Operating system vulnerabilities. Part IV

Here we are closer to the finish line of our review of operating system vulnerabilities. Today we will touch on quite rare OS, but deserve no less attention than, for example, macOS or Ubuntu Linux. And, in addition to the above, consider the holes in the notorious Windows Vista. For those who want to get acquainted with the materials from the previous parts, I provide the appropriate references: Part I , Part II , Part III .
But for starters, I would like to remind you why these are the OS we are examining today, how vulnerabilities are selected and what data about them is contained in the tables, of which you will see quite a lot below the text.
')
In this part we will study the third five operating systems from the table below (in bold):
| OS name | Manufacturer | Total number of vulnerabilities for 2017 | Total number of vulnerabilities for 2016 | The total number of vulnerabilities for all time statistics |
|---|---|---|---|---|
| Android | 666 | 523 | 1357 | |
| Linux Kernel | Linux | 381 | 217 | 1921 |
| Iphone os | Apple | 293 | 161 | 1277 |
| Windows 10 | Microsoft | 226 | 172 | 451 |
| Windows Server 2016 | Microsoft | 212 | 39 | 251 |
| Windows Server 2008 | Microsoft | 212 | 133 | 981 |
| Mac os x | Apple | 210 | 215 | 1888 |
| Windows Server 2012 | Microsoft | 201 | 156 | 606 |
| Windows 7 | Microsoft | 197 | 134 | 838 |
| Windows 8.1 | Microsoft | 192 | 154 | 542 |
| Windows RT 8.1 | Microsoft | 124 | 139 | 438 |
| Debian linux | Debian | 95 | 327 | 1029 |
| Fedora | Fedora project | 84 | 120 | 441 |
| Ubuntu linux | Canonical | 66 | 279 | 867 |
| Watchos | Apple | 65 | 77 | 231 |
| Windows vista | Microsoft | 64 | 125 | 814 |
| Opensuse | Opensuse project | 58 | five | 119 |
| Leap | Opensuse project | 57 | 2 | 60 |
| Leap | Novell | 48 | 260 | 349 |
| XEN | XEN | 44 | 28 | 228 |
Regarding the choice of vulnerabilities for more detailed consideration (since this was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
It is worth considering more closely some of the vulnerabilities seen on one or another OS. The CVE Details portal scores each of them. The number of points depends on the level of damage and mass distribution. The maximum indicator is 10 points. It is about such vulnerabilities (if they exist and if they are unique) that will be discussed further. In order for this article not to become Lenin’s five-volume, we will focus only on three vulnerabilities from the list, which may contain hundreds.
Regarding the data structure in the tables (since this was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
Description of the tables
In the tables of each of the types of vulnerabilities, certain additional parameters are indicated for a particular vulnerability. More about them.
Impact level
1) confidentiality :
2) integrity :
3) availability :
Difficulty of access
Authentication
In the tables of each of the types of vulnerabilities, certain additional parameters are indicated for a particular vulnerability. More about them.
Impact level
1) confidentiality :
- Full - the vulnerability allows attackers to access all information on the device;
- Partial - significant disclosure;
- None - privacy is not violated;
2) integrity :
- Full - the integrity of the system is completely compromised, the complete loss of system protection;
- Partial - modification of some system files or information is possible, but the attacker has no control over what can be changed;
- None - no impact on the integrity of the system;
3) availability :
- Full - the vulnerability allows an attacker to completely block access to the resource;
- Partial - performance degradation or intermittent availability of resources;
- None - no impact on system availability;
Difficulty of access
- Low - no special conditions for access are required, as well as no specific knowledge or skills are required;
- Medium - some conditions must be met to gain access;
- High - special access conditions limiting the exploit;
Authentication
- Not required - authentication is not required for the exploit of the vulnerability;
- Single system - the vulnerability requires the hacker to be logged into the system (for example, via the command line, desktop mode or via the web interface).
1. Windows Vista

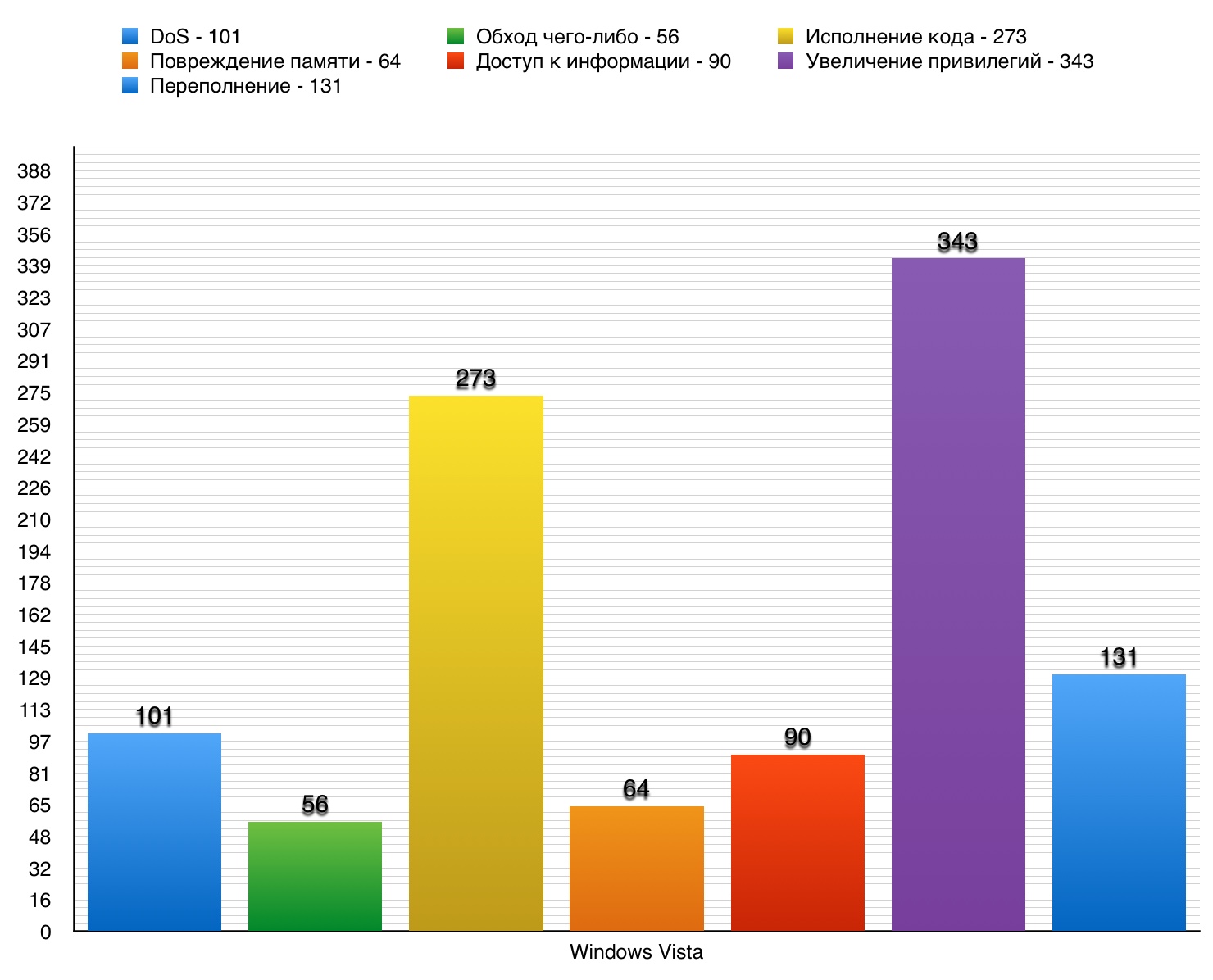
Windows Vista is the operating system of the Microsoft Windows NT family. It was released on January 30, 2007. The worst OS from Microsoft, the failure of the year and many more unflattering titles got Vista for its existence, which lasted a short time. And the percentage of distribution at the "peak of popularity" was depressingly small - only 18.6%. This was followed by a recession due to the release of new items - Windows 7. Many aspects of Vista were criticized, starting from the interface, ending with the slow work of some programs and the OS as a whole. We will step aside from these disputes and consider not opinions, but figures - data on the vulnerabilities of Vista.
DoS
Only 2 vulnerabilities out of 101 scored 10 points.
Vulnerability # 1 (10)
An array index error in implementing the SMBv2 protocol in srv2.sys allowed the remote attacker to execute the code or arrange the DoS via the “&” symbol in the process identifier in the NEGOTIATE PROTOCOL REQUEST package.
Vulnerability # 2 (10)
SMB client allowed remote SMB server and hacker to execute arbitrary code or arrange DoS through SMBv1 or SMBv2 operation response created by SMB.
Vulnerability # 3 (9.3)
Buffer overflow in stack of animated cursor code allowed remote hacker to execute arbitrary code or arrange DoS through large length of value in second anih block in RIFF .ANI, cur, or .ico file, which led to memory damage during cursor processing, animated cursors, icons .

Vulnerability Table "DoS" category in Windows Vista
Bypassing something
Only 1 of the 56 vulnerabilities scored 10 points.
Vulnerability # 1 (10)
IAS incorrectly verified the data in the MS-CHAP v2 PEAP authentication request, which allowed the remote attacker to access network resources through a malicious request.
Vulnerability # 2 (9.3)
ATL incorrectly restricted the use of OleLoadFromStream in created objects from data streams, which allowed a remote attacker to execute code through a created HTML document with an ATL component.
Vulnerability # 3 (9.3)
Microsoft Internet Explorer 5.01 SP4, 6, 6 SP1, 7, and 8 incorrectly rendered non-HTML local files as HTML documents, which made it possible to bypass access restrictions and read any files remotely.
Vulnerability Table "Crawl" category in Windows Vista
Code execution
30 vulnerabilities out of 273 scored 10 points.
Vulnerability # 1
Schannel allowed a remote hacker to execute code through the created packets.
Vulnerability # 2
A buffer overflow in the Telnet service allowed a remote attacker to execute arbitrary code through the created packets.
Vulnerability # 3
The Graphics component in the OS allowed the hacker to execute code through the created True Type font.
Code Execution Vulnerability Table for Windows Vista
Memory damage
Only 2 of the 64 vulnerabilities scored 10 points.
Vulnerability # 1 (10)
IAS incorrectly verified the data in the MS-CHAP v2 PEAP authentication request, which allowed the remote attacker to access network resources through a malicious request.
Vulnerability # 2 (10)
SMB client allowed remote SMB server and hacker to execute arbitrary code or arrange DoS through SMBv1 or SMBv2 operation response created by SMB.
Vulnerability # 3 (9.3)
Buffer overflow in stack of animated cursor code allowed remote hacker to execute arbitrary code or arrange DoS through large length of value in second anih block in RIFF .ANI, cur, or .ico file, which led to memory damage during cursor processing, animated cursors, icons .

Memory Corruption Vulnerability Table for Windows Vista
Access to the information
Of the 90 vulnerabilities, no one scored the maximum score.
Vulnerability # 1 (7.8)
The Teredo interface incorrectly handled some types of traffic, which allowed the remote attacker to bypass the firewall and get information through the generated IPv6 traffic.
Vulnerability # 2 (7.8)
The OS incorrectly imported the default IPsec protocols from the Windows Server 2003 domain to the Windows Server 2008 domain, which prevented the execution of IPsec rules and allowed the hacker to bypass access restrictions.
Vulnerability # 3 (7.2)
The OS used insecure default permissions for unspecified “local user information data stores” in the registry and file system, which allowed a local user to obtain information such as administrative passwords.

Access to Information Vulnerability Table on Windows Vista
Privilege increase
10 points scored 2 of 343 vulnerabilities.
Vulnerability # 1 (10)
Kernel-mode drivers allowed a remote hacker to obtain privileges through the application created.
Vulnerability # 2 (10)
The Graphics component in the kernel provided the opportunity to increase privileges through the application created.
Vulnerability # 3 (9.3)
The race condition in the SMB client implementation allowed remote SMB servers to increase privileges through the negotiation response created by the SMB.
Privilege Privilege Vulnerability Table for Windows Vista
Overflow
Total - 131 vulnerability. 10 points - 8 of them.
Vulnerability # 1
Kernel-mode drivers incorrectly processed memory objects, which made it possible to execute arbitrary code through the font file created by TrueType.
Vulnerability # 2
The DSA_InsertItem function in Comctl32.dll did not correctly allocate memory, which allowed the remote attacker to execute arbitrary code through the generated value in an ASP.NET web application argument.
Vulnerability # 3
A buffer overflow in the Telnet service allowed a remote attacker to execute arbitrary code through the created packets.

Vulnerability Table Overflow in Windows Vista
During its short existence, even though Vista support stopped in 2017, this OS did not accumulate so many vulnerabilities. If you view all the operating systems of the Windows family (from the first part to this one), it becomes clear that the main share of vulnerabilities is occupied by those that cause an increase in privileges. As we already know, this is extremely sad, since it is these vulnerabilities that open the door to malicious software.
2. Opensuse

openSUSE is a distribution of the Linux operating system. It first appeared in 1994. Initially, this distribution was developed in Germany, where it gained its great popularity, which spread throughout the world over the years. In 2003, Novell bought SUSE Linux, a distribution company. Many believed that this would lead to sad consequences. New broom on new sweeps, as they say. However, this did not happen. The corporation did not introduce ambiguous innovations; on the contrary, it followed the path chosen by the developers and the community themselves.
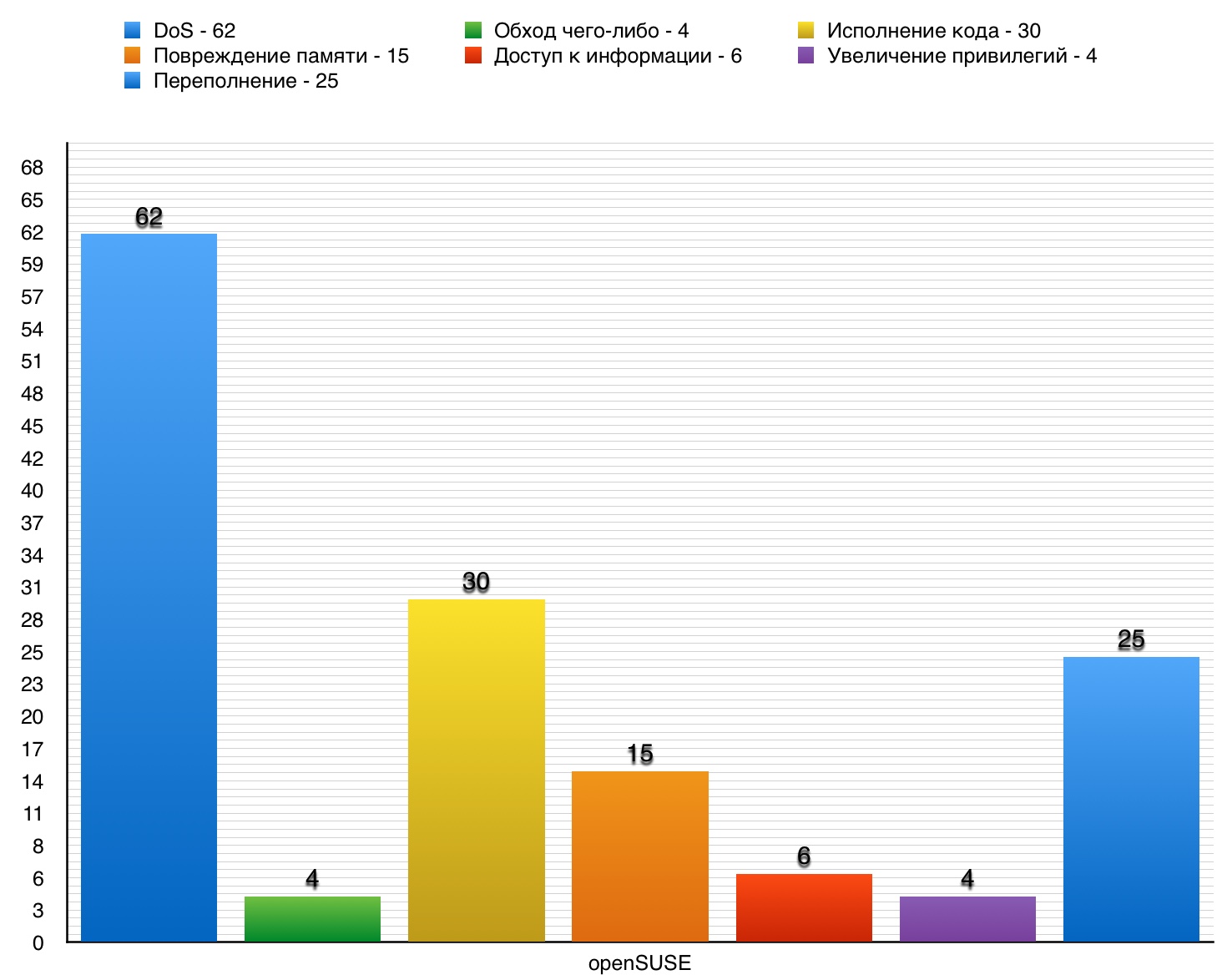
DoS
Total found 62 vulnerabilities. 10 points scored 13 of them.
Vulnerability # 1
Adobe Flash Player allowed an attacker to execute arbitrary code or arrange a DoS through an unspecified vector.
Vulnerability # 2
Pixman’s sse2_composite_src_x888_8888 function allowed a hacker to execute code or organize DoS through a created image through Canvas .
Canvas - HTML5 element for creating a racial two-dimensional image through scripts.
Vulnerability # 3
The mozilla :: dom :: OscillatorNodeEngine :: ComputeCustom function in the Web Audio subsystem in Mozilla Firefox prior to version 29.0 and in SeaMonkey up to version 2.26 allowed a remote attacker to execute arbitrary code and arrange DoS through the created content.
The DoS category vulnerability table in openSUSE OS
Bypassing something
None of the 4 vulnerabilities scored 10 points.
Vulnerability # 1 (6.8)
The function in Mozilla Firefox up to version 28.0 and in SeaMonkey up to version 2.25 allowed the remote attacker to bypass the Same Origin Policy and renders content in different domains through an unspecified vector.
Vulnerability # 2 (5.8)
The implementation of XrayWrapper in Mozilla Firefox up to version 29.0 and in SeaMonkey up to version 2.26 allowed the remote attacker to bypass the established access restrictions through the created website.
Vulnerability # 3 (5.0)
Adobe Flash Player made it possible to bypass access restrictions to memory addresses, which made it possible to bypass ASLR protection mechanisms through unspecified vectors.

Vulnerability Table "Crawl" category in openSUSE OS
Code execution
Total - 30. 10 points - 20.
Vulnerability # 1
The Adobe Flash Player use-after-free vulnerability allowed a cracker to execute arbitrary code through an unspecified vector.
Vulnerability # 2
The vulnerability of the double freeing of the memory space in Adobe Flash Player allowed the hacker to execute arbitrary code through an unspecified vector.
Vulnerability # 3
The implementation of Web workers in Mozilla Firefox up to version 27.0 and in SeaMonkey up to version 2.24 allowed a remote attacker to execute code through a vector, including the termination of the process that performed the end-to-end transfer of objects together using asm.js.

Code Execution Vulnerability Table in openSUSE OS
Memory damage
Total - 15. 10 points - 12.
Vulnerability # 1 (9.3)
A number of un-installed vulnerabilities in Mozilla Firefox browser up to version 28.0 and in SeaMonkey up to version 2.25 allowed a remote attacker to arrange DoS (resulting in memory damage and application crashes) or to execute code through an unspecified vector.
Vulnerability # 2 (9.3)
The mozilla :: dom :: TextTrack :: AddCue function in Mozilla Firefox prior to version 29.0 and in SeaMonkey prior to version 2.26 incorrectly collected garbage for Text Track Manager variables, which allowed a remote attacker to execute arbitrary code or arrange DoS (memory corruption) through the created VIDEO element in html document.
Vulnerability # 3 (7.5)
Google V8 allowed a remote attacker to arrange DoS (damaging memory) through an unspecified vector.
Table of vulnerabilities of the category "memory damage" in the OS openSUSE
Access to the information
10 points out of 6 vulnerabilities no one scored.
Vulnerability # 1 (5.0)
The vulnerability created syslog entries containing profile paths, which allowed the attacker to obtain information through the created application.
Vulnerability # 2 (5.0)
The configuration file “.encfs6.xml” in encfs prior to version 1.7.5 allowed the remote attacker to obtain specific data by setting the value “blockMACBytes” to 0 and adding 8 to “blockMACRandBytes”.
Vulnerability # 3 (5.0)
Adobe Flash Player incorrectly restricted the detection of memory addresses, which allowed an attacker to bypass the ASLR defense mechanisms through unspecified vectors.

Vulnerability table of the Access to Information category in the openSUSE OS
Privilege increase
None of the 4 vulnerabilities scored 10 points.
Vulnerability # 1 (7.2)
Google Chrome prior to version 19.0.1084.46 used invalid search paths for the Windows Media Player plugin, which could allow the user to increase privileges via a Trojan plugin in an unidentified directory.
Vulnerability # 2 (5.8)
A software overflow in inc / server.hpp in libnet6 prior to version 1.3.14 allowed a remote attacker to intercept connections and increase privileges, creating a large number of connections until an overflow occurs and another user ID becomes available.
Vulnerability # 3 (3.3)
The race condition in the Mozilla Maintenance Service allowed a local user to create files and get privileges through vectors that include hard links to the log file during the update.

Vulnerability privilege elevation table in openSUSE OS
Overflow
Total - 25. 10 points - 3.
Vulnerability # 1
Buffer overflow in Adobe Flash Player allowed an attacker to execute arbitrary code via an unspecified vector.
Vulnerability # 2
The Pixman sse2_composite_src_x888_8888 function in Pixman allowed a remote attacker to arrange DoS or execute code through the creation of CANVAS.
Vulnerability # 3
The mozilla :: dom :: OscillatorNodeEngine :: ComputeCustom feature in the Web Audio subsystem in Mozilla Firefox prior to version 29.0 and in SeaMonkey up to version 2.26 allowed the remote spiderman to execute arbitrary code or organize DoS through the created content.

Vulnerability Table Overflow in the openSUSE OS
An extremely small number of critical vulnerabilities, and indeed vulnerabilities in general, is a good indicator for the OS. OpenSUSE is designed for system administrators and developers, to a greater extent. And they are responsible for its performance, since they are actively involved in developing software for this system and polishing the elements of the system itself. It could have been different if the new owners of the developer company decided to “close” the system for the community and develop it on their own.
3. Leap Opensuse Project

Leap has become, in its own way, a new format, a new way of creating openSUSE distributions based on Linux. Appeared in November 2015.
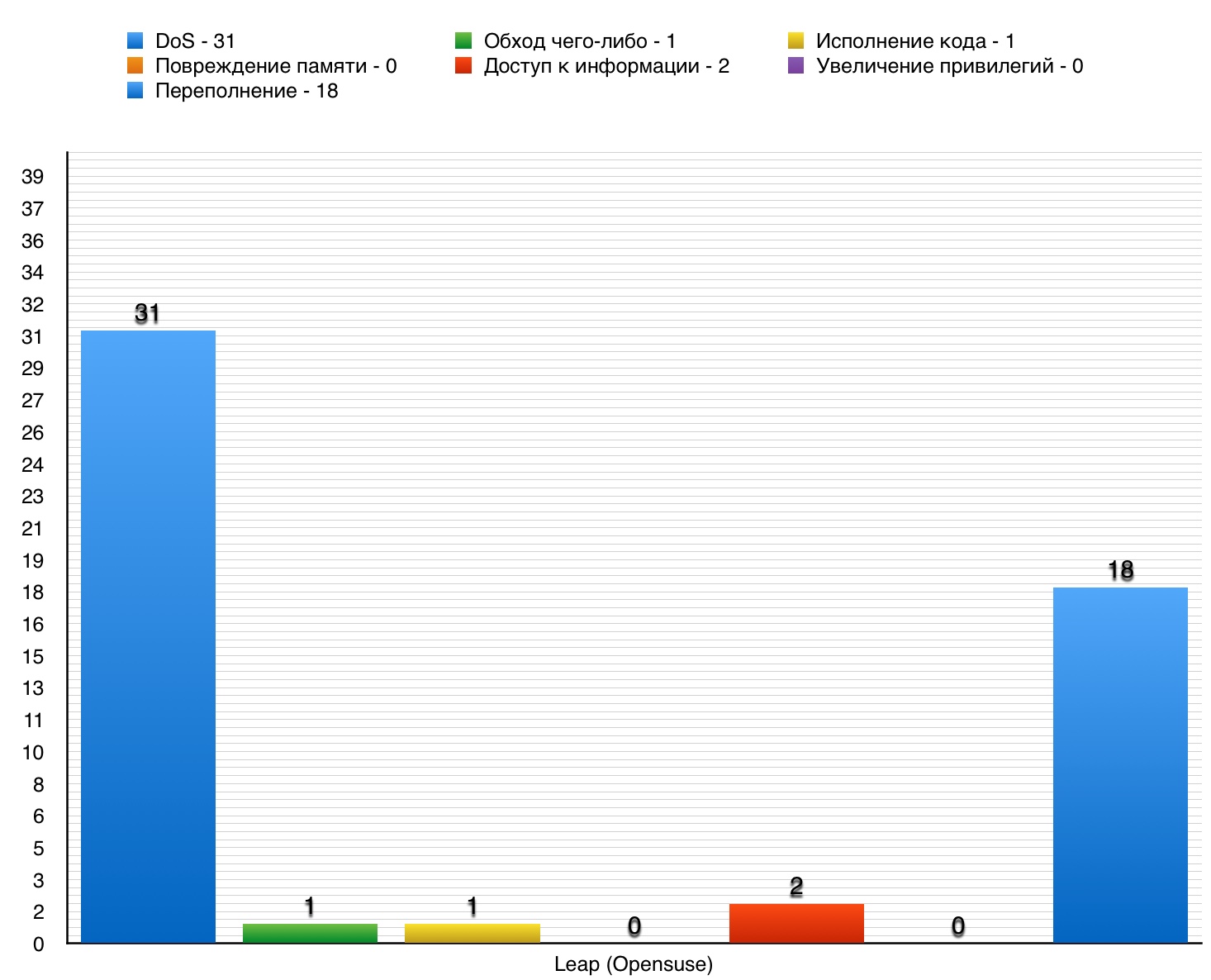
DoS
Of the 31 vulnerabilities are not those that scored 10 points.
Vulnerability # 1 (6.8)
A buffer overflow in a heap of data in the ReadRLEImage function in coders / rle.c in ImageMagick 6.9.4-8 allowed a remote attacker to arrange a DoS through the RLE file created.
Vulnerability # 2 (6.8)
The use-after-free vulnerability in ReadPWPImage function in coders / pwp.c in ImageMagick 6.9.5-5 allowed a remote attacker to organize DoS through the created file.
Vulnerability # 3 (5.0)
The memory leak in the ReadPSDLayers function in coders / psd.c in ImageMagick 6.8.9.9 allowed the remote hacker to set up a DoS through an unset vector.
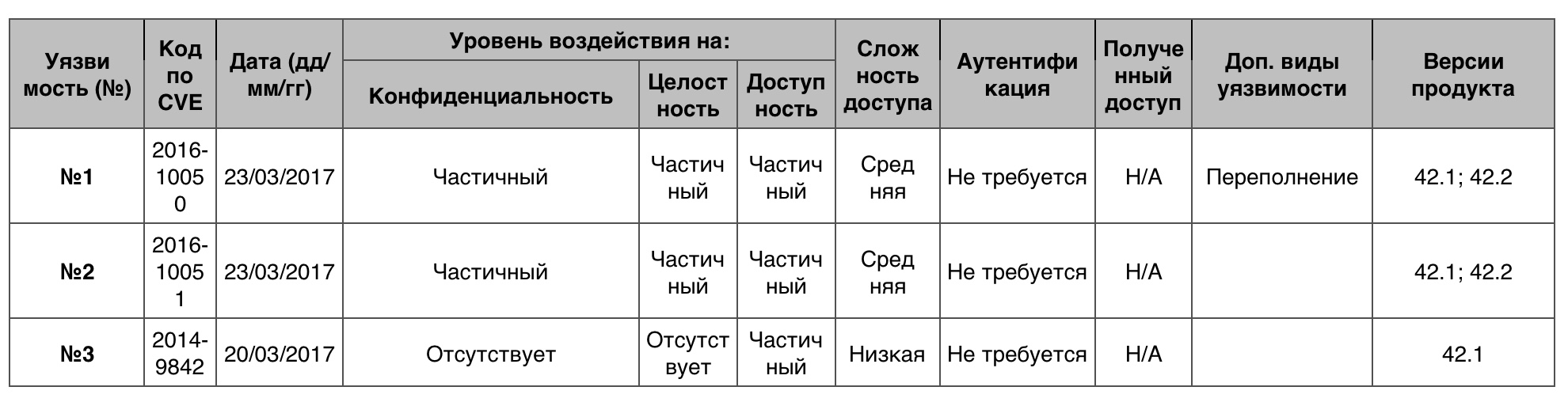
Vulnerability table of the “DoS” category in the Leap Opensuse Project
Bypassing something
Only one such vulnerability was recorded.
Vulnerability # 1 (5.0)
The validation code of the transit path in Heimdal prior to version 7.3 allowed the attacker to bypass the capath protection mechanism, using an unsuccessful attempt to add the previous hop realm to the transit ticket path.

Vulnerability Table "Crawl" category in the Leap Opensuse Project
Code execution
Only one such vulnerability was recorded.
Vulnerability # 1 (7.2)
glibc contains a vulnerability that allows a specially crafted LD_LIBRARY_PATH value to be manipulated by the heap / stack, leading to their substitution, which potentially leads to the possibility of code execution.

Code Execution Vulnerability Table in the Leap Opensuse Project
Memory damage
This type of vulnerability was not detected.
Access to the information
This type of vulnerabilities recorded a total of 2.
Vulnerability # 1 (4.3)
xbcrypt in Percona XtraBackup up to version 2.3.6 and in 2.4.x up to version 2.4.5 incorrectly sets the decryption initialization vector, which makes it easier for a hacker to get information from encrypted backup files.
Vulnerability # 2 (5.0)
The configuration file ".encfs6.xml" in encfs prior to version 1.7.5 allowed the remote attacker to obtain valuable data by setting blockMACBytes to 0 and adding 8 to blockMACRandBytes.

Vulnerability table of the category "Access to Information" in the Leap Opensuse Project
Privilege increase
This type of vulnerability was not detected.
Overflow
Of the 18 vulnerabilities, not one did not score 10 points.
Vulnerability # 1 (7.5)
The DecodePSDPixels function in coders / psd.c in ImageMagick 6.8.9.9 allowed a remote attacker to influence the system through an unspecified vector.
Vulnerability # 2 (7.5)
The buffer overflow in the ReadRLEImage function in coders / rle.c in ImageMagick 6.8.9.9 made it possible to influence the operation of the system.
Vulnerability # 3 (7.5)
The jng decoder in ImageMagick 6.8.9.9 allowed a remote attacker to make changes to the system.

Vulnerability Table of the Overflow Category in the Leap Opensuse Project
Leap from openSUSE can be called a record holder for the smallest number of vulnerabilities. Of course, this distribution has been around for a short time, since 2015. But other operating systems that did not exist longer managed to accumulate far more holes than openSUSE’s Leap.
4. Leap Novell

DoS
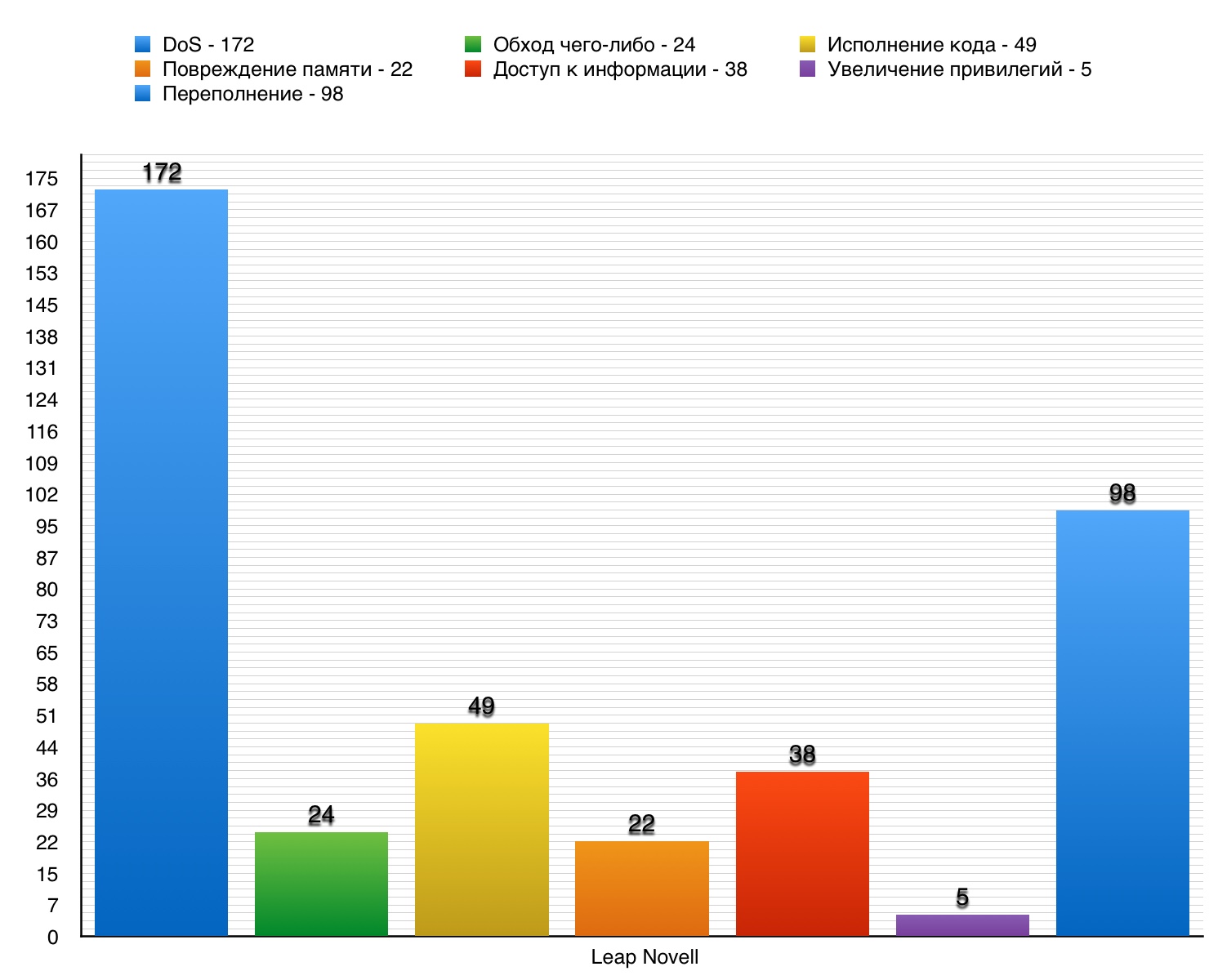
Total - 172. 10 points - 15.
Vulnerability # 1 (7.8) The
Utah RLE reader in GraphicsMagick before version 1.3.25 allowed the remote attacker to arrange DoS through the use of file size and information and header.
Vulnerability # 2 (8.3)
ext / phar / phar_object.c in PHP (up to version 5.5.32, 5.6.x - 5.6.18, 7.x - 7.0.3) incorrectly processed uncompressed data with a zero length, which allowed a remote hacker arrange DoS through the created TAR, ZIP or PHAR archive.
Vulnerability # 3 (10)
Buffer overflow in DirectWriteFontInfo :: LoadFontFamilyData function in gfx / thebes / gfxDWriteFontList.cpp in Mozilla Firefox prior to version 43.0 made it possible for a remote hacker to arrange DoS through the created font file name.

Leap Novell DoS Vulnerability Table
Bypassing anything
Total - 24. 10 points - 1.
Vulnerability # 1 (10)
Google Chrome prior to version 48.0.2564.116 allowed a remote hacker to bypass the Blink Same Origin Policy and sandbox protection mechanisms through an unspecified vector.
Vulnerability # 2 (6.8)
The ModuleSystem :: RequireForJsInner function in extensions / renderer / module_system.cc in the properties of Google Chrome prior to version 51.0.2704.63 allowed the remote attacker to carry out an attachment interception attack and bypass the Same Origin Policy through an unspecified vector.
Vulnerability # 3 (6.8)
Blink, which was used in Google Chrome prior to version 51.0.2704.63, allowed a remote attacker to bypass the Same Origin Policy via an unidentified vector.
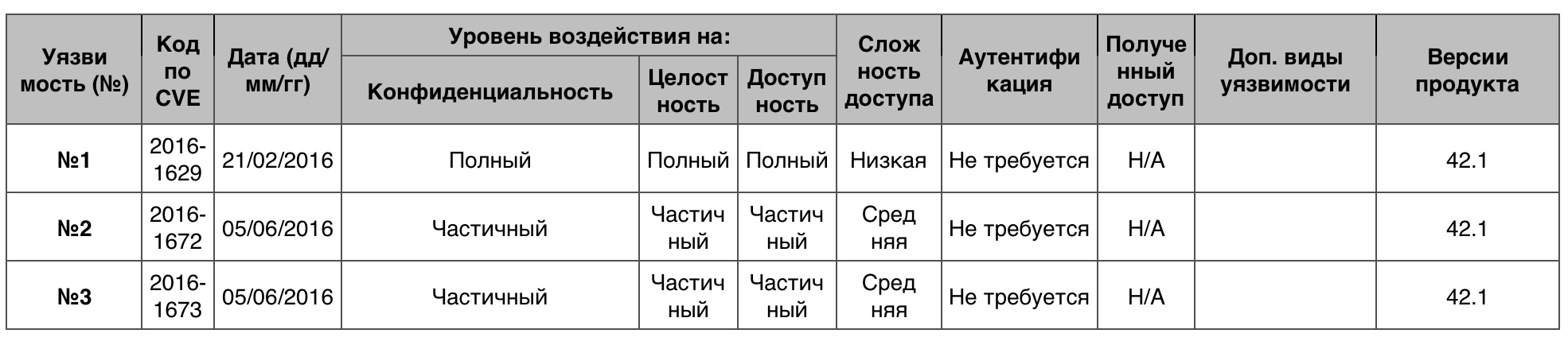
Vulnerability Table "Crawl" category in Leap Novell
Execution of the
Total code - 49. 10 points - 11.
Vulnerability # 1
The OpenBlob function in blob.c in GraphicsMagick prior to version 1.3.24 and in ImageMagick allows a remote attacker to execute arbitrary code through the use of the “|” symbol at the beginning of the file name.
Vulnerability # 2 of
revision.c in git prior to version 2.7.4 used an incorrect data type, which allowed a remote attacker to execute code through a long file name or a lot of nested data trees leading to a buffer overflow in the data heap.
Vulnerability # 3
SPICE smart card interoperability allowed a remote attacker to arrange DoS or execute code through using a connection to a guest VM, which caused a buffer overflow in the data heap.
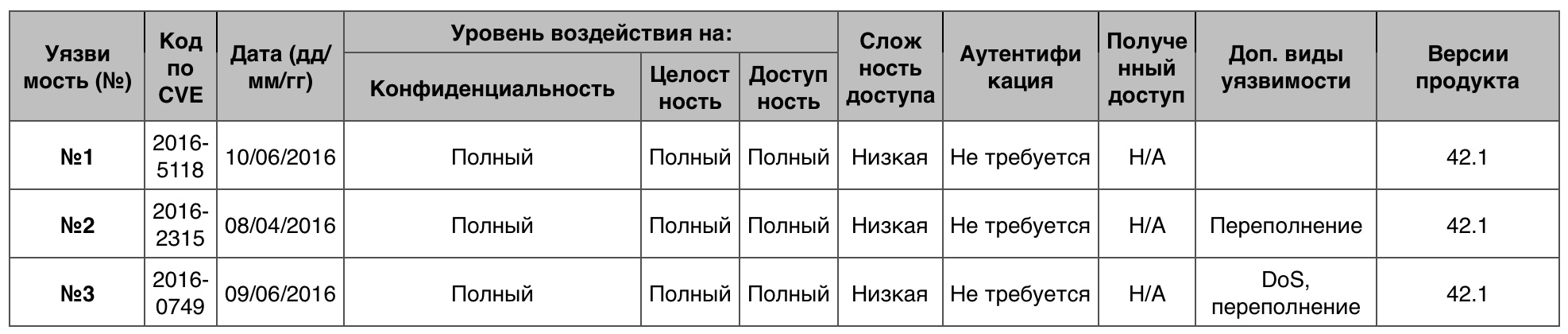
Leap Novell’s Code Execution Vulnerability Table Total
memory damage
- 22. 10 points - 7.
Vulnerability # 1 (10)
Buffer11 :: NativeBuffer11 :: map function in ANGLE used in Mozilla Firefox prior to version 44.0, allowed a remote attacker to arrange DoS or otherwise harm the system through an unspecified vector.
Vulnerability # 2 (8.3)
ext / phar / phar_object.c in PHP (up to version 5.5.32, 5.6.x - 5.6.18, 7.x - 7.0.3) incorrectly processed uncompressed data with a zero length, which allowed a remote hacker arrange DoS through the created TAR, ZIP or PHAR archive.
Vulnerability # 3 (7.5)
A software overflow in proto.c in libotr up to version 4.1.1 on 64-bit platforms allowed a remote attacker to arrange DoS (memory corruption) or execute code through a large OTR message, which causes a buffer overflow in the data heap.
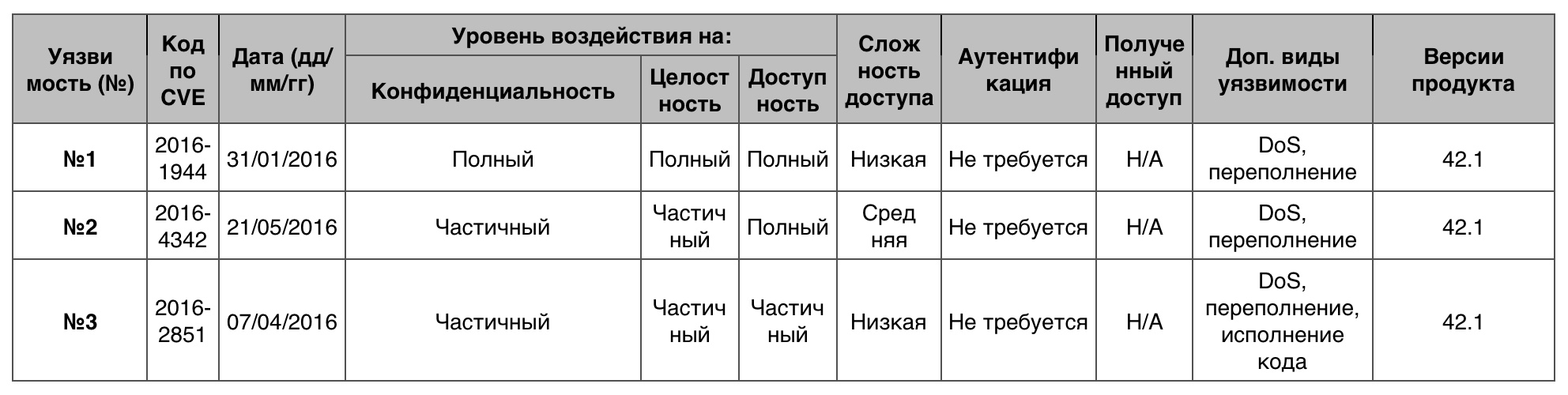
Vulnerability table of the category “memory corruption” in Leap Novell
Access to information
Total - 38. 10 points - 1.
Vulnerability # 1 (10)
Software overflow in the RTPReceiverVideo :: ParseRtpPacket function in Mozilla Firefox to version 43.0 and in Firefox ESR 38.x to version 38.5 allowed a remote hacker to obtain valuable information, arrange DoS using the created WebRTC RTP package.
Vulnerability # 2 (7.5)
The index_urlfetch function in index.c in Cyrus IMAP (versions: 2.3.x - 2.3.19, 2.4.x - 2.4.18, 2.5.x - 2.5.4) allowed a remote attacker to get information through a vector including the urlfetch range.
Vulnerability # 3 (6.4)
gd_xbm.c in the GD Graphics library prior to version 2.2.0, which was used in some custom PHP 5.5.x configurations, allowed the attacker to obtain information from the process memory or organize DoS through a long name.

Leap Novell’s Access to Information Vulnerability Table
Privilege Increase
Total - 5. 10 points - 0.
Vulnerability # 1 (7.2)
A stack-based buffer overflow in the FascistGecosUser function in lib / fascist.c in cracklib allowed a local user to arrange DoS or get privileges through a long GECOS field, including a long buffer.
Vulnerability # 2 (6.8)
The nsCSPContext :: SendReports feature in dom / security / nsCSPContext.cpp in Mozilla Firefox prior to version 45.0 and in Firefox ESR 38.x - 38.7 did not prevent the use of non-HTTP report-uri for a Content Security Policy violation report (CSP), which allowed to arrange DoS or obtain privileges through the definition of the URL of the local file.
Vulnerability # 3 (6.5)
git-shell in git allowed a remote authenticated user to get privileges through the name repository, which starts with the “-” symbol.
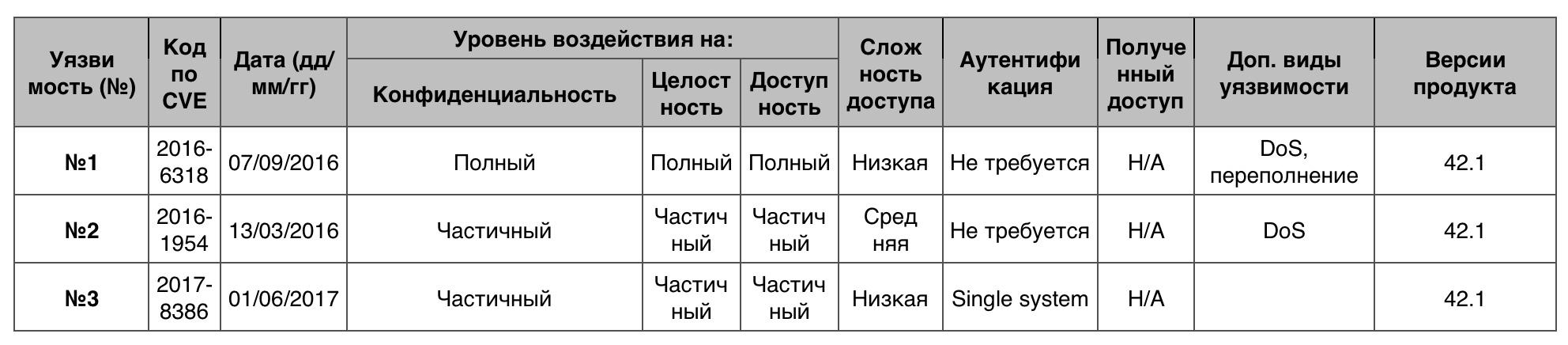
Table vulnerabilities "Increasing benefits" category Leap Novell
overflow
Total - 10 points 98. - 15.
Vulnerability №1
revision.c in git to version 2.7.4 using the wrong data type, allowing a remote attacker to execute arbitrary code via a long file name or a lot of embedded tree data, which leads to a buffer overflow.
Vulnerability # 2
The MoofParser :: Metadata function in binding / MoofParser.cpp in libstagefright in Mozilla Firefox prior to version 44.0 did not limit the size of read operations, which allowed a remote hacker to arrange DoS through the metadata created by him.
Vulnerability # 3
An off-by-one error in the tokenadd function in jv_parse.c in jq allowed a remote attacker to arrange a DoS through a long JSON-encoded number, which causes a buffer overflow.

Vulnerability Table Overflow in Leap Novell
5. XEN

XEN is a cross-platform hypervisor, it has been running since 2003. Yes, it is not an operating system. However, XEN is required for various operating systems to run on a virtual machine.
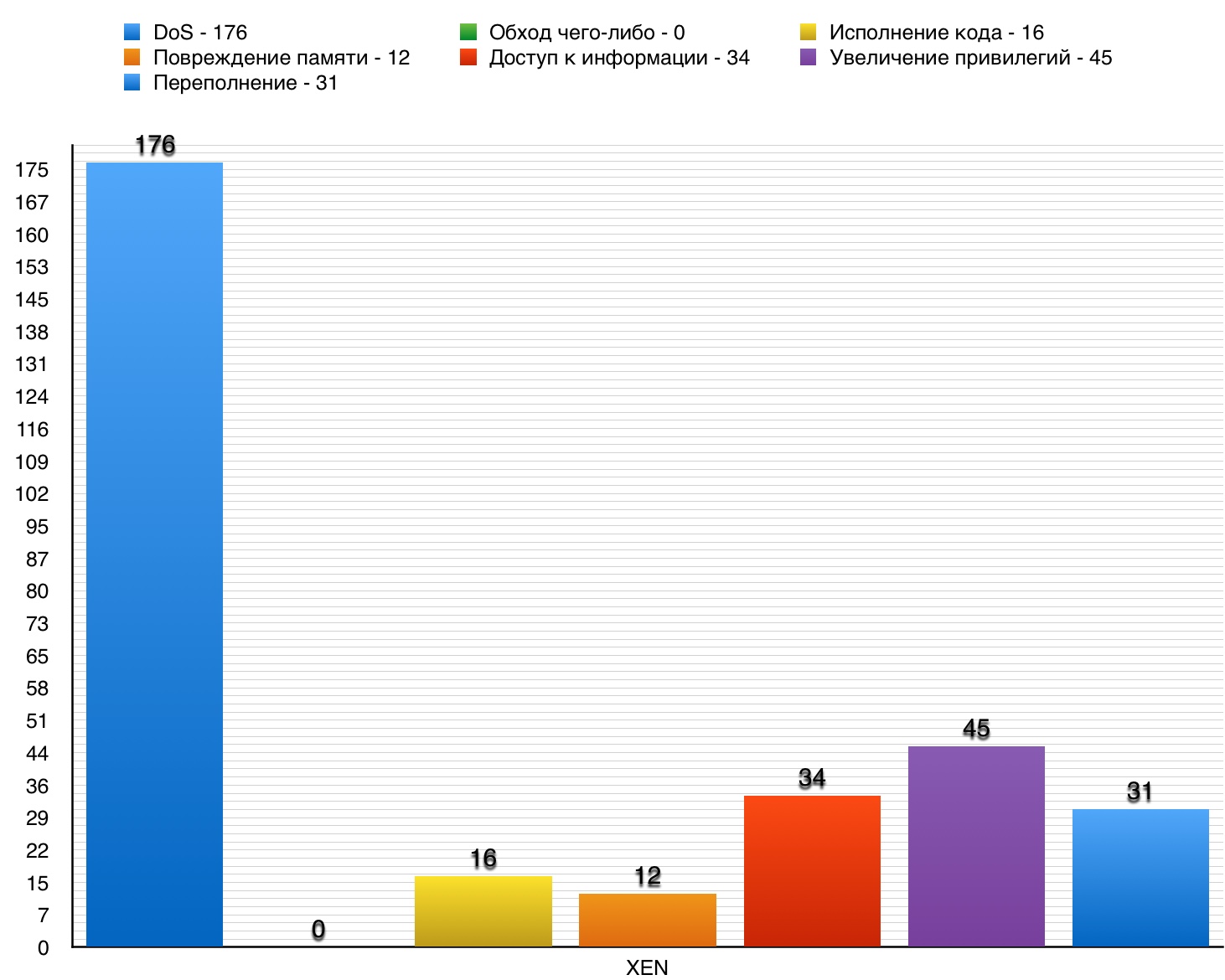
DoS
Total - 176. 10 points - 2.
Vulnerability # 1 (10)
The main table in Xen to version 4.8.x did not provide for the calculation of the sufficient display types GNTMAP_device_map and GNTMAP_host_map, which allowed the guest user to arrange DoS or increase privileges in access to the OS.
Vulnerability # 2 (9.4)
Xen incorrectly handled port numbers, which allowed a ready-made user to arrange DoS or get information.
Vulnerability # 3 (8.3)
The do_physdev_op function incorrectly restricted access to the PHYSDEVOP_prepare_msix and PHYSDEVOP_release_msix operations, which allowed the local PV user to arrange DoS or get privileges through an unspecified vector.

Table of vulnerabilities in the category "DoS" in XEN.
Bypassing something
Vulnerabilities of this kind have not yet been fixed. Total
code execution
- 16. 10 points - 0.
Vulnerability # 1 (7.5)
Buffer overflow in the data heap in the PCNET controller in QEMU allowed the remote attacker to execute arbitrary code, sending a packet with the TXSTATUS_STARTPACKET set and then a created packet with the TXSTATUS_DEVOWOWNS set.
Vulnerability # 2 (7.2)
x86 Xen emulation from 3.2.x to version 4.5.x incorrectly ignored redefinition of segments for instructions with register operands, which allowed the local guest user to get information through an unspecified vector.
Vulnerability # 3 (7.2)
The use-after-free vulnerability in the FIFO allowed the local guest of the OS with administrator rights to arrange DoS and execute the code or get information through the wrong guest frame number.

Code Execution Vulnerability Table in XEN
Memory damage
Total - 12. 10 points - 2.
Vulnerability # 1 (10)
The main table in Xen prior to version 4.8.x did not provide for the calculation of sufficient display types GNTMAP_device_map and GNTMAP_host_map, which allowed the guest user to arrange DoS or increase privileges in access to the OS.
Vulnerability # 2 (7.4)
Buffer overflow in Python to call xc_vcpu_setaffinity allowed the local administrator with permission to configure the VCPU to arrange DoS (memory corruption) and get privileges through the created cpumap.
Vulnerability # 3 (7.2)
x86 Xen emulation from 3.2.x to version 4.5.x incorrectly ignored redefinition of segments for instructions with register operands, which allowed the local guest user to get information through an unspecified vector.
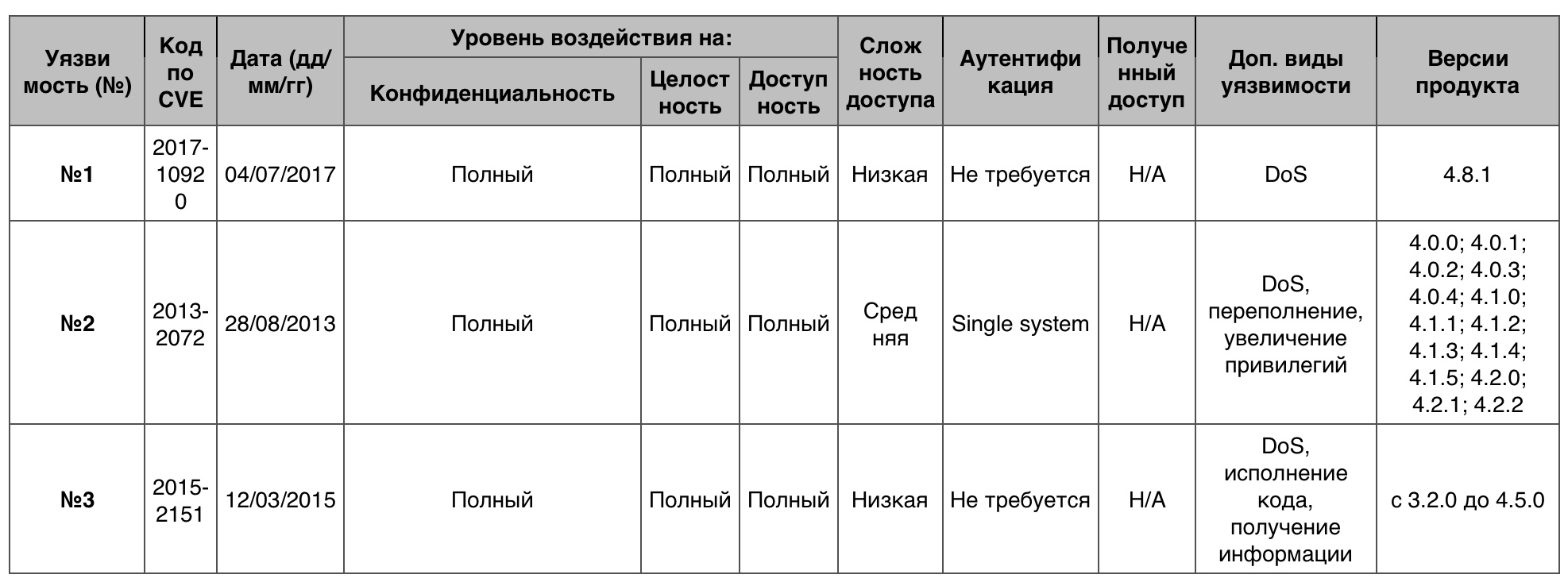
Table of vulnerabilities in the category "memory corruption" in XEN
Access to information
Total - 34. 10 points - 0.
Vulnerability # 1 (9.4)
Xen incorrectly processed port numbers, which allowed a ready-made user to arrange DoS or get information.
Vulnerability # 2 (7.5)
The main table in Xen incorrectly displayed information in certain cases of simultaneous undisclosed calls, which allowed the hacker to obtain information, arrange DoS or execute arbitrary code or increase privileges.
Vulnerability # 3 (7.2)
x86 Xen emulation from 3.2.x to version 4.5.x incorrectly ignored redefinition of segments for instructions with register operands, which allowed the local guest user to get information through an unspecified vector.

Vulnerability table of the category "Access to Information" in XEN
Privilege Increase
Total - 45. 10 points - 0.
Vulnerability # 1 (8.3)
The do_physdev_op function incorrectly restricted access to the PHYSDEVOP_prepare_msix and PHYSDEVOP_release_msix operations, which allowed the local PV user to arrange DoS or obtain privileges through an unspecified vector.
Vulnerability # 2 (7.9)
Xen, while using Intel VT-d for a bypass PCI, incorrectly got rid of TLB after clearing the existing translation field, which allowed a local user with administrative rights to arrange DoS or get privileges through an unspecified vector.
Vulnerability # 3 (7.5)
The main table in Xen incorrectly displayed information in certain cases of simultaneous undisclosed calls, which allowed the hacker to obtain information, arrange DoS or execute arbitrary code or increase privileges.
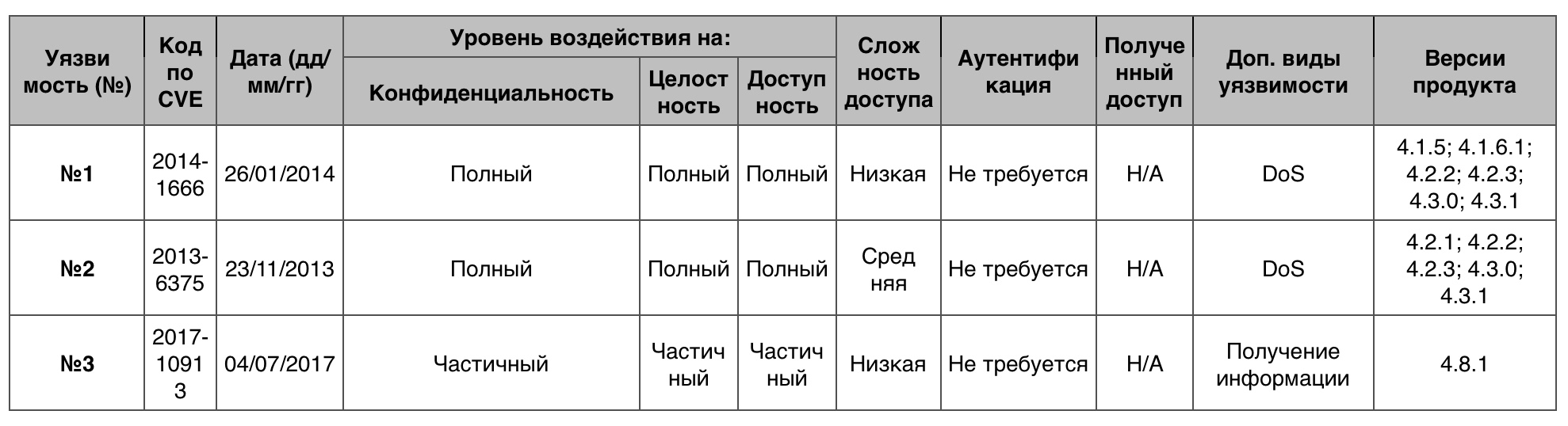
XEN Vulnerability Table in XEN Total
Overflow
- 31. 10 points - 0.
Vulnerability # 1 (7.5)
Buffer overflow in the data heap in the PCNET controller in QEMU allowed the remote attacker to execute arbitrary code by sending a packet with the TXSTATUS_STARTPACKET set and created package with TXSTATUS_DEVICEOWNS set.
Vulnerability # 2 (7.4)
Buffer overflow in Python to call xc_vcpu_setaffinity allowed the local administrator with permission to configure the VCPU to arrange DoS (memory corruption) and get privileges through the created cpumap.
Vulnerability # 3 (7.2)
The kernel system call functionality, when running on an Intel processor, incorrectly uses the sysret path in cases where certain addresses are not canonical, which allows a local user to get privileges through the created application.

XEN overflow vulnerability table in XEN. A
small number of vulnerabilities in the XEN hypervisor ensure stable operation of the virtual machine, reducing the likelihood of malicious interference.
This is where our statistical analysis of various OS vulnerabilities has come to an end. Some of them can boast a small number of holes, others - on the contrary. However, as mentioned earlier, the number of vulnerabilities is not as important as the extent and frequency of their exploit by attackers.
There are quite a few operating systems, not to mention the different versions of each of them. In this series of articles, we have only slightly touched some of them in order to have a simple idea of their vulnerabilities. In order to see the full picture, we would have to analyze all the operating systems, all their versions and all their holes, respectively. And such an analysis would take us an incredibly long time. And even, having conducted such an analysis, we would not be able to firmly state that this OS is bad, but that is a good one. In addition to vulnerabilities, other factors are taken into account to make such statements: functionality, supported software, interface, after all, and much more. Each OS can be ideal for a specific group of people who need to perform certain tasks with their help. I, personally, use both Windows 10 and macOS (on two laptops, of course). AND,understanding their differences, yet I appreciate both, without choosing favorites.
Choose an OS for your needs, analyze information, consider the functionality of applicants, and just use what you like, and not what most advises. Have a nice day and see you soon.
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
Source: https://habr.com/ru/post/371011/
All Articles