IPhone 5c password brute force demonstration with flash memory mirroring
In April 2016, the FBI and Apple staged a real show around the iPhone 5c shooter from San Bernardino, for which they allegedly could not find the password without the help of Apple.
The FBI pressured Apple, demanding technical assistance. Tim Cook published an open letter in which he accused the FBI of forcing Apple to build a backdoor in iOS. It came to the US Congress and the Senate, the problem was discussed by all major American media and television channels. The world with a sinking heart watched Santa Barbara and wondered if Apple would give the feds or not give access to the iPhone's cryptosystem.
')
iPhone is protected from brute-force through the option of deleting data on the device after ten incorrect input attempts and an increasing delay time between sets of unlock code (5 seconds after 5 attempts, then 1 minute, 5 minutes, 15 minutes and 60 minutes).
It is logical to get around the defense by copying the flash memory with brute-force copies (NAND mirroring), but for some reason, the FBI experts could not conduct such an attack . They turned to the NSA - they also could not help .
After lengthy unsuccessful attempts to pressure the Apple, the FBI paid more than $ 1 million to hackers (supposedly from Israel), who proposed the iPhone 5c password brute force method. Sources said at the time that the smartphone had been hacked using a previously unknown (0day) vulnerability in iOS 9. Despite Apple’s request, the FBI has not yet released information about the vulnerability so that Apple can fix it - such a fbrovski revenge.
The director of the FBI said that copying NAND did not apply because it does not work .
Now one simple hacker did what the FBI and NSA specialists could not do. Sergey Skorobogatov from the University of Cambridge (United Kingdom) vividly showed how the iPhone 5C password brute force is implemented after copying the flash memory. The scientific work on cryptography is published in the public domain on the site arXiv.org.
According to the iOS encryption scheme , a user password and a unique UID key are used to generate a key to the System Keybag system storage. The UID key is hardware-registered in the SoC and is not available at the software level, so it is impossible to conduct brute-force without access to a specific chip.
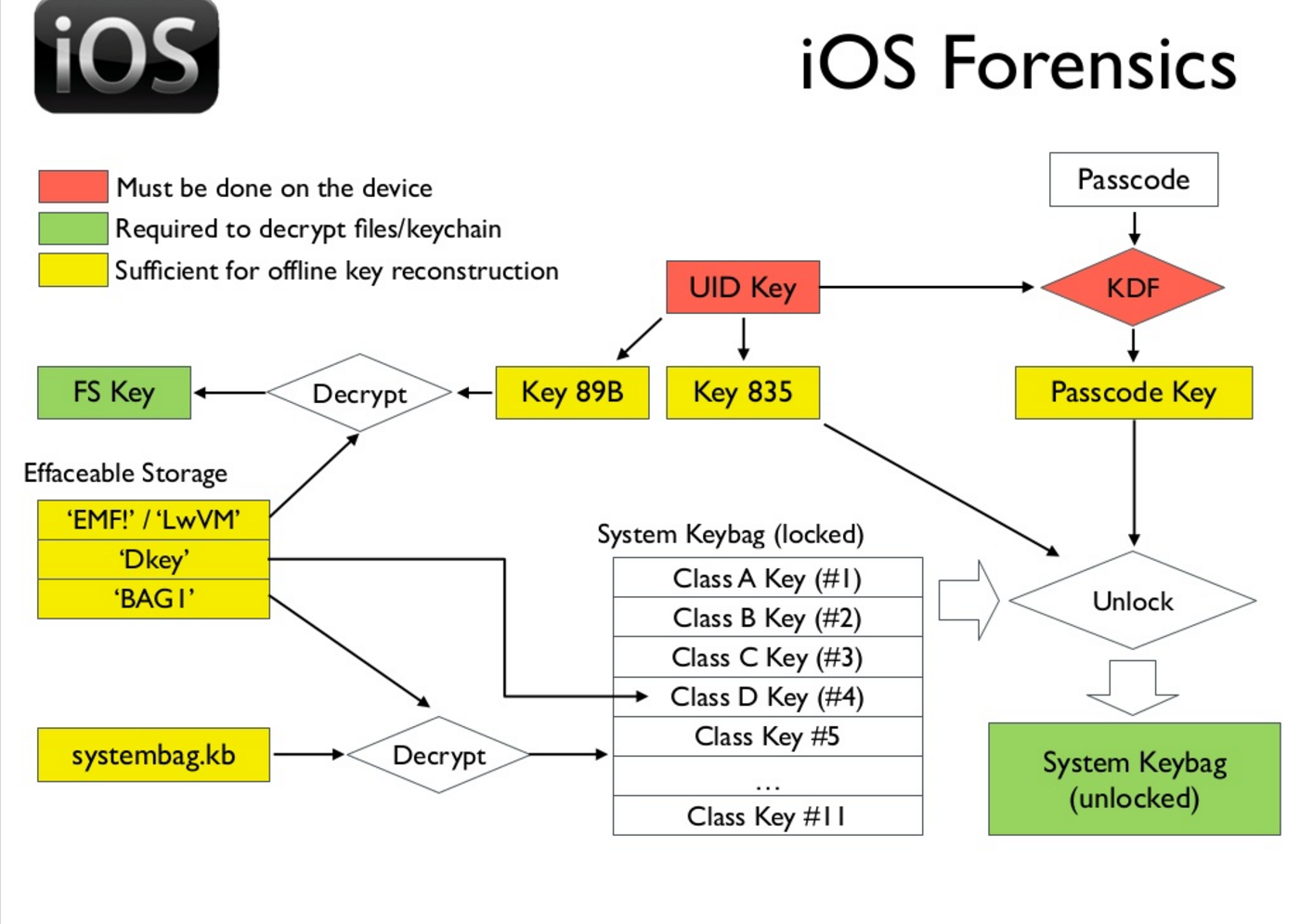
Although the architecture of the iPhone 5c is kept secret, on the forums you can find schemes and names of the chips iPhone 5c, iPhone 6 , etc., with a NAND pin. But Sergey Skorobogatov warns that some VCCQ and GND contacts have been swapped, so that the pinout can permanently damage the microcircuit. To study the protocols and commands you will need an oscilloscope and a logic analyzer.
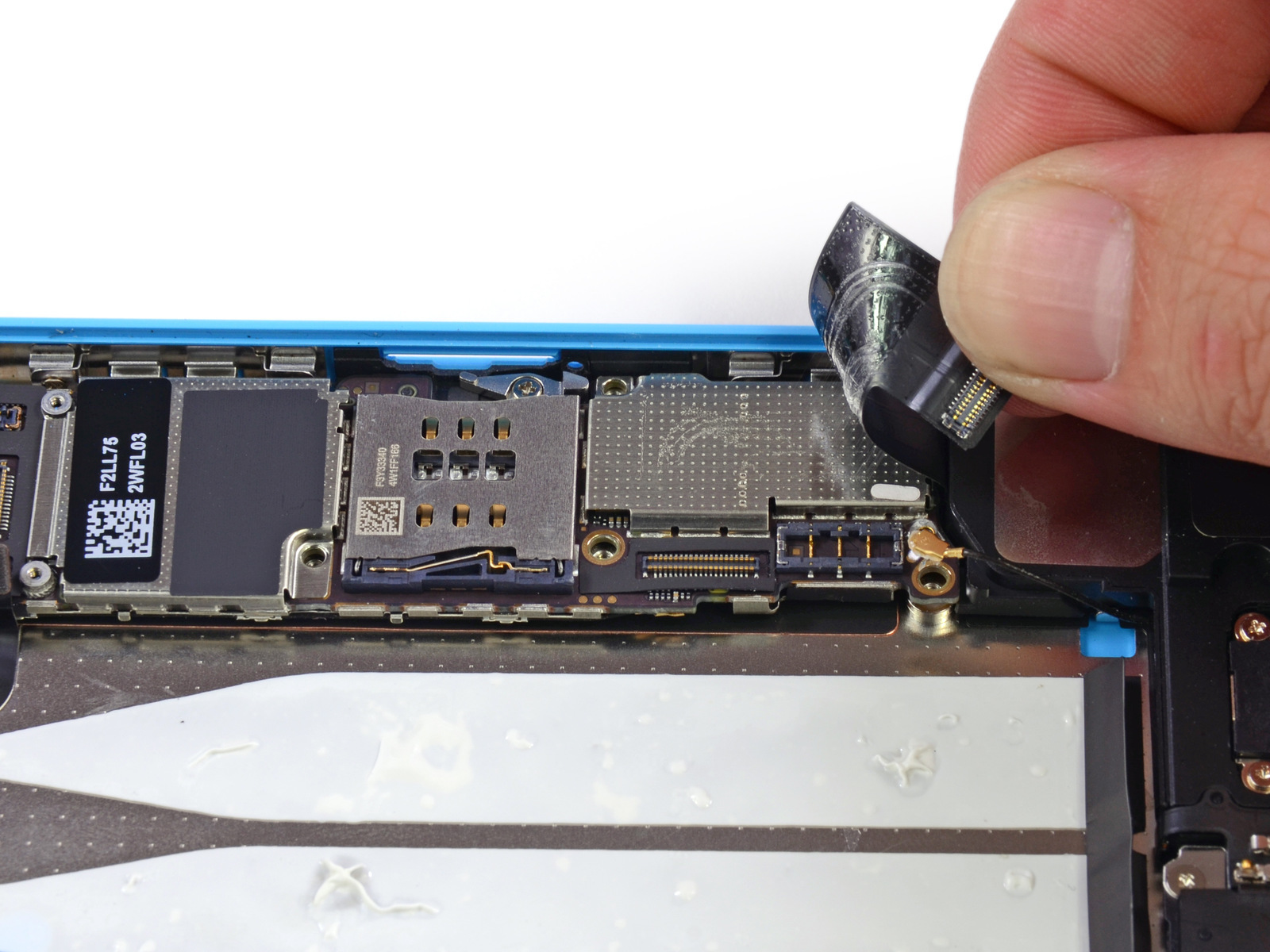
In the demo video, Sergey shows how to disassemble the iPhone, remove the chip with a flash memory chip, solder it with a blow dryer and clone the data. For similar instructions on parsing the iPhone 5C, see iFixit .
SoC A6 and NAND chip are located on different sides of the motherboard. The distance between NAND and the board is approximately 0.05 mm. Extraction will require a special thin knife and blowtorch with a temperature of more than 300 ° C.
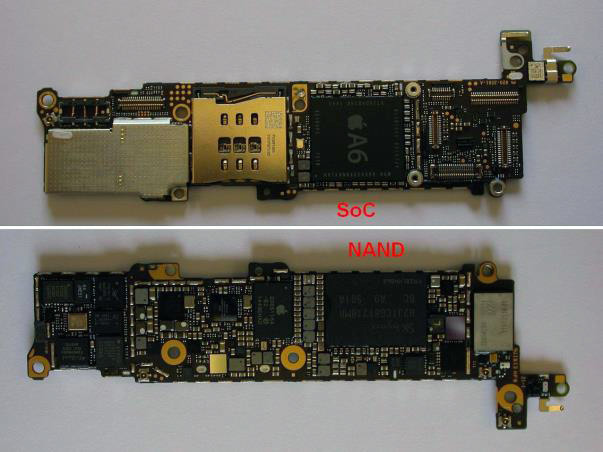
All small components around the chip were pre-protected with a temperature-resistant epoxy resin.

NAND extraction preparation
High temperature does not damage data in flash memory. Previous studies have shown that it can withstand up to 400 ° C.
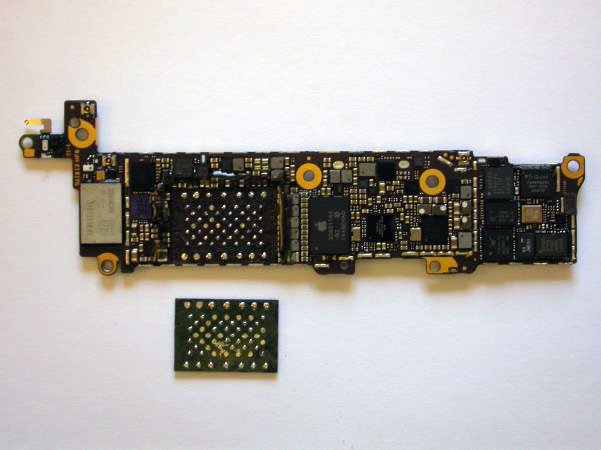
Extracted NAND Module
To test the functionality, each contact of the NAND module is connected to the motherboard with 0.3 mm wires with Teflon insulation (MGTF).
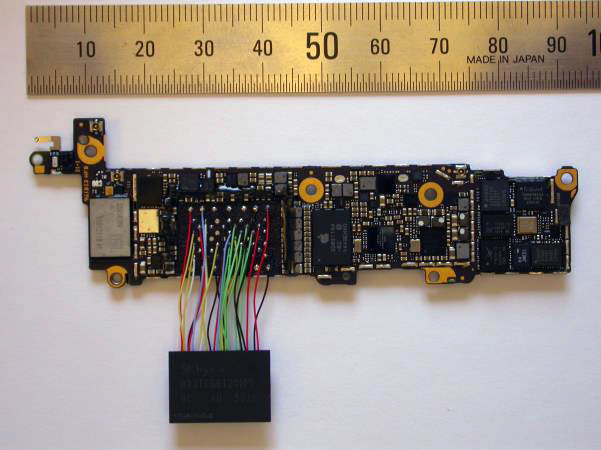
Then the motherboard was inserted into place, and a hole was cut out for wires with the NAND module removed.


At first, the phone was very buggy. Sergei found out that this is due to interference in long wires.
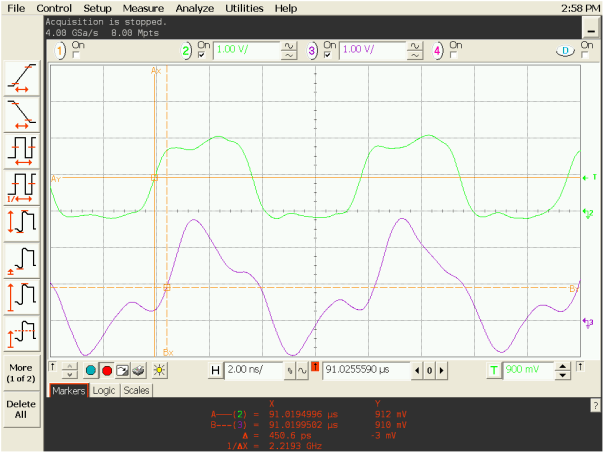
Noise signal
I had to add matching resistors to all signal wires. Then the signal leveled off and the phone stopped to fail.
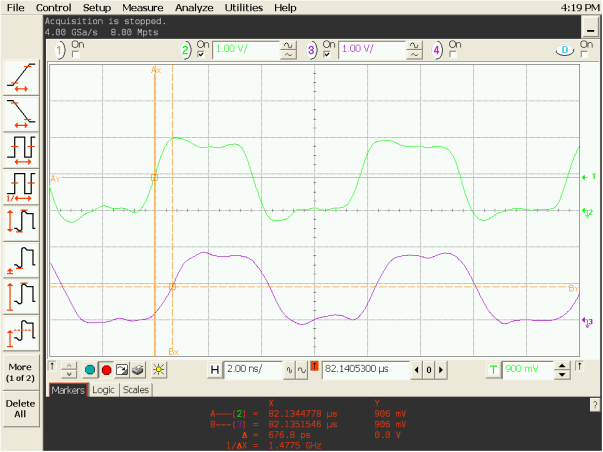
Signal without interference
Then an engineer from the University of Cambridge inserted an intermediate board for wiretapping the signal, connected an oscilloscope and a logic analyzer for reverse engineering of the protocol and commands of the iPhone 5c.
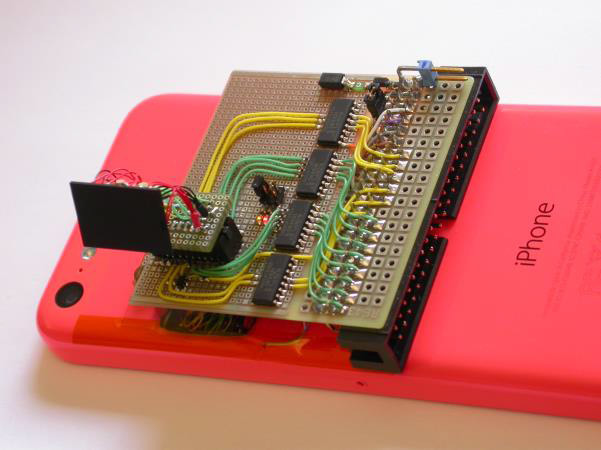
Intermediate fee for wiretapping
Here again, there were problems with the integrity of the signal, this time due to the input and output capacitances of the 74LVC and 74AVC buffer elements of 4 pF and 6 pF. I had to replace them with elements with a smaller capacity 74AUP and 74AXP.
In the end, the researcher still managed to prepare the iPhone 5c for reverse engineering. By this time he, obviously, had already gone further than the FBI and NSA specialists managed to do.

iPhone 5c with logic analyzer
Further was a matter of technique. It turned out that the iPhone 5c uses different interfaces and commands at different stages of loading, including undocumented proprietary commands at a clock frequency of 50 MHz. In the end, the logic analyzer wrote down all the commands and helped determine the specific proprietary protocol that is used to communicate with NAND.
Sergei Skorobogatov learned how to read, erase and write NAND memory at will. This is all that is needed for a successful brute force password.
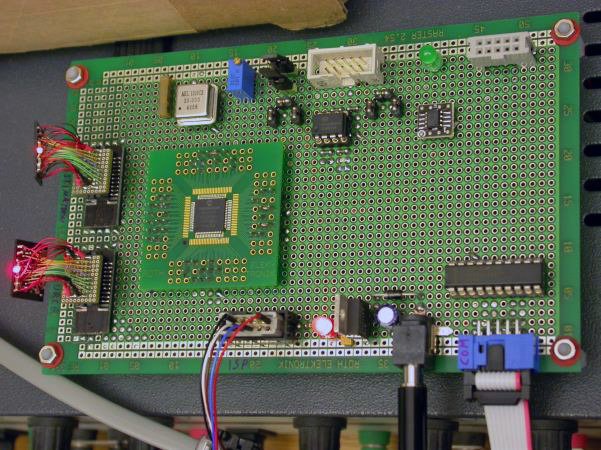
NAND Copy Test Bench
The bruteforce program tries six password options until a 1 minute delay appears, then the process of restoring the memory from the backup copy automatically starts (to reset the counter that protects against bruteforce), then the bruteforce continues. The recovery cycle after 6 attempts takes 90 seconds. Thus, complete enumeration of all four-digit pincode options will take about 40 hours.
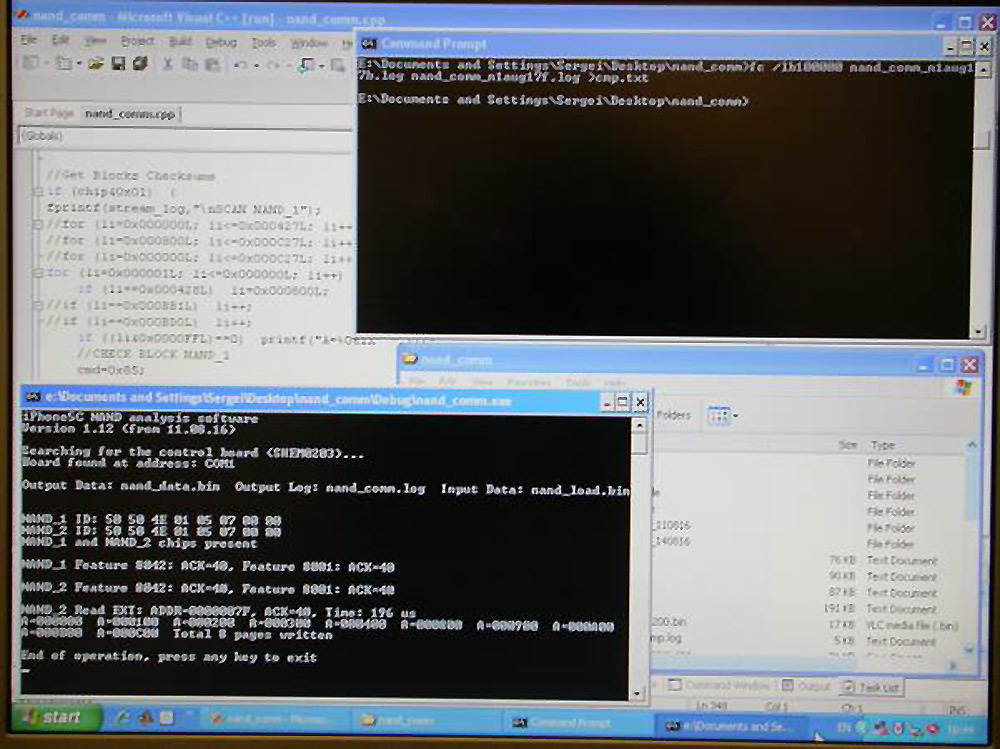
NAND Mirroring Software for iPhone 5c
This bruteforce method does not work in newer iPhones, which has the optional Secure Enclave protection. But it can be assumed that Sergey Skorobogatov’s colleagues from Elcomsoft and other companies that specialize in hacking smartphones, including those ordered by special services, are already solving this problem.
Source: https://habr.com/ru/post/372679/
All Articles