PHDays 8 Summary: Games Over

The eighth international forum on practical security Positive Hack Days came to an end. More than 5,200 participants at the site in Moscow watched the interception of the radio broadcasts of the cellular operator, the breaking of the ATM, the winding up of a smart electric meter (one of the participants was 12 years old!) And dozens of other hacker activities. This drama occurred in the final confrontation of the attackers and defenders of the city.
On the conflict of attackers and defenders
The Standoff’s 30-hour cyber battle has ended. At the end of two days, we can say that friendship has won. The attacking teams managed to hack some objects, but without a fight: most of them were not protected. Nevertheless, the battle between the attackers was hot: the standings changed dramatically half an hour before the end of the game.
')
The first day was not very eventful. By the end of the day, one of the attacking teams managed to hack an unprotected office - this was reported by the RT SOC team. In addition, urban infrastructure facilities were hacked: the attackers found vulnerabilities in the cells and launched a denial of service attack, while others “played around” with heating systems. Also during the day, the attackers gave the organizers information about vulnerabilities in the framework of bug bounty and bank card information.
As expected, all the fun happened at night. The Jet Antifraud Team, which defended the bank, recorded a massive attack, the purpose of which was to steal money from the accounts of city residents. During the day, there were only five attempts at transfers of 140 publications (the virtual currency of the city). In the evening and at night, there were three major attacks. In total there were about 20 thousand attempts to commit fraudulent transactions on 19 external accounts.
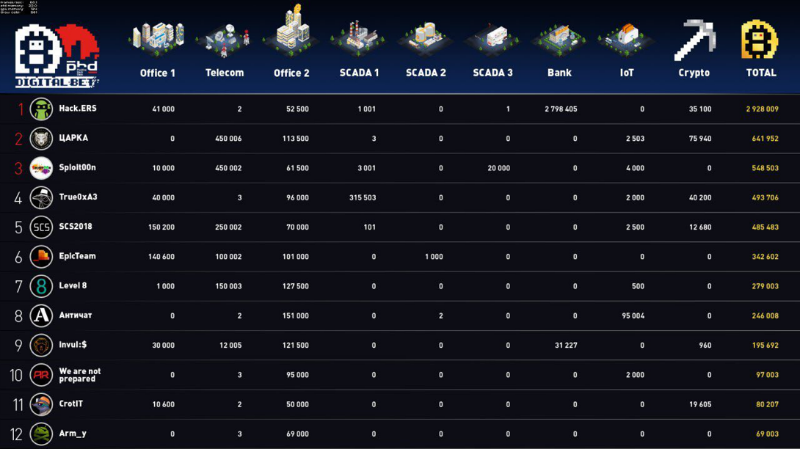
The teams of CARK and Sploit00n managed to hack the subscribers of the telecom operator: SMS messages were intercepted and the vehicle was found using GPS coordinates. Note that subscriber data security was not controlled by defense teams. In the middle of the day, CARK was also able to reset the passwords of all the subscribers of the telecom-operator portal and tried to sell the discounted uchetki to the buyer on the black market, but he quickly became suspicious and refused to buy fake uchetok. At this time, the telecom operator quickly restored the accounts from the backup after it received complaints from subscribers, and closed the hole in the portal. Next, the team tried to hand over accounting for the bug bounty program, but the telecom paid a penny for it. Note that this was not the omission of the protection team, as the organizers temporarily asked to disconnect WAF from the portal to install updates and test the new functionality, which the attackers took advantage of.
At the end of the day, unknown hackers attempted to roughly pull the SIP account online, but due to timely editing by Asterisk configuration defenders, which complicate online brute force, this attack was not successful. The fact that the attackers apparently did not have enough time for preliminary preparation also had an effect: they tried to sling out nonexistent telephone numbers (shorter than one digit). It is worth noting that neither defenders nor SOC noticed a brute force attack.
Later, several more teams attempted to hand over compromising information to a top manager of the city’s insurance company, but there was no information in one of the teams confirming that this correspondence belongs to the target of interest. Another team was able to intercept only part of the correspondence. The buyer on the black market, of course, also paid for this information, but not as much as the attackers expected. Also, at the end of the second day, another team was able to track the car via GSM.
But industrial facilities were not an easy task for teams. Having cracked an unprotected office on the eve, the attackers did not immediately guess that this office is the management company of the technology segment. When all attempts to gain remote access to the objects of the industrial control system were unsuccessful, the attackers tried to connect locally. As a result, closer to morning, an unexpected temporary truce happened between the attackers and the defenders. Together, they tried to study the infrastructure of the technology segment: hackers made hacking attempts under the supervision of defenders.
On the second day, the attackers reached another office. Some services have been hacked. As the SRV and Perspective Monitoring teams told, one Linux machine was tested for a long time by overwhelming the passwords. As a result, using the advanced dictionary, the attacker managed to hack accounts. The attackers tried to gain a foothold in the system and attack internal services bypassing the NGFW, but activity was stopped. Also, the defenders found and eliminated the miner. In just two days, the WAF defenders team repulsed about 1,500,000 attacks, and 30 security incidents were initiated.
By the end of the day, one of the teams carried out a local attack:
coming directly to the equipment, the attackers made (possibly by accident) a loop in the local network, which led to a loss of communication with the PLC and SCADA simultaneously. Because of this, there was an oil spill. Also, the True0xA3 team already in the last minutes of the competition arranged a blackout in the city. Took and rail: unknown hackers were able to control the locomotive
An hour before the end of the cyber battle, the city decided to abandon the anti-fraud system. This was used by the team Hack.ERS, which managed to clean the bank. This allowed them to rise from the basement of the tournament table and get into the winners, knocking out the CARK team (the winners of last year) from the leaders.
Results and detailed analysis of the tasks of the competition will be later.
On the wrong side of digitalization

Any modern technology has a downside. A few years ago, hackers used contextual advertising to target attacks against US defense and aerospace companies. The ability to narrow down the target audience, implemented by advertising networks, allowed attackers to deliver malicious software to employees of specific organizations. New challenges related to digitalization were discussed by representatives of Informzashchita, NKTSKI, Rostelecom, Sotsioma, IBM and Group-IB in the section “ Digitization - a threat or a chance? ".
Director of grocery office "Information Security" "Rostelecom" Stanislav Bartashevich noted that the number of attacks on the information resources of business and the state is growing. Rostelecom experts annually register about 800 DDoS attacks on the resources of the company and its clients: “Of the recent attacks on information resources, presidential elections were significant for us, when the CEC website and related resources produced more than 50 powerful attacks of different directions ( DDoS, attacks on web application vulnerabilities) ”.
The effectiveness of attacks, the types of attackers, their motivations were told by the head of the Threat Intelligence cyber intelligence department of Group-IB and its co-founder Dmitry Volkov: “We have two sources to track the success of attacks: our equipment, through which we see that attacks come, and the incident response, when an incident happens, becomes known to the owners of the company, and we leave to deal with the consequences. The number of trips from year to year is growing. This does not mean that the number of attacks in general is growing too, just attacks become more complex and attract more attention from company executives. Now there is a fashion trend to talk about an increase in the number of attacks: yes, the number of simple attacks is growing, but if we talk about their effectiveness, it decreases. ”
During the discussion, the section participants shared their assessment of security issues in the digital world, in particular, they talked about the attacker's portrait, the reachability of attacks, the effectiveness of remedies, and the nuances of regulatory requirements. Not spared the issues of human resources and internal offenders: a lot depends on the human factor, on the professionalism of the information security team and employees of the company as a whole. Following the discussion, the participants concluded that digitalization creates both new opportunities and new threats.
Hole in your pocket

Today, people use an average of 30 mobile apps per month. Gustavo Sorondo, Technical Director of Cinta Infinita, spoke about the security problems of smartphones and tablets in his report “How to survive the insecurity of mobile applications”. He tested his first smartphone app eight years ago. It was an Internet bank, and at that time very few people understood how to check such software. Only in 2014, OWASP for the first time released its top-10 vulnerabilities for mobile applications and in 2016 updated it. In the first place was the problem of incorrect use of the platform, replacing the vulnerability of weak controls at the server level. The second point Gustavo calls the most important - unsafe data storage, which is written to the logs, cache, etc. The third item - unsafe communication, when applications transmit data in open form or do not warn about forged or outdated certificates.
According to Gustavo, in terms of security, mobile applications are 10 years behind the web. If a popular browser is required to issue a warning about an outdated certificate, the mobile application can often be “silent” about the danger. Now there are no automated systems for testing mobile applications, there are only systems for analyzing the code, which often give a lot of false-positive results, so they are generally only suitable at the beginning of the pentest. When developing and testing mobile software, the speaker recommends using documents from the same OWASP - Mobile Application Security Verification Standard (MASVS) and Mobile Security Testing Guide .
Deep dive
The technical hardcore on PHDays was abound as always. Arseny Reutov, the head of the research team for the application protection tools development department of Positive Technologies, spoke about the problems of smart contracts in his speech “We predict random numbers in smart contracts of Ethereum”. Not everyone knows that Ether (Ethereum) is not only the second most popular cryptocurrency in the world, but also the most famous designer of smart contracts. Last year, Alfa-Bank and S7 Airlines used a deal on the basis of an air-based smart contract. The algorithm controlled the receipt of money on the account of the contractor after the arrival of documents on the performance of work. Smart contracts avoid many legal formalities, but they have one major drawback: they are vulnerable to hacker attacks, like any other program.
Computer on four wheels

According to Gartner's forecast, by 2020 there will be 250 million cars connected to the Internet in the world. They will exchange data with the services of the smart city about accidents and jams to reduce the number of traffic jams, help diagnose problems, provide information and entertainment services to passengers. Such systems make travel more convenient, but open up new opportunities for attackers. Stefan Tanase and Gabriel Chirlig of Ixia (Keysight Technologies) investigated the car with an integrated infotainment system and found many vulnerabilities in it. The experiments were carried out with a private car Gabriel Cheerlig. According to Stefan Tanase, vulnerabilities in a car are much more dangerous than in ordinary PCs, since human lives can be at risk: a car travels at high speed and the intervention of a cybercriminal can be fatal. To search for vulnerabilities of the car computer system, the speakers used, in particular, the open source software Mazda Aio Tweaks. During the presentation, “Smart Car as a Weapon”, researchers showed how cybercriminals can use the GPS data of cars embedded in cars to spy on their owners. One of the students even turned to Cheerlig with a request to connect to the entertainment system of her hijacked car in order to find her car using GPS logs.
About expensive toys in banks

The banking industry remains one of the main objectives of the attackers. In March of this year, the leader of the hacker group Cobalt was arrested, who stole more than 1 billion euros from about a hundred financial institutions around the world. The section “Security of credit and financial organizations” was devoted to countering such groupings. The section was chaired by Alexey Kachalin, executive director of the Sberbank cyber defense center.
The provocative question was voiced at the discussion: what will die first - DLP or antivirus on the nodes? Here are some comments from the discussion participants
Lev Shumsky, independent expert: “The business value of DLP is very hard to“ touch ”, and the money is substantial. Most likely, this technology will not die, but it will be used specifically. Well, it will work in a kind of "boxes" when people come to work and leave their gadgets in a closed, protected perimeter. In all other cases, it is an expensive toy that requires a lot of resources both in terms of administration and for the work of analysts and operators. As for antiviruses, their further evolution is quite obvious. ”
Dmitry Gadar, Tinkoff.ru: “One cannot raise the question of whether the technology will die, apart from what it will be applied to. Should there be an antivirus on the workstation? Antivirus owes nothing to anyone. Antivirus is probably a struggle with the consequences. In one of the banks I did not put antivirus on ATMs, I made a closed software environment there. It was such a thrill! You do not need to update anything on ATMs, because there is a rarely changing environment, it can be fixed, and no virus will be installed there. Same story with DLP. This is an expensive tool with an incomprehensible exhaust. At the same time, there are architectural solutions that avoid the use of this heavy technology. The difficulty is to correctly determine what technology for which we use, to determine the scope of work and technology for these works. Usually the security men are too lazy to do this. ”
Remove someone else's money on call

Independent researcher Alexander Kolchanov spoke about vulnerabilities in telephone banking systems that allow receiving confidential information from customers and transferring money from their accounts. In this case, communication with the bank and the management of funds on their accounts occurs, as a rule, through the call center operator or SMS. The speaker during the presentation “Vulnerabilities in telephone banks: disclosing personal data and stealing money from accounts” demonstrated a number of attacks, including those related to SMS authorization deficiencies.
According to Kolchanov, there may be several telephone banking systems in one bank, and some of them may be forgotten. Some systems are well protected, but at the same time there are systems where authorization is much easier. Another problem is to use only passport data for authorization, which may allow an illegitimate user to call the bank and try to carry out operations or find out customer data for the next stage of the attack. Some banks have separate banking systems for premium customers, which are often used by other authorization technologies.
An attacker can find out the passport data of such a client and its balance and make an attack. Another dangerous trend is the emergence of personal managers with separate mobile numbers from premium clients. In one large Russian bank, ordinary users are protected: they need to use a code word with passport data, and premium clients do not need to call a code word. Having found out the client’s and his personal manager’s numbers and some other personal data, an attacker can withdraw significant amounts of money.
How to turn SOC into a useful robot

At the end of the day, there was a section “What should be done to make SOC finally work ?!”, led by Vladimir Bengin, Director of Sales Technologies Support Department. Section participants from companies GTLK, Angara Technologies Group and Solar Security shared their experience in building information security situational centers, and also explained how to “teach” SOC to prevent incidents. Sergey Rysin from GTLK said that one of the cornerstones in building a SOC is the readiness of the IT division to cooperate. The information security unit of STLC consists of one person, so the management with the help of a private SOC allowed Sergey to automate everything that is possible. For example, in the case of an unauthorized connection to a Wi-Fi network, the network segment is automatically blocked, and in the case of copying sensitive data to USB-carriers, SMS messages are received to responsible people. The final incidents are addressed to the security or IT department. Alexander Sukhomlin from Solar Security said that some customers think that by calling the MSSP provider, they will build an SO, but this is not quite the case - it is also necessary to build customer response processes.
“With SOC, you are not observing people, a program, a server, or another separate entity; You control what brings the company money, ”said Dmitry Zabelin, head of risk management at Angara Technologies Group. - And money brings business processes. , SOC, . , , - «» 240 ».
-
On the forum site, competitions were held on hacking smart grids, searching vulnerabilities in smart contracts of blockchain, going through a maze in a smart house, hacking duels in the one-on-one format, various online competitions. Traditionally PHDays is a cultural event. The competition for creators of comics, cyberpunk reading was performed by the team of creators of the legendary radio program “Model for Assembly”, the festival of musical groups of IT companies Positive Hard Days: each team performed with a 20-minute set. We will tell about all this later, stay tuned!
Source: https://habr.com/ru/post/358878/
All Articles