Hacker has published a method for selecting pin codes to the iPhone without additional devices.
The recent history of the device for selecting the pin-code for the iPhone so impressed by the famous hacker and jailbreak developer for iOS, Majid Alfhayli , that he wondered if it was impossible to make a programmatic selection of the pin-code for the device, and even faster than one pin in 40 seconds? It turned out - you can. The only requirement is that the device must be subjected to a jailbreak.
First, the developer wrote the following code to iterate through all passwords from 0000 to 9999:
(void)bruteforce { NSString *numString; NSString *oneZeroString = @"0"; NSString *twoZeroString = @"00"; NSString *threeZeroString = @"000"; for (int i = 1; i <= 9999; i++) { numString = [NSString stringWithFormat:@"%d", i]; switch ([numString length]) { case 1: { numString = [threeZeroString stringByAppendingString:numString]; break; } case 2: { numString = [twoZeroString stringByAppendingString:numString]; break; } case 3: { numString = [oneZeroString stringByAppendingString:numString]; break; } default: break; } NSLog(@"code : %@", numString); } } ')
Then in the SpringBoard dump, he found the SBDeviceLockController class with the method
(BOOL) attemptDeviceUnlockWithPassword: (id) password appRequested: (BOOL) requested;
Then he made a library that connects to the SpringBoard process and runs the above code at the end of the process, and calls the attemptDeviceUnlockWithPassword: appRequested for each new pincode.
Everything worked, except that after 10 attempts the phone was blocked. After additional research, the hacker found methods in the SBFDeviceLockController class.
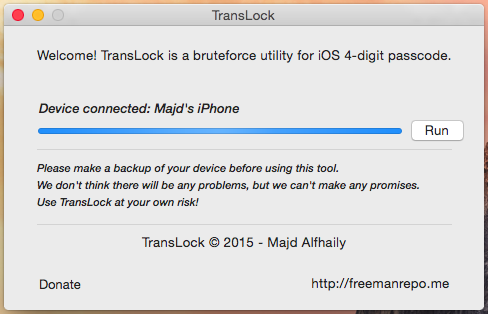
(bool)_temporarilyBlocked; (bool)isPasscodeLockedOrBlocked; (bool)isBlocked; After redefining these methods so that they return NO, the code is fully operational. 10 attempts do not block the device, checking one pin-code takes 5 seconds - that is, checking all four-digit codes will take no more than 14 hours. Now the hacker is working on an automatic utility that can send this code to the device via USB.
Conclusion: the longer and more difficult the password, the higher your security. However, this was already so obvious.
Source: https://habr.com/ru/post/366605/
All Articles