Roskomnadzor starts a war against proxies and VPN

According to reports in Telegram channels and in the media , in particular on the Zatelecom channel (led by Mikhail Klimarev, Executive Director of the Internet Protection Society), the RKN is launching a new round of struggle with the messenger: this time, the proxies and VPN services located directly at the hosting end up providers.
The blocking mechanism is presumably:
')
- Mail.ru's powers (network 128.140.168.0/21 and in particular 128.140.175.98) scans the Internet for proxies and VPN services that allow access to Telegram.
- Abuse is sent to the hoster (some report a direct hit on the RKN ban)
- Hoster terminates the service
Or, some hosters, like at KDPV, for example, are beginning to preemptively suspend their services.
Mail.ru itself denies the charges and transfers the arrows to a certain "tenant-client"
A possible way to deal with this is to send packets from 128.140.168.0/21 and not only to / dev / null.
Full list of Mail.ru networks
thank you orlovdl
5.61.16.0/21
5.61.232.0/21
79.137.157.0/24
79.137.174.0/23
79.137.183.0/24
94.100.176.0/20
95.163.32.0/19
95.163.212.0/22
95.163.216.0/22
95.163.248.0/21
128.140.168.0/21
178.22.88.0/21
178.237.16.0/20
185.5.136.0/22
185.6.244.0/22
185.16.148.0/22
185.16.244.0/22
188.93.56.0/21
194.186.63.0/24
195.211.20.0/22
195.211.128.0/22
195.218.168.0/24
195.218.190.0/23
208.87.93.0/24
208.87.94.0/23
217.20.144.0/20
217.69.128.0/20
2a00: 1148 :: / 29
2a00: 1148 :: / 32
2a00: a300 :: / 32
2a00: b4c0 :: / 32
2a00: 1148: 5 :: / 48
A set of commands for ufw from cooladmin
5.61.16.0/21
5.61.232.0/21
79.137.157.0/24
79.137.174.0/23
79.137.183.0/24
94.100.176.0/20
95.163.32.0/19
95.163.212.0/22
95.163.216.0/22
95.163.248.0/21
128.140.168.0/21
178.22.88.0/21
178.237.16.0/20
185.5.136.0/22
185.6.244.0/22
185.16.148.0/22
185.16.244.0/22
188.93.56.0/21
194.186.63.0/24
195.211.20.0/22
195.211.128.0/22
195.218.168.0/24
195.218.190.0/23
208.87.93.0/24
208.87.94.0/23
217.20.144.0/20
217.69.128.0/20
2a00: 1148 :: / 29
2a00: 1148 :: / 32
2a00: a300 :: / 32
2a00: b4c0 :: / 32
2a00: 1148: 5 :: / 48
A set of commands for ufw from cooladmin
More proofs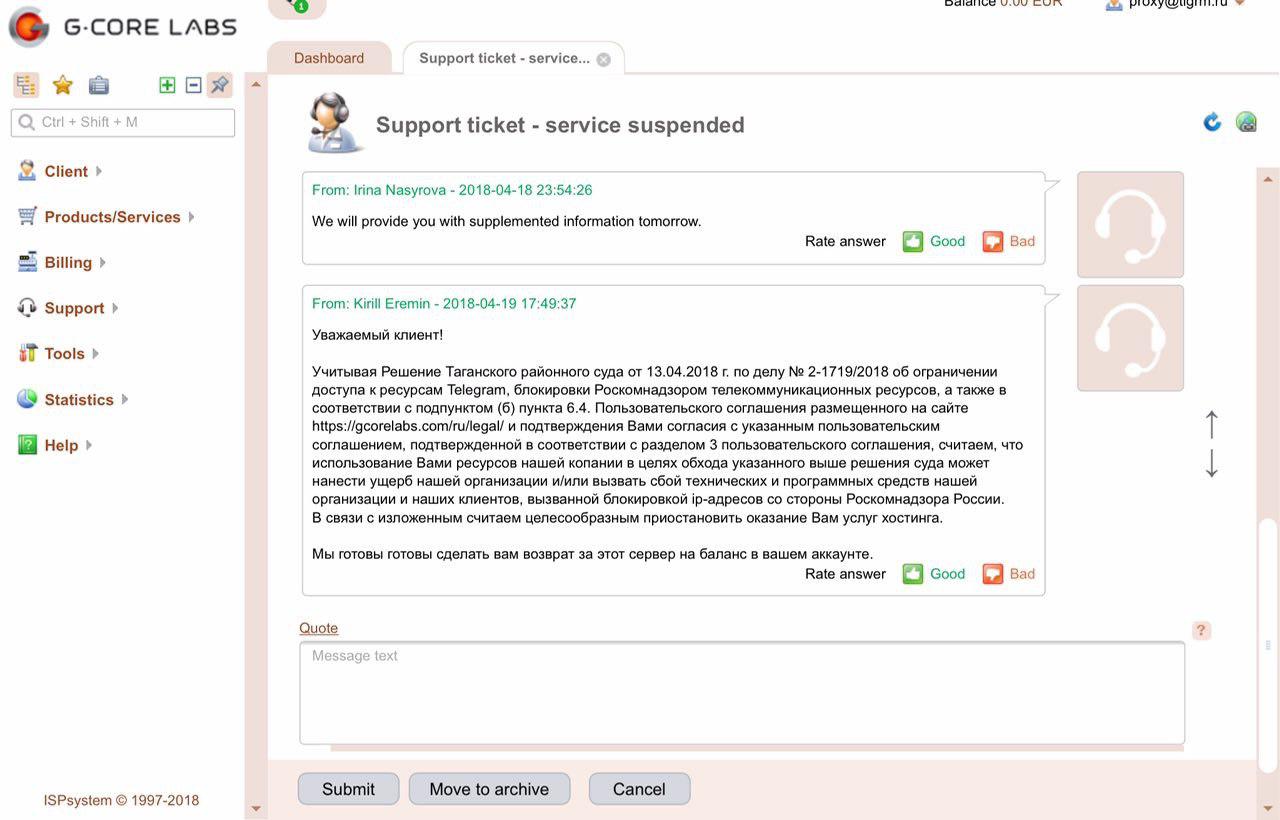
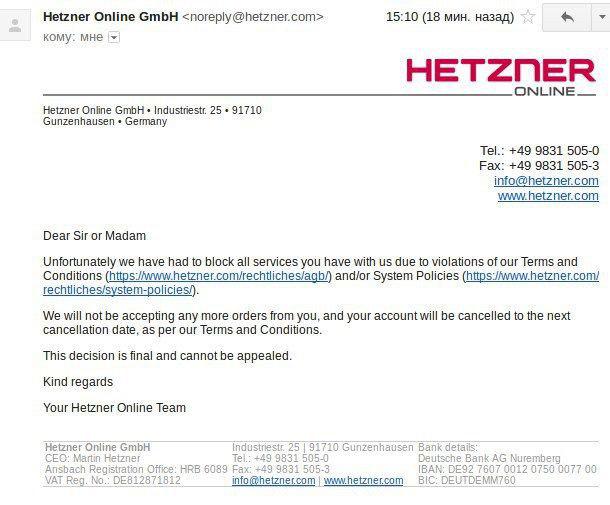


Thus, in addition to the obvious AWS, DO, GCC, Hetzner, Hostland, GCoreLabs, Fozzy, FastVPS and, probably, many others are also under the gun.
Source: https://habr.com/ru/post/357990/
All Articles