And again: do not use public WiFi

The idea presented in this post may seem obvious and banal to someone, but, as the conversation in the smoking room with colleagues showed, many, even those related to IT, did not even think about it, let alone more distant people from technology.
When it comes to “What is a bad public Wi-Fi in transport / cafes / hotels / etc.?” Most often the first answer is that the main problem is either completely missing encryption or using the same encryption key for all users. Many will rightly object to this, they say, now almost all sites and services use HTTPS, so an attacker who listens to traffic cannot intercept your passwords and personal data.
Those who are technically savvy or have a healthy paranoia, use encrypted VPN when working through public networks, thus creating an extra layer of protection.
But today it is not about that.
')
According to the current legislation of the Russian Federation, the main condition for free access to wi-fi is the authorization of users. When connecting to the public network, the user must pass identification of his / her device.
List of legislation
- FL No. 126 “On Communications”, which entered into force on July 7, 2003;
- Government Resolution No. 801 “On Amendments to Certain Acts of the Government of the Russian Federation”;
- Federal Law of the Russian Federation dated July 27, 2006 No. 149- “On Information, Information Technologies and Information Protection”;
- Order of the Ministry of Communications and Mass Media of Russia No. 83 dated April 16, 2014;
- Federal Law of the Russian Federation dated July 27, 2006 N 152- “On Personal Data” with amendments and additions;
- Rules for the provision of communication services for data transmission, approved by the Government of the Russian Federation on January 23, 2006N 32;
- Rules for the provision of telematic communication services, approved by the Government of the Russian Federation of September 10, 2007 N 575;
- Rules for the provision of universal telecommunications services, approved by the Government of the Russian Federation on April 21, 2005 N 241;
- Resolution of the Government of the Russian Federation of July 31, 2014 N 758.
When you connect to free WiFi for the first time, you are automatically redirected to the authorization page, which may look, for example, something like this:
Authorization is usually possible in one or several ways:
- By entering a mobile phone number, and receiving a code on it by SMS or call. According to the adopted amendments to the Law "On Communications", SIM-cards can be sold only at specialized points and if there are documents proving the identity of the buyer. Moreover, the relevant state. Structures are carrying out plans to combat the "gray" and "left" Sims.
- Authorization through the ESIA ("Gosuslugi"), the creation of an account in which likewise requires the presentation of identity documents
- Some Internet providers allow their subscribers to connect to their public Wi-Fi using a login-password from their home Internet, the contract for which, again, is with the indication of passport data.
Almost always, after going through the authorization procedure, a record of the form 'MAC address of your device' / 'is some identifier that clearly indicates your identity' is stored in the database of the service provider (phone number, login on public services, contract number, etc. ). This is necessary so that when you next connect to the same network, you don’t have to go through the whole procedure again - the service provider’s router recognizes your phone, tablet or laptop by its MAC address and automatically applies the necessary access rules. In most cases, the MAC address is the only thing the provider identifies you as a user.
Now consider the very real situation.
You, as a law-abiding person, came to a public place, for example, in a cafe or subway car, logged in to the public WiFi-network using your phone number or any other method provided, used the World Wide Web, and then disconnected from the network and left from this place.
At the same time with you in this place there is a certain not quite law-abiding citizen, who has with him the most ordinary laptop, which has the most usual WiFi-adapter capable of working in the monitor-mode and utilities from the aircrack-ng package. With all this, a bad person quietly and quietly listens to the broadcast, noting that the devices with which MAC addresses appeared on the network, exchanged traffic with an access point, and then disconnected from it. It looks like this:
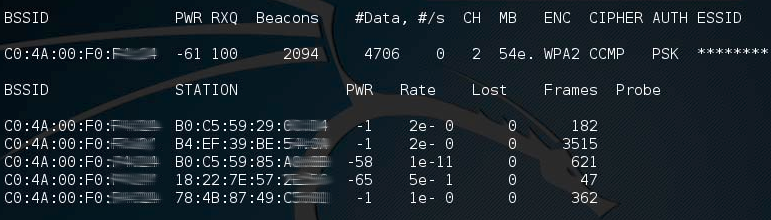
After you leave a place with this WiFi network, a bad person changes the MAC address of the WiFi adapter on his device to the MAC address of your device, connects to the network, the equipment recognizes it as an “old friend” (that is, you) and lets on the Internet without any authorization.
It is worth noting that doing all this can not necessarily with evil intentions. Some people ( all personalities and events are fictional, coincidences are random ) do so to access the WiFi network on the subway without viewing advertisements (by finding the MAC address of the device of the person who paid for the premium account without banners).
Having successfully logged in the network, a bad person can do something that goes against the current legislation - write some message on social networks, like someone else's post or a screenshot from a feature film, in short, to do something that in our time It is considered a violation of Articles 280 and 282 , and in addition another 242 or 272 of the Criminal Code of the Russian Federation.
And here all the fun begins.
Under current law, telecom operators must keep authorization data for at least 6 months. When activating the prosecutor's office and investigators and requesting a service provider from whose network the “offense” was committed, the logs will indicate not the “bad person”, but you as the legal owner of the device with the MAC address from which access was made.
In the ideal case, everything will fall apart even at the stage of pre-investigation checks.
In a good case, you will have to spend time and effort to prove that you have nothing to do with - to attract experts who will justify that the MAC address cannot be a unique identifier of a specific device and a specific user, collect witness testimony and recordings from surveillance cameras (if they will not be removed beyond the statute of limitations) that at the time of the event you were no longer in that place, and pray that the judge would not reject your petitions to admit all this to the materials of the case as “irrelevant”.
There is no need to go far for examples - the case of Dmitry Bogatov , the administrator of the TOR node, from whose IP address the unknown person called for mass riots. Despite the recordings from surveillance cameras, clearly confirming that Dmitriy was at a fitness club at the time of the offense and not at his computer at home, and the expert opinion that the IP address could not be an identifier, Bogatov he was arrested, later under public pressure he was transferred under house arrest, and as a result, the criminal case against him was discontinued only a year later. If this story had not received wide media coverage, and human rights organizations from all over the world would not have stood up for Dmitry, everything could have ended much worse.
In a bad case ... let's not talk about bad cases, everything is clear here.
How can you avoid this? Alas, no way. It all comes down to the imperfection of the authorization and authentication methods of telecom operators, as well as in particular the work of our law enforcement and judicial systems. I do not see technical methods to exclude the possibility of such situations from ordinary users (the option of using SIM cards for unauthorized persons is not considered for the reasons described above). One conclusion suggests itself: do not use public WiFi networks.
It is also worth noting that vigilance should be maintained not only when using public WiFi. Today, the vast majority of home users use the WPA2-PSK encryption protocol on their WiFi routers, which is also subject to brute-force encryption key selection , which, when using simple passwords (and with further development of computing power, not only simple ones) connecting unauthorized persons to the home WiFi-network and accessing the Internet on behalf of the owner of the router. This problem is solved by technical methods (for example, you can configure the equipment so that when you connect to the WiFi network, access is only to the VPN server, through which you can access the outside world, or WPA-802.1X - but in both cases support is needed from iron), but few ordinary people with this will bother, alas.
Source: https://habr.com/ru/post/358866/
All Articles