The mobile Signal application bypasses government blocking by passing traffic through Google App Engine.
Circumvention of state censorship through the protection of domains, from the scientific work of 2015
From December 21, 2016, the Open Whisper Systems crypto-messenger Signal began to use the original method of circumventing state censorship, due to which users from Egypt and the UAE were disconnected from the network. The method is called “domain fronting” and is described in detail in 2015 in the scientific work of researchers from universities in California, Berkeley and Princeton.
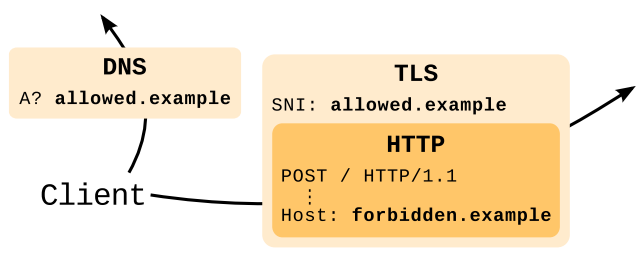
The censor sees only the domains specified in the DNS query and in the TLS SNI field, but it does not see the HTTP Host header, in which the system hides the real domain name for sending traffic. The real domain name is securely hidden using HTTPS encryption.
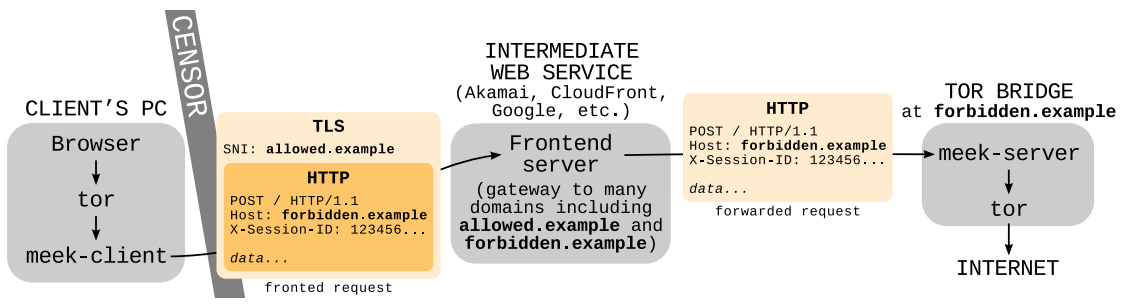
Recently, the governments of Egypt and the United Arab Emirates have been trying to turn off in the Signal countries, blocking servers for the contact list. Now, when users from these countries send a message via Signal, it passes through a reflector (a simple script on App Engine) and an external proxy, but it looks like a normal HTTPS request to www.google.com . Thus, to block Signal, these states will have to block the domains google.com, gmail.com, googleapis.com and many other domains that are allowed to use as a “roof” for the application on Google App Engine. A similar method of repeaters is used in other systems of circumventing state censorship - Tor , Lantern and Psiphon .
')
As is clear from the illustration below, the scheme provides for the use of an intermediate “roof” - this is the frontend server on the intermediate web service. For such a "roof" is used legal foreign domain. Domains of various cloud services that allow traffic are suitable for this. The most reliable is the domain of Google.
Circumvention of state censorship through the protection of domains, from the scientific work of 2015
In addition to Google App Engine, for this purpose you can use Amazon CloudFront, Azure, Fastly, CloudFlare, Akamai, Level 3 and similar CDN services. As for the cost of traffic, it looks like Azure and Google App Engine, but the cost of traffic depends on a number of conditions, including the amount of traffic, the number of instances dynamically raised to service the traffic, the number of hours they work, the area of the data center location (such tariffs in Amazon CloudFront) and some other options. Separate CDNs like Akamai do not publish tariffs for transmitted traffic at all, so they have to be learned from resellers.
In general, tariffs for different “roofs” start at about $ 0.08 per gigabyte. For a text messaging service, even for a free service, eight cents is not a lot of money. Even the great Tor, which passes a large amount of traffic, pays only $ 2043 a month for the roof. This is the figure for May 2015, that month 11,666 GB of traffic passed through these channels. Tor uses Google App Engine, Amazon CloudFront, and (presumably) Microsoft Azure.
You have to sacrifice a bit the speed of messaging The ping and data transfer rate increases slightly, but here the costs are not that big. When sending text messages, the data transfer speed can be easily donated.
In general, Signal provides a very good example to other mobile applications and services that want to protect themselves from government censorship, and at the same time further protect the privacy of their users' private correspondence. It is likely that many applications will still face this problem, since governments around the world are showing increasing interest in private communication of citizens via Internet services and mobile applications, especially if strong cryptography is used there.
As the Signal experience shows, when a state loses the ability to listen to traffic, it tries to block it.
The situation is especially dangerous for countries with a small number of Internet service providers that control external communication channels. If necessary, they can even temporarily disable communication with the outside world and leave users access only to the internal segment of the Internet. From this position, the goal of Signal is to make the blocking of the service possible only if the state completely blocks access to the Internet for citizens.
After updating the mobile application for Android, Signal users can freely use the service, quietly traveling even in countries with current state censorship. Now you do not need to use VPN services. The corresponding version of the Signal app for iOS is still in beta and will also be released soon in official release. If necessary, you can subscribe to the beta channel and get the beta version now by sending an email to
support@whispersystems.org .Security experts call Signal one of the safest instant messengers. Its open and proven end-to-end encryption protocol is also used by other popular instant messengers, including Facebook Messenger and WhatsApp.
Source: https://habr.com/ru/post/370007/
All Articles