Operating system vulnerabilities. Part II

A blessing in disguise, and a good in a blessing. In each barrel of honey there is a fly in the ointment. There are quite a lot of folk wisdom, aphorisms and quotes about the presence of flaws in anything. Today we will continue to study the shortcomings, or rather the vulnerabilities, of various operating systems (operating systems). I present to you the second part of the OS Vulnerability series of publications. You can find the first one here ( link to part I ). Today we will study the problem areas of several representatives of the Windows family and its eternal opponent - macOS.
But for starters, I would like to remind you of why it is these OSs that we are examining today, how vulnerabilities are selected and what data about them is contained in the tables, of which you will see quite a bit lower in the text.
')
In this part we will study the second five operating systems from the table below (in bold):
| OS name | Manufacturer | Total number of vulnerabilities for 2017 | Total number of vulnerabilities for 2016 | The total number of vulnerabilities for all time statistics |
|---|---|---|---|---|
| Android | 666 | 523 | 1357 | |
| Linux Kernel | Linux | 381 | 217 | 1921 |
| Iphone os | Apple | 293 | 161 | 1277 |
| Windows 10 | Microsoft | 226 | 172 | 451 |
| Windows Server 2016 | Microsoft | 212 | 39 | 251 |
| Windows Server 2008 | Microsoft | 212 | 133 | 981 |
| Mac os x | Apple | 210 | 215 | 1888 |
| Windows Server 2012 | Microsoft | 201 | 156 | 606 |
| Windows 7 | Microsoft | 197 | 134 | 838 |
| Windows 8.1 | Microsoft | 192 | 154 | 542 |
| Windows RT 8.1 | Microsoft | 124 | 139 | 438 |
| Debian linux | Debian | 95 | 327 | 1029 |
| Fedora | Fedora project | 84 | 120 | 441 |
| Ubuntu linux | Canonical | 66 | 279 | 867 |
| Watchos | Apple | 65 | 77 | 231 |
| Windows vista | Microsoft | 64 | 125 | 814 |
| Opensuse | Opensuse project | 58 | five | 119 |
| Leap | Opensuse project | 57 | 2 | 60 |
| Leap | Novell | 48 | 260 | 349 |
| XEN | XEN | 44 | 28 | 228 |
Regarding the choice of vulnerabilities for more detailed consideration (since this was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
It is worth considering more closely some of the vulnerabilities seen on one or another OS. The CVE Details portal scores each of them. The number of points depends on the level of damage and mass distribution. The maximum indicator is 10 points. It is about such vulnerabilities (if they exist and if they are unique) that will be discussed further. In order for this article not to become Lenin’s five-volume, we will focus only on three vulnerabilities from the list, which may contain hundreds.
Regarding the data structure in the tables (since this was already written in the previous part, we will hide everything under the spoiler so as not to lengthen the text):
Description of the tables
In the tables of each of the types of vulnerabilities, certain additional parameters are indicated for a particular vulnerability. More about them.
Impact level
1) confidentiality :
2) integrity :
3) availability :
Difficulty of access
Authentication
In the tables of each of the types of vulnerabilities, certain additional parameters are indicated for a particular vulnerability. More about them.
Impact level
1) confidentiality :
- Full - the vulnerability allows attackers to access all information on the device;
- Partial - significant disclosure;
- None - privacy is not violated;
2) integrity :
- Full - the integrity of the system is completely compromised, the complete loss of system protection;
- Partial - modification of some system files or information is possible, but the attacker has no control over what can be changed;
- None - no impact on the integrity of the system;
3) availability :
- Full - the vulnerability allows an attacker to completely block access to the resource;
- Partial - performance degradation or intermittent availability of resources;
- None - no impact on system availability;
Difficulty of access
- Low - no special conditions for access are required, as well as no specific knowledge or skills are required;
- Medium - some conditions must be met to gain access;
- High - special access conditions limiting the exploit;
Authentication
- Not required - authentication is not required for the exploit of the vulnerability;
- Single system - the vulnerability requires the hacker to be logged into the system (for example, via the command line, desktop mode or via the web interface).
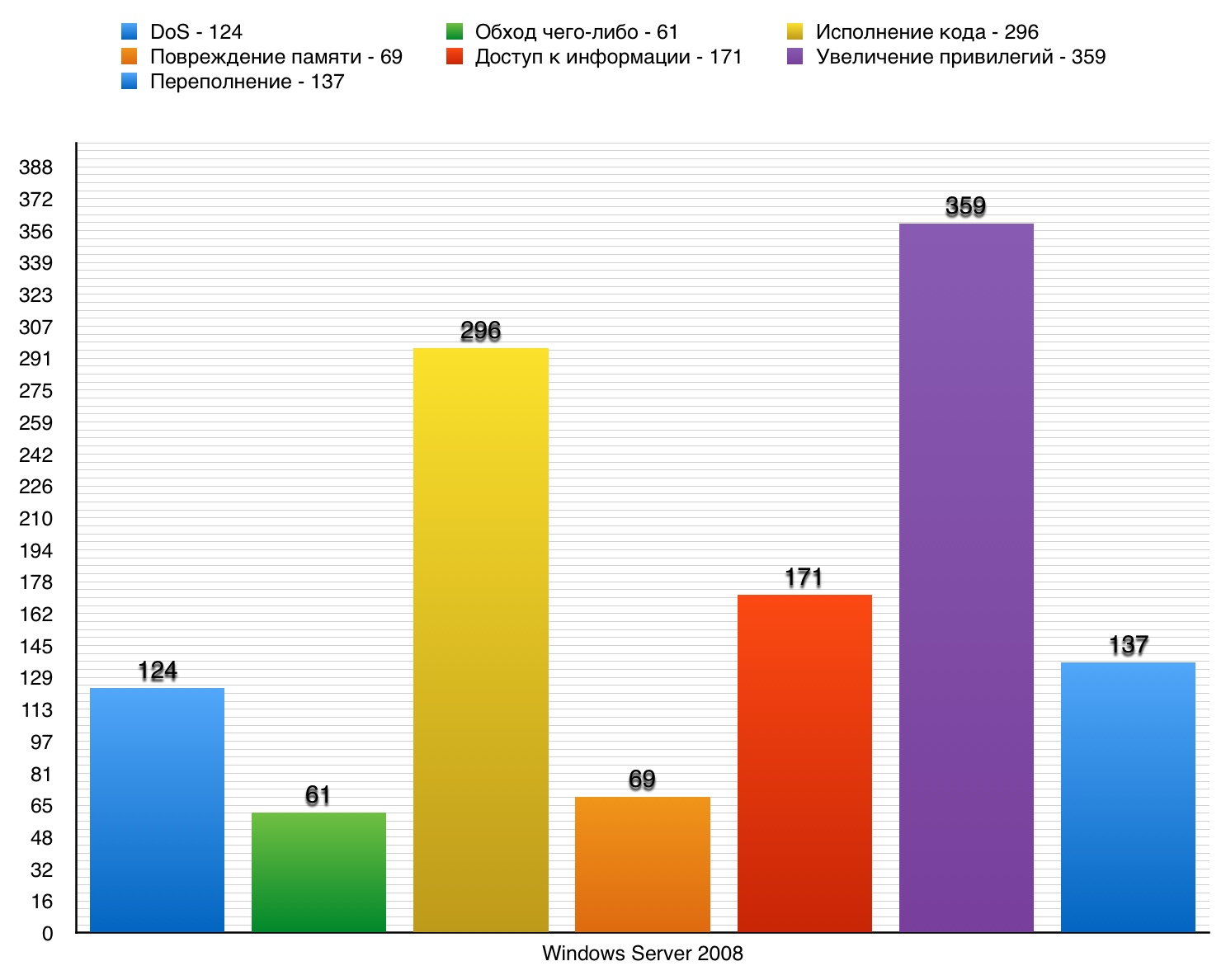
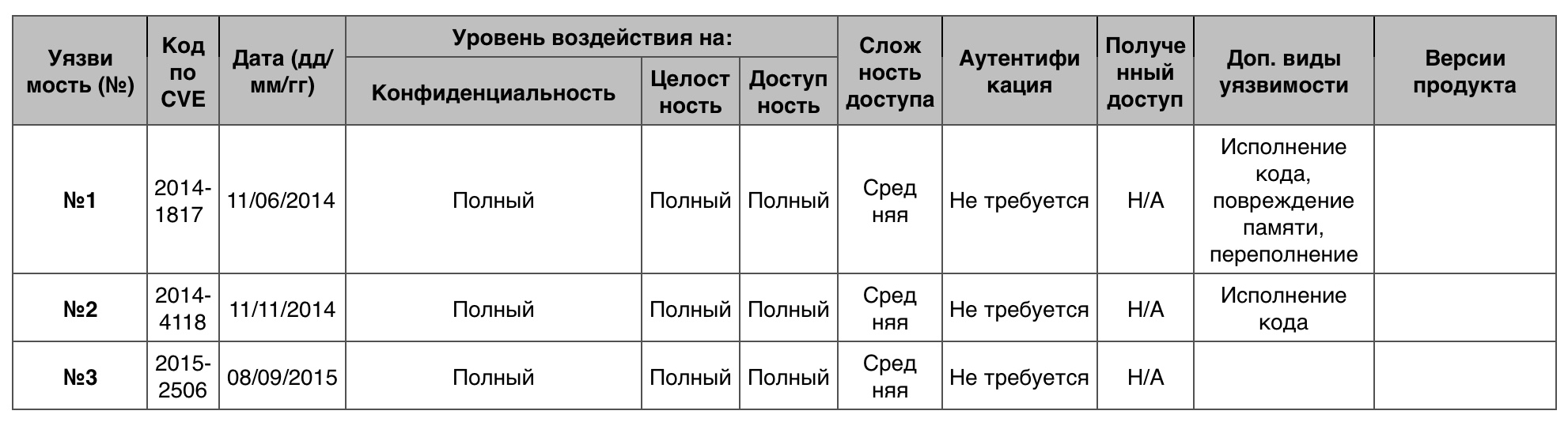
1. Windows Server 2008

Windows Server 2008 is a server operating system from Microsoft released on February 27, 2008. Became the first representative of a new generation of OS family Vista. This OS, which has become a replacement for Windows Server 2003, has many new features, including improved security protocols. At the moment, modern equipment no longer supports the once revolutionary server OS. Now is the era of 2012 and 2016 versions.
DoS
Of the 125 vulnerabilities, 4 scored 10 points.
Vulnerability # 1
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 2
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 3
Creating a task for printing through Print Spooler made it possible to arrange DoS.
Table of vulnerabilities category "DoS" in Windows Server 2008
Bypassing something
Of the 61 vulnerabilities, 10 points scored only one.
Vulnerability # 1 (10)
IAS incorrectly verified the credentials in the MS-CHAP v2 Protected Extensible Authentication Protocol (PEAP) authentication request, which allowed remote access to network resources via a malicious request.
IAS - Internet Authentication Service - a Windows Server OS component that centrally manages user accounts.
Vulnerability # 2 (9.3)
ATL could not properly restrict the use of OleLoadFromStream in the created objects from data streams, which allowed to execute arbitrary code through the created HTML document with the ATL component or bypass security protocols.
ATL - Active Template Library - a set of template classes of the C ++ language necessary to simplify the process of writing COM components.
Vulnerability # 3 (9.3)
Microsoft Internet Explorer 5.01 SP4, 6, 6 SP1, 7, and 8 did not prevent rendering local non-HTML files as HTML documents, which made it possible to remotely bypass access restrictions and read any files through vectors, which include an exploit using software text / html as standard content-type files that are found after the redirect.
Vulnerability Table "Crawl" category in Windows Server 2008
Code execution
Of the 302 vulnerabilities received 10 points 37.
Vulnerability # 1
The OS provided the hacker with complete control over the system when Windows Search could not handle the handling of memory objects.
Vulnerability # 2
The OS provided the hacker with complete control over the system when Windows Search could not handle the handling of memory objects.
Vulnerability # 3
Windows Search made it possible to execute code because of a failure in the process of processing DNS responses.

Code Execution Vulnerability Table in Windows Server 2008
Memory damage
Only 69 vulnerabilities. 10 points - 4 vulnerabilities.
Vulnerability # 1
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 2
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 3
Creating a task for printing through Print Spooler opened the possibility to damage the memory.

Memory Corruption Vulnerability Table in Windows Server 2008
Access to the information
Total - 176. 10 points - 0.
Vulnerability # 1 (7.2)
Kernel-mode drivers allowed a local authenticated user to execute an application created by him for information.
Vulnerability # 2 (6.8)
The implementation of the Group Policy did not distribute passwords correctly, which made it possible to take possession of credentials and gain privileges using access to SYSVOL .
SYSVOL - System Volume - a common directory on the server that stores copies of public domain files.
Vulnerability # 3 (6.6)
win32k.sys in the kernel mode drivers made it possible for local users to acquire information from the kernel memory through the application created.
Table of Vulnerabilities in the Access to Information Category on Windows Server 2008
Privilege increase
359 - in total. 10 points - 2 vulnerabilities.
Vulnerability # 1 (10)
Kernel-mode drivers made it possible to obtain privileges through the application created.
Vulnerability # 2 (10)
The Graphics component in the kernel allowed a local user to obtain privileges through the application created.
Vulnerability # 3 (9.3)
The race condition in the SMB client implementation allowed remote SMB servers to increase privileges through the negotiation response created by the SMB.
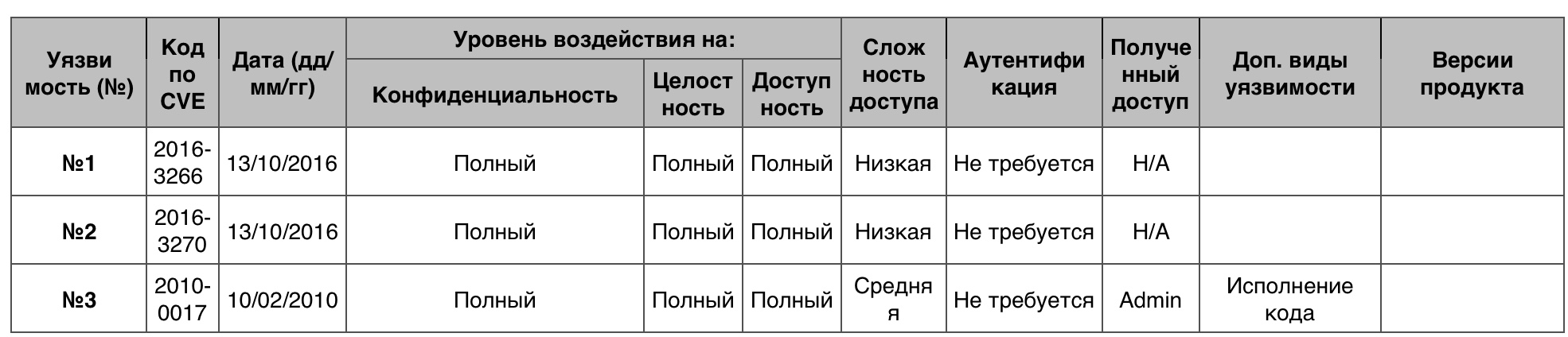
Privilege escalation vulnerability table in Windows Server 2008
Overflow
Of the 139 vulnerabilities, 9 of them scored the maximum score.
Vulnerability # 1
Creating a print task through Print Spooler could lead to software overflow.
Vulnerability # 2
The DSA_InsertItem function in Comctl32.dll did not allocate memory properly, allowing a remote attacker to execute code through the generated value in an ASP.NE argument of the web application.
Vulnerability # 3
A buffer overflow in the Telnet service allowed to execute arbitrary code through the created packages.
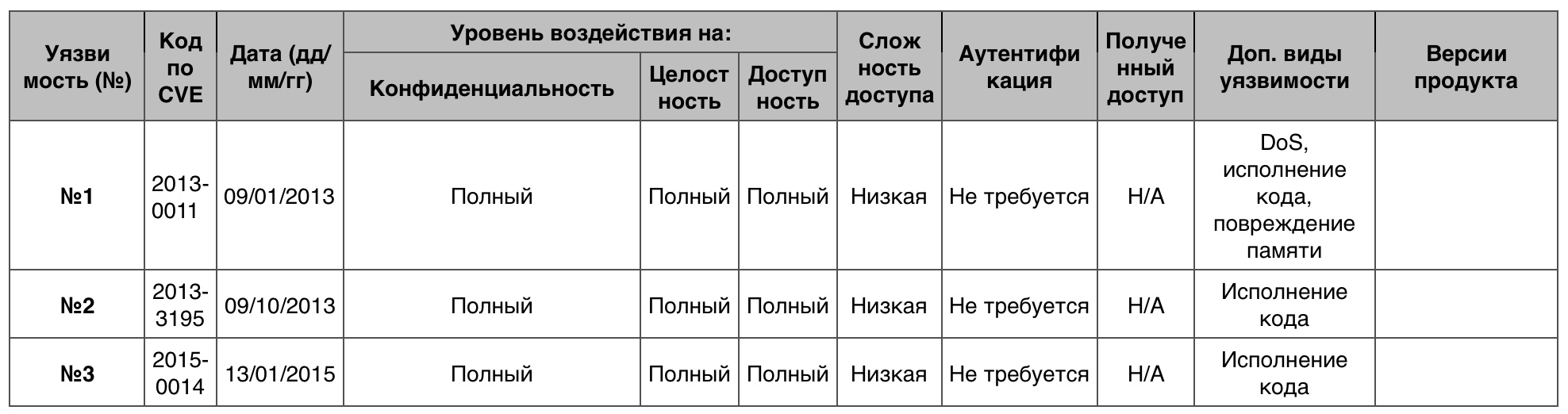
Vulnerability Table Overflow in Windows Server 2008
2. Mac Os X

Mac Os X is an operating system from Apple. It was first introduced as a beta version in 2001. Until 2012, Mac OS X was called, then -OS X, and from 2016 - macOS. According to various data, the correctness of which is extremely difficult to verify, the market share of macOS is about 5%. Naturally most of the market is occupied by various versions of Windows, for example Windows 7 - more than 25%.
The total number of recorded vulnerabilities is formed on a database collected from 1999 to 2017, and is 1888.

DoS
Of the 891 vulnerabilities, 10 points scored 47.
Vulnerability # 1
ImageIO allowed a remote hacker to execute arbitrary code or organize DoS through the xStride and yStride he created in the EXR image.
Vulnerability # 2
libxml2 allowed a remote attacker to execute arbitrary code or organize DoS through an XML document created by it.
Vulnerability # 3
Audio in OS X prior to version 10.12 allowed a remote hacker to execute arbitrary code or organize DoS via an unspecified vector.

Table of vulnerabilities category "DoS" in OS macOS
Bypassing something
176 - total. 10 points - 21.
Vulnerability # 1
Adobe Reader and Acrobat 10.x (up to version 10.1.14) and 11.x (up to version 11.0.11) allowed an attacker to bypass restrictions on the execution of the JavaScript API via an unspecified vector.
Vulnerability # 2
Adobe Reader and Acrobat 10.x (up to version 10.1.14) and 11.x (up to version 11.0.11) allowed an attacker to bypass restrictions on the execution of the JavaScript API via an unspecified vector.
Vulnerability # 3
The File Bookmark component in OS X prior to version 10.11.2 made it possible to bypass the sandbox security protocols for application bookmarks through the created path to the file.

Vulnerability Table "Crawl" category in macOS
Code execution
843 vulnerability in all. Scored 10 points - 83.
Vulnerability # 1
ImageIO allowed a remote hacker to execute arbitrary code or organize DoS through the xStride and yStride he created in the EXR image.
Vulnerability # 2
libxml2 allowed a remote attacker to execute arbitrary code or organize DoS through an XML document created by it.
Vulnerability # 3
Audio in OS X prior to version 10.12 allowed a remote hacker to execute arbitrary code or organize DoS via an unspecified vector.
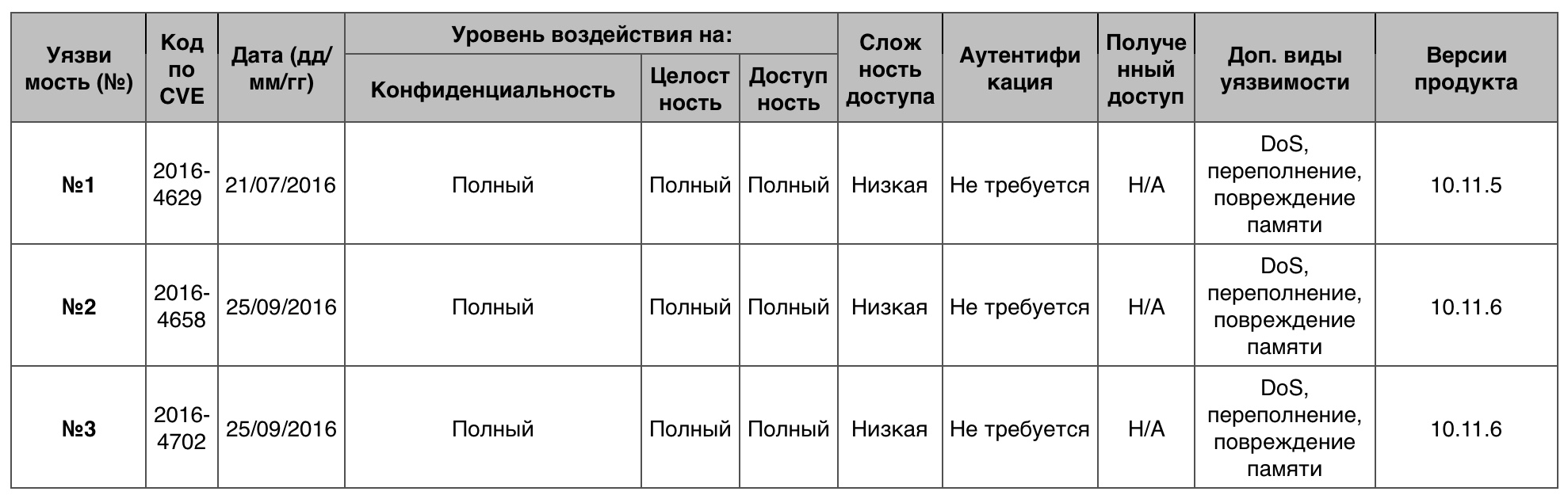
Code Execution Vulnerability Table on MacOS
Memory damage
425 vulnerabilities in total, of which 10 points scored 26.
Vulnerability # 1
ImageIO allowed a remote hacker to execute arbitrary code or organize DoS through the xStride and yStride he created in the EXR image.
Vulnerability # 2
libxml2 allowed a remote attacker to execute arbitrary code or organize DoS through an XML document created by it.
Vulnerability # 3
Audio in OS X prior to version 10.12 allowed a remote hacker to execute arbitrary code or organize DoS via an unspecified vector.
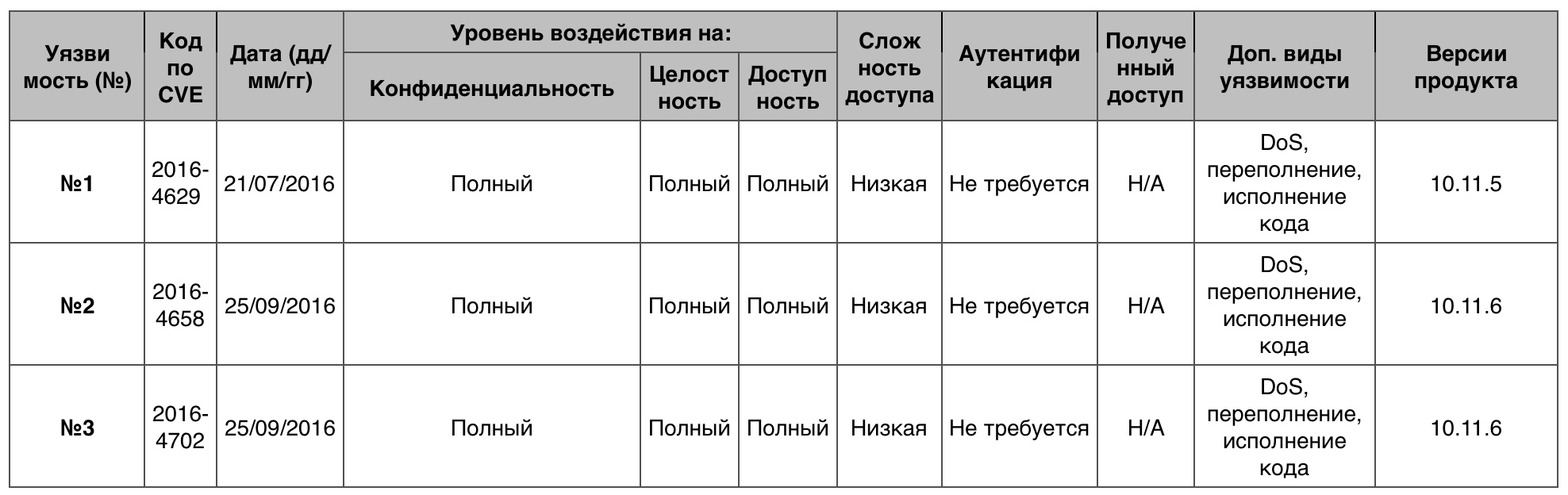
Table of vulnerabilities of the category "memory corruption" in the OS macOS
Access to the information
230 vulnerabilities in total, of which none of them score 10 points.
Vulnerability # 1 (9.4)
Quick Look, while previewing the HTML file, did not prevent the creation of a network request by the plugins, which could open the way to getting information.
Vulnerability # 2 (9.3)
Using the created application in the login window, an attacker could get information, execute code, or lead to DoS.
Vulnerability # 3 (9.3)
Using the created application in the login window, an attacker could get information, execute code, or lead to DoS.
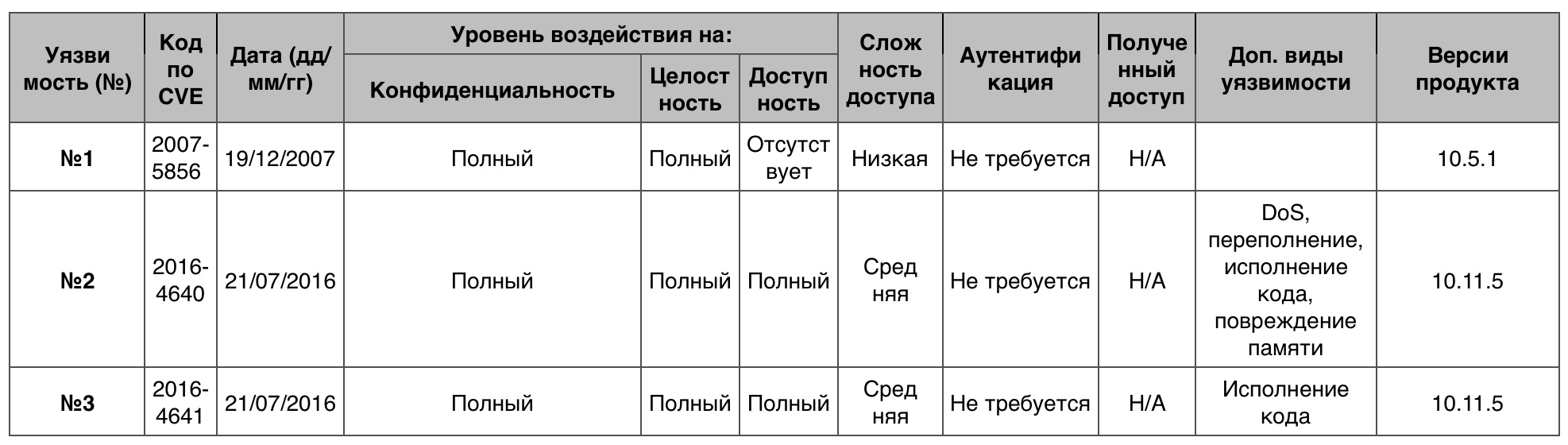
Vulnerability table of the category "Access to Information" in OS MacOS
Privilege increase
5 vulnerabilities out of 161 scored 10 points.
Vulnerability # 1
Graphic drivers provided an opportunity to increase privileges through a 32-bit executable file for the created application.
Vulnerability # 2
The fontd in Apple Type Services (ATS) allowed a local user to get privileges through an unspecified vector.
Vulnerability # 3
The OS kernel gave local users the opportunity to obtain privileges through an unspecified vector.
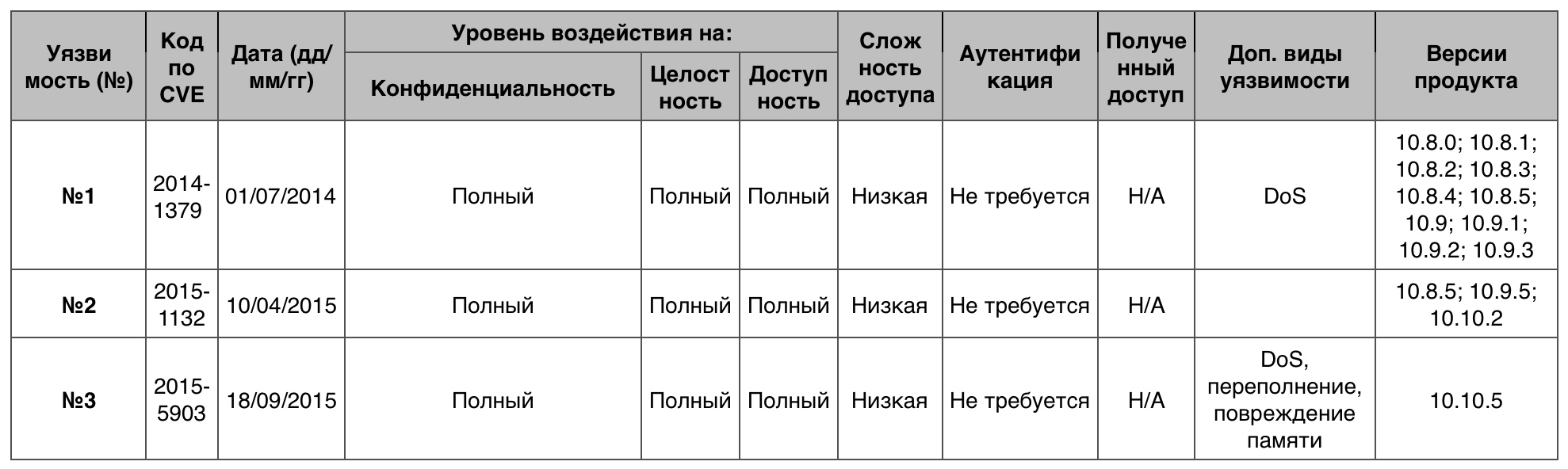
Vulnerability table of the “Privilege escalation” category in macOS
Overflow
691 vulnerabilities of which 10 points earned 45.
Vulnerability # 1
ImageIO allowed a remote hacker to execute arbitrary code or organize DoS through the xStride and yStride he created in the EXR image.
Vulnerability # 2
libxml2 allowed a remote attacker to execute arbitrary code or organize DoS through an XML document created by it.
Vulnerability # 3
Audio in OS X prior to version 10.12 allowed a remote hacker to execute arbitrary code or organize DoS via an unspecified vector.
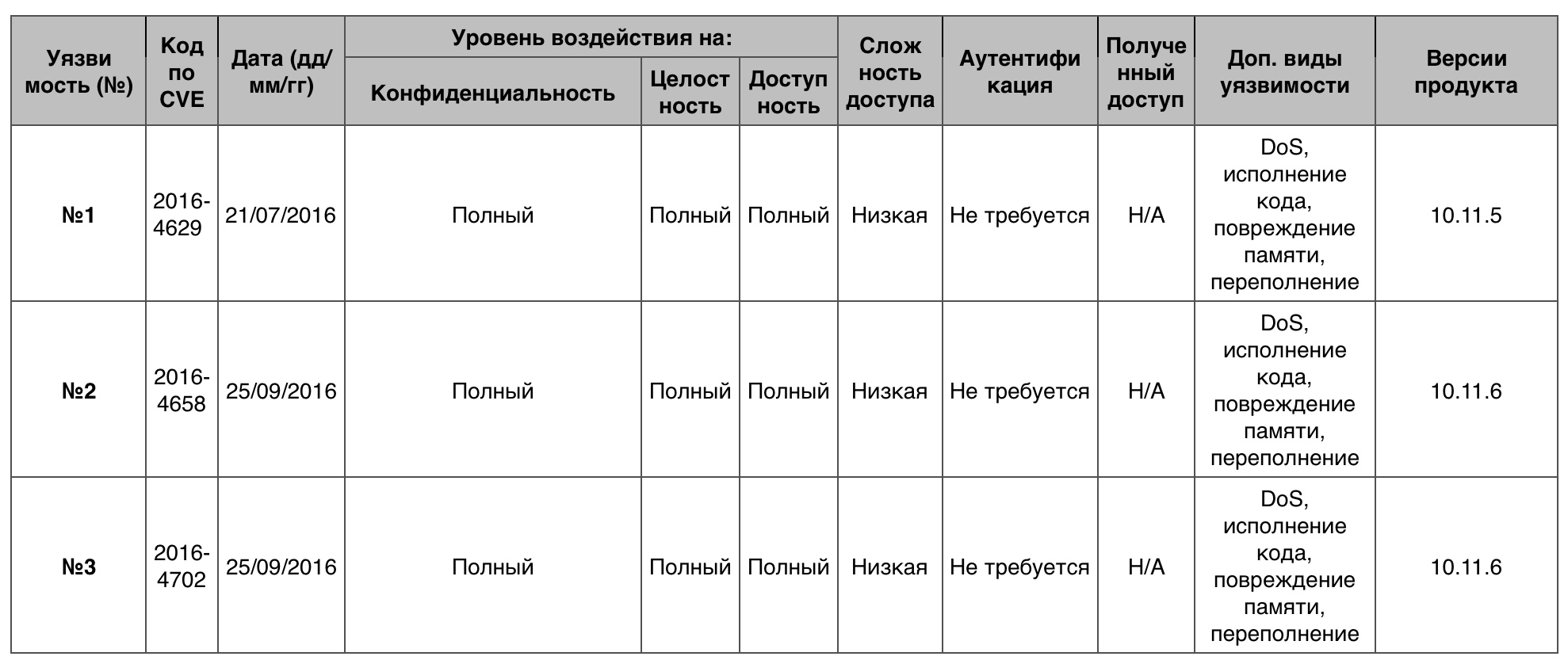
Table of vulnerabilities category "Overflow" in OS macOS
The above data can be interpreted in different ways. However, it is worth being objective. For example, “Access to information” - 230 vulnerabilities, but there are no critical ones, which indicates a decent level of data protection. Of course, it is impossible to judge the security of the OS by the presence of holes. It is worth considering exactly how many instances of these holes were exploited.
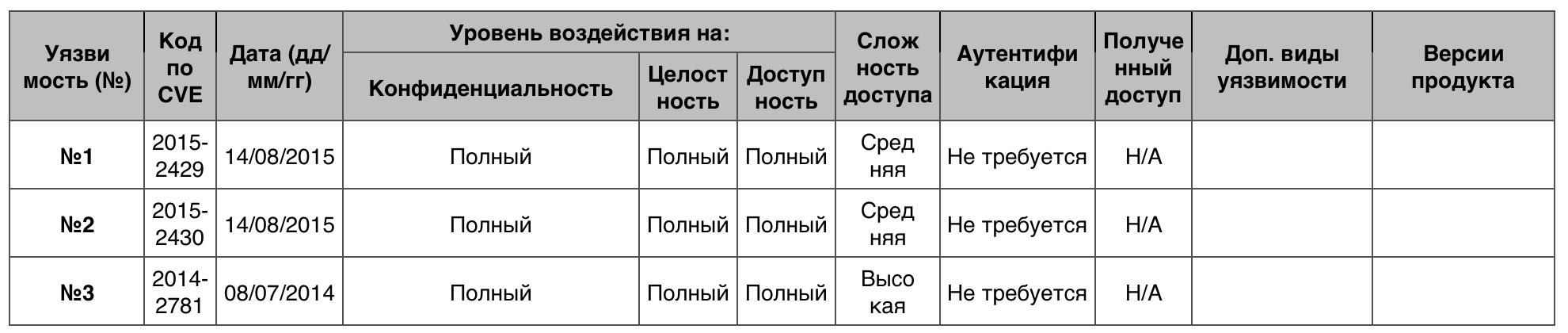
3. Windows Server 2012

Windows Server 2012 is a server operating system from Microsoft, released September 4, 2012. Quite a young and popular OS for servers, provides users with a special service Dynamic Access Control, which improves file-level domain protection and increases folder security.
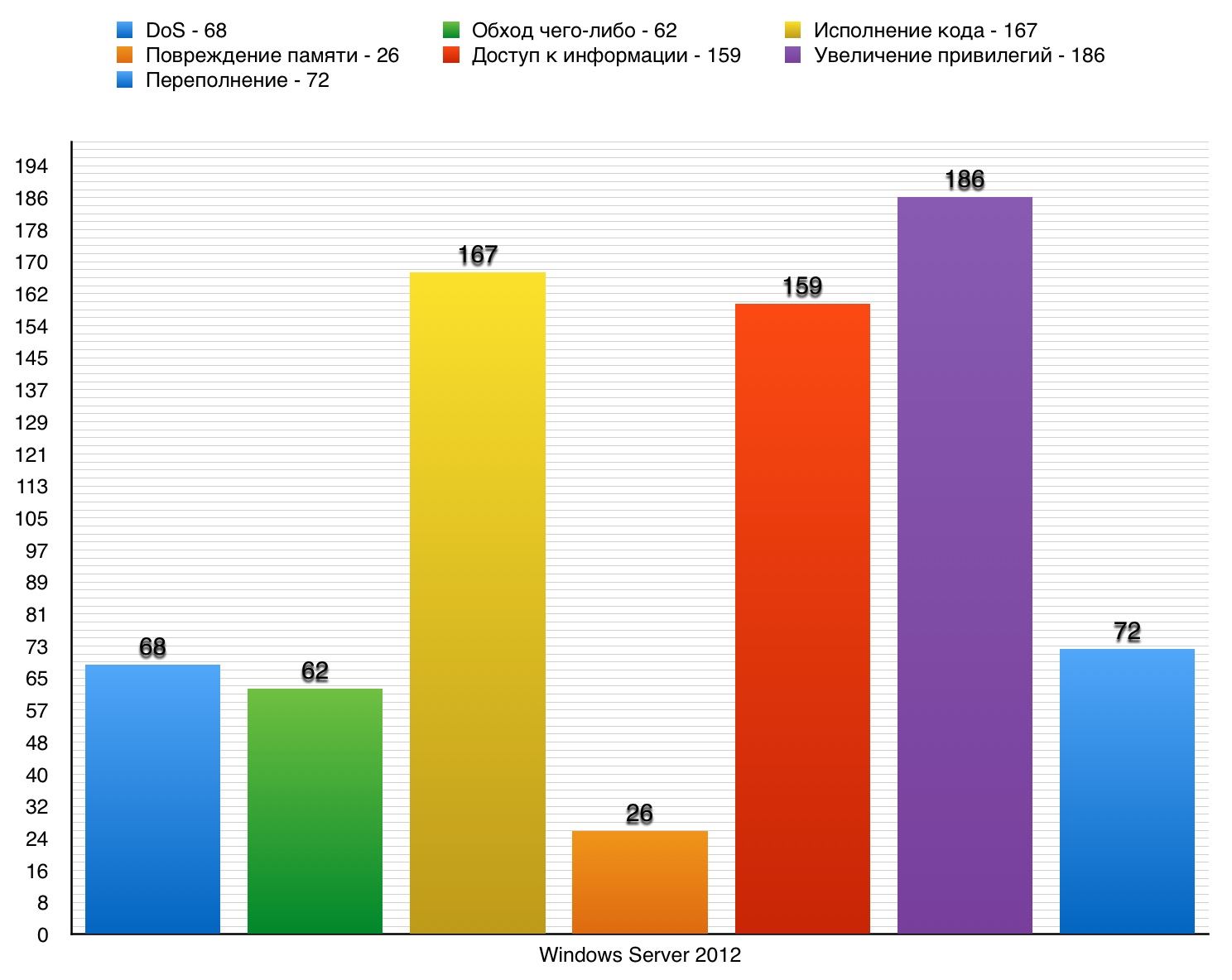
DoS
68 - in total. 10 points - 0.
Vulnerability # 1 (9.3)
The usp10.dll in Uniscribe made it possible to add an entry to the EMF + font file, which made it possible to execute the code or result in a DoS.
Vulnerability # 2 (9.3)
MSXML 3.0 allowed to create DoS through the created XML content.
MSXML - Microsoft XML Core Services.
Vulnerability # 3 (9.3)
The atmfd.dll in the Adobe Type Manager library allowed a remote attacker to arrange DoS through the font he created with OpenType.
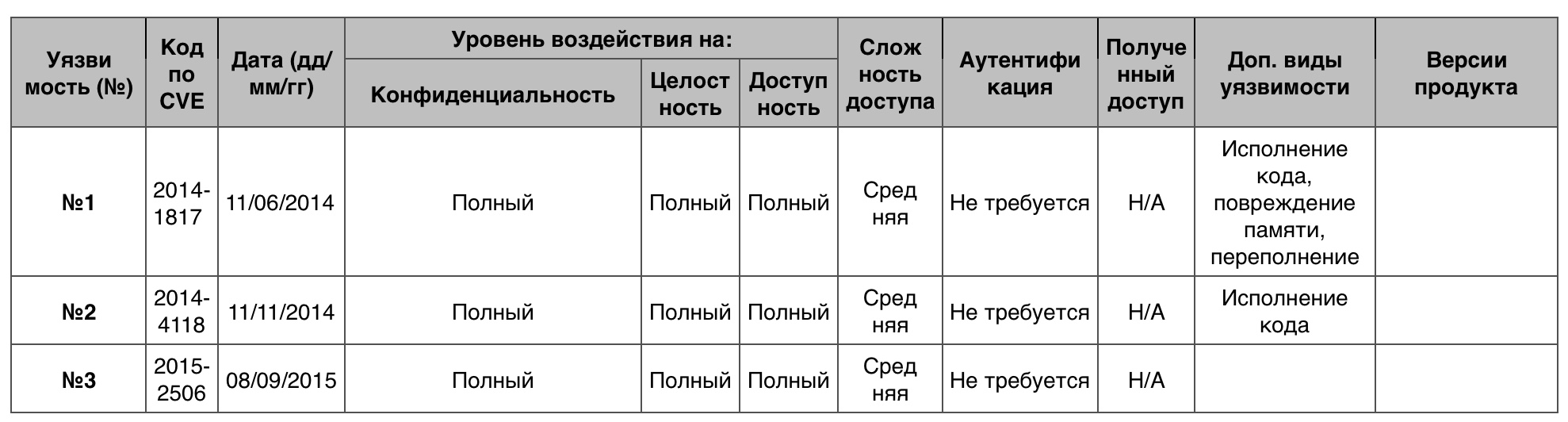
Table of vulnerabilities category "DoS" in Windows Server 2012
Bypassing something
Total - 62. 10 points - 0.
Vulnerability # 1 (9.3)
The OS allowed the hacker to bypass the application sandbox security protocols and perform certain actions in the registry through the application created.
Vulnerability # 2 (9.3)
The OS allowed the hacker to bypass the security protocols of the application sandbox and to perform certain actions in the file system through the application created.
Vulnerability # 3 (7.6)
The OS could not correctly restrict the exchange of keyboard and mouse data between programs at different levels of integrity, which allowed the attacker to bypass access restrictions by gaining control over the low-level process to launch the on-screen keyboard, and then download the created application.
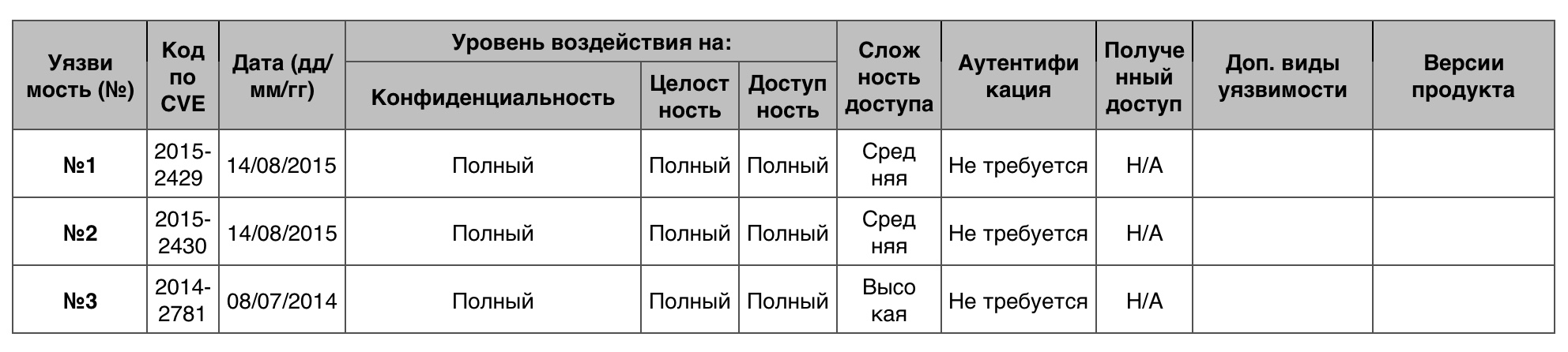
Vulnerability Table "Crawl" category in Windows Server 2012
Code execution
Total - 167. 10 points - 12.
Vulnerability # 1
The OS allowed you to remotely gain control over the system when Windows Search could not cope with the processing of memory objects.
Vulnerability # 2
The OS allowed you to remotely gain control over the system when Windows Search could not cope with the processing of memory objects.
Vulnerability # 3
OS allowed to remotely execute arbitrary code when it could not cope with processing DNS responses.
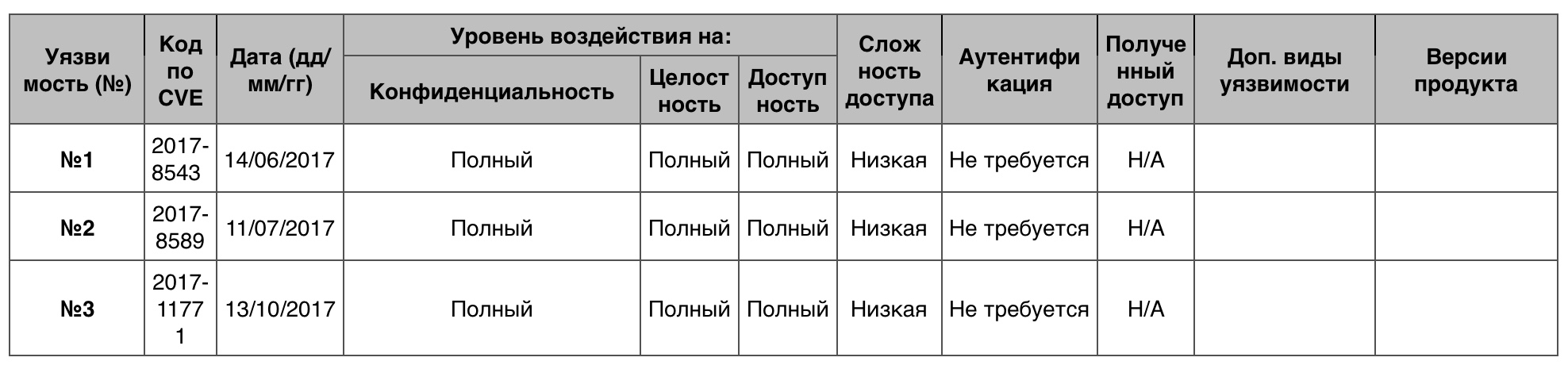
Code Execution Vulnerability Table in Windows Server 2012
Memory damage
Total - 26. 10 points - 0.
Vulnerability # 1 (9.3)
Animation Manager allowed an attacker to execute code through the website created.
Vulnerability # 2 (9.3)
The Media Foundation allowed the attacker to execute the code through the website created.
Vulnerability # 3 (9.3)
The iSNS Server service allowed attackers to send requests through software overflow.
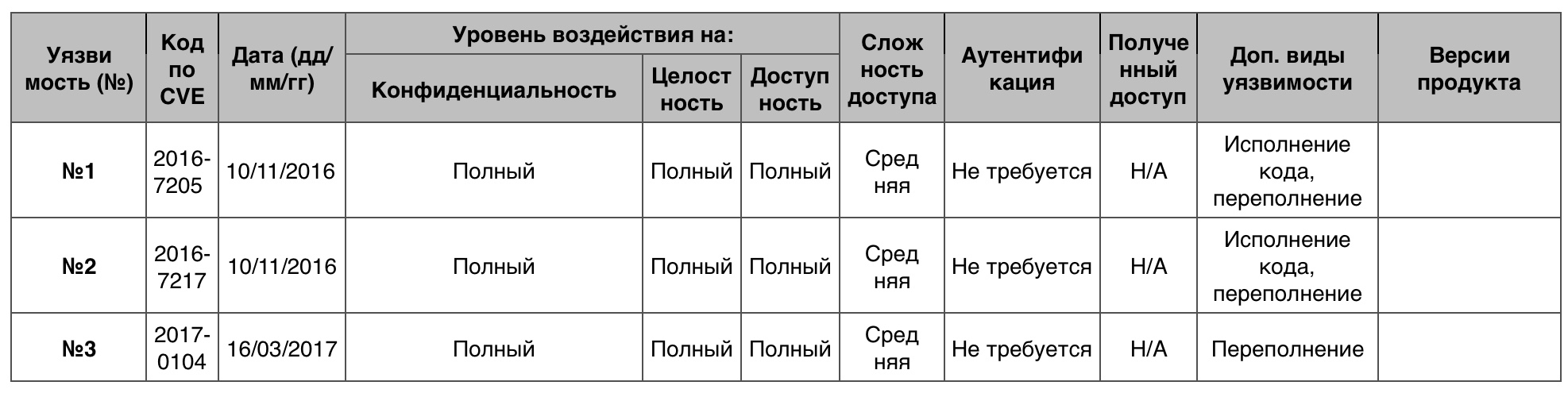
Memory Corruption Vulnerability Table in Windows Server 2012
Access to the information
Total - 159. 10 points - 0.
Vulnerability # 1 (7.2)
Kernel-mode drivers allowed a local authenticated user to execute a specially crafted application for positioning information.
Vulnerability # 2 (6.8)
The implementation of the Group Policy did not distribute passwords correctly, which made it possible to take possession of credentials and gain privileges using access to SYSVOL.
Vulnerability # 3 (6.6)
win32k.sys in the kernel mode drivers made it possible for local users to acquire information from the kernel memory through the application created.

Table of Vulnerabilities in the Access to Information Category in Windows Server 2012
Privilege increase
Total - 186. 10 points - 2.
Vulnerability # 1 (10)
Kernel-mode drivers allowed to increase privileges through a specially created application.
Vulnerability # 2 (10)
The Graphics component in the OS kernel allowed local users to get privileges through the application created.
Vulnerability # 3 (9.3)
The software overflow in Windows Shell allows local users to get privileges through the created briefcase .
Briefcase - briefcase - a tool to automatically synchronize multiple copies of files.

Privilege escalation vulnerability table in Windows Server 2012
Overflow
Total - 72. 10 points - 3.
Vulnerability # 1
OS kernel mode drivers did not properly handle memory objects. which allowed the hacker to remotely execute the code through the font file created by him TrueType.
Vulnerability # 2
The DSA_InsertItem function in Comctl32.dll did not allocate memory properly, allowing a remote attacker to execute code through the generated value in an ASP.NE argument of the web application.
Vulnerability # 3
A buffer overflow in the Telnet service allowed to execute arbitrary code through the created packages.
Vulnerability Table Overflow in Windows Server 2012
Among all the vulnerabilities, the most common are those that lead to an increase in privileges. However, they had no critical consequences. More advanced, with improved security protocols, Windows Server 2012 has become an excellent replacement for Windows Server 2008.
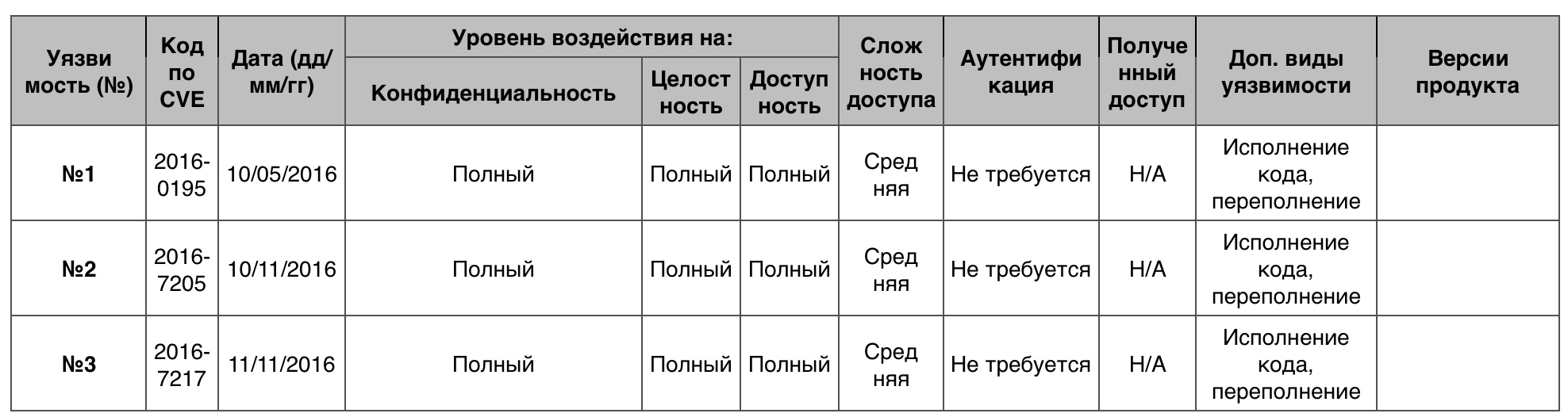
4. Windows 7

Windows 7 is the operating system of the user-defined type of the Windows NT family, released on October 22, 2009. At the moment, the new version of the Windows family of operating systems already exists and is gaining momentum - this is Windows 10. But despite the progress, the seven remain the leaders in popularity, occupying about 25% of the market. If we consider only Microsoft products, then Windows 7, among others, the version (including 8, and 10) takes 40%.
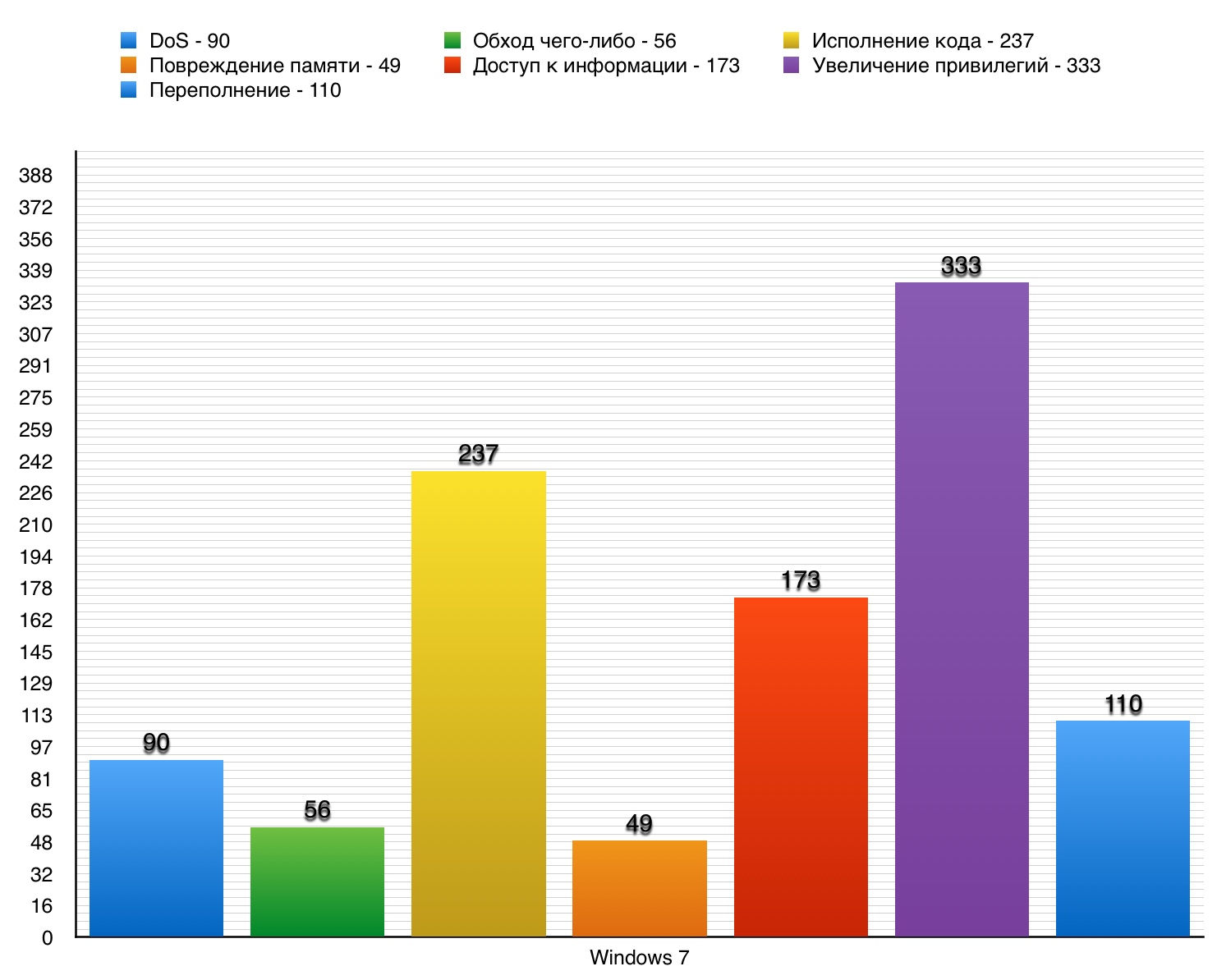
DoS
Total - 90. 10 points - 3.
Vulnerability # 1
The SMB client incorrectly checked the fields in the SMB response records, which allowed SMB servers and attackers to execute the code, lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 2
The SMB client incorrectly checked the fields in the SMB response records, which allowed SMB servers and attackers to execute the code, lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 3
Creating a task for printing through Print Spooler made it possible to arrange DoS.
Table of vulnerabilities category "DoS" in Windows 7
Bypassing something
Total - 56. 10 points - 0.
Vulnerability # 1 (9.3)
The OS, when IMJPDCT.EXE was installed, allowed the remote hacker to bypass the sandbox security protocols through the created PDF document.
Vulnerability # 2 (9.3)
The OS allowed the hacker to bypass the application sandbox security protocols and perform certain actions in the registry through the application created.
Vulnerability # 3 (9.3)
The OS allowed the hacker to bypass the security protocols of the application sandbox and to perform certain actions in the file system through the application created.
Vulnerability Table "Crawl" category in Windows 7
Code execution
Total - 237. 10 points - 23.
Vulnerability # 1
The OS allowed remotely execute arbitrary code due to how Windows Search processed memory objects.
Vulnerability # 2
The OS allowed the remote execution of the code when it could not cope with the processing of DNS responses.
Vulnerability # 3
Microsoft .NET Framework 1.0 SP3, 1.1 SP1 and 2.0 SP1 incorrectly checked .NET code, which allowed a remote attacker to access the memory stack and execute arbitrary code through a browser application created by XAML or an ASP.NET application or .NET Framework application.
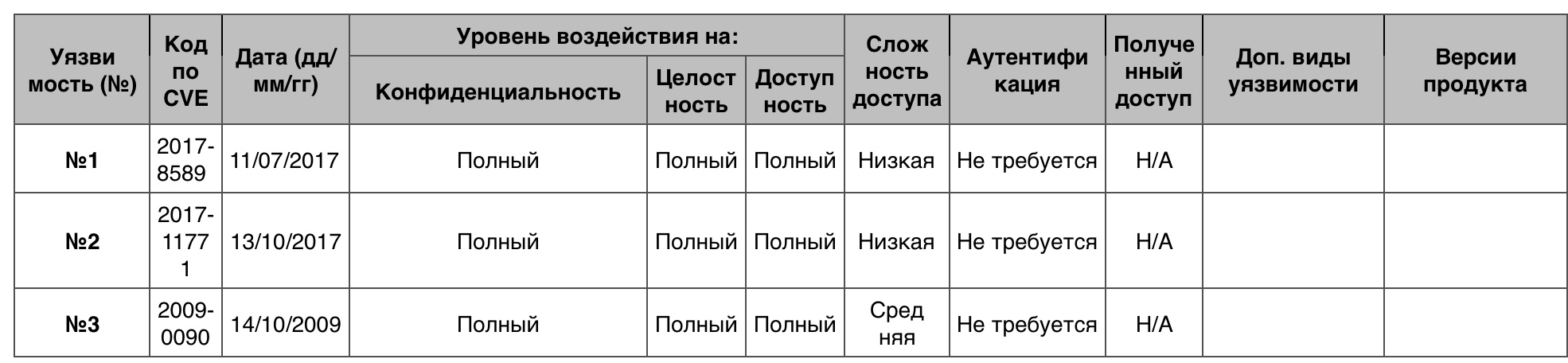
Code Execution Vulnerability Table for Windows 7
Memory damage
Total - 49. 10 points - 3.
Vulnerability # 1
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 2
The SMB client in Microsoft Windows Server 2008 R2 did not correctly check the fields in the SMB response records, which allowed SMB servers and attackers to execute code and lead to DoS through the created SMBv1 or SMBv2 response.
Vulnerability # 3
Creating a task for printing through Print Spooler opened the possibility to damage the memory.
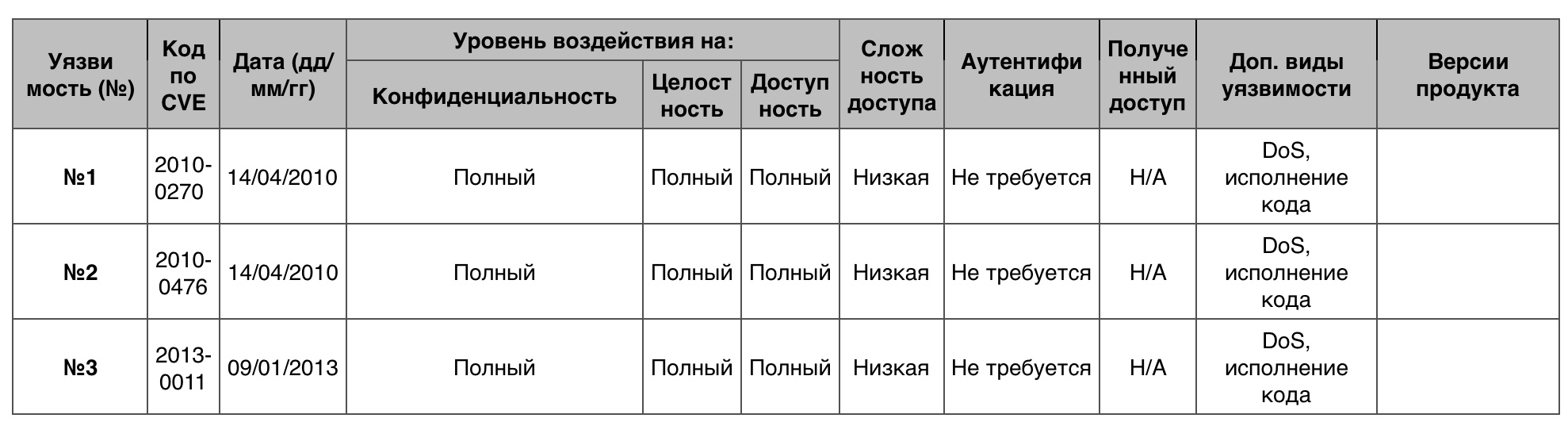
Table of vulnerabilities in the category "memory corruption" in Windows 7
Access to the information
Total - 173. 10 points - 0.
Vulnerability # 1 (7.2)
OS kernel mode drivers allowed a local authenticated user to execute a specially crafted application for retrieving information.
Vulnerability # 2 (6.8)
Group Policy ( ) , , SYSVOL.
№3 (6.6)
win32k.sys .
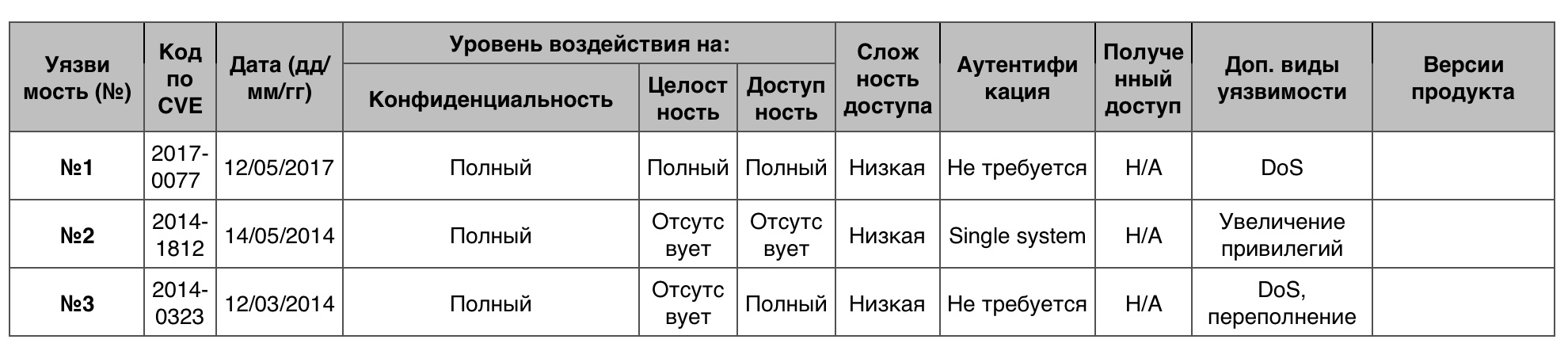
« » Windows 7
— 333. 10 — 2.
№1 (10)
.
№2 (10)
Graphics .
№3 (9.3)
SMB SMB SMB .

« » Windows 7
— 110. 10 — 6.
№1
Print Spooler .
№2
DSA_InsertItem Comctl32.dll , ASP.NE -.
№3
Telnet .
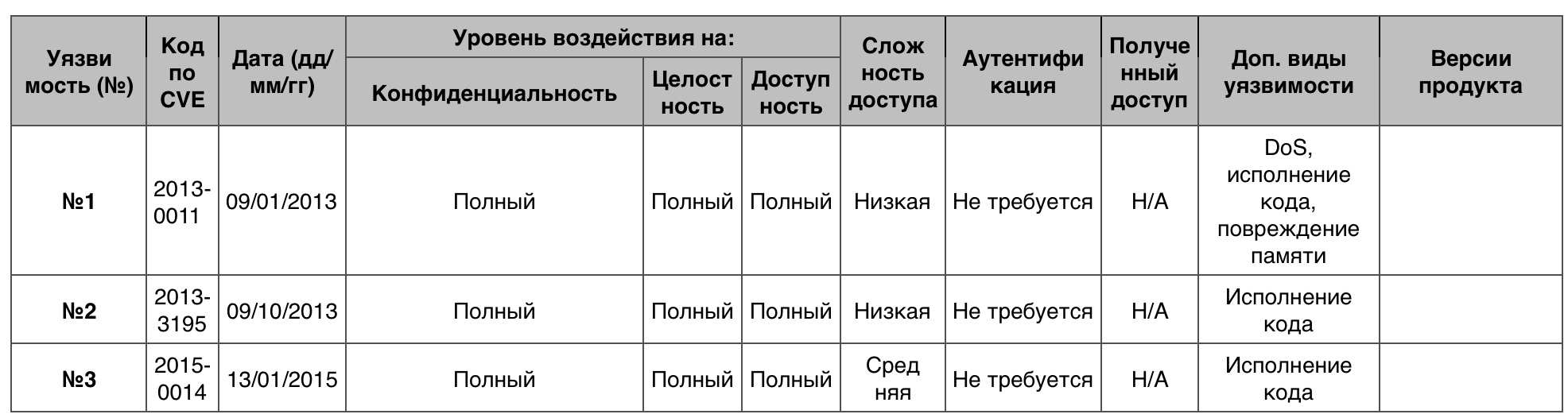
«» Windows 7
Windows 7 . , , .
5. Windows 8.1

Windows 8.1 — Windows NT, 17 2013. Windows 8 Windows 10.
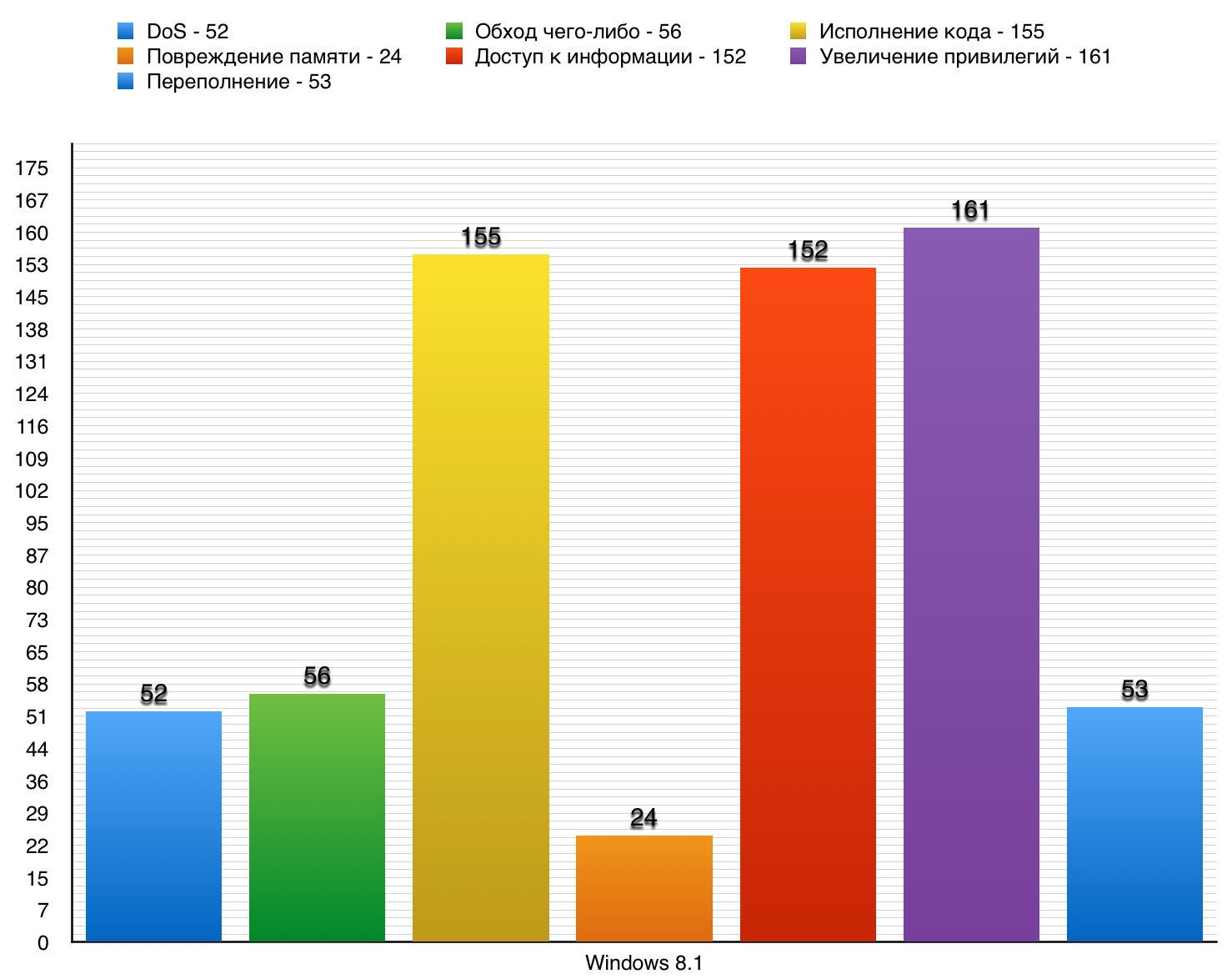
DoS
— 52. 10 — 0.
№1 (9.3)
usp10.dll Uniscribe EMF+ , DoS.
№2 (9.3)
MSXML 3.0 XML DoS.
№3 (9.3)
atmfd.dll Adobe Type Manager DoS OpenType .
«DoS» Windows 8.1
-
56 , 0 10 .
№1 (9.3)
.
№2 (9.3)
.
№3 (7.6)
, , , .
« -» Windows 8.1
155 7 10 .
№1
, Windows Search .
№2
, Windows Search .
№3
, DNS .

« » Windows 8.1
24, 10 .
№1 (9.3)
Imaging .
№2 (9.3)
Animation Manager -.
№3 (9.3)
Media Foundation -.
« » Windows 8.1
152 . 0 10 .
№1 (7.2)
.
№2 (6.8)
Group Policy ( ) , , SYSVOL.
№3 (6.6)
win32k.sys .
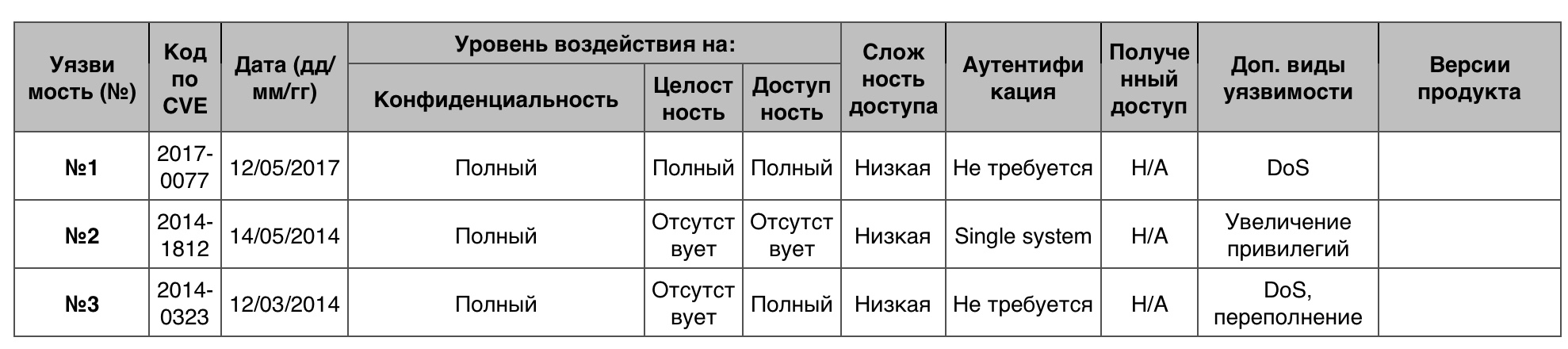
« » Windows 8.1
— 161. 10 — 2.
№1
.
№2
Graphics .
№3 (9.3)
.
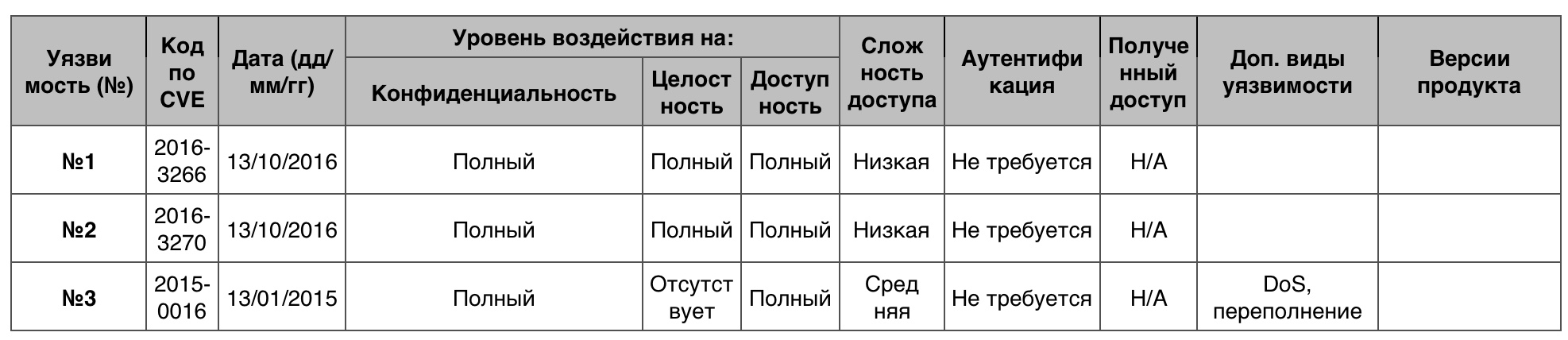
« » Windows 8.1
— 53. 10 — 1.
№1
Telnet .
№2 (9.3)
icardie.dll DoS -, Internet Explorer.
№3 (9.3)
GDI DoS Windows Write (.wri), WordPad-.
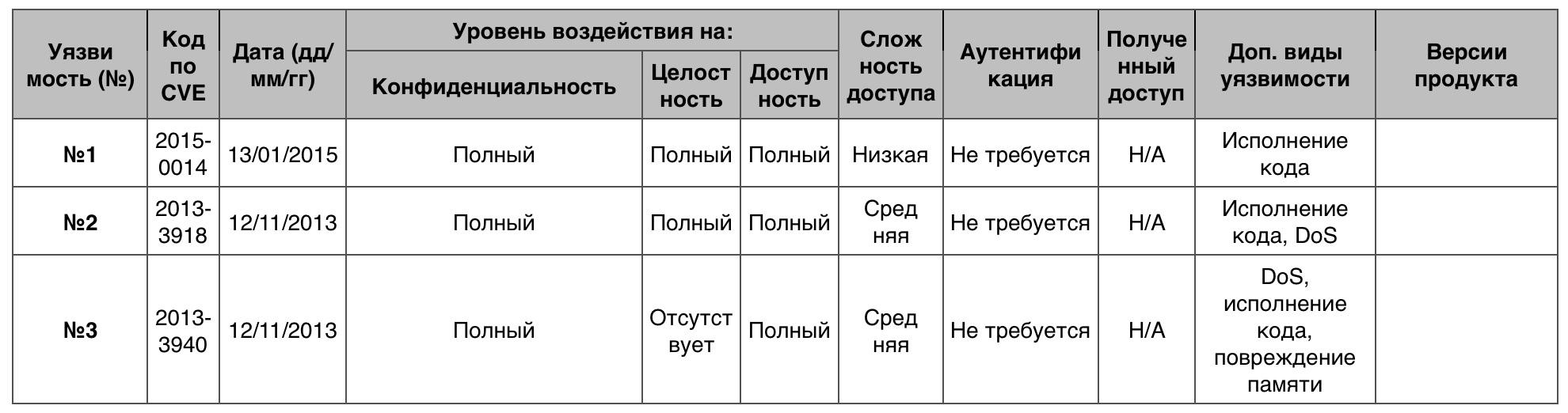
«» Windows 8.1
. , Windows, « » « ». , — , .
— . , , . - . , , . — .
Windows (, , ) .
.
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
Source: https://habr.com/ru/post/370987/
All Articles