Calm before IoT-storm or a year after Mirai

More than a year has passed since the mass attack on the IoT devices implemented by the creators of the Mirai botnet . It is worth noting that the gadgets from the world of the “Internet of things” were chosen for the attack not by chance. Very few manufacturers of such systems are really serious about protecting devices from external interference. In most cases, the developers try to make the gadget functional, pleasant looking, but forget about security. The massive attack on the IoT system was only a matter of time, and last year that time came.
For the spread of the malware Mrai it took no zero-day vulnerabilities and other complex things. As it turned out, the developers of most smart devices set the same password to access the administrator account. In total, the creators of Mirai have provided a selection of 61 different combinations to access the administrator account. Most of the systems affected by the worm were manufactured using components from XiongMai Technologies, so that cameras from different manufacturers were exposed to the same vulnerabilities.
Almost immediately after the botnet was launched, it was used to attack the resource of journalist Brian Krebs , who specializes in information security topics. The power of a DDoS attack on its resource was 665 Gbit / s. This is one of the most powerful attacks in history. A little later, attackers attacked French hosting provider OVH and Dyn, which provides network infrastructure and DNS services for major US companies. On that day, the power of DDoS attacks was about 1 Tbit / s.
')
Over time, the activity of Mirai faded away. Initially, vulnerabilities were found that other attackers took advantage of, putting the botnet into their service. But the operators were arrested, so that they could no longer manage the IoT-zombie network. Then cyber security officers started fighting Mirai, the reception was quite successful. The same Brian Krebs could even compute the creator and operators of Mirai. For almost a year now, almost nothing has been heard about this botnet, except for rare news about the appearance of new varieties of worm and botnet.
After the malicious code became available, it was used by both experienced and novice hackers, as well as information security specialists. Some users try to add new features and capabilities to the code. Employees of Arbor Networks, an information security company, found that some hackers "customize and improve the attack capabilities of the original botnet code," then using the modified software for their own purposes.
And what about Mirai?
Now, a year later, network security experts began to sound the alarm. A new problem has emerged on the Web - another powerful malware that has come to be known as Reaper and IoTroop. It also finds vulnerabilities in the software and hardware of cloud devices, and infects them, turning them into zombies.
So far, the goals of the creators of the worm and botnet of a new type are unclear. The botnet is already formed, but it has not attacked anyone yet. It may well be that developers are just waiting for something, some suitable moment.
One of the first companies to announce the appearance of a new botnet was Israeli CheckPoint. Why experts consider a new botnet more dangerous than Mirai? The fact is that he is able to hit a much larger number of devices than his predecessor. There are dozens of types of devices from a wide range of manufacturers in the Reaper vulnerability base, including companies such as AVTECH, D-Link, GoAhead, Netgear, and Linksys.
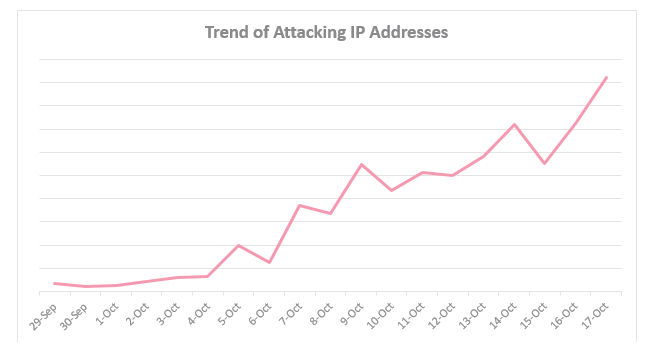
The chart, built by CheckPoint, shows the activity of a botnet, which affects more and more IoT devices.
Interestingly, Mirai and Reaper are not just similar to “interest” in IoT devices. These malware, if I may say so, are relatives. The fact is that the new Reaper worm is partially based on the old Mirai functionality. This was stated by representatives of another company - the Chinese Netlab 360. Experts from the same company believe that in the source code of Reaper there are substantial sections of the source code Mirai. Reaper has another difference - it is much more “soft”, not as aggressive as Mirai. Accordingly, it acts more slowly. This was done not because the developers could not achieve speed, but because they wanted their system to go unnoticed as long as possible. And they succeeded.
By the way, it may well be that the Reaper was not created to conduct DDoS attacks. He could have been designed for other needs. There are a lot of opportunities, from mining cryptocurrency (although there is not a lot on IoT systems) to creating a different type of distributed computer network. Mining bitcoins involved, for example, a variant of the ELF Linux / Mirai trojan with an added cryptocurrency unit. The number of coins that a single IoT device can mine is ridiculous, we are talking about millionths of a cryptocurrency unit. But if millions of devices are combined in a botnet, it will still make some money.
The uniqueness of the botnet is also noted by those who first discovered it - CheckPoint. “While many technical aspects have allowed us to suspect a possible connection with the Mirai botnet, the new botnet is a new type of campaign, it is rapidly expanding around the globe,” a CheckPoint spokesman said.
According to Netlab, about half of the exploits used by Reaper have been discovered and documented over the past few months. This may indicate that the worm uses far more vulnerabilities than Mirai, and some of these vulnerabilities are still unknown. True, now more and more network security specialists are working on this problem, so one can hope that all this will become known in the near future.

Equipment manufacturers that are vulnerable to Reaper urgently investigate the problem and patch holes. Netlab . One of the main problems is the peer-to-peer (P2P) function on many IoT devices. This feature, which turns into a vulnerability in the event of a Reaper worm attack, is documented by Depth Security. According to the report of this company, P2P allows the virus that hit one of the IoT devices on the network to infect other systems on the same network than other elements do not have to be connected to the Internet. This problem for some systems can be fixed with a patch .

Interestingly, Brian Krebs warned about P2P vulnerabilities back in 2016. Then he talked about the potential vulnerability of the P2P component of many cameras, which was called Foscam. Worst of all, even if you disable this component in the security settings, P2P is still not deactivated. Only a specially released patch allows you to do this, but it is clear that only a small fraction of users of IoT devices, firstly, is aware of the problem, and secondly, they will install a patch to solve the problem.
As for the latter, there is one more nuance. The fact is that even if the user is ready to install a patch or an updated firmware, he may be faced with the fact that all this is not so easy to find. Manufacturers sometimes hide updates deep in the depths of their sites, and the reason for this is poorly understood. Most likely, the matter is in ordinary negligence.
Two companies at once, Netlab and Checkpoint, write that the Reapera code is still being finalized. Judging by what can be found in the code today, the Reaper can exist peacefully with Mirai. However, it is not yet clear whether both botnets will fight for the same devices. So far there have been no such conflicts, and, if developers are to be believed, they are unlikely to appear in the near foreseeable future.
Reaper can search for infected Mirai devices and also infect them (this is about the same as Mirai did with its own predecessor, Qbot).
Anyway, after the discovery of a new botnet, many companies working in the field of information security began to study the worm and the botnet itself. Well, since many companies have gained experience in fighting Mirai, it is possible that the fight against the Reaper will be more effective.
Source: https://habr.com/ru/post/357850/
All Articles