External scripts with access to your credit cards and personal account

Tell me, how would you react to the sellers giving the opportunity to collect the attributes of your cards, including the number, surname and CVC, to some other person at the time of payment, and also, without a password, allowed to see what you are doing in your account some kind of service, to whom and how much you pay, for example. How many phones do you have and how do you use them. Those. you enter under the password, confirm the right of ownership by SMS, logged in, and there people crowd, who came just to see. Rave? However, many services do this. Who would you feel if you found a surveillance camera in a room for opening bank cells? But, we will not be again about banks, let's about everything consistently.
I apologize in advance to those to whom the explanations seem too chewy, despite the audience, last time many people did not understand what was at stake.
Most webmasters ignore the fact that pages with sensitive information should be static in the content of the code. What is different from the usual virus program? By the fact that a program appears on the computer, written by someone who does not understand, consumes resources and performs incomprehensible actions for the purposes of their authors (allow a free definition for the sake of explanation). And here we take the page, for example, Beeline personal account.
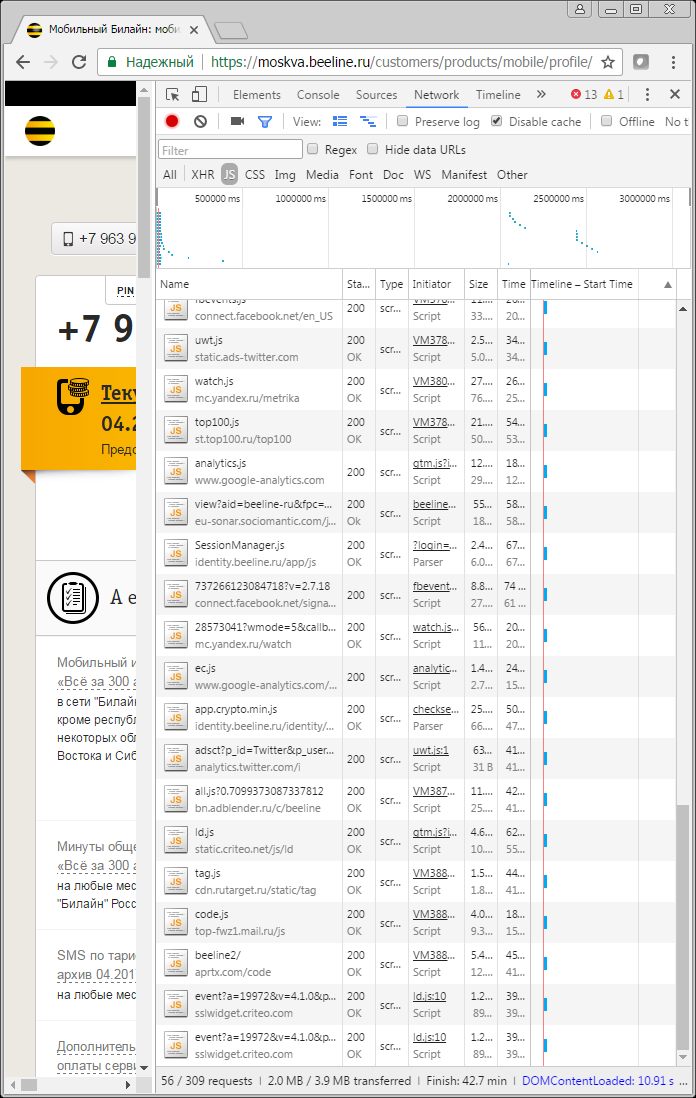
In addition to the regular address of Beeline, we see that the page contains addresses that do not apply to it. Those. there is a code that Beeline employees wrote and there is a code that is loaded from some other servers, written by other people, moreover, this code is not controlled at all by Beeline employees, because it is loaded not by Beeline, but by the addresses you see. If he is not controlled, then what actions he performs is also not clear.
')
Here you are, a small video on the fact that you can create external scripts in your account
If someone is interested to read the details here they are, it is for Beeline
Go to the next what promised in the title.
Passing by the MTS payment site, I accidentally discovered protests of a banner cutter. Fortunately, there are not very many scripts. But the popular Google analytics is there. Right here on the page where you enter the card number and CVV.
Small explanatory video:
I will describe what is happening on the video, if someone can not see it. Having deceived the DNS, I redirected the analytics scripts to my web server, where I successfully replaced them with my own. This is not a hack and the goal is to expose the vulnerability detected, although some likelihood of this also exists. With my scripts, I safely collected random random credit card numbers entered by myself and sent them to the server. To demonstrate the capabilities of the script, I also changed the amount of payment.
Sorry, I repeat, there is some company (listed above, like many others, is not the name). They write a site, in which they lay secrets and some kind of functional, where (I believe in it) no one should edit personal data and they don’t flow anywhere. In order to collect statistics on their users, they are lazy and use other people's scripts. Those. they give a command to users' browsers in their website - go to another server and take a script for statistics there. What is this script at this time only know the owners of another server. What it does, site owners cannot know. Moreover, in some cases, the user's browsers can be said to take scripts from somewhere else and then the number of those who can change them increases dramatically. Owners of servers of statistics and other inserts can collect everything they reach. I am sure that the owners of the main sites do not even know where they want to reach.
There is no reason to believe in the integrity of the company providing the analytics. However, people work in it. And people sometimes break the law. And even though the company will later take you outside the bath and shoot the violating officers, will it be easier for you personally? Can this compensate for the loss? I basically do not understand why give extra opportunity to access such data? If someone really hopes for SMS, I recommend reading this article and recalling the recent history with how dishonest employees of one of the salons duplicated sim cards of a cellular operator.
My letter to MTS:
Good afternoon, please specify why third-party scripts are used, including foreign ones, on the pages of the MTS website? This can also be a threat to the preservation of information transmitted between your company and the user.
And the following is such a reply
Hello, Oleg Andreevich.
The safety of information is protected by the legislation of the Russian Federation.
Respectfully,
**** ******
MTS PJSC
And laughter, and sin. I don’t want an employee to be made a scapegoat, which happened to me quite understandably, because the name has started to star. Then I shot and sent the video that you saw above, after which there was a message that it was sent to some security unit and I did not receive any further messages. Collected and chronology of MTS
Well, so that they do not suspect me of bias, Megafon has the same thing.
Two scripts, metrics and analytics. We change for our own and enjoy receiving data and changing all sorts of texts.
Just in case, I will explain how you can see if you put a pig in your personal account. For example, using the Chrome browser. Go to your personal account or what you have there contains personal data, press Shift-Ctrl-J, select the Network section, subsection JS and press F5. In the list that will be filled after this there should not be any "foreign" addresses, only belonging to the resource on which you are located. It is highly desirable, of course, that at this moment all browser extensions are turned off. Find something interesting - write in the comments, what resource and what connects to your personal account. Do not panic right away, yet there are some restrictions on the access of scripts to the content. But on webmaster sites that pay attention to security, external scripts are excluded in principle. I recommend this rule to be followed by anyone who does not want to substitute people using the service. The statistics can be collected by own means, and the most accurate one will be from web server logs, where there are no distortions from banner cutters. There are options for JS statistics, the scripts of which can be stored in oneself.
I thought it right to first report the problem to the companies themselves before publication, so at the moment it could have changed. But, in light of what is happening, there are still a lot of resources with external statistics on pages with your data.
Source: https://habr.com/ru/post/357700/
All Articles