Malicious software that has gone down in history. Part I

I think computer viruses should be considered as a form of life. It says a lot about human nature: the only form of life that we have created to date is only destruction. We create life in the image and likeness of ours.Stephen Hawking
If there are rules, then there will definitely be someone who wants to break them. The same goes for the creators of malware. Some of them want to profit, others just show their talent to the world. Anyway, malware has become an integral part of the IT sphere. Their species diversity is amazing. Some are virtually harmless, while others suffer billions in losses for government agencies and private companies. In this article we will get acquainted with the most outstanding and famous malware in the history of mankind, starting with the very first, in chronological order.
Brain - 1986
')
By most accounts, Brain is the first virus on the PC. However, unlike his fellows, he carried almost no harm.
Two brothers, Bazit and Amjad Farouk Alvi, were involved in the development and implementation of medical software in Lahore, Pakistan. They are very worried about the issue of computer piracy, that is why they created Brain.

The computer was infected in the following way. A copy of the virus was written to the boot sector of the floppy disk, the old information was transferred to another sector and marked as damaged. After that, the following message was displayed in the boot sector:
Welcome to the Dungeon © 1986 Basit & Amjads (pvt) Ltd VIRUS_SHOE RECORD V9.0 Dedicated to you today - Thanks GOODNESS !!! BEWARE OF THE er..VIRUS: this program is catching program following these messages .... $ # @% $ @ !!
Because of the virus, the floppy disk performance slowed down, and DOS lost access to 7 kilobytes of memory. However, Brain contained a built-in check of hard disk partitions, which did not allow it to infect data, thereby preserving it.
In the source code of the virus, it was possible to find information with the names of its creators, as well as their address and telephone number:
Welcome to the Dungeon 1986 Basit & Amjads (pvt). BRAIN COMPUTER SERVICES 730 NIZAM BLOCK ALLAMA IQBAL TOWN LAHORE-PAKISTAN PHONE: 430791,443248,280530. Beware of this VIRUS ... Contact us for vaccination ...
The spread of the Brain virus was impressive. Within a few weeks, calls to the Alvi brothers' number began to receive calls demanding that the virus be removed from the infected PC. There were so many calls that the phone lines had to be turned off.
Now the Alvi brothers head one of the largest telecommunications companies in Pakistan with the very nostalgic name Brain Telecommunications.
Stoned - 1987
Another representative of viruses with extremely minor consequences. The essence of the virus was that, with a probability of 1 to 8, the following message will appear on the PC screen: “ Your PC is now Stoned! Legalize Marijuana .
The program was written by a student from Wellington, New Zealand. And it most likely worked exclusively with IBM PC 360KB diskettes, since the virus worked with IBM AT 1.2MB diskettes problematically, and on systems with more than 96 files, the virus did not load at all. PCs were usually infected when booting from an infected floppy. When a floppy disk was connected to an infected computer, it was also infected.
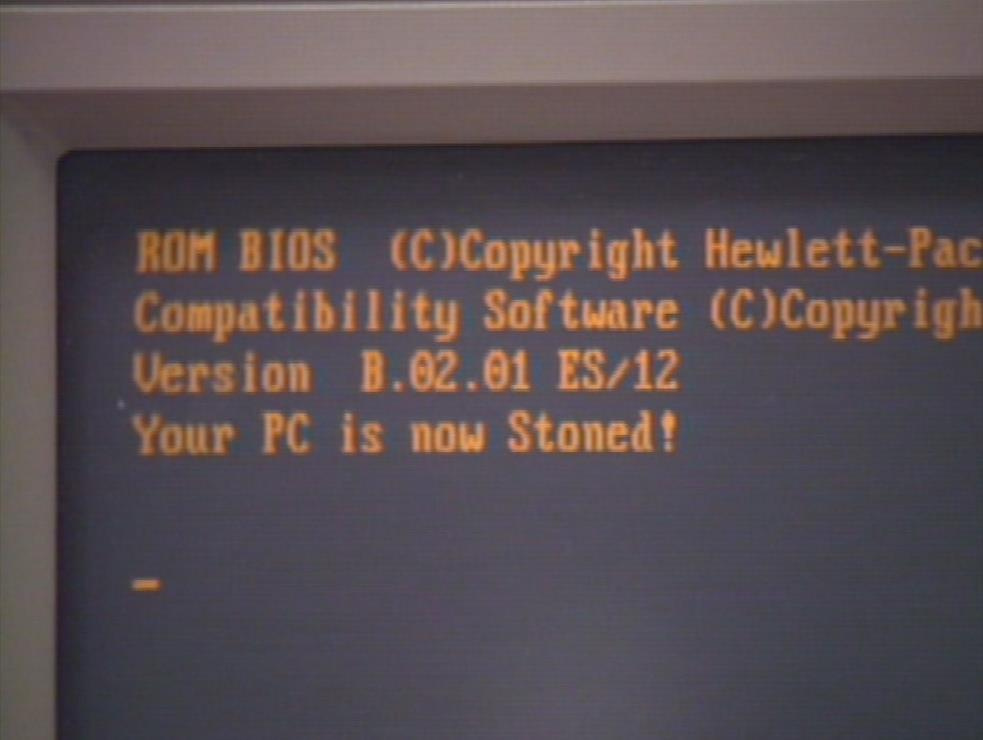
The simplicity of this virus allowed even a person without any specific knowledge to reprogram it, for example, by changing the text of the message.
Known variants of the Stoned virus:
- Bloody! Jun. 4, 1989 (on this day, protests on Tiananmen Square in China were brutally dispersed by the authorities);
- The Swedish Disaster;
- Manitoba (does not have an activation mode and does not save the original boot sector on a diskette, overwriting it; it wins 2.88MB EHD diskettes);
- NoInt (stops programs attempting to track it, causing read errors if the computer tries to access the partition table; reduces the available memory by 2 kB);
- Flame, Stamford (used 1 kB of DOS memory; memorized the month when the system was infected, when the month changed, displayed a colorful flame on the screen and re-recorded the master boot record);
- Angelina (the virus gave the message "Greetings from ANGELINA !!! / by Garfield / Zielona Gora")
Form - 1990
A virus from Switzerland that infected the boot sector instead of the master boot record. When the computer was booted from the infected sector, the Form became resident, capturing the interrupt vector table. Further, the original boot sector (in which the virus was hiding) was marked as faulty. The virus infects any media that has interacted with the infected computer.
Form is also remembered for some unusual symptoms, including:
- consumed 2KB of memory, while the DOS MEM command indicated that this memory was not available;
- On floppy disks, there were 2 bad sectors (1 KV);
- It was also possible to unearth the following text among the virus files: “The FORM-Virus sends this text. FORM doesn't destroy data! Don't panic! F * ckings go to Corinne. ";
- Form considered DOS FAT to be the active partition; if this was not the case (for example, in Windows NT), the virus overwritten the partition, which resulted in complete data loss;
- And the most unusual symptom - on the 18th of every month, there were “clicking” sounds when you press the keyboard keys
Michelangelo - 1992
The virus was first noticed on February 4, 1991 in Australia, however, it was widely publicized only in 1992. Michelangelo is another representative of viruses that work in the boot sector at the BIOS level.
What did the virus do? Every March 6 (the birthday of the great Renaissance artist Michelangelo Buonarroti), he rewritten the first hundred sectors on the hard disk to zero. The PC user data was still on the hard drive, but it was extremely difficult to get it from there. Despite the fact that Michelangelo was programmed to work in the DOS OS, it could easily disrupt other OSs as well, since it infected the main boot record of the hard disk. Any media connected to an infected PC was instantly infected.
When Michelangelo began to gain "popularity", many experts, including the founder of the antivirus company, John McAfee, announced they had infected millions of machines. However, on March 6, 1992 there were recorded cases of infection in the range of 10,000-20000. The anti-malignant software advice was also funny - just do not turn on the computer on March 6 or transfer the date of March 5 to the seventh, thereby skipping the sixth.
VCL - 1992
VCL is not a virus, but a whole program for creating viruses. Created her Nowhere Man from a group of hackers NuKE. VCL had a standard window interface and worked on the MS-DOS platform. Among the functions of the program you could choose:
- type of victim files;
- the possibility of self-encryption of the virus;
- the presence of anti-debug code;
- internal text strings;
- one of 10 effects that occur when the virus is activated;
- distribution method
However, unfortunately for Nowhere Man, the viruses released by the VCL were extremely primitive and did not bear much damage, and besides, they were easy to detect and eliminate.
Monkey - 1993
A distant relative of the virus Stoned, Monkey integrating f files and spreading quickly. Being an early version of the rootkit, the virus blocked booting from a floppy disk, and if improperly eliminated it could block any download at all.
Concept - 1995
The first computer virus, developed in the macro language (hereinafter referred to as such viruses, called macro viruses), infected Microsoft Word files. It has become the most common virus, because it could infect any operating system that could run Word.
Happy99 - 1999
The harmless holiday worm was first discovered on January 20, 1999. Happy99 is considered the first worm and the first malware to spread via email. It was written by a Frenchman under the nickname Spanska.

Happy99 spread via e-mail and Usenet (computer network for communication and file transfer). In the case of opening a worm file, an animated firework and the inscription " Happy New Year 1999 " appeared.
Happy99 changed Winsock, giving itself the opportunity to spread further. The infected machine sent this worm to everyone who was on the user's email list. For distribution, the worm used port 25 or port 119 if the first one was closed. Happy99 automatically activated when you restart your computer.
Melissa - 1999
Another macro virus with colossal consequences both for PC users, the state, and for the one who distributed it.

Spanska words about author Melissa
The virus was written by a certain Kwyjibo. But David L. Smith released him on March 26, 1999. Melissa infects MS Word files and spreads by sending itself to everyone who is listed in the user's email address book. In addition, the virus could also send the files themselves, thereby violating the confidentiality of their owner. Having quickly spread, the Melissa virus caused a damage of $ 80 million. This does not go unpunished. Using the UUID (software identification method) David L. Smith was calculated and presented before the court. He was sentenced to 10 years in prison and fined $ 5,000.
Loveletter - 2000
Three secret words, hacked millions of computers running Windows around the world. The worm spread as an attached file “LOVE-LETTER-FOR-YOU.TXT.vbs” in an email with the subject “ILoveYou”. It was enough to open this file as the user's machine was infected. The worm sent copies of itself to all contacts from the Microsoft Outlook address book and overwritten certain file types. Created LOVE-LETTER-FOR-YOU.HTM files in the Windows system directory and distributed via IRC channels.
The whole trick was the manipulation of people. The fact is that the file extension in Windows was hidden by default, that is, the victim saw the following: LOVE-LETTER-FOR-YOU.TXT (without .vbs), considering it as a harmless text file and opening it. This gave the malware a head start.
As for the creators of this creation, they were two young guys from the Philippines - Reonel Ramones and Onel de Guzmán. For the creation and distribution of the virus, the guys were arrested by the NBI (the National Bureau of Investigation of the Philippines). The trial was difficult and even funny, since the Filipino laws did not contain penalties for creating malicious SPs. First, the suspects wanted to attribute credit card fraud, then damage to property. However, the evidence was not enough, and Reonel Ramones and Onel de Guzmán were released.
In 2002, their creation was included in the Guinness Book of Records as the most dangerous computer virus of all time (the global economy’s losses from ILoveYou were approximately $ 5.5 billion).
Code Red - 2001
In July 2001, a group of eEye Digital Security employees (Mark Maifret, Ryan Perm and Riley Hassel) uncovered a computer worm called Code Red (at the time of the discovery, the guys just drank a drink called Code Red Mountain Dew). Already on July 19, the number of infected machines was about 360,000.
By spreading to the worm, there was a vulnerability in the Microsoft IIS indexing utility, and it was based on a buffer overflow. The worm did not check for IIS on the machine (potential victim), but simply forwarded the exploit packets to a random IP address. This method was very primitive and extremely noticeable, however, it gave its fruits. Because even the Apache logs contained the following:
GET /default.ida?NNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNN
% u9090% u6858% ucbd3% u7801% u9090% u6858% ucbd3% u7801
% u9090% u6858% ucbd3% u7801% u9090% u9090% u8190% u00c3
% u0003% u8b00% u531b% u53ff% u0078% u0000% u00 = a HTTP / 1.0
Code Red cyclically during the month did the following:
Day 1-19
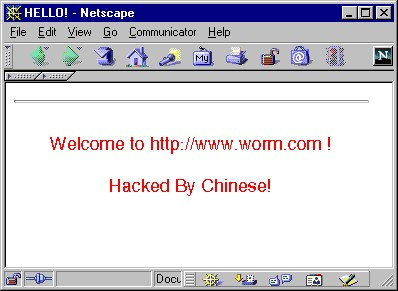
- The infected site issued the following message - “HELLO! Welcome to w * w.worm.c * m! Hacked By Chinese! ”
- generated multiple IP addresses, thereby trying to spread
Day 20-27
- A massive DoS attack on some IP addresses (including the White House)
Day 28 - the end of the month
- Code Red idle
The source of the spread of the worm is the city of Makati (Philippines). But this is inaccurate information.
Slammer - 2003
This computer worm literally burst into the Internet, infecting more than 75,000 cars in the first 10 minutes of its existence. Slammer “organized” DoS attacks on some Internet hosts and slowed down Internet traffic altogether.
Slammer technology, like malware, was very simple and was based on the flaws in Microsoft's SQL and Desktop Engine. Half a year before the spread of the worm, patch MS02-039 was released, which was supposed to close all holes and eliminate vulnerabilities, but not all computers have downloaded this patch. This provided a loophole for the spread of Slammer.

The worm, consisting of a pair of lines of code, just generated a random IP and sent itself to it. If the selected IP belonged to a device with unpatched Microsoft's SQL, the worm infected it and spread further through this device.
Slammer caused a real chain reaction. When too much traffic passes through the router, it either slows down or interrupts the transmission. However, the routers spent by the worm simply failed. Other routers received some kind of notification of this and passed it to other routers. The stream of notifications about the update of the routing tables led to the failure of the new routers, which, when restarted, started to update their status in the table again. All this became possible also because Slammer occupied only 376 bytes and could fit in one single packet. As they say, small, yes deleted.
Sobig - 2003
A hybrid computer worm and trojan, Sobig has existed in several forms since its inception. Sobig.F, first recorded on August 19, 2003, acquired the biggest publicity.
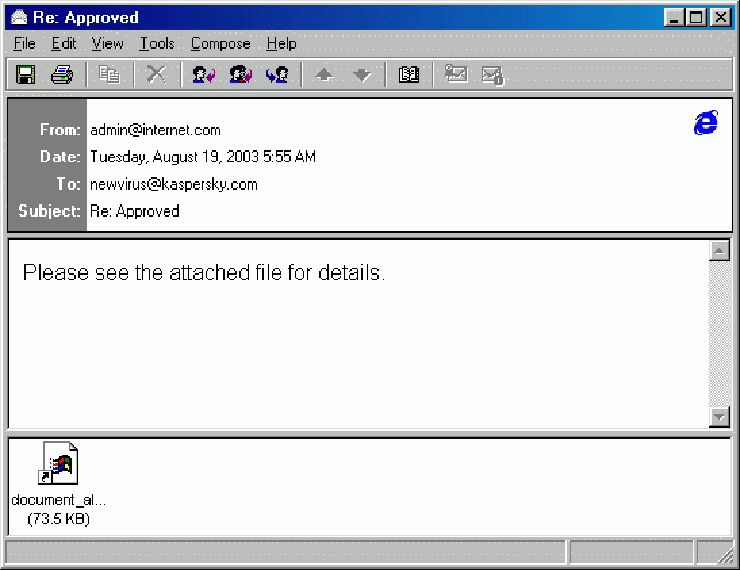
The worm was an email with an attached file. The subject of the letter could be different (Re: Approved; Re: Details; Re: Re: My details; Re: Thank you !; Re: That movie; Re: Wicked screensaver; Re: Your application; Thank you !; Your details). The letter also contained the following text: “See the attached file for details” or “See the attached file for details”.
The attached file could also be distinguished by name (application.pif; details.pif; document_9446.pif; document_all.pif; movie0045.pif; thank_you.pif; your_details.pif; your_document.pif; wicked_scr.scr). When opening one of these files, the worm replicated itself using its own SMTP agent. Then he collected all possible email addresses that he searched for by scanning files (such extensions: .dbx; .eml; .hlp; .htm; .html; .mht; .wab; .txt) on the infected computer. And, of course, spread further.
Sobig.F was programmed to establish a connection with 20 IP addresses via UDP port 8998 to install some software or self-update. Later it turned out that this software was a WinGate proxy server (often used as a backdoor to spread spam).
Already on September 10, 2003, Sobig.F was deactivated. But Microsoft was not satisfied with this completion of the story, and the company put up a reward of $ 250,000 to anyone who provided any information that would help to capture the creator of Sobig. But to this day it has not happened.
Fizzer - 2003
He became the most top virus (more precisely a worm) in 2003. Fizzer got on the computer via e-mail or through the shared folder KaZaA. The subject of the letter could be different, as well as the language in which it was written, the text is short, and the attached file of the .com, .exe, pif or .scr extension.
When extracting from a letter, Fizzer copied itself to the Windows folder, creating several files there: iservc.exe, initbak.dat, ProgOp.exe, iservc.dll, data1-2.cab, iservc.dat, Uninstall.pky and upd.bin . The worm also added iservc.exe to the launch key of the local machine, for activation at the moment the PC was turned on. Each time a text file was opened, the ProgOp.exe and iservc.exe processes were launched. What is even more surprising is that Fizzer monitored and stopped any processes containing such lines: NAV, SCAN, AVP, TASKM, VIRUS, F-PROT, VSHW, ANTIV, VSS and NMAIN. And all in order not to be detected.
Fizzer had several useful functions for a hacker. First, he connected to the IRC servers (irc.awesomechat.net, irc.blueshadownet.org, irc.chatlands.org, irc.darkmyst.org, irc.hemmet.chalmers.se, irc.exodusirc.net and irc. mirc.gr) to wait for commands; secondly, created a fake name in the AOL Instant Messenger chat; and third, it worked as an HTTP server on port 81, using ports 2018, 2019, 2020 and 2021 for additional backdoor functions.
Despite its versatility, Fizzer didn’t bring much harm, especially since the need for human involvement for further infection (opening a file in a letter) did not allow the worm to quickly crawl around the world. It was concentrated mainly in China and Hong Kong, but was also noticed in Europe and the USA.
SDBot - 2003
A computer worm that gives a hacker complete remote access to a victim’s computer. The connection is established using the IRC (Internet Relay Chat) protocol. Worm distribution methods are e-mail, shared network access folders, or direct transfer from computer to computer.
In addition to providing access to the victim's files, SDBot records information about logins and passwords, also reads the identification data of the victim on the Internet.
The advantage of SDBot is the ego stealth, as it runs in the background. But many modern antiviruses can easily detect and eliminate it.
Cabir - 2004
The world's first worm, capable of infecting mobile phones and spread via Bluetooth, and the first on the Symbian OS.
Cabir activation method is completely dependent on the decisions of the person. The phone can fix the Bluetooth connection that the person must accept. After that, the worm file is downloaded. Next, the malware asks the user if he wants to launch it. In the event of a launch, the worm displays the message “Caribe - VZ / 29a” or “Caribe” on the screen. In the \ system \ apps directory, the worm creates a folder called caribe and installs the files caribe.app, flo.mdl and caribe.rsc. A folder caribesecuritymanager is also created in the \ system \ symbiansecuredata directory. When you run caribe.app, it installs the caribe.app, caribe.rsc and caribe.sis files. And the file flo.mdl is placed in the \ system \ recogs folder.
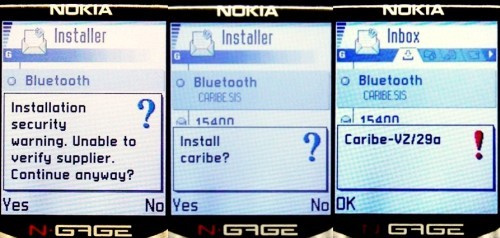
Each phone switch on when Cabir starts searching for an active Bluetooth connection and, having found one, copies itself to another phone. This process can be repeated only if the infected phone is restarted. In this case, the transmission via Bluetooth will still be, even if the user has disabled it in the settings.
During the World Championships in Athletics in August 2004, many telephones were infected. This is due to the large crowding of people in the stadiums. A total of Cabir infected 115,000 phones.
It is believed that the author of this worm is a hacker Valtezz from group 29A. In June 2007, a man was arrested in Valencia (Spain), accused of creating such malware. But it is still not known whether the detainee was Valtezz.
Mydoom - 2004
One of the most scandalous and powerful computer worms of its time. The worm spread in a way we already knew - in the form of an e-mail with a message about an alleged error: “Error”, “Mail Delivery System”, “Test” or “Mail Transaction Failed”. Having opened the file attached to the letter, the victim gave the worm access to the address book, and the latter spread further. He also copied himself to the Kazaa application share (file sharing).

Initially, the first version of the worm named Mydoom.A should have done the following:
- create a backdoor on port 3127 / tcp for remote access to an infected PC (by placing its SHIMGAPI.DLL file in the system32 folder, launching it as a child process of Windows Explorer)
- DoS attack on SCO Group, scheduled for February 1, 2004
Mydoom.V, the second version of the worm, possessed the same features plus attacked Microsoft sites and popular antiviruses.
First seen on January 26, 2004, Mydoom slowed down overall Internet traffic by 10% that day, and the average download speed for web pages decreased by 50%. The worm suffered most from the work of the SCO Group. About a quarter of Mydoom-infected hosts attacked the company's website with a flood. Some experts, including representatives of the SCO Group, began to accuse Linux of developing a worm. Allegedly, this attack on the company was revenge for the lawsuits that the SCO Group launched against Linux. However, evidence of this was not found. For the day of the DoS attack (January 31), which was mentioned earlier, the SCO Group withdrew its website www.sco.com from the DNS. Therefore, it is still not known whether the company's website was really subject to attack or not. February 3, DoS fell on Microsoft. The company has prepared for this. An alternative non-attackable site, information.microsoft.com, was proposed to users. Despite fears, the attack power on the main Microsoft site was minimal and his work was not interrupted.
Both Microsoft and the SCO Group promised $ 250,000 for any information about the developer of the Mydoom worm.
Sasser - 2004
A computer worm that uses buffer overflow in LSASS (Local Security Authority Subsystem Service). To search for victims, the worm scanned a wide range of IP addresses, then through port 445 or 139 penetrated the PC. The main feature of Sasser was that to activate it did not need the participation of the user of the infected computer.
Many companies and institutions suffered from the worm’s actions (Delta Air Lines, AFP News Agency, Nordic Insurance Company, British Coast Guard, Goldman Sachs, Deutsche Post, European Commission, even the Department of Roentgenology at Lund University Hospital). Microsoft (as is customary in their case) has announced a charge of $ 250,000 for information regarding the creator of Sasser.
The author of this “masterpiece” was a 17-year-old German named Sven Yashan. He was detained and sentenced to 1 year and 9 months of imprisonment with a probation period of 3 years, plus 30 hours of community service. Currently, Sven has become a “white” hacker (testing computer system security) and a cyber security consultant.
Haxdoor - 2005
Trojan that initiated the formation of a whole family of Trojans called Win32 / Haxdoor. The main task of this type of program is the theft of personal data (login / passwords, bank card data, etc.) of an infected machine user to a cracker through remote access. To hide their presence, Win32 / Haxdoor processes use kernel-level rootkit components. Among other things, Haxdoor can deactivate antivirus software, redirect user requests to URLs, delete data on disks, and shut down Windows.
Sony BMG - 2005-2007 year
In 2005, Sony BMG, which distributes record labels, was at the center of a huge global scandal. The company decided to supply their CDs not only with music, but also with a couple of unauthorized copy protection programs. But this software, in consequence, brought a lot of problems to both simple PC users and Sony BMG itself.

Over 22 million CDs released by Sony BMG included two programs: Extended Copy Protection (hereafter referred to as XCP) and MediaMax CD-3. And now more about each.
Xcp
On October 31, 2005, Mark Russinovich, an employee of Microsoft, wrote on his blog about an unusual discovery, which he made by inserting a CD he bought into a computer. This discovery was XCP. Mark, like many others, was outraged by the fact that there was not a word in the EULA license agreement about this software. That is, the program was installed without the knowledge of the user and in every way concealed its existence, which characterizes it as a rootkit.

From the point of view of copyright holders, this software was made with good intentions, but at the same time, XCP created a lot of problems and vulnerabilities:
- XCP created security holes that could be used (and were, in fact) by other malware;
- XCP worked in the background all the time, consuming most of the system resources, slowing down the PC;
- to start and disable XCP used unsafe procedures that cause the system to crash;
- XCP did not have an uninstaller, and most attempts to remove it led to the fact that the OS did not recognize the existing drivers.
After Russinovich’s statement, many intruders used the security holes created by XCP to spread viruses and worms.
MediaMax CD-3
A scandalous feature of this software was the installation despite the license agreement. That is, before the actual use of the disk, the user should have agreed with the clauses of the license agreement. If you refuse, close the window or even “kill” the process, MediaMax was still installed on the computer.
Effects
The news about malware on Sony's CD BMG spread at the speed of sound.As a result, the company was forced to announce the return of unsold copies. However, despite this statement, in many cities the sale of infected disks was carried on.
On November 21, 2005, Texas Attorney General Greg Abbott filed a lawsuit against Sony BMG. Texas was the first (but not the last) state to decide to sue Sony BMG. The main idea of the accusation was that the company secretly installed harmful software on users PCs, which disrupted the system and caused security problems. Naturally, Sony BMG lost in court and had to pay $ 750,000 in legal costs, $ 150 for each damaged PC, place a detailed description of the malware on its website and indicate its existence in its ads on Google, Yahoo! and MSN.
This was followed by many claims from the victims. It developed two methods of conflict resolution. In the first version, the victim received $ 7.5 in compensation and the opportunity to download a music album for free. In the second - download 3 albums but without monetary compensation.
Such a strong public response, financial losses and litigation still prompted Sony BMG to make a decision - no longer use similar software on their disks.
Storm Worm - 2007
Trojan, discovered on January 17, 2007. It was distributed via e-mail with the subject “230 dead as storm batters Europe” (from which it got its name). The main task of the Storm Worm was to create a botnet.
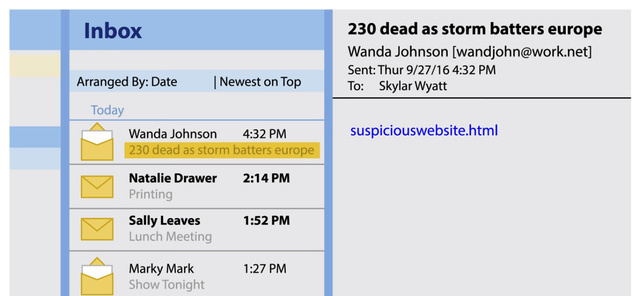
The letter contained an attached file, opening which, the user reluctantly started the installation process of the wincom32 service. Also, a trojan could download and install another Trojan.Abwiz.F and a W32.Mixor.Q@mm worm. The rapid spread and survivability of the Storm Worm was promoted by changing its packet code every 10 minutes and using fast flux to change the IP address of its management server.
Infected PC became part of the botnet, which was difficult to eliminate. Most normal botnets are managed by a single central server, the elimination of which leads to the fall of the botnet. In the case of the Storm Worm, it was extremely difficult to identify the central server. Each of the infected machines was connected only with a part of the botnet (30-35 machines). None of the machines had a complete list of the botnet, but only a part of it, which did not allow identifying the management server. According to September 7, 2007, from 1 to 10 million computers participated in the botnet.
Mebroot - 2008
Rootkit based on the master boot record, which is used to form botnets. Mebroot was launched before the system was loaded, which gave it the opportunity to bypass the security protocols. An encrypted channel was installed to the infected computer through which the attacker could install a couple more Trojans. The main purpose of Mebroot, in conjunction with his brother Anserin, was the theft of banking information. Infection with the triple occurred through a visit to the websites where he “lived”, they were counted about 1500.
Conficker - 2008
People who know German will understand the whole rudeness of this name. The first part of the con is part of the word configuration, and the second ficker is the German equivalent of fucker (I think everyone guessed what it means in translation).
Conficker used to infect a vulnerability in the network service of Windows OS, which according to the good old tradition was eliminated in the patch even before the worm appeared.
By infecting a computer, Conficker disabled certain services in order to extend its existence — automatic updating of Windows, Windows Error Reporting, Windows Defender, and Windows Security Center. Next, to receive commands, the worm generated a list of sites to which it established an HTTP connection. Also Conficker blocked access to the sites of many antiviruses.
Detection and elimination of this worm is an extremely difficult process, since its creators monitor all antivirus updates to improve their product and eliminate vulnerabilities in it.
Stuxnet 2010
A large, very large computer worm (about 10 times larger than normal), which has become a weapon of industrial espionage and sabotage. It was first seen in 2010. For its rapid spread, it used a zero-day vulnerability (a vulnerability that has not yet been discovered by software developers). Spread using USB flash drives. The main purpose of the worm was programmable logic controllers (PLC / PLC) from Siemens. PLC allows to automate electromechanical processes (assembly line at enterprises, for example).

Stuxnet was programmed to attack very specific and specific targets. First of all, the computer had to work on Windows. Next, the worm detected Siemens Simatic Step7 software (software for developing automation systems based on PLC) and changed the command codes, but the user did not do this. In a nutshell, Stuxnet intercepted and modified the information that was transmitted between the Simatic Step7 PLC and the Simatic WinCC SCADA workstations. At the same time, the worm was disguised due to the presence of real digital signatures - certificates from Realtek and JMicron.
PLC infection was not erratic, but followed several parameters laid down in the worm code. The worm attacked PLC systems with frequency converters exclusively from two vendors: Vacon (Finland) and Fararo Paya (Iran). In addition, Stuxnet read the frequencies of the connected centrifuges, attacking only those that were in the interval 807 Hz - 1.210 Hz. Then, the worm installed its own PD in the DB890 PLC memory block, which controls the Profibus (open industrial network). When all criteria meet, the worm changes the frequency of the centrifuges by 1.410 Hz, then 2 Hz, then 1.064 Hz. Thereby breaking their work. Stuxnet also uses a rootkit, which hides from the monitoring system the fact that the speed of the centrifuges is jumping.

By such actions, Stuxnet was able to disrupt the work and actually disable 1000 centrifuges to enrich uranium. This rejected Iran’s nuclear program a few years ago.
There is no exact information about who created Stuxnet and why. However, many consider Stuxnet to be a common creation of the United States and Israel, aimed specifically at the Iranian nuclear program. Since according to statistics, it was Iran that suffered the most (58.85%)
Afterword
No one likes viruses, worms and Trojans (except for their creators, of course). But it is impossible to underestimate their contribution to the development of technologies, namely security systems. After all, not having an opponent worthy of confronting you, you will not develop to overcome it. And last, do not forget to update your antivirus. See you in the next section, where we will talk about malware from 2010-2017.
As advertising. Stock! Only now get up to 4 months of free use of VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB - $ 29 / month and above, options with RAID1 and RAID10 are available) , a full-fledged analogue of dedicated servers, when ordering for a period of 1-12 months, the conditions of the promotion are here, existing subscribers can receive a 2-month bonus!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/370819/
All Articles