Microsoft cloud technologists helped deal with the Dorkbot botnet
Welcome readers of the blog iover ! In December of this year, the cybercrime group that brings together Microsoft Cybercrime Center, the Polish CERT bureau, ESET, the FBI, Interpol, Europol and other Computer Emergency Response services from several countries conducted a large-scale operation to disarm the Win32 / Dorkbot botnet that hit the computers users from more than 200 countries. In the article you will find a link to a small program ESET, which will allow you to check the computer and, if necessary, remove the malware.
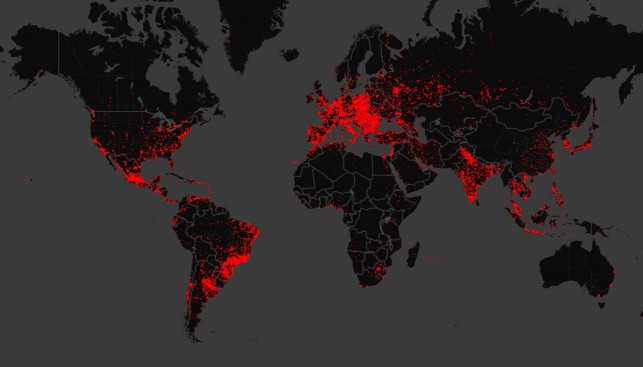
ESET virus analysts presented a technical analysis of the Win32 / Dorkbot malware, which affected users in more than 200 countries around the world. Program to check the computer and remove Dorkbot at the end of the article.
The malware spreads primarily through social networks, exploit kits, spam emails and removable media. Being installed on a PC, Dorkbot contributes to disruptions in the operation of antivirus programs, blocks their updating, and receives instructions from intruders via the IRC protocol.
')
“The scale of the spread of Dorkbot, without exaggeration, became ominous. The number of users whose computers are monthly infected with the latest version of Dorkbot at the time of the operation reached 100,000. " - said Tanmay Ganacharya, chief scientific officer of the Malware Microsoft Protection Center (MMPC).
The malware steals passwords from Facebook and Twitter services, facilitates the installation of other malicious software, in particular DDoS attacks — Win32 / Kasidet and the Win32 / Lethic spam bot. A very significant number of Dorkbot samples were found on removable media.
The specialists found out that when the Dorkbot dropper is launched from the USB media, the malware tries to download the main component of the malicious program from a remote server. And the server address is sewn up in an executable dropper file. After downloading, the file code executes the Win32 / Dorkbot.L file - a wrapper for installing the main component of Win32 / Dorkbot.B.
Win32 / Dorkbot.B, in turn, is responsible for interacting with a remote IRC server. Win32 / Dorkbot.L wrapper intercepts the DnsQuery API function from the main component. This method, to a certain extent, makes it difficult to detect the real control servers of attackers.
Upon installation, the bot tries to connect to the IRC server and receives commands from its operators via a fixed channel. Most often, Dorkbot sends commands to download and execute new malware. “Once a device is infected, the malware literally communicates with the criminals and waits for them to indicate what is required of it,” said Richard Boshkovich, Assistant General Counsel on digital crimes at Microsoft (DCU). “Millions of machines are infected, the number of pings between these infected devices and the servers providing them with instructions is staggering. We can talk sometimes about billions of pings a day. ”
To suppress the activity of Dorkbot, experts from the Cybercrime Center at Microsoft Cybercrime Center used analytical software that works in the "cloud", which processes huge amounts of information every second and allows you to visualize the spread of threats. According to the results of the program analysis, the experts came to a disappointing conclusion: the rate of infection spread was twice as high as they had expected. A coordinated blow to the virus was delivered in December of this year.
The servers through which the malware spread were physically disabled. After blocking the main servers, the botnet's traffic was redirected to protected servers under Microsoft control, which allowed identifying infected computers, notifying their users and briefing on the virus neutralization algorithm and further measures to counteract the infection.
The use of Microsoft Azure cloud technology has provided the necessary computing power. The data obtained in the process of research botnet, in turn, made it possible to take some measures to improve the level of protection of the service Azure Active Directory Premium. This service provides IT administrators with up-to-date information to ensure the required level of security, informs them about attempts by infected devices to connect to the corporate network and helps protect against large-scale attacks.
Like Microsoft, ESET virus laboratories receive almost daily modified malware samples from users. To check your computer for the presence of Dorkbot and its subsequent removal, ESET offers to use a small free program Dorkbot Cleaner, which can be downloaded here . After downloading the program, scanning usually takes less than a minute.
Read more
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review articles and other publications and will try to do everything possible so that the time spent with us will be useful for you. And, of course, do not forget to subscribe to our headings .

Our other articles and events

ESET virus analysts presented a technical analysis of the Win32 / Dorkbot malware, which affected users in more than 200 countries around the world. Program to check the computer and remove Dorkbot at the end of the article.
The malware spreads primarily through social networks, exploit kits, spam emails and removable media. Being installed on a PC, Dorkbot contributes to disruptions in the operation of antivirus programs, blocks their updating, and receives instructions from intruders via the IRC protocol.
')
“The scale of the spread of Dorkbot, without exaggeration, became ominous. The number of users whose computers are monthly infected with the latest version of Dorkbot at the time of the operation reached 100,000. " - said Tanmay Ganacharya, chief scientific officer of the Malware Microsoft Protection Center (MMPC).
The malware steals passwords from Facebook and Twitter services, facilitates the installation of other malicious software, in particular DDoS attacks — Win32 / Kasidet and the Win32 / Lethic spam bot. A very significant number of Dorkbot samples were found on removable media.
The specialists found out that when the Dorkbot dropper is launched from the USB media, the malware tries to download the main component of the malicious program from a remote server. And the server address is sewn up in an executable dropper file. After downloading, the file code executes the Win32 / Dorkbot.L file - a wrapper for installing the main component of Win32 / Dorkbot.B.
Win32 / Dorkbot.B, in turn, is responsible for interacting with a remote IRC server. Win32 / Dorkbot.L wrapper intercepts the DnsQuery API function from the main component. This method, to a certain extent, makes it difficult to detect the real control servers of attackers.
Upon installation, the bot tries to connect to the IRC server and receives commands from its operators via a fixed channel. Most often, Dorkbot sends commands to download and execute new malware. “Once a device is infected, the malware literally communicates with the criminals and waits for them to indicate what is required of it,” said Richard Boshkovich, Assistant General Counsel on digital crimes at Microsoft (DCU). “Millions of machines are infected, the number of pings between these infected devices and the servers providing them with instructions is staggering. We can talk sometimes about billions of pings a day. ”
To suppress the activity of Dorkbot, experts from the Cybercrime Center at Microsoft Cybercrime Center used analytical software that works in the "cloud", which processes huge amounts of information every second and allows you to visualize the spread of threats. According to the results of the program analysis, the experts came to a disappointing conclusion: the rate of infection spread was twice as high as they had expected. A coordinated blow to the virus was delivered in December of this year.
The servers through which the malware spread were physically disabled. After blocking the main servers, the botnet's traffic was redirected to protected servers under Microsoft control, which allowed identifying infected computers, notifying their users and briefing on the virus neutralization algorithm and further measures to counteract the infection.
The use of Microsoft Azure cloud technology has provided the necessary computing power. The data obtained in the process of research botnet, in turn, made it possible to take some measures to improve the level of protection of the service Azure Active Directory Premium. This service provides IT administrators with up-to-date information to ensure the required level of security, informs them about attempts by infected devices to connect to the corporate network and helps protect against large-scale attacks.
Like Microsoft, ESET virus laboratories receive almost daily modified malware samples from users. To check your computer for the presence of Dorkbot and its subsequent removal, ESET offers to use a small free program Dorkbot Cleaner, which can be downloaded here . After downloading the program, scanning usually takes less than a minute.
Read more
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review articles and other publications and will try to do everything possible so that the time spent with us will be useful for you. And, of course, do not forget to subscribe to our headings .

Our other articles and events
- A selection of Christmas gifts to 2016 rubles from iCover
- Buy iMac or Macbook win headset
- Review of the portable audio player Cowon Plenue M: The thing is in the sound
- Cougar gaming peripherals. Press "X" to win
- Smart cleaning with iRobot + gifts
- Exclusive records from iCover and Warner Music
- 20% discount on futurism and classics
Source: https://habr.com/ru/post/371547/
All Articles