Certificate Store in LibreOffice Office Suite
 LibreOffice is a powerful office suite. LibreOffice is free and open source.
LibreOffice is a powerful office suite. LibreOffice is free and open source.The office package contains a text and spreadsheet processor, a program for preparing and viewing presentations, a vector graphics editor, a database management system and a formula editor:
Moreover, the ongoing policy of import substitution, when domestic Linux forks are increasingly appearing on officials' tables instead of MS Windows, contributes to the widespread use of the LibreOffice package in government.
')
LibreOffice is developing intensively and since its inception has absorbed many additional features. One of these possibilities is the electronic signature (digital signature in the terminology of the LibreOffice) document. To generate an electronic signature ( File → Digital signatures → Digital signatures ... → Sign a document ) personal certificates are used:
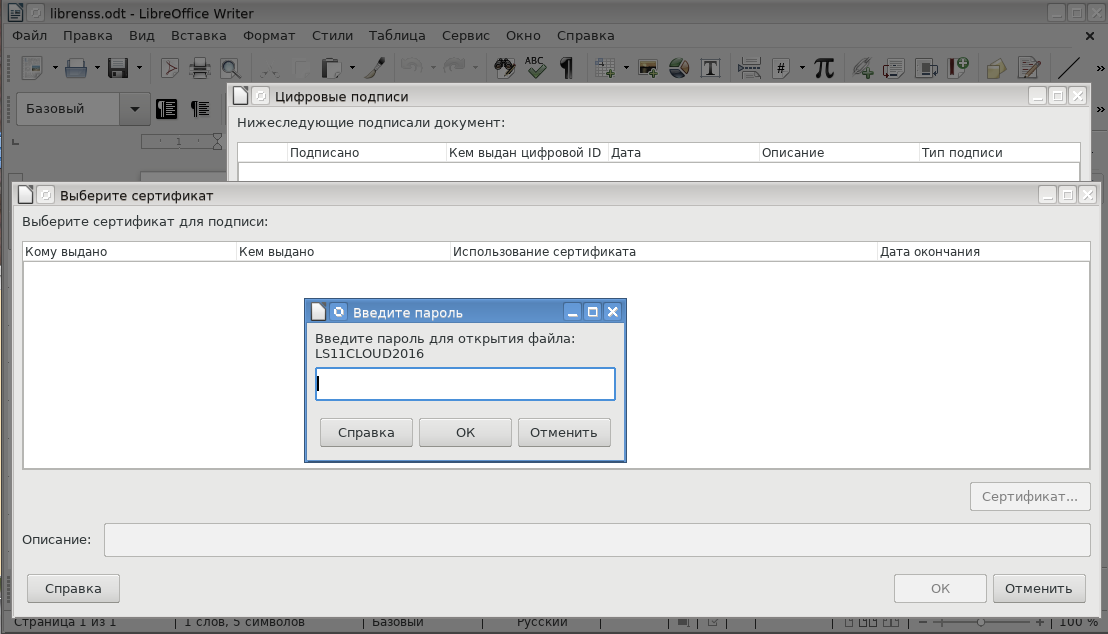
Looking at the picture, an inexperienced user (and even more so an official) has a deep sense of misunderstanding: what kind of file is about to open, what kind of password should be entered!
It should be noted that this is not a very good translation of the LibreOffice developers. This is not about the file, but about the PKCS # 11 token / smartcard, and not about the password, but about the user PIN for the token. There must be something like this:
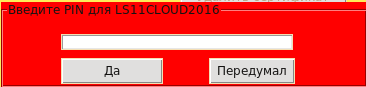
Here we come to the main question: where and how are the certificates that LibreOffice uses for generating electronic signature of documents stored?
As a certificate store, LibreOffice uses, as a rule, certificate stores created and maintained by Mozilla products (Firefox, Thunderbird, SeaMonkey). By default, this is the Thunderbird email client certificate store ( Tools → Options ... → Security → Certificate ... ):
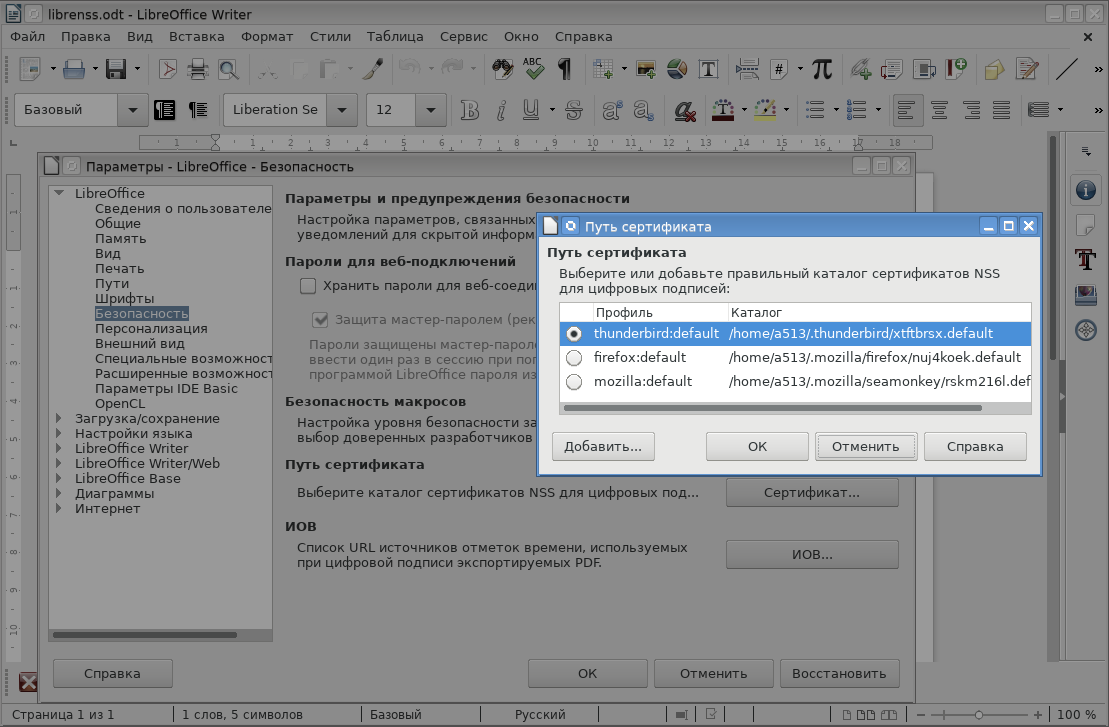
Certificate stores for Mozilla products are created using the Network Security Services ( NSS) package. Using command line utilities, you can create your own certificate store, for example:
bash-4.3$ cd /home/a513/tmp bash-4.3$ mkdir db_for_libre bash-4.3$ modutil -create -dbdir /home/a513/tmp/db_for_libre WARNING: Performing this operation while the browser is running could cause corruption of your security databases. If the browser is currently running, you should exit browser before continuing this operation. Type 'q <enter>' to abort, or <enter> to continue: bash-4.3$ ls -l db_for_libre 60 -rw------- 1 a513 a513 65536 31 16:49 cert8.db -rw------- 1 a513 a513 16384 31 16:49 key3.db -rw------- 1 a513 a513 16384 31 16:49 secmod.db bash-4.3$ The certificate store created in the / home / a513 / tmp / db_for_libre directory contains three databases, namely cert8.db, key3.db, and secmod.db. To create them, the old version of the Berkeley database (usually described in NSS documents as “DBM”) is used, unlike the certificate store, say, google-chrome , which is also created and maintained using the NSS package, but to support the databases ( cert9.db, key4.db, and pkcs11.txt) the storage uses the SQLite3 mechanism. To work with both storage, the same NSS utilities are used, just in the –d (storage directory) parameter before the storage path, if you are going to work with the new storage format (SQLite3), you just need to specify the prefix: -d sql: <path to storage>.
Moreover, it is also easy to create a repository in the new format (cert9.db, key4.db and pkcs11.txt) from the old-format certificate storage (cert8.db, key3.db and secmod.db). To do this, simply run the certutil certificate utility in the key (-K) or certificate (-L) mode with the –X parameter:
bash-4.3$ ls -l /home/a513/tmp/db_for_libre/ 60 -rw------- 1 a513 a513 65536 31 17:56 cert8.db -rw------- 1 a513 a513 16384 31 17:56 key3.db -rw------- 1 a513 a513 16384 31 16:49 secmod.db bash-4.3$ certutil -L -d sql:/home/a513/tmp/db_for_libre -X Certificate Nickname Trust Attributes SSL,S/MIME, JAR/XPI bash-4.3$ ls -l /home/a513/tmp/db_for_libre/ 120 -rw------- 1 a513 a513 65536 31 17:56 cert8.db -rw------- 1 a513 a513 28672 31 17:56 cert9.db -rw------- 1 a513 a513 16384 31 17:56 key3.db -rw------- 1 a513 a513 28672 31 17:56 key4.db -rw------- 1 a513 a513 440 31 17:56 pkcs11.txt -rw------- 1 a513 a513 16384 31 16:49 secmod.db bash-4.3$ As you can see, now in the repository there are databases in both the old and the new formats.
Unfortunately, the reverse transformation is unknown to me and therefore new certificate stores, for example, google-chrome (~ / .pki) in LibreOffice are not available.
The NSS package supports work with PKCS # 11 tokens / smartcards, on which, as a rule, users keep their personal certificates with private keys. Note that personal certificates are received today in certification centers .
So, we stopped at the fact that we had requested a PIN to the token. PKCS # 11 tokens / smartcards can be connected via Firefox, Thunderbir, Seamonkey , or modutil. For example, to connect a cloud token, just run the command:
$modutil –add LS11CLOUD2016 –libfile libls11cloud.so –dbdir /home/a513/tmp/db_for_libre $ It is to this token that LibreOffice requested a password:
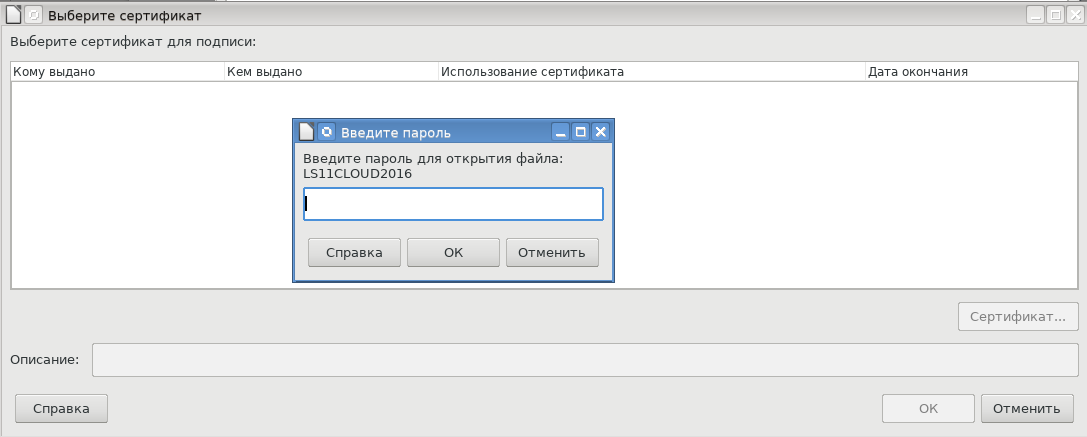
After entering the password, a list of personal certificates will be available that can be used to generate a signature. Here you can also view the contents of certificates:
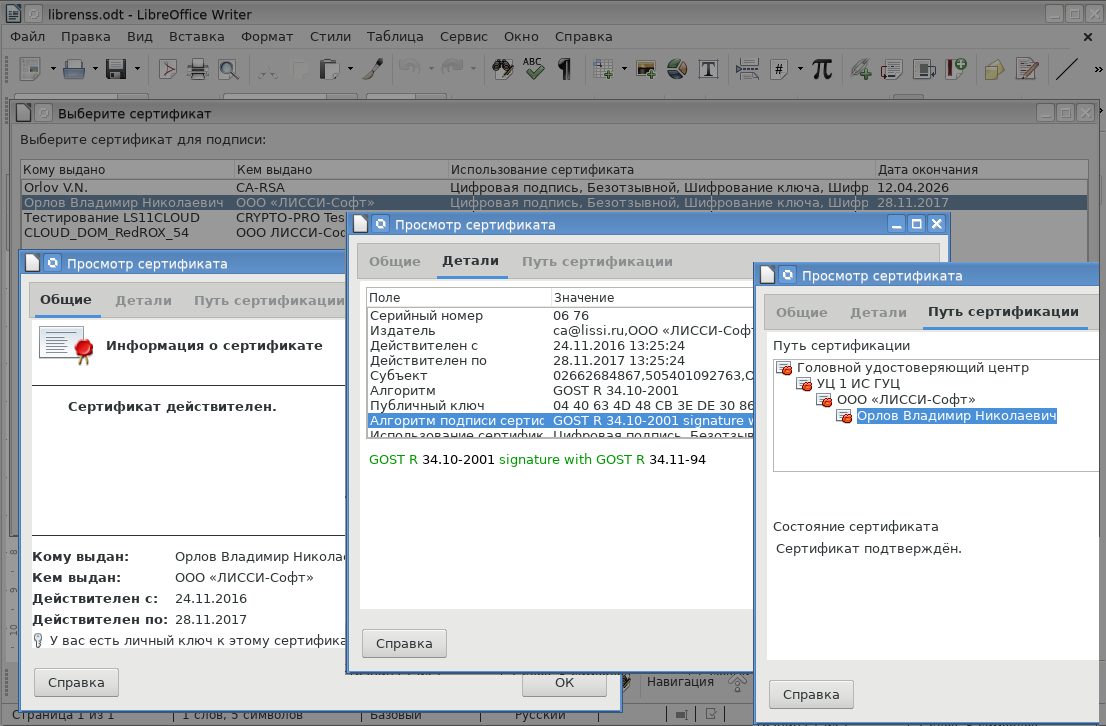
As soon as the certificate is selected, the electronic signature will be generated:
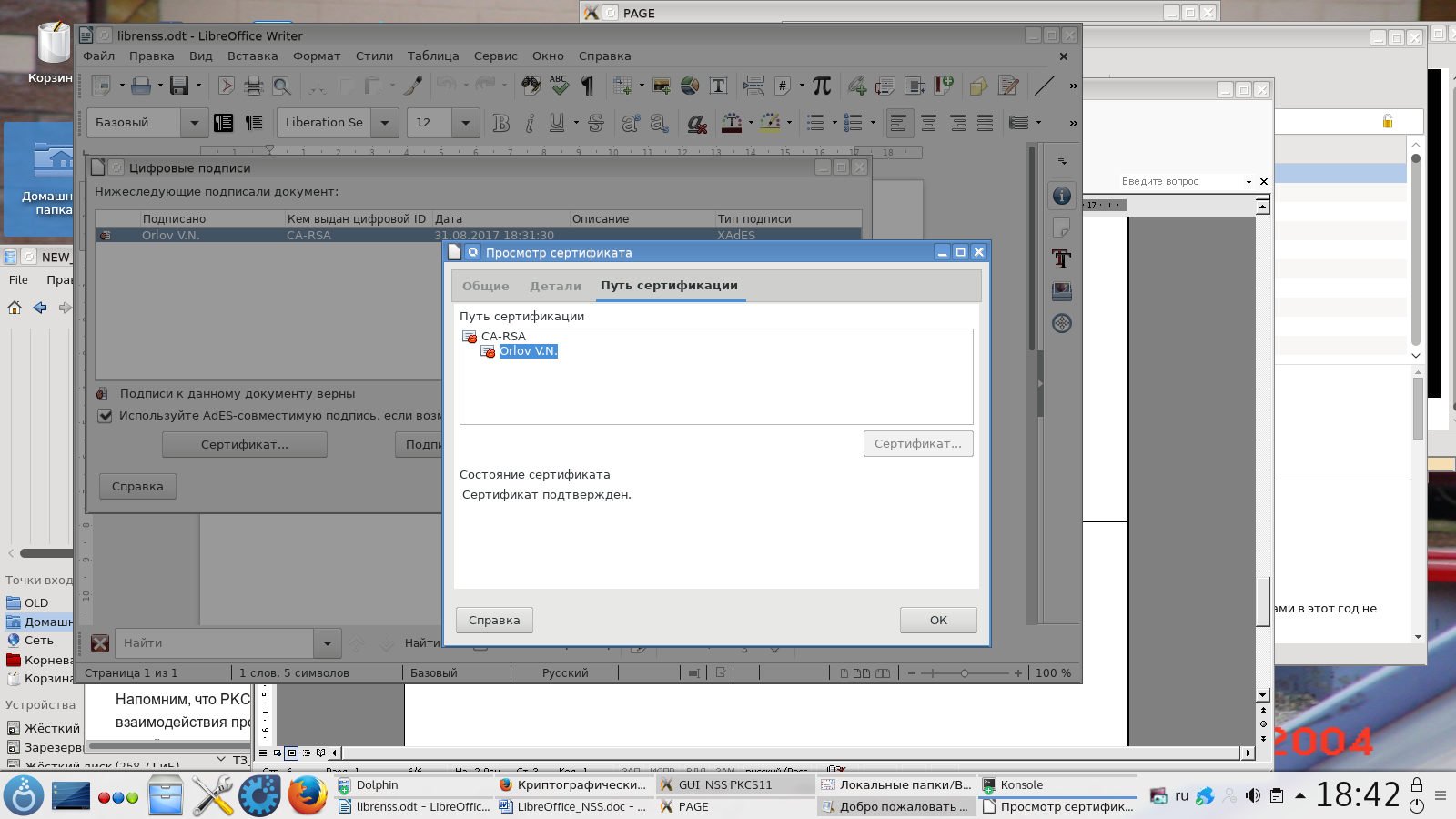
Now, when the document is reopened to work with it, then by the presence of a correct signature, you can be sure that the document has not been corrected by anyone. Otherwise, there is no trust in the document.
In conclusion, a few words about working with the certificate store. If the user decides to create his own repository other than Mozilla products and use the NSS command line utilities for this, it is convenient to use GUINSS GUI , which can be downloaded here.
This utility allows you to connect tokens / smart cards, import root certificates and certificates from a secure container PKCS # 12. It also allows you to create requests (CSR) for certificates in the PKCS # 10 format:

A generated certificate request can be sent to the CA to receive a certificate:
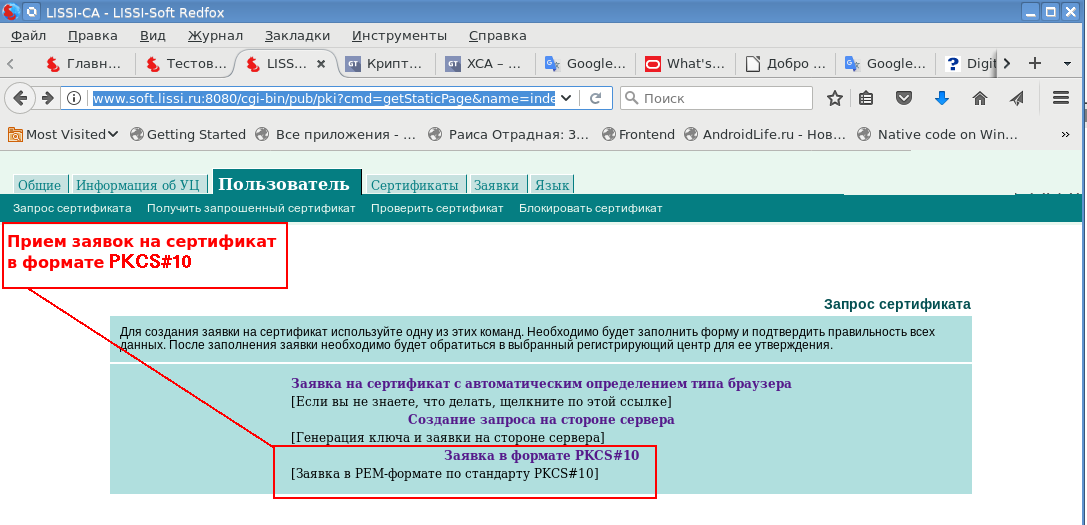
The created repository can be used outside of LibreOffice.
PS In the office package, certificates from the store are now used to generate an electronic signature in accordance with GOST R 34.10-2001 / 2012 in PDF documents .
Source: https://habr.com/ru/post/357692/
All Articles