How is AADHAAR - the largest biometric system in the world
The Indian project Aadhaar is the largest biometric system in the world, in which more than 1.1 billion users are already registered. In the previous article I talked about the stages of development of the project, now I will move on to how the system works.

Aadhaar is an Indian online authentication service provided by the state agency UIDAI . Organizations (banks, government agencies, etc.) transmit the Aadhaar number and read biometric data of the user (one or more fingerprint templates or iris of the eye). In response, the service gives the answer "yes / no." Additionally (Aadhaar e-KYC service), the user's personal data can be verified with the obligatory consent.
In total, the system has more than 1.1 billion users; each account has: 10 biometric fingerprint templates, 2 iris templates, a photo and personal data (address, gender, date of birth). Total database occupies ~ 25 PB.
')
The current system load is up to 20 million requests per day (an average of 100 requests per second with a peak value of 500 requests - at the beginning and end of the working day of civil servants), the system is designed for 40 million requests. It is planned to modernize the equipment with the calculation of up to 100 million requests per day.
At the initial stage, when the database was “total” for 84 million people, UIDAI analyzed the system’s performance. I'll start with the numbers:
Failure to Enroll Rate (FTE) - 0% . Error adding to system. Aadhaar get everything.
Biometric Failure to Enroll Rate (B-FTE) - 0.14% . This is the number of users who can not be uniquely identified using biometric data, they must be checked manually. According to preliminary calculations, the system would be operational at B-FTE <15%.
False Positive Identification Rate (FPIR) - 0.057% . The percentage of duplicate errors found. This means that with a maximum load of 1 million new users per day, 570 people need to be checked manually.
False Negative Identification Rate (FNIR) - 0.0352% . The percentage of missed duplicates.
Poor quality fingerprints - 2.9% . The percentage of users with low quality prints. For these users, it is preferable to use the identification by the iris.
Poor quality fingerprint and poor quality irises: 0.23% - The percentage of users who, due to the poor quality of the biometric templates (and the fingerprint and iris of the eye), are subject to authentication errors.
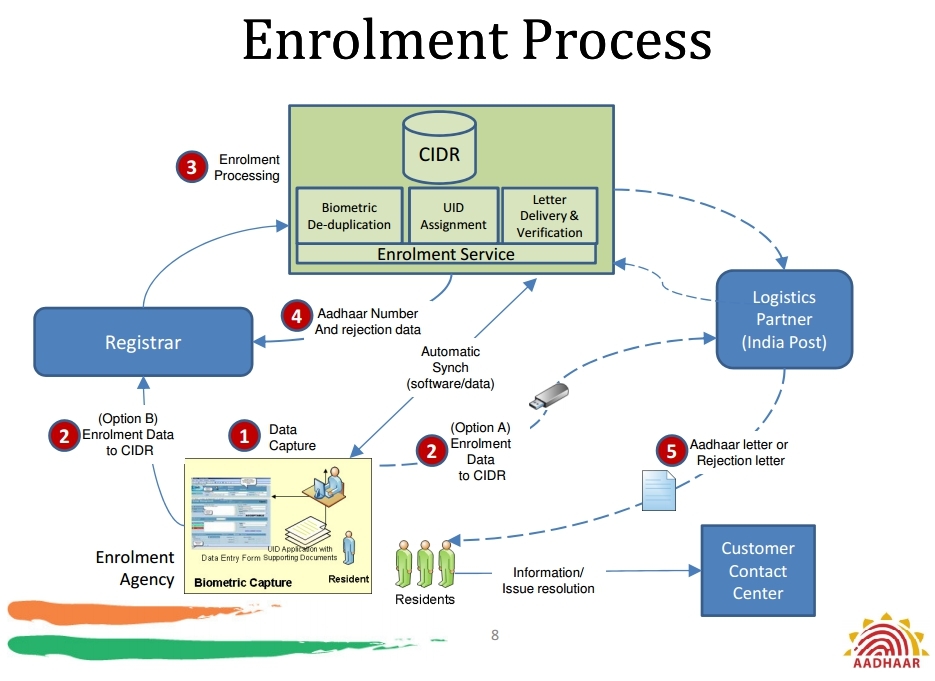
In the diagram below, the process of processing new user data:

The collection of biometric and personal data of users is carried out by certified organizations (Enrollment Center) at workstations of specially trained operators, where an offline application is installed. From the data received from the user, the package (Enrollment package) is formed, which is supplemented with data about the operator, the time of data collection and is encrypted. The size of one package is up to 5 MB (mostly 2-3), the maximum load was 1 million new users per day.
All packets are sent to the CIDR (Central Identities Data Repository). Synchronization with CIDR should be done at least once every two days. All data from workstations is deleted after a response has been received from CIDR about the successful creation of Aadhaar. Upon completion of the verification, the original images of the fingerprint and iris are stored in CIDR and stored separately.
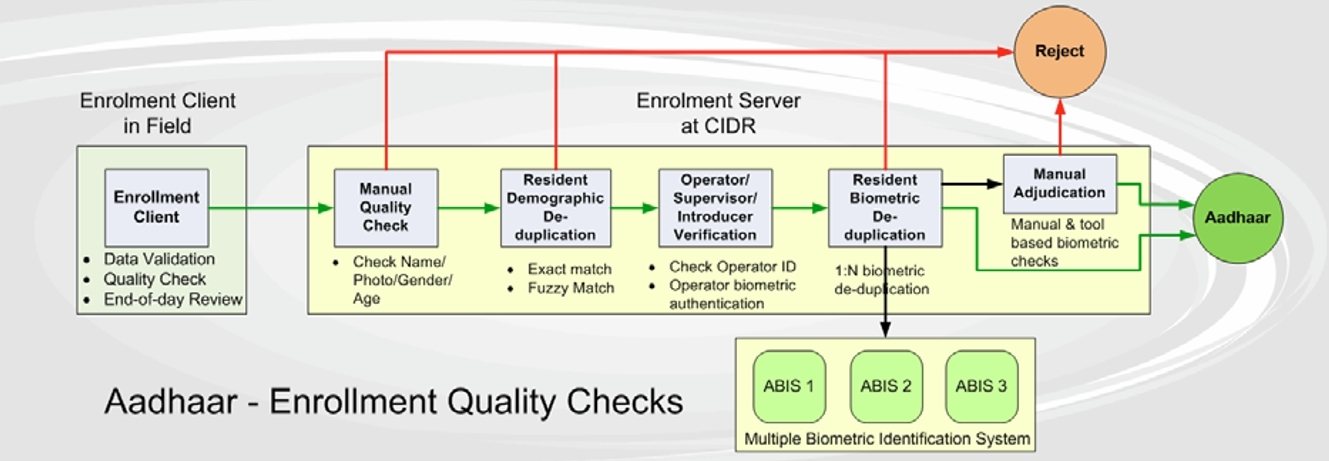
CIDR first checks for duplication, falsification and malware, then enters the processing: personal and then biometric data is checked. To do this, use 3 automatic biometric systems (ABIS - Automatic Biometric Identification System) from different developers, combined into one Multi-ABIS. ABIS works in parallel, but suspicious registrations or poor quality data are additionally passed through all ABIS. When a duplicate is found, it is processed first by a special SDK for scanning errors, and then transmitted for manual verification. For 97% of users, the process of adding to the database takes less than 5 minutes.
It was found that 20% of well-defined duplicates are the result of mixed identification caused by operator errors. Another 20% of duplicates accounted for the coincidence of patterns from different people. To reduce these figures, the UIDAI adjusted the client software to reduce the role of operators.

In order to receive the service, the user enters his Aadhaar number or local identifier and is identified on the biometric terminal. From the received data (biometric template + number), an XML request is generated, which is sent to the server of the organization providing the service (AUA - Authentication User Agency). On the server, the request is supplemented with data from the AUA itself and is sent to CIDR via the ASA server (Authentication Service Agency). Here, the biometric data is verified (in 1 to 1 mode) and a yes / no answer is issued, which is returned to the AUA server and confirms / denies the service. Verification in 98% of cases takes less than 1 second. With a large number of false operations Aadhaar number will be blocked. The number of authentication attempts is not fixed and depends on a number of factors.

A separate API describes the work of Aadhaar e-KYC. With its help, with successful user authentication, you can check personal data stored in the CIDR address, date of birth, get a photo of the user and an electronic copy of the Aadhaar issuance letter. Thus, the bank, mobile operator, etc. can quickly and accurately fill and verify customer data.
Access to this service is limited: you must first register as an AUA, make 300,000 transactions in 3 months and get a separate permission from UIDAI. CIDR is accessed through the KYC Service Agency (KSA) server.
The issue of security is one of the most painful when discussing such projects. UIDAI has been criticized for it almost from day one. Below is a diagram of the system protection levels:
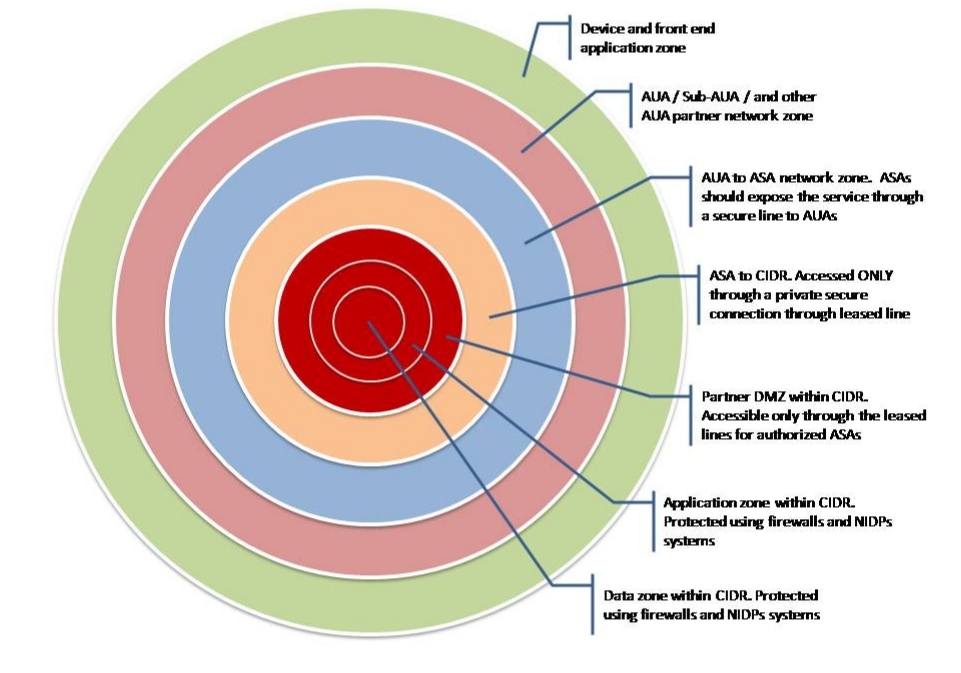
Data security to ASA servers is under the responsibility of the AUA and is described in a separate document. From the required items:
- The entered data should be encrypted already on the device and should be stored only until the transaction is completed;
- Within the AUA systems, users must use local identifiers (driver's license, one-time password, student ID, etc.), which are matched with the Aadhaar number.
- If the operation is carried out by an operator, he must pass identification, for example, using his Aadhaar number;
- The obtained biometric data for authentication is generally not allowed to be stored anywhere;
- A dedicated and secure communication channel or SSL must be used to communicate with the ASA.
Directly to the CIDR have access only ASA. Large AUA can afford their ASA, but smaller ones are required to connect through someone else.
ASA must meet the following requirements:
- Connection to CIDR only through a dedicated and secure channel,
- Transaction data must be stored for at least 6 months,
- User IDs, encryption keys used for authentication, are generally not allowed to be stored anywhere.
At the beginning of the year, news appeared that criminal cases were instituted against several organizations that allowed illegal authentication using stored biometric data. The violation was revealed when it turned out that one person had performed 397 biometric transactions from July 14, 2016 to February 19, 2017. And in March, UIDAI announced the update of encryption keys on all devices by June 1.

At the very beginning it was possible to add to the system again, or under an assumed name. So your Aadhaar number appeared in several Hindu Gods: Brahma, Hanuman. UIDAI covered this loophole and now for such jokes, as in the example with the owner of the dog, you can go to court. Also, there are already precedents when sent to court for re-registration.
The collection of biometric data and the issuance of Aadhaar-numbers - the procedure is free. Sometimes operators selflessly fight this injustice, refusing to work with users without a bribe. They are either not at all in the workplace, or "sorry, we have no connection to the server." Ostap Bender would be pleased.
But there is no UIDAI. Over the past 3 months, about 1,000 unscrupulous operators were identified and then dismissed and fined. And one of the Aadhaar centers was blocked for 10 years for leaking the personal data of a popular cricketer from there.
PS That's all for now, and a small bonus to those who read to the end. A little national humor that Aadhaar will soon begin to appropriate and cows))

general description
Aadhaar is an Indian online authentication service provided by the state agency UIDAI . Organizations (banks, government agencies, etc.) transmit the Aadhaar number and read biometric data of the user (one or more fingerprint templates or iris of the eye). In response, the service gives the answer "yes / no." Additionally (Aadhaar e-KYC service), the user's personal data can be verified with the obligatory consent.
In total, the system has more than 1.1 billion users; each account has: 10 biometric fingerprint templates, 2 iris templates, a photo and personal data (address, gender, date of birth). Total database occupies ~ 25 PB.
')
The current system load is up to 20 million requests per day (an average of 100 requests per second with a peak value of 500 requests - at the beginning and end of the working day of civil servants), the system is designed for 40 million requests. It is planned to modernize the equipment with the calculation of up to 100 million requests per day.
Add users

At the initial stage, when the database was “total” for 84 million people, UIDAI analyzed the system’s performance. I'll start with the numbers:
Failure to Enroll Rate (FTE) - 0% . Error adding to system. Aadhaar get everything.
Biometric Failure to Enroll Rate (B-FTE) - 0.14% . This is the number of users who can not be uniquely identified using biometric data, they must be checked manually. According to preliminary calculations, the system would be operational at B-FTE <15%.
False Positive Identification Rate (FPIR) - 0.057% . The percentage of duplicate errors found. This means that with a maximum load of 1 million new users per day, 570 people need to be checked manually.
False Negative Identification Rate (FNIR) - 0.0352% . The percentage of missed duplicates.
Poor quality fingerprints - 2.9% . The percentage of users with low quality prints. For these users, it is preferable to use the identification by the iris.
Poor quality fingerprint and poor quality irises: 0.23% - The percentage of users who, due to the poor quality of the biometric templates (and the fingerprint and iris of the eye), are subject to authentication errors.
In the diagram below, the process of processing new user data:

The architecture of this subsystem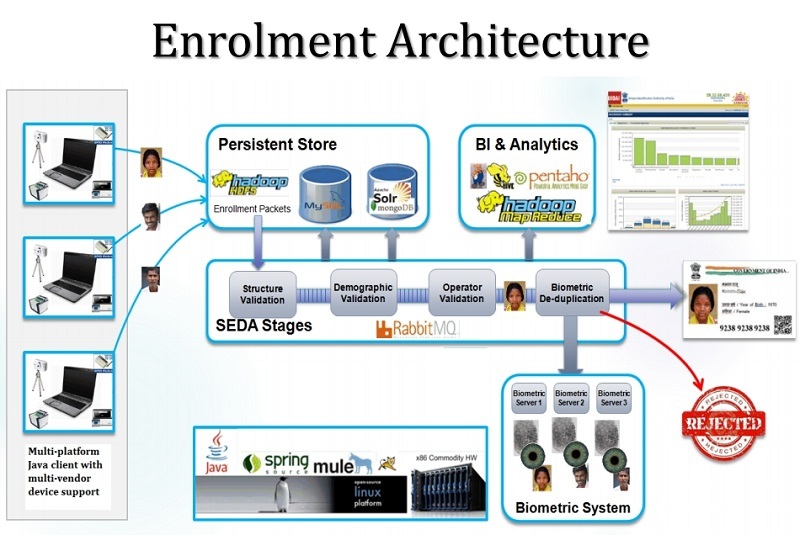

The collection of biometric and personal data of users is carried out by certified organizations (Enrollment Center) at workstations of specially trained operators, where an offline application is installed. From the data received from the user, the package (Enrollment package) is formed, which is supplemented with data about the operator, the time of data collection and is encrypted. The size of one package is up to 5 MB (mostly 2-3), the maximum load was 1 million new users per day.
All packets are sent to the CIDR (Central Identities Data Repository). Synchronization with CIDR should be done at least once every two days. All data from workstations is deleted after a response has been received from CIDR about the successful creation of Aadhaar. Upon completion of the verification, the original images of the fingerprint and iris are stored in CIDR and stored separately.

The duration of each step

CIDR first checks for duplication, falsification and malware, then enters the processing: personal and then biometric data is checked. To do this, use 3 automatic biometric systems (ABIS - Automatic Biometric Identification System) from different developers, combined into one Multi-ABIS. ABIS works in parallel, but suspicious registrations or poor quality data are additionally passed through all ABIS. When a duplicate is found, it is processed first by a special SDK for scanning errors, and then transmitted for manual verification. For 97% of users, the process of adding to the database takes less than 5 minutes.
It was found that 20% of well-defined duplicates are the result of mixed identification caused by operator errors. Another 20% of duplicates accounted for the coincidence of patterns from different people. To reduce these figures, the UIDAI adjusted the client software to reduce the role of operators.
Authentication process

In order to receive the service, the user enters his Aadhaar number or local identifier and is identified on the biometric terminal. From the received data (biometric template + number), an XML request is generated, which is sent to the server of the organization providing the service (AUA - Authentication User Agency). On the server, the request is supplemented with data from the AUA itself and is sent to CIDR via the ASA server (Authentication Service Agency). Here, the biometric data is verified (in 1 to 1 mode) and a yes / no answer is issued, which is returned to the AUA server and confirms / denies the service. Verification in 98% of cases takes less than 1 second. With a large number of false operations Aadhaar number will be blocked. The number of authentication attempts is not fixed and depends on a number of factors.
Aadhaar e-KYC

A separate API describes the work of Aadhaar e-KYC. With its help, with successful user authentication, you can check personal data stored in the CIDR address, date of birth, get a photo of the user and an electronic copy of the Aadhaar issuance letter. Thus, the bank, mobile operator, etc. can quickly and accurately fill and verify customer data.
Access to this service is limited: you must first register as an AUA, make 300,000 transactions in 3 months and get a separate permission from UIDAI. CIDR is accessed through the KYC Service Agency (KSA) server.
Security
The issue of security is one of the most painful when discussing such projects. UIDAI has been criticized for it almost from day one. Below is a diagram of the system protection levels:

Data security to ASA servers is under the responsibility of the AUA and is described in a separate document. From the required items:
- The entered data should be encrypted already on the device and should be stored only until the transaction is completed;
- Within the AUA systems, users must use local identifiers (driver's license, one-time password, student ID, etc.), which are matched with the Aadhaar number.
- If the operation is carried out by an operator, he must pass identification, for example, using his Aadhaar number;
- The obtained biometric data for authentication is generally not allowed to be stored anywhere;
- A dedicated and secure communication channel or SSL must be used to communicate with the ASA.
Directly to the CIDR have access only ASA. Large AUA can afford their ASA, but smaller ones are required to connect through someone else.
ASA must meet the following requirements:
- Connection to CIDR only through a dedicated and secure channel,
- Transaction data must be stored for at least 6 months,
- User IDs, encryption keys used for authentication, are generally not allowed to be stored anywhere.
At the beginning of the year, news appeared that criminal cases were instituted against several organizations that allowed illegal authentication using stored biometric data. The violation was revealed when it turned out that one person had performed 397 biometric transactions from July 14, 2016 to February 19, 2017. And in March, UIDAI announced the update of encryption keys on all devices by June 1.
Human factor

At the very beginning it was possible to add to the system again, or under an assumed name. So your Aadhaar number appeared in several Hindu Gods: Brahma, Hanuman. UIDAI covered this loophole and now for such jokes, as in the example with the owner of the dog, you can go to court. Also, there are already precedents when sent to court for re-registration.
The collection of biometric data and the issuance of Aadhaar-numbers - the procedure is free. Sometimes operators selflessly fight this injustice, refusing to work with users without a bribe. They are either not at all in the workplace, or "sorry, we have no connection to the server." Ostap Bender would be pleased.
But there is no UIDAI. Over the past 3 months, about 1,000 unscrupulous operators were identified and then dismissed and fined. And one of the Aadhaar centers was blocked for 10 years for leaking the personal data of a popular cricketer from there.
PS That's all for now, and a small bonus to those who read to the end. A little national humor that Aadhaar will soon begin to appropriate and cows))
Source: https://habr.com/ru/post/358170/
All Articles