Hackers broke into a moving Tesla Model S from 20 kilometers

Developers from Keen Security Lab, a division of Chinese Internet giant Tencent, have demonstrated exploitation of a vulnerability in Tesla Model S software. A team of experts after detecting a vulnerability reported it to Tesla. In the public access, information about the problem was posted after it was fixed by the manufacturer.
Vulnerability compromises CAN bus, which controls most electric vehicle systems. To exploit this vulnerability, it is necessary that the machine be connected to a WiFi access point configured by attackers. All this works through the browser of the automobile PC. The team that discovered the vulnerability says that a number of conditions must be met to intercept control over the car.
A confluence of circumstances that can lead to this is unlikely, but a potential danger does exist. If the attacker takes control of the car, he can cause significant damage.
')
Demonstration of exploitation of vulnerability Keen Security Lab was filmed and uploaded to the network. It shows how researchers, using the capabilities of an electric vehicle, found the nearest charging station. And here the authors of the work managed to take control over a number of functions of the Tesla Model S, as well as remotely lock the doors. They were able to remotely open the trunk, turn the side mirror, and also activate the braking during the movement of the electric vehicle. We managed to manage almost all the functions of the Tesla Model S.
Within ten days after receiving information about the problem, the company fixed the vulnerability by releasing update v7.1, 2.36.31. Tesla also published an official statement, stating the following: “The vulnerability can only be triggered if the driver works with the browser. Also, the electric vehicle must be connected to a wireless access point configured by hackers. We believe that the risk in this case is very low, but it was still necessary to solve the problem. We work with information security experts to find and eliminate security vulnerabilities in our products on time before they can become a problem. We also plan to pay a reward to the team according to our bug bounty program. ”
In 2014, Chinese experts from Qihoo already reported that they managed to hack the Tesla Model S.
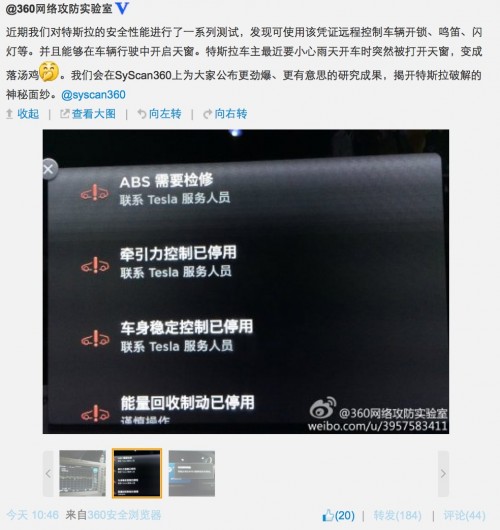
And in this case, the control over the car managed to intercept while driving. As a result of the exploitation of the remaining unknown vulnerability, the Chinese were able to gain remote access to the on-board electronics of the electric vehicle. Among other systems, managed to manage the lock cars, headlights and sound signals. Also, hackers were able to open and close the Tesla Model S hatch during the movement.
Tesla Model S is one of the most popular electric vehicles from Tesla Motors. This is a five-door car, the prototype of which was first presented at the Frankfurt Motor Show in 2009. The first deliveries to customers began in June 2012.
A lithium-ion battery with a capacity of 85 kWh provides a range of 420 km. The base model uses liquid cooling of an AC motor. Its capacity is 362 horsepower.
This year, the electric car received an updated design that makes the Tesla Model S look like the new Tesla Model 3 model. Three versions are now available: 70D, 90D, P90D, P100D.
Vulnerabilities in modern car software are not uncommon. Some companies quickly fix the problem after it becomes known. Example - Tesla, a company that eliminated a potential vulnerability in its software in just 10 days. Other companies take longer to solve a problem. For example, Chrysler solved the issue with the vulnerability of the software platform Uconnect more than nine months.

Moreover, the problem with Chrysler was much more dangerous than the problem with the Tesla Model S. Information security specialists, who discovered the vulnerability, said that it was enough for an attacker to know the IP of the car in order to do whatever he wanted with it.
Experts conducted a demonstration of exploitation of a vulnerability for one of the editors of Wired. He was driving the Jeep Grand Cherokee while hackers connected to the Uconnect system. This software platform allows the car owner to remotely control his car. For management, you only need a smartphone or tablet with a specialized application installed. It allows you to start the engine, track the location of the car, monitor the microclimate in the cabin or perform other actions.
Charlie Miller and Chris Valasek were able to take control of the climate control, windshield wipers and the music system. After that, experts were able to reduce the speed of the Jeep Grand Cherokee, and also demonstrated the ability to lock the steering and brakes. At the very end of the test, the journalist was sent to a ditch along with the car.
As it turned out, the vulnerability is relevant for 471,000 vehicles of the company. Others that are vulnerable include the 2013-2014 Dodge Ram, Dodge Viper, Dodge Durango and Jeep. Plus, the company released the correction, but now the car owners themselves had to install it (and only to those who found out about the problem in some way or another). A new firmware was required to download from the network, save to a USB flash drive and install software into the car computer system from it. As far as can be judged, if the car owner did not install the new firmware version independently, then the vulnerability remained relevant.
Source: https://habr.com/ru/post/372687/
All Articles