Attack of BitErrant with SHA-1 collisions: create different .exe with the same .torrent file
On February 23, 2017, Google and the Center for Mathematics and Computer Science in Amsterdam presented the first collision generation algorithm for SHA-1 . This finding was the result of a two-year study, which began shortly after the publication in 2013 of the work of the cryptographer Mark Stevens from the Center for Mathematics and Computer Science in Amsterdam on the theoretical approach to creating a SHA-1 collision. He further continued the search for practical methods of hacking. Now, together with colleagues from Google, he published a scientific paper , which describes the general principles of generating documents with message blocks prone to SHA-1 collisions ( SHAttered attack).
It immediately became clear how dangerous the attack can be, because the outdated cryptographic hash function SHA-1 is still widely used, including in applications and security protocols, including TLS and SSL, PGP, SSH, S / MIME, IPsec. The SHA-1 hashes are used in different Git, Mercurial, and other version control systems to verify the content and detect data corruption (see Torvalds' comment on collisions in Git). The SHA-1 hashes are even used in the Wii game console to verify signatures at boot time. The use of SHA-1 is legally required by some government organizations. And the most interesting thing for the topic of this article is SHA-1 hashes are used in the BitTorrent peering network protocol for file exchange over the Internet.
In short, how BitTorrent works, namely how the torrent file works.
')
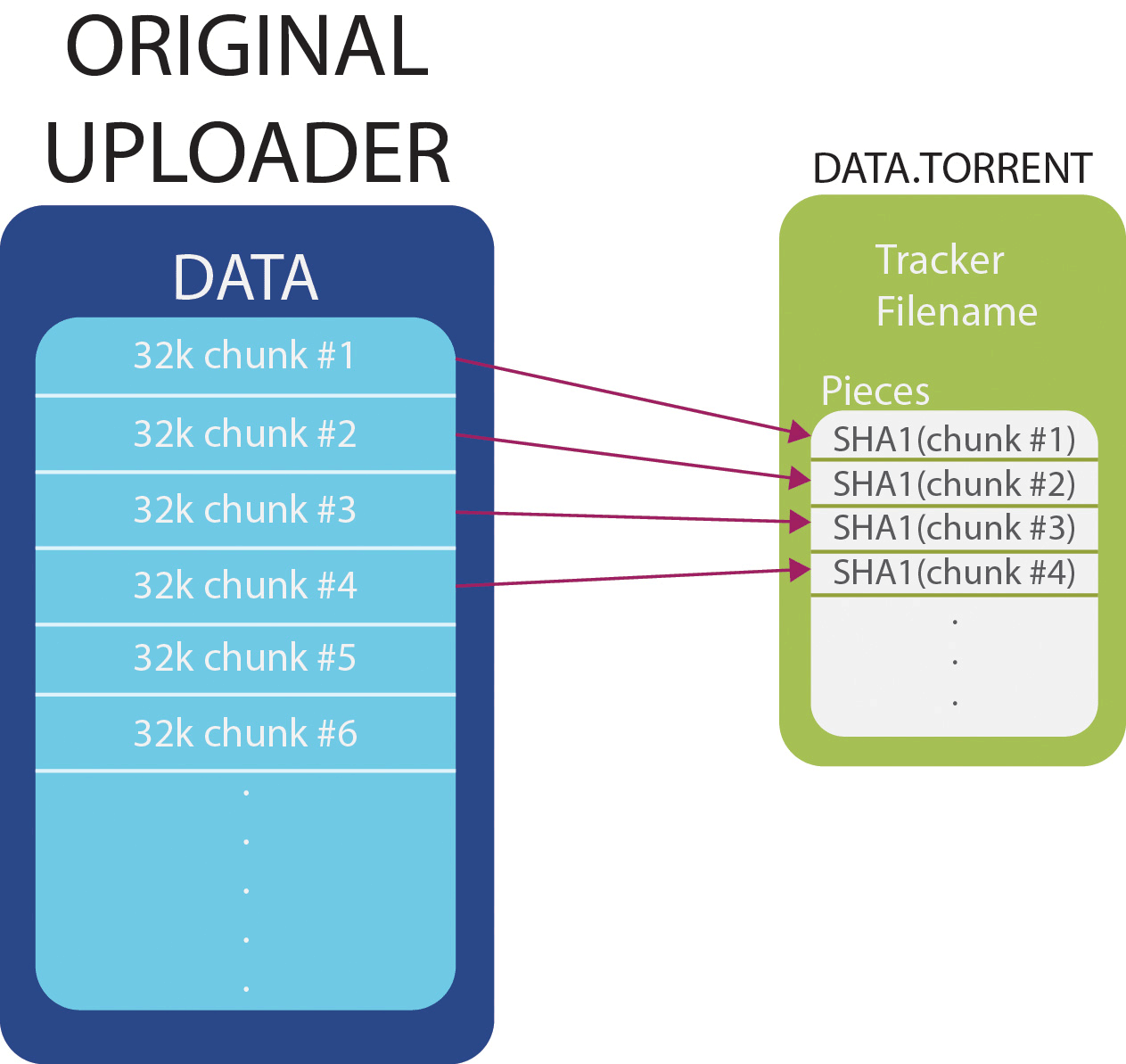
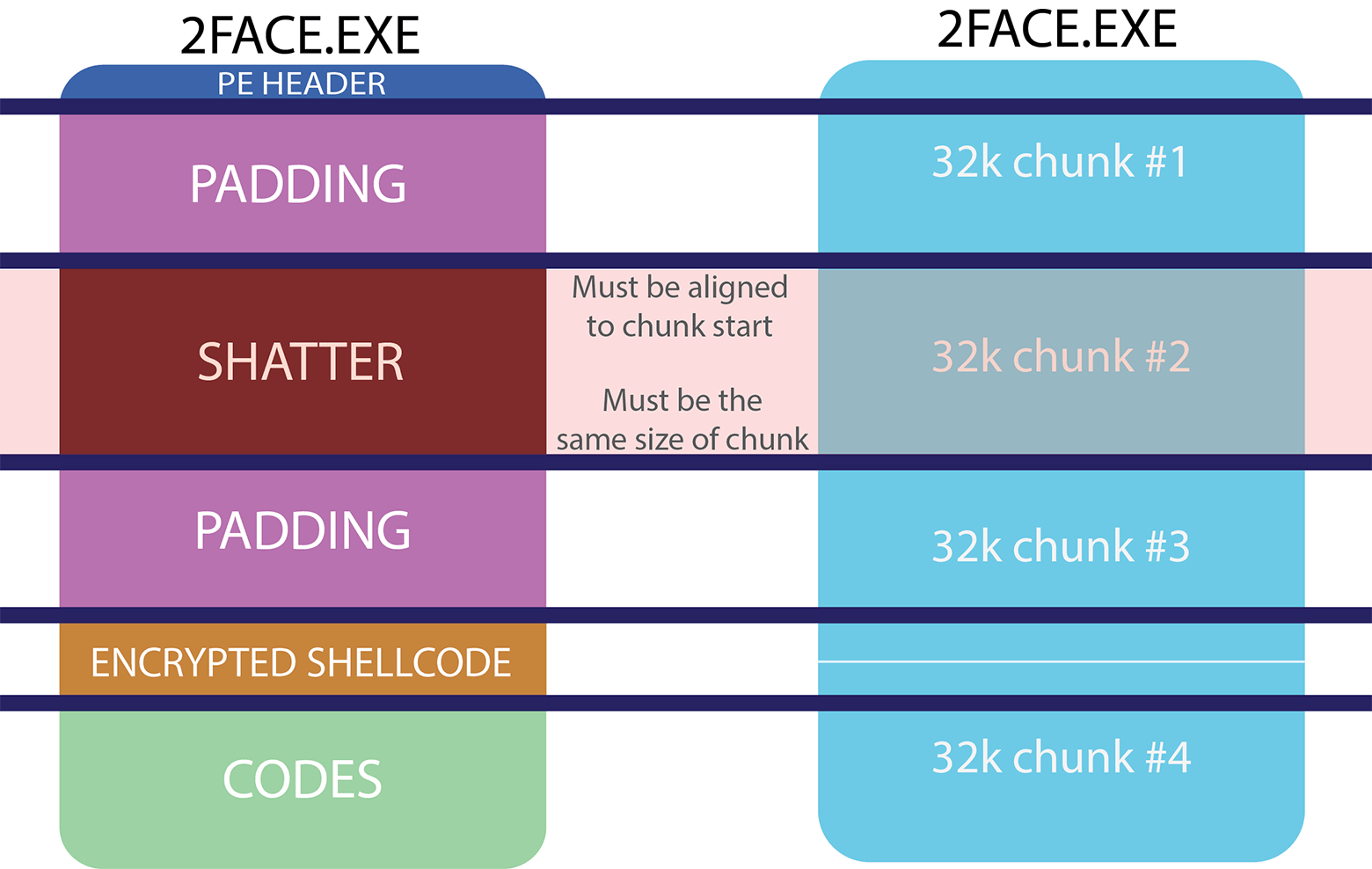
To distribute a file through torrents, in the first step, you need to generate a special torrent file with the extension .torrent (DATA.torrent) from this file (DATA). The original file is divided into a certain number of segments (chunks), for each of them the SHA-1 hash is calculated. All received hashes are connected together and stored in the torrent file in the line of
pieces under the common key of the dictionary. The length of this string is 20 * the number of pieces.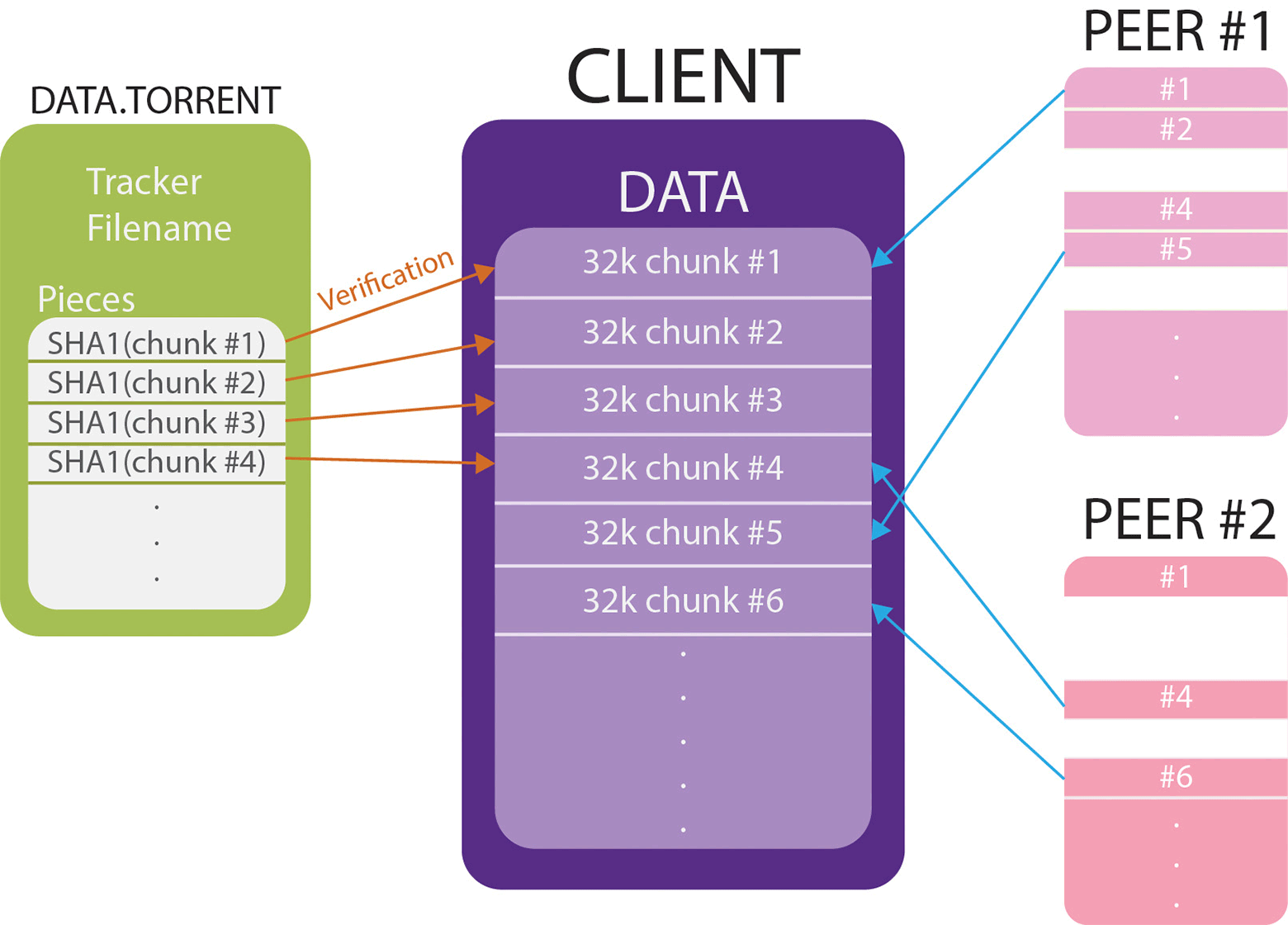
When someone tries to download a file (DATA) via BitTorrent, he first needs to download the torrent file DATA.torrent and parse it. Based on the information from this file, the client searches for peers and downloads segments of the original file (DATA). To protect against peers who are trying to slip malicious data, the client checks each segment with its hash from the torrent file. If the hash in the torrent file does not match the SHA1 hash in the downloaded fragment, then the bad fragment is rejected.
Now the attack vector becomes clear.

An attacker can create an executable file that, when executed, does not do anything forbidden and looks harmless, but changes the way commands are executed depending on the contents of the SHATTER region. When antivirus checks the original file will not cause suspicion, because the malicious part is stored in an encrypted blob and never runs for execution.
And this is where the fun begins.
BitErrant Attack
If an attacker can create two data blobs with the same SHA1 hashes, then under certain conditions it is possible to generate two executable files with different data inside. But both files will match the same torrent file.
If all the conditions are met, then we get two executable files in which one part can be replaced by another. If you replace it, the command execution path will change and the malicious code will work.
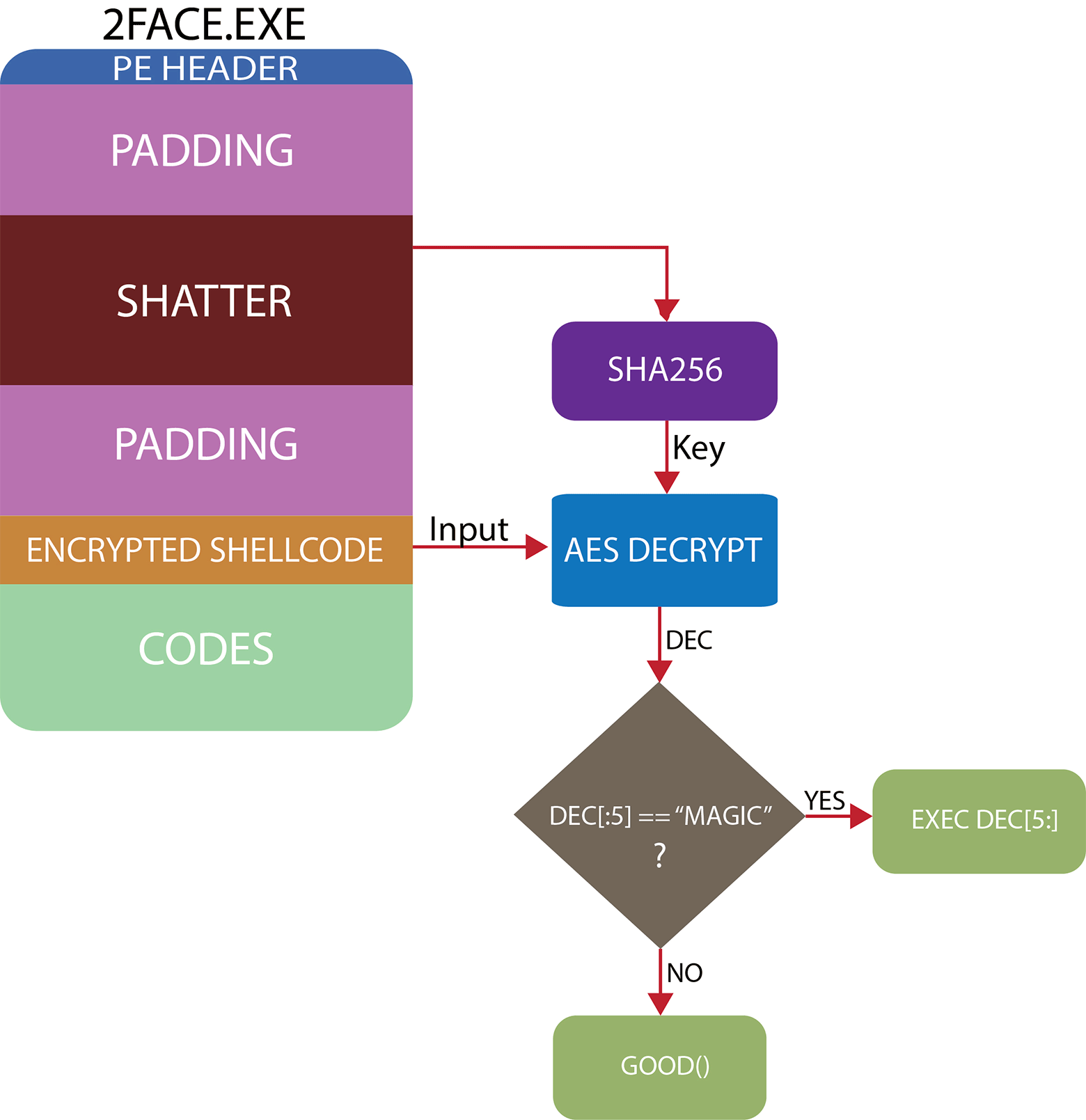
It is this “variable” functionality of the executable file that can be implemented in practice thanks to the BitTorrent protocol. The principle is simple: we start seeding through torrents with a “good” file, and then at a certain moment replace it with “bad”, effectively changing the data fragment from those who download this file on the peer network.
Demonstration and toolkit
biterrant_poc.zip
The archive contains two executable EXE files with different functionality (the malicious file contains the Meterpreter stuffing for the Metasploit framework, which in this case starts to listen on all interfaces).
Password to decrypt the archive: biterrant.io
SHA1: eed49a31e0a605464b41df46fbca189dcc620fc5
A good file on VirusTotal , a bad file in the same place.
The author of the attack BitErrant has developed the appropriate toolkit - a framework for generating executable files with the same .torrent. With this framework, you can put an arbitrary load in the encrypted part of the executable file and get the parameters for its call, which are then placed in the executable part of the file. Then choose the innocent functions of your choice for a good file replaceable part. Then the Python script generates two executable files — good and bad — that correspond to the same .torrent file.
So far, no one is using this attack to distribute files through official torrent trackers. And even "good" files with variable functionality look suspicious for some antiviruses. So the danger of this attack should not be taken too seriously.
To protect against this attack, it is enough to always check the total hash of the file being downloaded and compare it with the hash of the file that is in the distribution, that's all. By the way, there is even an option to include the common hash of the MD5 file directly into the torrent file, then this attack will become impossible. In most cases, no one uses this option.
Source: https://habr.com/ru/post/357944/
All Articles