Configure BGP to bypass locks, version 2, “not thinking”
I re-read my previous post with a sober look and realized that it would be difficult for newcomers, through all these heaps of updates and discussions in the comments (which were even more useful than the post itself).
Therefore, here I will give a concise step-by-step instruction on how to bypass locks, if you have:
- Linux machine (ubuntu) outside the lock box;
- Mikrotik router, to which you have already raised the VPN tunnel to this Linux machine;
- configured NAT on this tunnel, allowing you to work through it;
- a wish.
If you do not have any of this or you have something else or you want to know why this is the case and not the other - welcome to the previous post , where all this is described in more or less detail. Keep in mind that the inclusion schemes and settings in this post are slightly different to simplify the solution.
Those who have already done everything based on the previous post, in this useful information is not gathered.
TL; DR
We automate access to resources through your existing tunnel using ready lists of IP addresses based on the RKN registry and BGP protocol. The goal is to remove all traffic addressed to blocked resources to the tunnel.
Initial data
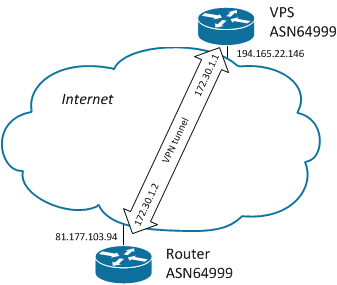
IP addresses inside the tunnel 172.30.1.1 - Linux, 172.30.1.2 - Mikrotik.
The interface of the VPN tunnel on the Linux side is called tun0.
In this edition of the post it is strictly assumed that the tunnel and the bgp server are running on the same Linux machine.
We perform the settings on Linux as root (i.e. before starting the configuration, we execute the sudo su - command).
Initial lists of IP addresses will be received from the new service antifilter.download .
Briefly - decision logic
- Install and configure the routing service
- We receive and regularly update lists of IP-addresses, create on the basis of them the settings of the routing service
- We connect the router to the service and configure sending all the traffic through the tunnel.
Decision
Installing and configuring the routing service
On the linux machine, add the official PPA software developers to the system and install the bird.
add-apt-repository ppa:cz.nic-labs/bird apt update apt install bird Disable bird for IPv6 and stop while bird for IPv4.
systemctl stop bird6 systemctl disable bird6 systemctl stop bird Save the /etc/bird/bird.conf file with the following contents:
log syslog all; router id 172.30.1.1; protocol kernel { scan time 60; import none; export none; } protocol device { scan time 60; } protocol static static_bgp { include "subnet.txt"; include "ipsum.txt"; } protocol bgp OurRouter { description "Our Router"; neighbor 172.30.1.2 as 64999; import none; export where proto = "static_bgp"; next hop self; local as 64999; source address 172.30.1.1; passive off; } Get and compile lists of IP addresses
Create a folder / root / blacklist and a subfolder list in it
mkdir -p /root/blacklist/list cd /root/blacklist Create the file / root / blacklist / chklist with the following contents:
#!/bin/bash cd /root/blacklist/list wget -N https://antifilter.download/list/ipsum.lst https://antifilter.download/list/subnet.lst old=$(cat /root/blacklist/md5.txt); new=$(cat /root/blacklist/list/*.lst | md5sum | head -c 32); if [ "$old" != "$new" ] then cat /root/blacklist/list/ipsum.lst | sed 's_.*_route & reject;_' > /etc/bird/ipsum.txt cat /root/blacklist/list/subnet.lst | sed 's_.*_route & reject;_' > /etc/bird/subnet.txt /usr/sbin/birdc configure; logger "RKN list reconfigured"; echo $new > /root/blacklist/md5.txt; fi We make the file executable and run it once for verification, after that the necessary files will appear in the / etc / bird folder and you can run bird.
chmod +x /root/blacklist/chklist /root/blacklist/chklist systemctl start bird Add a crontab -e file once every half hour
*/30 * * * * bash /root/blacklist/chklist After that, the routing service works and, using the command birdc show route, shows a long set of routes to the forbidden resources.
Configuring Mikrotik from the command line
We execute the following commands on the device in the terminal window (remember that direct copy-paste may not work, since it will complete auto-completion):
/routing bgp instance set default as=64999 ignore-as-path-len=yes router-id=172.30.1.2 /routing bgp peer add name=VPS remote-address=172.30.1.1 remote-as=64999 ttl=default A few seconds after these commands are executed, a little more than 13 thousand routes pointing to the nextop inside the tunnel will arrive in your Mikrotik router. And it will work.
Conclusion
I hope that it turned out short and clear.
If your task does not fit into this simple scheme - perhaps you should read the previous post with comments and, most likely, you will find there some tips.
')
Source: https://habr.com/ru/post/359268/
All Articles