Chinese researchers have proposed to supplement the Bitcoin network with anonymization methods from Tor
Schematic diagram of the proposed system
Chinese computer security researchers from Shenzhen University have proposed an improved way to organize a network of transactions for cryptocurrencies. It should solve one of the problems of current networks - the lack of guarantees of anonymity of transactions.
Although in the Bitcoin network transactions pass between generated addresses that do not contain information about the sender, an attacker can always try to write down the ip-addresses of the parties involved in the transfer and thus get to the parties to the transactions. In this regard, working with Bitcoins is often called pseudo-anonymous.
')
In the most well-known network with the anonymization of Tor connections, there is a “onion” packet transfer scheme, when each of several randomly selected nodes has access only to its own portion of data. As a result, the sender of the packet does not know the recipient's ip-address, and the recipient who received the packet does not already know the sender's ip-address.
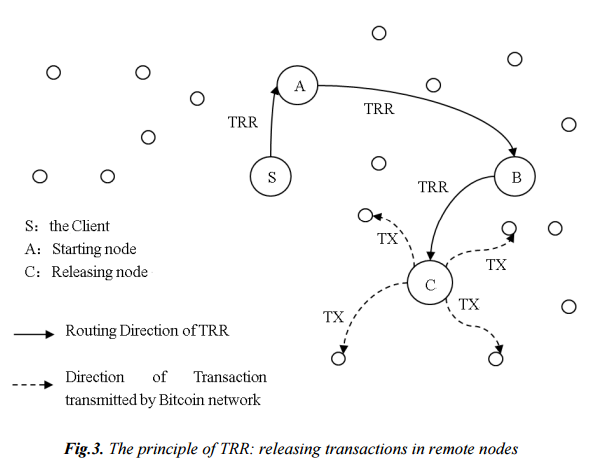
According to this scheme, anonymization works both for accessing Internet sites and for “hidden services” - Tor nodes that are maintained by network users who are sure of the anonymity of their actions. The Chinese propose to add the exact same scheme to the Bitcoin system’s core in order to add anonymity to monetary transactions. They called their system Transaction Remote Release (TRR, Remote Transaction Release ).
Thanks to multi-level encryption, the contents of the transaction become known only to the sender and the end node. At the same time, intermediate nodes do not know the contents of the transaction and do not know about all its participants at the same time. A transaction is sent only when it arrives at the receiving node.
The problem is that this scheme, if it is approved, will need to be introduced into the core of the system bitcoin. And considering how long developers are arguing about a possible increase in block size, this process can be delayed, to say the least.
The second difficulty stems from the fact that once the system is taken from the Tor network, the problems of this network will come along with it. Using several controlled nodes, one can try to perform a “mediator attack” (MitM) by intercepting packets going over the network. But as the number of bona fide nodes increases, the likelihood of success of such an attack decreases.
Source: https://habr.com/ru/post/368481/
All Articles