Building an extended anti-virus protection system for a small enterprise. Part 2. Antivirus Gateway USG40W by Zyxel

This publication is dedicated to the Zyxel USG40 / USG40W / USG60 / USG60W product line and is a continuation of the series “ Building an Advanced Antivirus Protection System for a Small Enterprise .”
Foreword
In short, what was discussed in the first part and what questions might arise.
Single-stage protection in the form of a corporate antivirus with agents on servers and workstations is not always effective. This can be compared with the post-moderation on the forum, when the moderator responds to a message that has already appeared and managed to cause a certain effect.
To enhance protection, it is necessary to cut off most of the malicious programs (viruses, trojans, etc.) even at the far borders, before penetrating beyond the perimeter of the network. In principle, this is a similar antivirus, but which does not work “under the user's nose”, but much earlier, for example, on the border of the demilitarized zone.
')
For such tasks, a variant with the use of a software and hardware complex is well suited. Firstly, this solution is less vulnerable, secondly, specialized devices do not require powerful hardware, consume less power and are generally more economical.
It should be understood that the capabilities of the equipment are not limitless, so anti-virus software must be adapted for such use cases.
At the same time, it should be a fairly effective, well-proven solution from a reputable manufacturer who can be trusted.
The security gateways we are considering use the Kaspersky Lab Safe Stream II antivirus product. This is a streaming antivirus adapted for use on specialized devices. Therefore, it does not include some features, such as quarantine and deep heuristic analysis. Safe Stream is a fairly reliable "first line of defense" from a well-established anti-virus software vendor that blocks many annoying viruses, trojans, worms.
Also included in the armament modules of anti-spam and content filtering from Cyren Technology .
NOTE . Within a small publication, it is impossible to cover the whole range of solutions related to the concept of information security and protection against malicious code. This series of articles is the first acquaintance with the products USG40 / USG40W / USG60 / USG60W. A full description of the capabilities of these devices can be found here .
Initial Setup and USG40W / USG60W
The following is a description of the procedure for setting up and installing a USG40W device. This information is also valid for other positions from the same line: USG40, USG60 and USG60W.
Reset to factory settings
Strictly speaking, this procedure is not mandatory.
But sometimes before installing “on a new permanent place of residence” it makes sense to return to the default settings and start operation from scratch.
What happens when you return to the factory settings?
When changing settings during operation, the new device configuration is saved in the
startup-config.conf file.Default settings are stored in the
sytem-default.conf file sytem-default.confDuring the factory reset, the
startup-config.conf file is overwritten with the backup sytem-default.conf , and thus the default settings are restored.Step-by-step description of the factory reset procedure:
1. Turn on the device and wait for the full download. Ready signal - stopping the flashing of the SYS indicator. Verify that the SYS LED is on steadily.

Figure 1. USG40W front view. The SYS indicator is highlighted with a red circle.
2. Press the RESET button and hold it until the SYS indicator starts blinking again (it usually takes about 5 seconds).

Figure 2. USG40W rear view. The red circle is the RESET button.
Release the RESET button and wait for the device to restart. During the factory reset procedure, a reboot can take several minutes.
When reset to factory settings, the following values are restored:
- IP Address: 192.168.1.1
- Subnet Mask: 255.255.255.0
- Default login: admin
- Password: 1234
Connect via SSH
Immediately after resetting the settings, you can connect to the device via an SSH connection and get control over the command line interface.
The principles embodied in the command interface of this device are in many ways reminiscent of Cisco IOS, which allows you to quickly familiarize yourself with the appropriate environment.
For example, the command for switching to the privileged mode — enable, parameter inversion through the “no” prefix, as well as the famous hint in the form of the question “?” Correspond to generally accepted standards (or preferences).
Configuring connection settings via the web interface
The address for connecting to the default web interface is 192.168.1.1.

Figure 3. Login window in Zyxel USG40W web-interface.
In some cases, it is necessary to perform additional configuration of security algorithms, in particular, RC4 for HTTPS connections.
The fact is that popular browsers do not use RC4 and DES security algorithms for HTTPS connections. For example, this is the case in Google Chrome, starting with version 48.
A signal to this incompatibility will be a message as in Figure 4 (or similar):
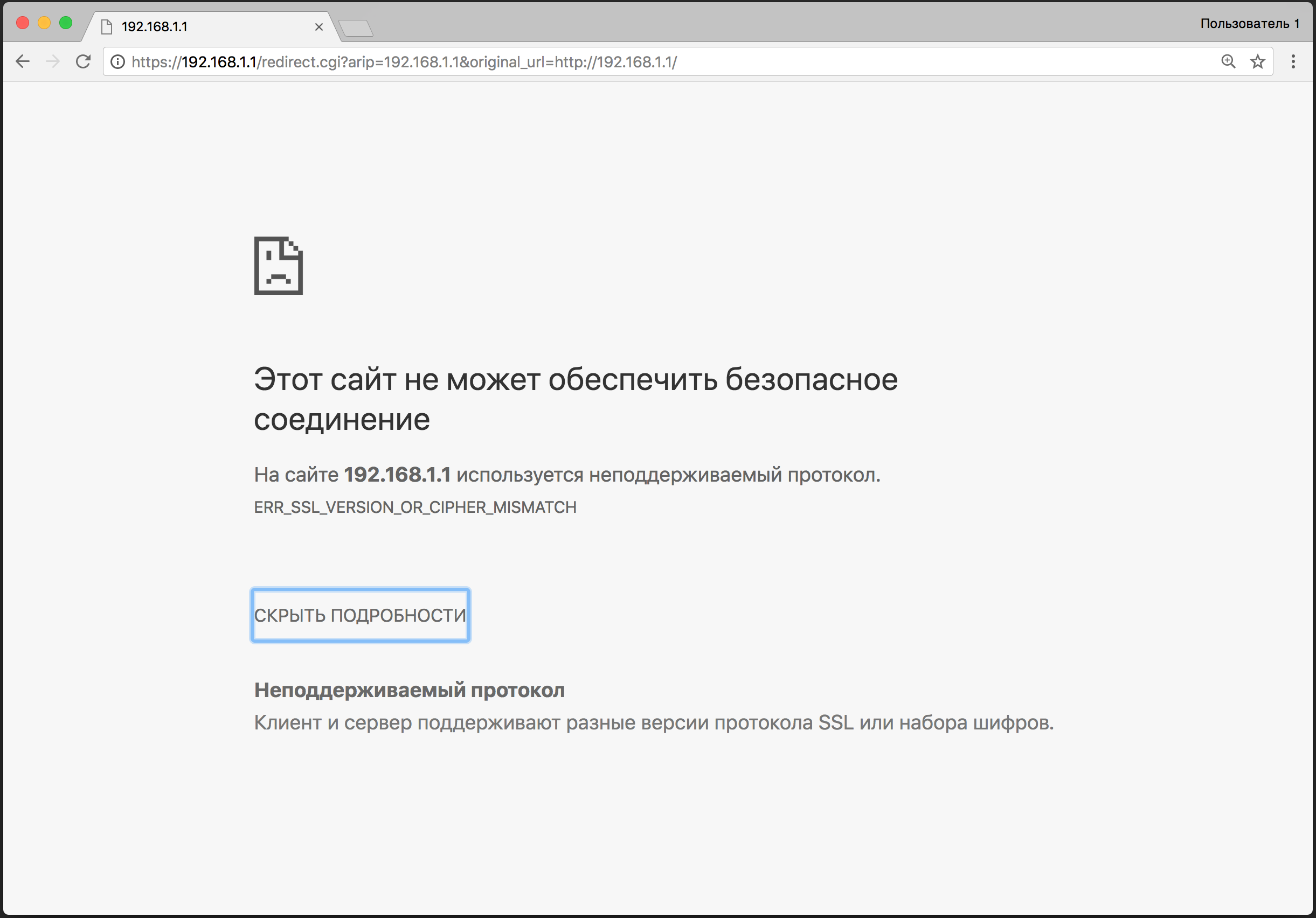
Figure 4. The message about the inaccessibility of the web interface due to the encryption algorithm.
To be able to log in, you need to disable the old RC4 and DES encryption methods.
Then the AES encryption method will be used by default, and the connection via the web interface will be available for all types of browsers that support this algorithm.
Note. To connect via SSH from UNIX-like operating systems (including MAC OS X), you can use the "ssh" command. For operating systems of the MS Windows family, it is recommended to use the PUTTY program.
After connecting to the command line shell, a standard username and password dialog will appear.
Then, after receiving the invitation, enter the command to switch to the privileged mode:
Router> enable Note that just like Cisco IOS, when you switch to privileged mode, the invitation icon “>” has changed to “#”.
Go to configuration mode:
Router# configure terminal Note. If you successfully enter this mode of the system, the word “config” is added to the invitation.
Enter the command to prohibit the old encryption methods RC4 and DES:
Router(config)# no ip http secure-server cipher-suite rc4 Router(config)# no ip http secure-server cipher-suite des Record changes:
Router(config)# write Exit the interface:
Router(config)# exit Router# exit 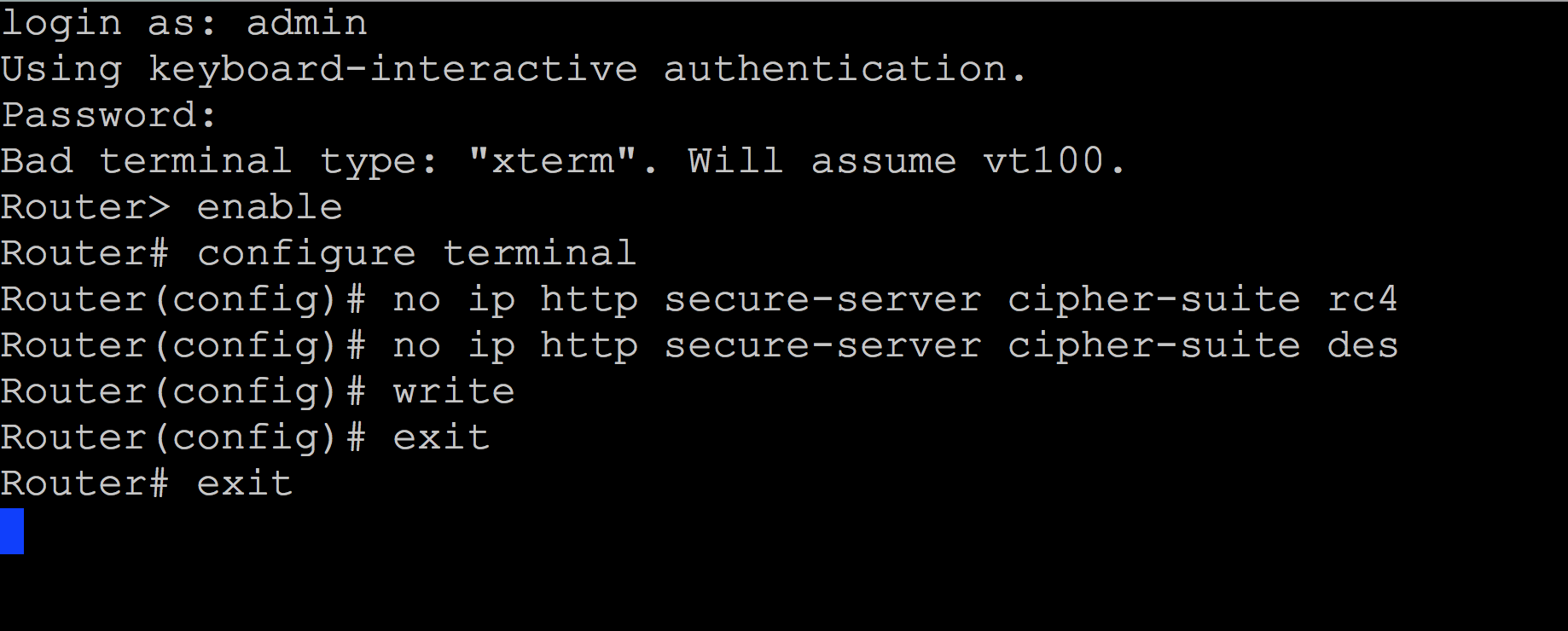
Figure 5. Disabling the old RC4 and DES encryption methods in the CLI.
Note As you can see from the example, when working with devices from Zyxel for specialists who have been trained on the equipment of other vendors, there should be no particular difficulties.
Now, by setting an exception, you can log in to the web interface.

Figure 6. Browser window after setting the correct encryption method.
Then everything is more or less standard: click "Show details" and "Go to the website 192.168.1.1 (unsafe)" will appear. In some cases, for example, for the Windows family, you will be prompted to accept and install the appropriate certificate.
For the first login, you must enter a default login and password.
Immediately after the very first user authentication, they will be asked to change the password.
Introduction to the main modes of the web-interface
In order to simplify the initial entry into work with the new equipment, two main modes are built into the Zyxel USG40 / USG40W / USG60 / USG60W web interface:
- Simple mode - designed for quick configuration of the main modules;
- Advanced mode - to perform fine adjustments and full control over the device.

Figure 7. Simple control mode.
Figure 8. Advanced user mode.
Switching between modes is possible at any time.
In Simple mode, just click on the “Advanced user mode” button in the upper right corner of the screen.
In the "Advanced User" mode - you need to select the menu item "Simple Mode" in the upper right corner of the screen.
When switching, a dialog box opens prompting you to save your selection for the next sessions.

Figure 9 Window save operation mode.
Firmware update
A good practice before starting the setup will be to update the device to the latest firmware.
To do this, go to the section "Service" - the subsection "File Manager" and select the tab. "Firmware Management".

Figure 10. Firmware management.
To search for new updates, just click on the “Check Now” item. If an update is available, a version number greater than the specified one will be displayed.
After “Check Now” you need to click on the cloud icon to the right of the Standby section (you can and Running, only in this case, after downloading the firmware update will immediately go).

Figure 11. Update window via the Internet.
Next, a window will appear asking you to confirm the reboot of the device.
If you select “Yes”, the firmware will start to be installed immediately after the copying is completed, if “No” - it will simply download and install it later, by entering the necessary section and clicking the “Restart” button.
Instead of a conclusion. About specialized courses and first steps
Modern management interface Zyxel allows you to perform many simple operations without prior preparation.
At the same time, there are specialized courses .
It is worth noting that obtaining advanced knowledge on the issue with which you have to work is a very good thing and sooner or later there is a need for such training.
However, to master the work with the equipment Zyxel - not necessarily becoming just a network engineer. A general system administrator who alone performs IT infrastructure maintenance work can independently cope with many aspects of configuring such devices. Affordable management and good documentation allows you to solve many questions without in-depth immersion in the nuances of the command line interface. You can immediately perform the initial settings in the Simple mode of management, and already as you master it, attain the maximum level of adaptation to the IT infrastructure.
Sources
- Building an extended anti-virus protection system for a small enterprise. Part 1 . The choice of strategies and solutions.
- Product Page Kaspersky SafeStream II
- Cyren Technology website (antispam and content filtering)
- Next Generation Unified Security Products Section USG40 / USG40W / USG60 / USG60W
- Information on specialized Zyxel courses
Source: https://habr.com/ru/post/358612/
All Articles