Do not call me by name: cryptographer is distributed in the e-mail with the exact data of the recipient
The degree of confidence in such messages and attachments to them is much higher than to normal malicious spam.
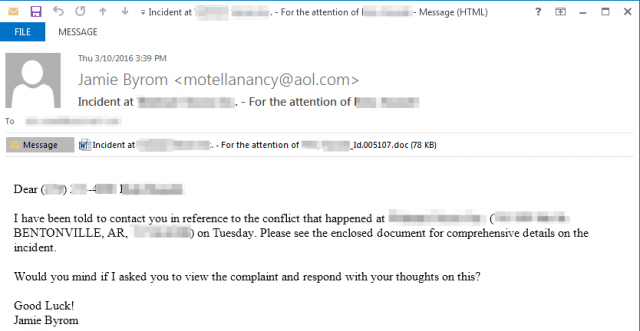
Phishing has existed for many years, it is one of the most popular methods that attackers use to obtain any data from web users. There is an interesting type of technology - spear phishing. Attacks of this kind are limited in scale, because usually user data that can be used for targeted phishing is not so easy to get (if we are talking about top managers, high-ranking officials, etc.). For many years, targeted phishing was used only if the game was worth the candle - that is, the benefit from obtaining certain information was higher than the labor and financial costs of attackers in obtaining personal data from users. But now the situation has changed.
')
From the beginning of the year, various users from many organizations in different countries began to receive letters with malware-attachments, where the address, subject, address - everything was targeted. A person sees his name in the title (not the nickname of the mailing address, but the real name), telephone number, position. In most cases, such messages are more trustworthy than the usual “Dear friend, see the attachment - there are my photos on the beach”. Now it is in such personified letters that the TA530 cryptographer began to spread. Its creators clearly count on attacks by bank employees, engineers of various stripes, and users of other categories for whom personal data is sometimes more important than any money.
The company Proofpoint, which specializes in information security, tried to understand the features of the cryptographer. Part of the information the company has published in its blog .
The post says, in particular, that TA530 customizes an e-mail for each particular victim, indicating the name, position, phone number and company name in the message body, subject and application names. In some cases, the company was able to verify the specified data, and they turned out to be true for each of the verified victims. So far, the source of the data is not entirely clear, but, as experts point out, all of this data is available on regular websites, on social networks - the same Linkedin or company’s website.
So far, the campaign to distribute TA530 has not become as large-scale as in the case of Dridex and Locky. But tens of thousands of users from various organizations in the USA, Great Britain and Australia have already received an e-mail with this cryptographer. In scale, this campaign targeted phishing is much more unparalleled.
The attackers behind the attack are working in a number of areas, including financial services, retail, manufacturing, healthcare, and so on.

Letters are not sent to all employees of the company, but mainly to management, middle managers and top managers. There is a logic to this - after all, when opening an application with a cryptographer by a top manager, the money is most likely to be sent to attackers - the cost of encrypted information is usually much higher than what cybervoors require. Access to databases, sales archives, bank accounts - all this can cost tens of millions of US dollars.
Experts Proofpoint argue that malicious software discovered by them, improved. The “quality” of personalized messages is also improving; they are gaining more and more trust among the recipients. Yes, if such a letter is received by an IT worker, he will most likely understand what the catch is. But, as we see, the specialization of ransomware in this case is not at all information security specialists.

Phishing has existed for many years, it is one of the most popular methods that attackers use to obtain any data from web users. There is an interesting type of technology - spear phishing. Attacks of this kind are limited in scale, because usually user data that can be used for targeted phishing is not so easy to get (if we are talking about top managers, high-ranking officials, etc.). For many years, targeted phishing was used only if the game was worth the candle - that is, the benefit from obtaining certain information was higher than the labor and financial costs of attackers in obtaining personal data from users. But now the situation has changed.
')
From the beginning of the year, various users from many organizations in different countries began to receive letters with malware-attachments, where the address, subject, address - everything was targeted. A person sees his name in the title (not the nickname of the mailing address, but the real name), telephone number, position. In most cases, such messages are more trustworthy than the usual “Dear friend, see the attachment - there are my photos on the beach”. Now it is in such personified letters that the TA530 cryptographer began to spread. Its creators clearly count on attacks by bank employees, engineers of various stripes, and users of other categories for whom personal data is sometimes more important than any money.
The company Proofpoint, which specializes in information security, tried to understand the features of the cryptographer. Part of the information the company has published in its blog .
The post says, in particular, that TA530 customizes an e-mail for each particular victim, indicating the name, position, phone number and company name in the message body, subject and application names. In some cases, the company was able to verify the specified data, and they turned out to be true for each of the verified victims. So far, the source of the data is not entirely clear, but, as experts point out, all of this data is available on regular websites, on social networks - the same Linkedin or company’s website.
So far, the campaign to distribute TA530 has not become as large-scale as in the case of Dridex and Locky. But tens of thousands of users from various organizations in the USA, Great Britain and Australia have already received an e-mail with this cryptographer. In scale, this campaign targeted phishing is much more unparalleled.
The attackers behind the attack are working in a number of areas, including financial services, retail, manufacturing, healthcare, and so on.

Letters are not sent to all employees of the company, but mainly to management, middle managers and top managers. There is a logic to this - after all, when opening an application with a cryptographer by a top manager, the money is most likely to be sent to attackers - the cost of encrypted information is usually much higher than what cybervoors require. Access to databases, sales archives, bank accounts - all this can cost tens of millions of US dollars.
Experts Proofpoint argue that malicious software discovered by them, improved. The “quality” of personalized messages is also improving; they are gaining more and more trust among the recipients. Yes, if such a letter is received by an IT worker, he will most likely understand what the catch is. But, as we see, the specialization of ransomware in this case is not at all information security specialists.
Source: https://habr.com/ru/post/372059/
All Articles