A story about how I, with the help of Google, found passwords on dozens of Trello public boards
Kushagra Patak deals with information security. On April 25, he discovered that many individuals and companies are posting sensitive information on Trello's public boards. In particular, we are talking about information relating to unrepaired errors and vulnerabilities in programs, account credentials in social networks and in postal services, names and passwords for access to servers and administrators control panels. All of this, as well as other similar information, was on the publicly accessible Trello boards, which are indexed by all search engines, which allows anyone to find this information. In the material, the translation of which we are publishing today, we will talk about how this find was made.

I searched for instances of Jira owned by companies that offer Bug Bounty programs. To do this, use the following search query:
I want to draw your attention to the fact that I used the so-called Google dork queries . Such queries are search strings that include advanced search operators . They are used to search for information that is indexed by search engines, but, during normal work with sites, is not available.
')
During the experiments, I, in the above query, instead of
I was completely shocked by this find.
Why is this a problem? The fact is that Trello is an online tool designed to manage projects and personal tasks. There are entities called boards that are used to manage projects and tasks. The user can customize the visibility of their boards, in particular, setting it to
After I discovered the above problem, I thought it would be interesting to look for similar vulnerabilities related to the unsafe storage of other data, say, mailbox access information.
Then I modified the request so that it was sent to search for Trello boards containing passwords for Gmail accounts.
That's what the search engine issued.
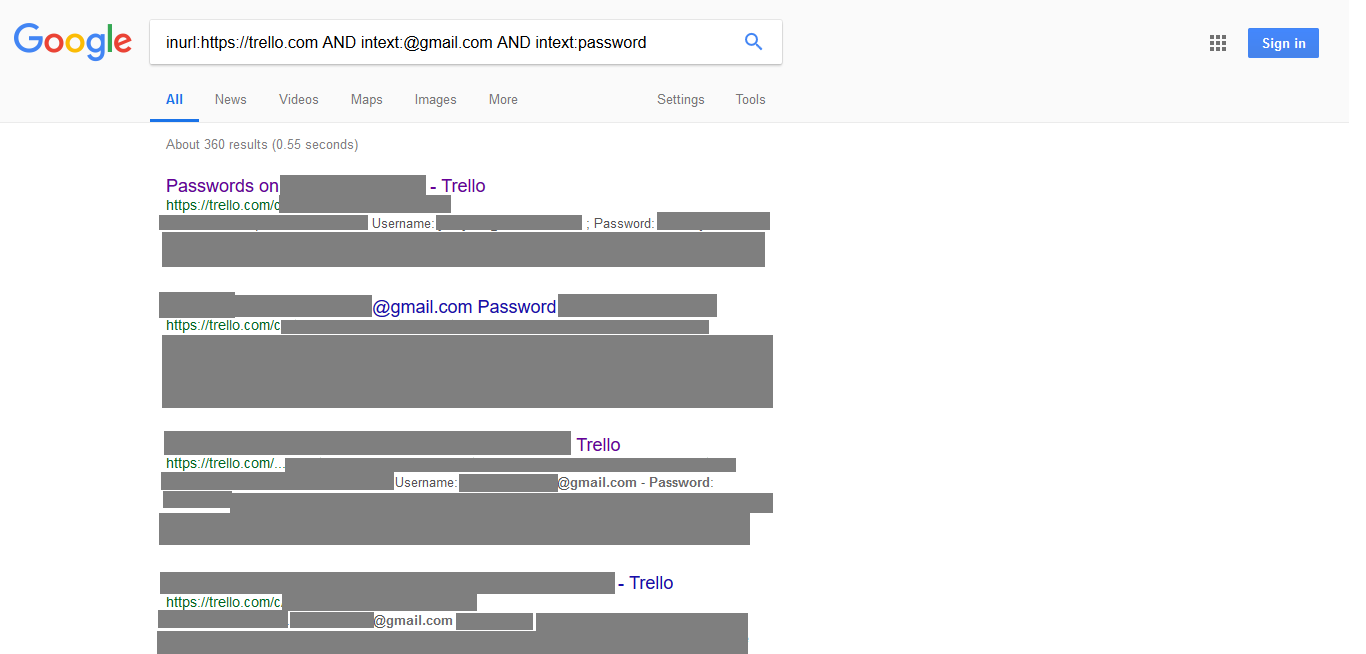
Trello board search with mailbox access credentials
What about SSH and FTP?
Something could be found on these requests.

Search for Trello boards with data for accessing SSH and FTP accounts
After experimenting with queries for hours, I discovered other interesting things. We managed to find them by modifying queries.
Some companies use Trello's public boards to manage work related to bugs and vulnerabilities found in their applications or websites.
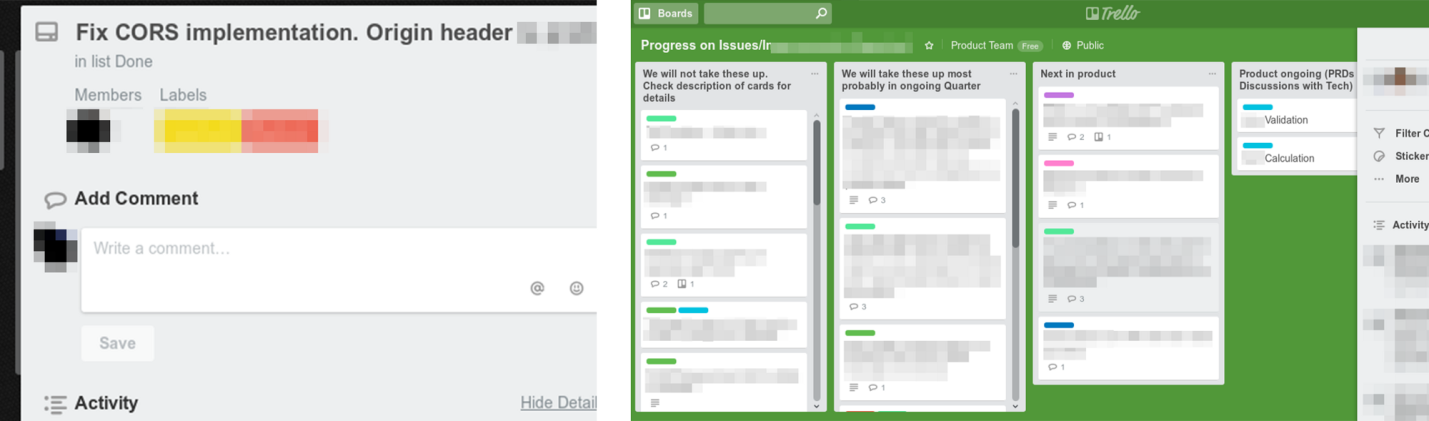
Vulnerability Information Boards
In addition, ordinary people use Trello's public boards as wonderful public password managers for the credentials of the companies in which they work.
Among the examples of what could be discovered are data for access to servers, CMS systems, CRM systems, web analytics systems. There were also the names and passwords of corporate mailboxes, Stripe accounts, AdWords, and social networks. And this is not a complete list of finds.
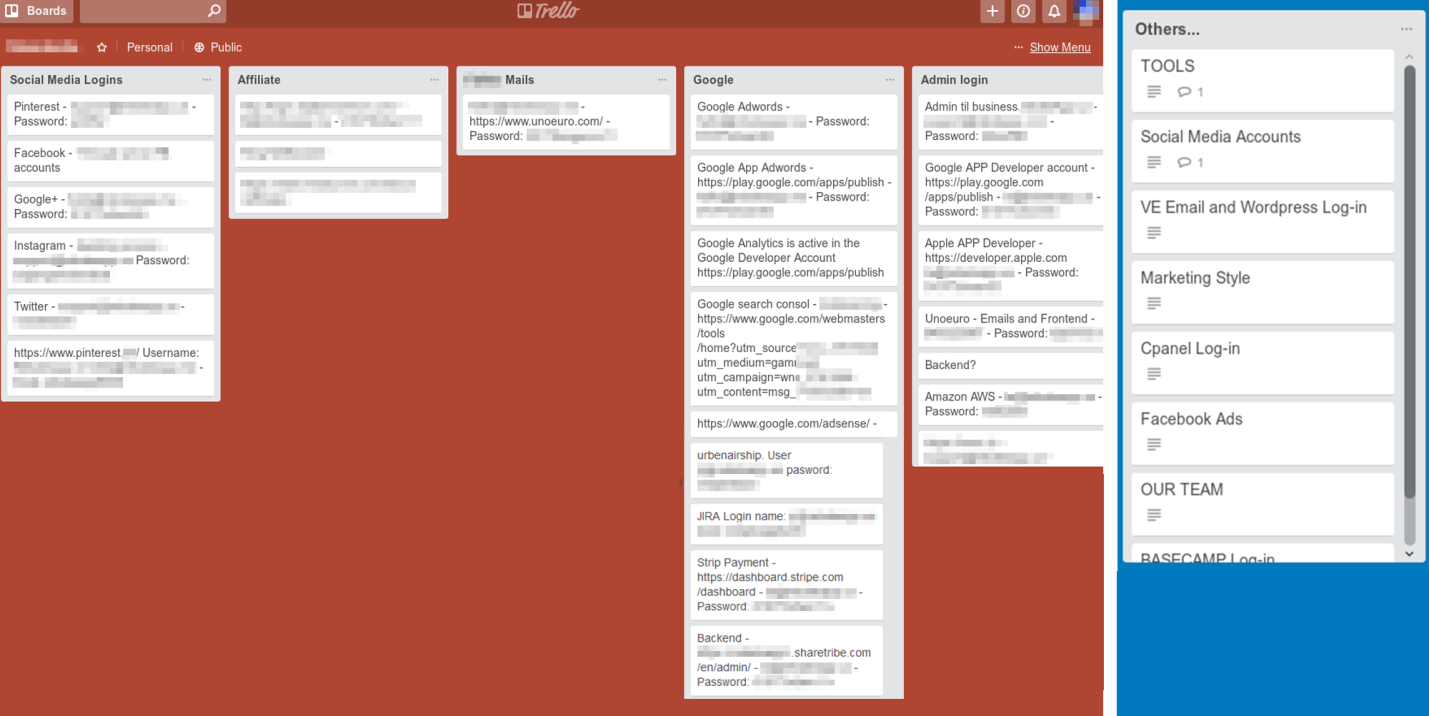
Trello public boards that contain sensitive information
Here is another example.

Information about a database containing personal data and financial information was shared
Before I managed to discover all this, I was not engaged in research aimed at any particular company or Bug Bounty program.
However, nine hours after I discovered this Trello vulnerability, I found contact information for about 25 companies that had leaked sensitive data and informed them about the problem. By the way, finding this contact information was not so easy.
I also made an entry in the private Slack channel, which uses those who participate in Bug Bounty programs, and in the Discord channel dedicated to information security. I, immediately after finding the vulnerability, published the corresponding tweet . The reaction of those who found out about this was similar to mine.
Then I began to receive messages from those who took advantage of the vulnerability I discovered to search for data to access corporate mailboxes, Jira instances and other sensitive information within the framework of Bug Bounty programs.
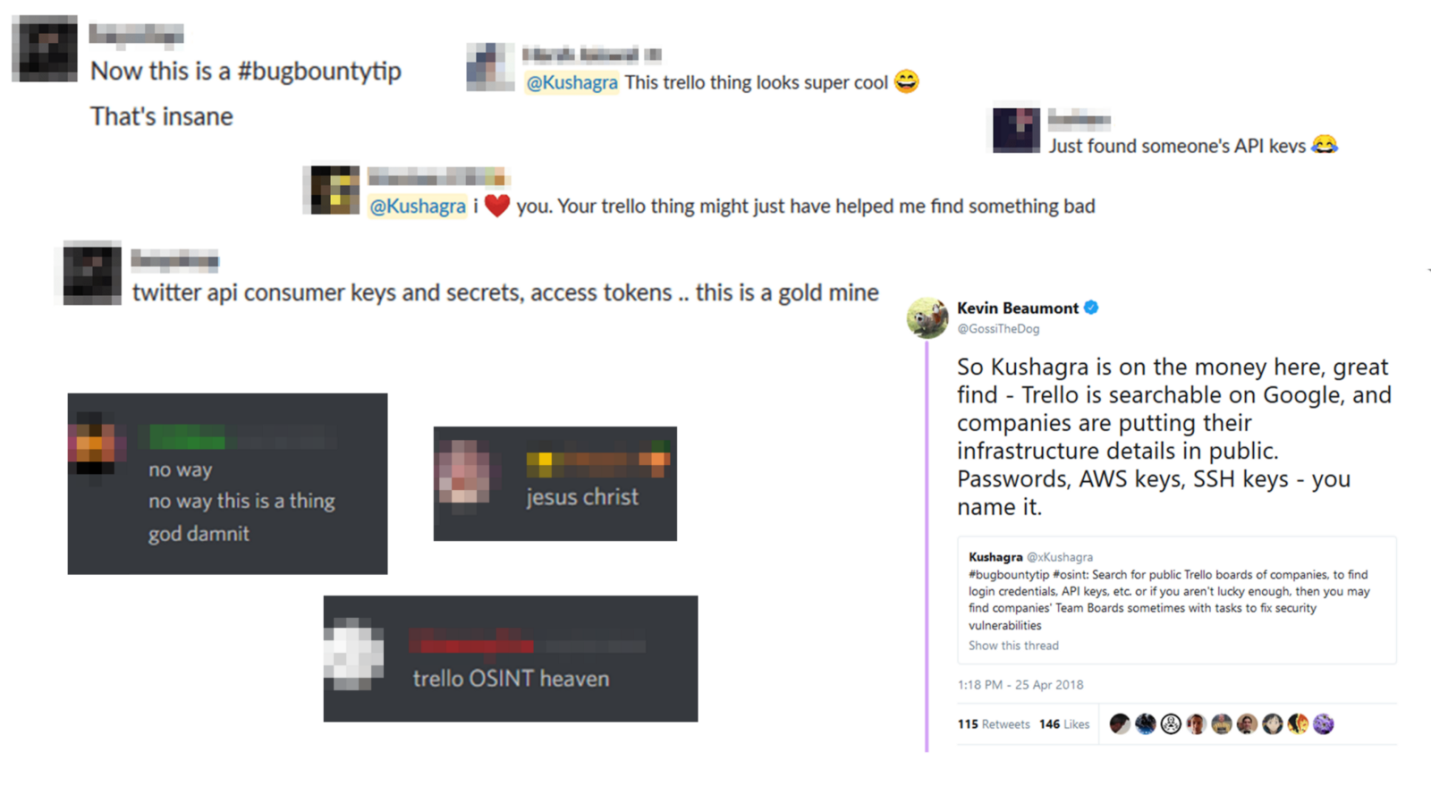
Audience response to a vulnerability message
Approximately 10 hours after the discovery of the vulnerability described here, I focused on researching companies that had Bug Bounty programs. Then - checked one well-known company that organizes the sharing of vehicles, applying the following request:
I immediately found the Trello board, containing data for accessing an employee’s corporate mailbox, and another board with information that was clearly not intended for anyone’s eyes.
In order to make sure that what I found is really confidential data that accidentally went public, I contacted an employee of the security services of this company. I was told that they were already informed about these problems, but asked to send a full report on the vulnerabilities found. Unfortunately, my report was closed as a repeat, as the company later discovered that it had already received a report on the same vulnerability. Then I reported on similar problems in 15 more companies. Some of them were large organizations, but many of them did not have Bug Bounty programs. True, one of them had such a program, and I reported a problem found within this program. Unfortunately, I did not receive any remuneration from them, since the problem I found did not relate to the vulnerabilities they were willing to pay for discovering.
Dear readers! Have you checked your boards in Trello for leaks of confidential information?

History of discovery
I searched for instances of Jira owned by companies that offer Bug Bounty programs. To do this, use the following search query:
inurl:jira AND intitle:login AND inurl:[company_name] I want to draw your attention to the fact that I used the so-called Google dork queries . Such queries are search strings that include advanced search operators . They are used to search for information that is indexed by search engines, but, during normal work with sites, is not available.
')
During the experiments, I, in the above query, instead of
[company_name] , entered Trello . Google issued several results - links to public boards Trello. They contained data to connect to some instances of Jira. It happened at 8:19 AM UTC.I was completely shocked by this find.
Why is this a problem? The fact is that Trello is an online tool designed to manage projects and personal tasks. There are entities called boards that are used to manage projects and tasks. The user can customize the visibility of their boards, in particular, setting it to
After I discovered the above problem, I thought it would be interesting to look for similar vulnerabilities related to the unsafe storage of other data, say, mailbox access information.
Then I modified the request so that it was sent to search for Trello boards containing passwords for Gmail accounts.
inurl:https://trello.com AND intext:@gmail.com AND intext:password That's what the search engine issued.
Trello board search with mailbox access credentials
What about SSH and FTP?
inurl:https://trello.com AND intext:ftp AND intext:password inurl:https://trello.com AND intext:ssh AND intext:password Something could be found on these requests.
Search for Trello boards with data for accessing SSH and FTP accounts
Continuing searches
After experimenting with queries for hours, I discovered other interesting things. We managed to find them by modifying queries.
Some companies use Trello's public boards to manage work related to bugs and vulnerabilities found in their applications or websites.
Vulnerability Information Boards
In addition, ordinary people use Trello's public boards as wonderful public password managers for the credentials of the companies in which they work.
Among the examples of what could be discovered are data for access to servers, CMS systems, CRM systems, web analytics systems. There were also the names and passwords of corporate mailboxes, Stripe accounts, AdWords, and social networks. And this is not a complete list of finds.
Trello public boards that contain sensitive information
Here is another example.
Information about a database containing personal data and financial information was shared
Before I managed to discover all this, I was not engaged in research aimed at any particular company or Bug Bounty program.
However, nine hours after I discovered this Trello vulnerability, I found contact information for about 25 companies that had leaked sensitive data and informed them about the problem. By the way, finding this contact information was not so easy.
I also made an entry in the private Slack channel, which uses those who participate in Bug Bounty programs, and in the Discord channel dedicated to information security. I, immediately after finding the vulnerability, published the corresponding tweet . The reaction of those who found out about this was similar to mine.
Then I began to receive messages from those who took advantage of the vulnerability I discovered to search for data to access corporate mailboxes, Jira instances and other sensitive information within the framework of Bug Bounty programs.
Audience response to a vulnerability message
Approximately 10 hours after the discovery of the vulnerability described here, I focused on researching companies that had Bug Bounty programs. Then - checked one well-known company that organizes the sharing of vehicles, applying the following request:
inurl:https://trello.com AND intext:[company_name] I immediately found the Trello board, containing data for accessing an employee’s corporate mailbox, and another board with information that was clearly not intended for anyone’s eyes.
In order to make sure that what I found is really confidential data that accidentally went public, I contacted an employee of the security services of this company. I was told that they were already informed about these problems, but asked to send a full report on the vulnerabilities found. Unfortunately, my report was closed as a repeat, as the company later discovered that it had already received a report on the same vulnerability. Then I reported on similar problems in 15 more companies. Some of them were large organizations, but many of them did not have Bug Bounty programs. True, one of them had such a program, and I reported a problem found within this program. Unfortunately, I did not receive any remuneration from them, since the problem I found did not relate to the vulnerabilities they were willing to pay for discovering.
Dear readers! Have you checked your boards in Trello for leaks of confidential information?
Source: https://habr.com/ru/post/358624/
All Articles
