for Xiphos Research. In his opinion, such a loophole can be used by other intruders who will take control of the infected device and use it for their own purposes. The same backdoor can also be used by information security specialists who wish to disconnect individual elements of a botnet from the network. “If the backdoor is open, it makes it easier to destroy it,” added Martin.

Marshal Webb, a spokesman for DDoS protection services for BackConnect , explains that thanks to the added feature of Mirai, this botnet becomes easier to track. This applies to both attacks carried out with the help of such a botnet, and individual infected devices. According to Webb, the actions of intruders to add such features to a botnet software are a terrible and wrong idea. This specialist believes that inexperienced hackers who have just started their activity are adding some features.
“Now all scripts from hacker forums have source code. You can see more of these junk code revisions, ”says Webb.
According to Arbor, after the source code of the malware got onto the Web, the devices infected with the botnet became more active. In addition, the number of infected systems is increasing. Last week, attacks using the Mirai botnet were carried out not only on the East Coast of the United States, as before, but also in some parts of Europe.
Unfortunately, so far no one knows exactly how to stop the Mirai offensive on the IoT device. This is not able to do either the FBI or hackers-beloshlyapniki.
Arbor experts advise using predictable methods of dealing with Mirai and DDoS attacks carried out with the help of this malware:
- Where possible, network operators should scan their networks to identify vulnerable and compromised IoT devices in their own infrastructure and networks of their customers or partners. When identifying such devices, it is necessary to take certain steps to isolate these devices, at the same time notifying their owners of the problem;
- Scanning should be directed to identify and classify the signs of TCP / 23 and TCP / 2323 activity of infected devices. When they are identified, it is necessary to take the necessary measures to isolate such devices, at the same time notifying their owners of the problem;
- Network operators should regularly upload telemetry data (NetFlow, IPFIX, s / Flow, cflowd / jflow, Netstream, etc.) to analyze this data using specific systems that can detect and classify DDoS attacks;
- If such an attack is detected, network operators should take steps to eliminate it.
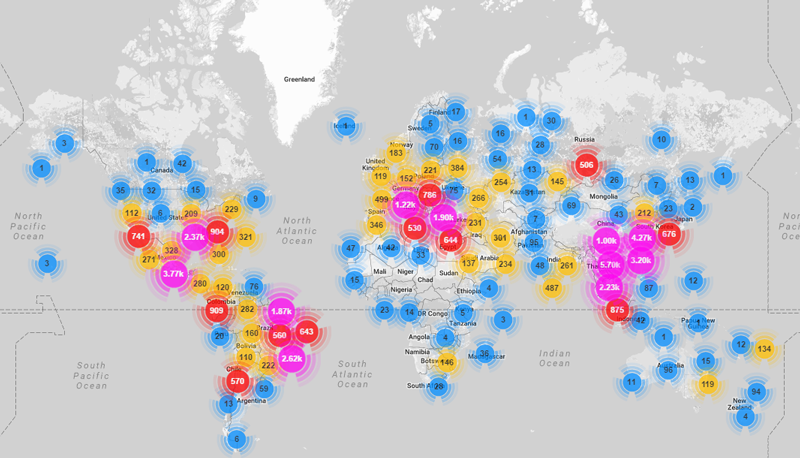
Location of compromised devices that participated in Dyn DDoS attack ( Incapsula data)
Despite its relative simplicity, Mirai is a threat. Infobase specialists are making efforts to eliminate the botnet formed by Mirai. But they do it poorly. This month, for example, a significant portion of the Internet has been intermittent . Millions of users experienced problems accessing Twitter, Amazon, Tumblr, Reddit, Spotify, Netflix, and other services.
Source: https://habr.com/ru/post/372817/
All Articles