Denuvo company lit directory / fileadmin
 Lead Programmer Matthias Werner and his colleagues from the Austrian company Denuvo enjoyed the reputation of great professionals. Their copy protection works at a low level, binds to the hardware and generates a unique cryptographic key. What can I say - system programmers, real hackers, without a doubt. But on an experienced webmaster they spared money, and Matthias himself was not very good at this.
Lead Programmer Matthias Werner and his colleagues from the Austrian company Denuvo enjoyed the reputation of great professionals. Their copy protection works at a low level, binds to the hardware and generates a unique cryptographic key. What can I say - system programmers, real hackers, without a doubt. But on an experienced webmaster they spared money, and Matthias himself was not very good at this.On the evening of February 5, the 4chan forum began to walk links to http://www.denuvo.com/fileadmin/ , which poured all the content into open access. Something interesting was found there.
The guys from the forums immediately began to study the files in all the folders / fileadmin / , and the largest treasure was found in the directory / fileadmin / logs / - there was a file /logs/ajax.log 11 MB in size. At first glance, it seemed that there was nothing special in the file - just some e-mails sent by sendmail via a web form on a page with contact information . Messages of this type:
sendmail 2016-02-03 18:53:59 array ( 'name' => 'Nrouf92@Gmail.com', 'email' => 'Nrouf92@Gmail.com', 'phone' => '07799943084', 'message' => 'Hi there. As a massive Denuvo supporter and someone against piracy, I have found something worrying and sickening with regards to video game with denuvo. The game in question is Rise of the tomb raider for the PC. Here is the link where I found information about the crack. Can you please have it investigated as I do not want the PC gaming industry to go down and I respect the developers of the game. http://corepacks.com/index.php?/topic/9419-deadnuvo-project-cracking-tutorial-part-ii/', 'captcha' => 'KCapmD', ) Among the messages to Denuvo were obscene . Obviously, not all users like protecting games from illegal copying.
')
sendmail 2017-01-15 19:06:19 array ( 'name' => 'FuckDenuvo', 'email' => 'fuck@you.com', 'phone' => '', 'message' => 'Dear Denuvo I know you must get messages like this every day. Hundreds, even thousands. But I believe that even if only one person hears this, I will have done something right. Fuck. You. You are a worthless company and I hate everything about you. Yes, even you, the person who has to sort through these messages and delete ones like this. You work for an evil, evil company and you are supporting them by doing that. Fuck you.', 'captcha' => '4drZlC', ) In another file, http://denuvo.com/fileadmin/config/aws_config.json found something interesting:
{ "includes": ["_aws"], "services": { "default_settings": { "params": { "credentials":{ "key":"AKIAIMDAVSEKSKZ5YAWA", "secret":"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" }, "profile": "default", "region": "eu-west-1" } } } } Looks like private access keys to the AWS cloud service. However, it was not possible to extract this key especially because Denuvo used AWS service to a minimum degree, only AWS SDK for PHP : aws-aws-sdk-php-2.8.31-0-g64fa4b0.zip .
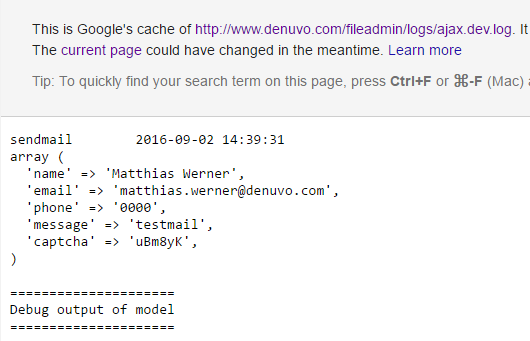
Apparently, in the Denuvo company, the lead programmer Mathias Werner himself was in charge of setting up the server. At least, his name is also found in the logs. It seems that he tested the form of sending messages.
Most of the messages in the logs are spam, claims and attacks from angry pirates who cannot launch the game, cursing and cursing the company, writes Ars Technica, which managed to download the file from the server before access was closed. But since the contact information page on the Denuvo website does not have a contact email address, some normal people, including game developers and publishers, used this form. At least, in many messages there are real addresses of gaming studios 343 Industries, TaleWorlds, Harmonix Games, Capcom, Ninja Theory, Codemasters, Relic Entertainment, 505 Games, Kalypso and many others. Publishers often ask to meet with Denuvo representatives or to introduce copy protection into their games.
Shortly after publication in the media, Denuvo admins woke up and closed access to / fileadmin, although some of the information remained online and the fastest managed to download it.

A week ago, there was a crack for Resident Evil 7 five days after the official release. This is the fastest hack protection Denuvo in history. With such low efficiency, protection makes little sense — developers are unlikely to recoup the money spent on it. However, it depends on how much Denuvo will ask for - maybe after the recent events, the cost of implementing Denuvo protection will drop by an order of magnitude. But by and large it can no longer be taken into account. Someone thought that it was time to bury Denuvo’s company. But no. The last nail in the lid of the coffin of Denuvo was hammered in not then, but right now - with the publication of logs, private letters and AWS keys. Such a fat control nail. Or is this a mockery of a corpse? If Denuvo continues to work in the field of information security, it will be just ridiculous.
→ Copy ajax.log
→ Google cache
Source: https://habr.com/ru/post/370141/
All Articles