Apple does not want to help crack the iPhone. Why is it important?
 Not the biggest decision of Apple was the impetus for the start of a new round of discussions on issues of encryption and privacy. The company refused to unlock the encrypted smartphone, which appeared in the case of the attacks in San Bernandino. The manufacturer explains that he does not feel sympathy for terrorists. Nevertheless, Apple refused to give the secret services a backdoor.
Not the biggest decision of Apple was the impetus for the start of a new round of discussions on issues of encryption and privacy. The company refused to unlock the encrypted smartphone, which appeared in the case of the attacks in San Bernandino. The manufacturer explains that he does not feel sympathy for terrorists. Nevertheless, Apple refused to give the secret services a backdoor.Such a case sparked a debate about what is more important: helping special services in one of the investigations into the brutal murder of people or ensuring information security. The conflict has been brewing for a long time, since the moment when encryption was enabled by default in the iPhone.
The course of events
The problems did not begin after the start of an investigation or the publication of an open letter from Apple CEO Tim Cook, but after the release of iOS 8 in 2014. It is in the eighth version that encryption was enabled by default. Then the security services were really worried.
How to encrypt data in the device's memory? For this, a cryptographic key is needed, most often 128 or 256-bit. It would be inconvenient to memorize and introduce like every time you turn it on. Therefore, Apple went a little different way. All the latest iPhones have built-in hardware cryptography and security measures. The Secure Enclave (SE) component is embedded in each of the A7 chips and later A-models. In essence, SE is a separate computer inside the system on a chip. It does not depend on ordinary ARM-cores. It communicates with the main processor SE using a message queue and shared memory buffers.
')
Secure Enclave uses a user-defined password, UID and other keys to encrypt data in the flash memory of the smartphone. The resulting system is designed to provide both acceptable safety and high speed. By the way, the recently popped up error 53 is connected with the peculiarities of the SE operation. This is a message that the system gives in an attempt to unauthorized replacement of the fingerprint sensor: SE rejects an unfamiliar device so that attackers cannot brute-force access.
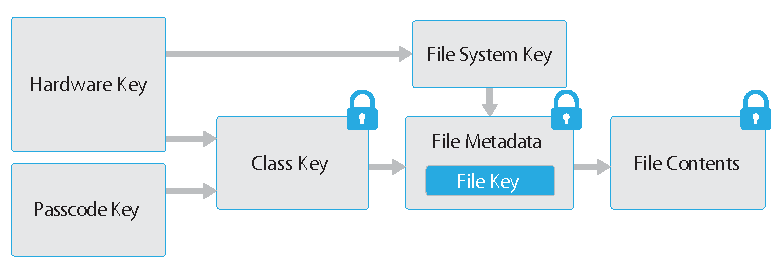
A fragment of an Apple document on iOS security .
The user enters a password that unlocks the phone. This can be either a tiny 4-D or 6-digit string by information security standards, or a combination of characters of arbitrary length. Setting a password also means that it will be used to encrypt data on the phone. The 256-bit key for AES encryption is obtained from a user-defined password and a unique key accessible only to Secure Enclave. This means that even if the chips are soldered, data cannot be obtained from the memory. To decrypt data, you need a password and a key that is securely hidden deep in the chip. The attack must be carried out only on the target device.
SE prevents attempts to quickly sort passwords. Delays increase with errors. For example, after the fifth attempt will be given a delay per minute, after the ninth - an hour. According to Apple, it will take 5.5 years to bust a 6-character password from numbers and letters. Also, to ensure enhanced security, you can enable data wiping in the settings after 10 unsuccessful password attempts.
The password delay policy is controlled by Secure Enclave. It does not help even hacking the operating system. The SE firmware itself can be updated, but you need the appropriate keys for this, according to the computer security company Trail of Bits. That is, you will need to roll a special firmware on the SE, which will remove any restrictions on the number of attempts and their frequency. You will also need to install a hacked version of iOS, which also will not interfere with brute force. Opinions differ: someone thought that even Apple could not update the Secure Enclave firmware without entering a password. But former Apple security expert John Kelly claims that the SE firmware update does not require entering a password, does not delete cryptographic keys or user data.
But the case is the iPhone 5C under iOS 9, in which the system is installed on the A6 chip. It can also include data destruction after 10 attempts. The phone does not have a hardware secure Enclave. In this model, many security features are provided at the operating system level. Therefore, for hacking may need only a special update OSes. After that, the only limitation will be the frequency of receiving the encryption key - every 80 milliseconds. However, all this is the opinion of experts.
The bottom line is not about encryption or technical ability to crack it. Encryption enabled by default in iOS appeared in the eighth version in the fall of 2014. Even then, the American special services began to show concern and discontent with new security measures. The FBI didn’t like that it would be impossible to access data. And access is needed to pursue criminals and prevent terrorism, the special service claims. FBI Director James Koumi proposed to introduce a “transparent, understandable procedure”, which he called the front door. He also spoke out against backdoors. Computer security experts have called such a substitution of concepts. Later, the FBI made a proposal to legally oblige manufacturers to leave loopholes.
The hidden confrontation turned into a conflict after the San Bernandino massacre case. During the investigation, it was necessary to gain access to the data on the service iPhone 5C of one of the defendants in the case. Apple in court ordered to create a tool for the selection of a user password. On February 16, Tim Cook published an open letter in which he called the likes of a backdoor.
Why does Apple need to help the FBI and reveal data on the device?
The point is the seriousness of what is happening: there was a terrorist attack in which 16 people were killed, 24 were injured. This is one of the most brutal terrorist attacks in the United States after the attacks of September 11. The investigation should shed light on the possible connection of the two terrorists with the ISIL organization banned in Russia. For this, the court requires you to unlock one and only one smartphone. There can be a lot in memory: these are both two-factor authentication applications, instant messengers with encryption such as Signal or Telegram, and other files that are not downloaded in iCloud backups. The FBI does not explain what it can be. But it is said that there are reasons to predict the availability of such data. The backups history of the late owner of the smartphone is irregular, and the FBI’s data in it will not be enough .

Apple is asked to deactivate possibly enabled auto-delete data after 10 attempts, remove restrictions on the frequency of attempts and add the ability to enter a password not on the screen, but electronically. As they say in the FBI, they are only asking for a chance to guess the password on a particular terrorist’s smartphone, and not about weakening the protection in general. Court decisions in plain text say that the creation of a special firmware is regarded as a possible solution. But it also mentions that the image of this firmware should work only on the target iPhone. It is unlikely that the created tool can be adapted to work on smartphones with Secure Enclave, that is, with A7 chips and newer.
Alternative ways to solve the problem is perhaps that smile. Of course, the corpses are not protected by the fourth amendment . But to open the smartphone with the fingerprint of the dead owner will not work - there is no TouchID sensor in iPhone 5C.
Why does Apple need to think about users?
The case in the precedent of what is happening. If you satisfy this request, it will be difficult to refuse in the future. This case differs from the previous requests of the special services by the depth of the work to be done and the danger of the tools provided. Apple has never cracked iPhone data in the past. Today it is one smartphone of a terrorist, and tomorrow a new round of surveillance programs. Such programs have already been - this is PRISM , which became known only thanks to the leaks of Edward Snowden. The project recorded telephone conversations, copied emails. It was easy to search for the necessary in the vast array of metadata. Encryption, which the FBI is trying to fight, can help protect against surveillance. The law enforcement agency needs to develop and provide a code that must never leave Cupertino.
The very behavior of the FBI inspires fear. Last weekend, it turned out that the iCloud password was reset less than a day after the government received the phone. The ill-fated iPhone could be turned on and left for auto-backup via Wi-Fi. It would be possible, but now will not succeed. Only one solution remains - to crack it. And for this you may need a tool that can easily open any other similar iPhone.
Task setting is incorrect. Court documents regard Apple as a company that writes software. Therefore, it seems that Apple will be easy to write something new. In fact, both the creation of critical security solutions and low-level solutions to bypass them mean a lot of work and testing. This is about the same as obliging the automaker to make a truck with the fifth drive wheel in a month: you can do it, but it is expensive, and the resulting vehicle will not be tested for safety.
Suppose a tool is created. Created software will have to sign certificates that are sewn into the device at the hardware level. This is an extremely important component that should never leave the company. It is probably stored in some storage with limited access. Probably in parts and in several. Probably, access to the repository may be performed by a limited circle of persons. Be that as it may, if regular hacks become the norm at the request of special services, the security of these keys will be compromised. As a result, something that already happened to Stuxnet and Flame could happen - the malware was signed with the correct certificates.
The signing ceremony for an Internet root certificate allows you to understand the importance of encryption keys.
According to Cupertino, the FBI is the first agency that requested such a hack. Prior to that, no country required to break the defense. If the whole procedure is worked out, then Apple will quickly begin to receive similar requests from the special services of other states. Their intentions can not always be regarded as good.
Finally, hacking the phone may not make any sense. After the attacks, the owner physically destroyed his personal phone and his wife’s phone. Perhaps there is nothing in the flash memory of the iPhone 5C service terrorist, or there has never been - after all, it has remained untouched. In this case, the FBI has collected a large array of information from telecommunications companies and Apple. The requirement to create a password guessing tool can be a political game to create a precedent. Indeed, lists of other iPhone unlock requests began to appear . It is unclear whether they all require the creation of a special backdoor firmware.
There is also a third option. He assumes that the choice between two evils does not play any role. The FBI will either create the necessary tools on its own, or Apple simply plays with the user's privacy advocate. The company can be understood: you need to protect the brand in the eyes of customers. Therefore, the whole performance is just marketing, according to the US Department of Justice.
The head of the company, Tim Cook, published an open letter in which he explained the company's position. It was not an ordinary dialogue between a private organization and a state structure, but a call to the public. Perhaps something in the data request was done wrong. If Apple were to remain silent, the smartphone would already be unlocked. After all, Apple in the past gave data from 70 phones. Although this only concerned the handsets on iOS 7 and below, without breaking the encryption and unlocking.
The complexity of the situation caused the expected split of opinions. Politicians, heads of large companies and other influential personalities in the field of information technology have been expressed. Few have taken explicit positions: someone says that the situation is difficult, someone says that privacy is important, as well as countering terrorism, someone is completely silent . But many sharply outlined their views.
Apple does not need to cooperate.
One of the first to respond was Google Executive Director Sundar Pichai . He wrote in his microblog: “We create secure products that securely store your information. Yes, we can disclose data at the official request of law enforcement agencies, but this is not at all the same thing as requiring companies to facilitate the hacking of user devices and data. This can be a very dangerous precedent. ”
Apple 's decision was supported by the Electronic Frontier Foundation and Reform Government Surveillance , including Microsoft (the founder), Google, and Yahoo. The RGS notes that fighting terrorism is important, but companies should not be required to create backdoors for their information security products. The press statement from Facebook contained the same idea: it is important to fight crime, but not at the expense of the privacy of ordinary people. Later, the head of the social network Mark Zuckerberg also spoke in favor of encryption. The decision of Tim Cook was supported by co-founder of Twitter microblogging service Jack Dorsey .
There was no Apple at the Mobile World Congress, but the presence was felt. The founder of VKontakte and the head of the creator of the protected Telegram messenger Pavel Durov said that he shares Apple’s side. There is always a danger that the iPhone may be stolen, and the data used on it against the owner. It is dangerous to allow additional risks of data decryption, said Durov. It is easy to see Telegram's interest in the case of an encrypted smartphone. A key feature of Telegram are end-to-end encrypted secret chats that cannot be intercepted. These correspondence remain only in the memory of smartphones.
In the messenger WhatsApp end-to-end encryption appeared in November 2014. The co-founder of the company, Jan Kum, said that he shared Tim Cook’s ideals in protecting the privacy of users. Kum believes that this dangerous precedent should not take place in the form of hacking its own device.
The American system administrator, Edward Snowden, worked for the National Security Agency, which gave him the opportunity to familiarize himself with the scale of the secret surveillance of American intelligence services. Snowden fled the country and handed over to journalists documents relating to the programs PRISM, X-Keyscore and Tempora. In an attempt to reach Brazil, Snowden stopped in Russia, where he received political asylum. Now he is actively leading microblogging on Twitter, where he regularly scolds his own secret services. Of course, the conflict between Apple and the FBI was not ignored. Snowden called it the most important event in a decade.
Apple should help the FBI
Data protection is important, but in this case it is necessary to help the investigation. So consider the victims of attacks . These people have become the target of a terrorist act, and they want to understand why. Fourteen people died, many lives were mutilated. The victims deserve a full investigation, and therefore some of them support the FBI.
But not only the participants express a similar opinion. According to a Pew Research Center study, only 38% of Americans believe that Apple should not unlock a smartphone. The vast majority of Americans surveyed (51%) share the position of the FBI and the US Department of Justice. Somehow it is difficult to describe the supporters of each of the parties to the conflict, since the share among different social groups does not fluctuate significantly. Among iPhone users themselves, 43% consider Tim Cook’s position to be correct, 47% believe that the terrorist’s iPhone should be hacked.
US elections will be held only in the fall, but the election campaign traditionally begins early. This time, candidates began to appear on television more than a year before election day. Almost all of them are nonsense, demonstrating a lack of understanding of the technical component. Especially distinguished popular candidate from the Republican Party, Donald, "I will force Apple to produce its damned computers in our country" Trump . Previously, he already remembered a variety of statements that relate to computers. In November last year, he demanded that the Internet be taken away from terrorists who use it for their own purposes. In December, this thought came again, but this time Trump added that Bill Gates should be shut down. Another statement concerned Apple: one of the most expensive American companies produces smartphones and computers outside of the United States, in China. Trump offered to make Cupertino do it on American soil. In the case of an encrypted phone, Donald harshly criticized the refusal to cooperate: “Who did they imagine?” Trump suggested boycotting Apple.
Bill Gates did not like being counted among the supporters. First, in an interview with the Financial Times, the co-founder and former head of Microsoft compared the situation with the fact that the bank could tie up a hard disk with a ribbon, and then refuse to cut it, because it would take too much to cut. The tone of Gates’s statements hinted to support the FBI’s actions and Apple’s responsibility to create a backdoor for its own product. But later, the billionaire in an interview with Bloomberg expressed disappointment with the misinterpretation of his words. Gates believes that a discussion is needed to solve the problem. Data protection is important, but government agencies should not be denied access. We need a balance between the two extremes. In other words, Gates quickly retreated to the middle position, to which many of those who do not want to attract attention, resort.
Comics A house of iPhones! , The Joy of Tech.
Source: https://habr.com/ru/post/371835/
All Articles