Bots scan GitHub for Amazon AWS keys
Inattention can cost several thousand dollars
 Christmas (which is celebrated on December 25 in the United States and a number of other countries) is a holiday, that is, an excellent opportunity to learn new technology, which is not enough time on working days.
Christmas (which is celebrated on December 25 in the United States and a number of other countries) is a holiday, that is, an excellent opportunity to learn new technology, which is not enough time on working days.This is exactly what Andrew Hoffman thought , who decided to familiarize himself with the basics of Ruby on Rails. But the result of a small mistake while working on a test project almost cost him $ 2,375.
In general, nothing particularly new happened: Amazon Web Services back in March last year warned users about the need to be more careful about the privacy of secret cloud service keys when uploading the source codes of their projects to GitHub.
When registering for AWS, users receive private keys so that their applications can manage account settings. Amazon repeatedly reminds in the site interface that these keys need to be stored in a secure environment, since anyone who owns this information can access the resources and files of the private cloud. The attacker is able to delete files and clear entire accounts.
')
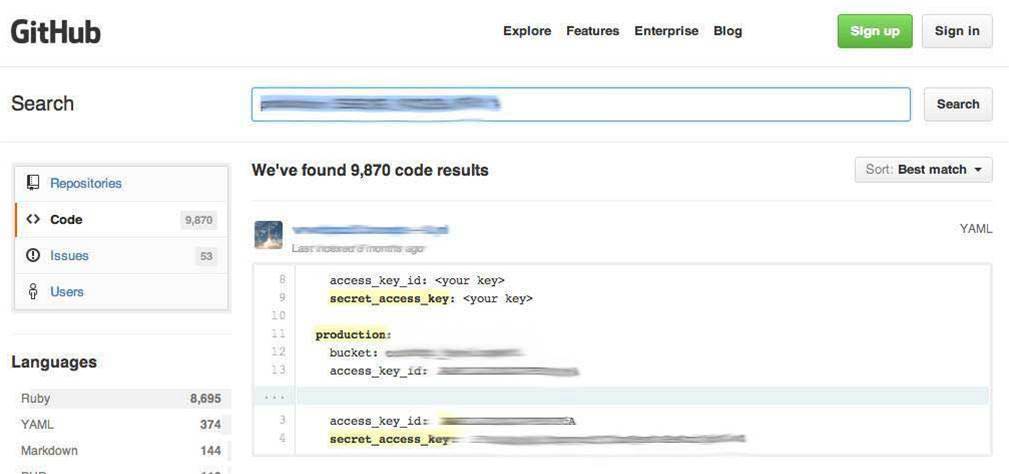
A few months ago, thugs left thousands of these keys on the Github. Developers in the best traditions of the world of open source software published the code of their projects, so that anyone could read them, but forgot to remove the private keys of Amazon Web Services from them. Many of the keys, however, could have been non-working even then - Amazon takes into account the distraction of customers and monitors the use of accounts.
Andy Hoffman took a short Ruby on Rails course on Lynda , and then decided to try out his skills in action. He designed a simple clone of the service reviews of restaurants and other small service enterprises Yelp.
The site was written under Heroku based on Rails and PostgreSQL DBMS. In the process, Hoffman was faced with the need to store custom images. The choice fell on the AWS free annual test offer, there were only some restrictions on unloading. Connecting file hosting S3 did not cause much difficulty.
The developer relied on the Figaro gems to protect private keys when unloading code. But they still got to GitHub. When checking, Hoffman quickly noticed something was wrong and immediately removed any traces of important data. Just before the removal took about 5 minutes.
The next morning, Hoffman found 4 emails, 1 missed call from AWS, and a bill of 2375 dollars. It turned out that with the help of a stolen key, EC2 instances can be launched - no necessary restrictions on access rights were set. In total, 140 servers were created from the Hoffman account.
Judging by what happened to the Hoffman key, the attackers have already automated the process of collecting and using these keys. Bots scan GitHub around the clock for API keys. After being found, EC2 servers are started and the cryptocurrency mining begins.
The good news is that Amazon often repays damages in its generous manner.
This is a long-standing practice: in December 2013, Luke Chadwick received an invoice for 3.5 thousand dollars - an unknown minil lightcoins from his AWS account. Upon request, technical support canceled these costs. So it was with Hoffman's score.
It should be noted that any troubles could have been avoided by re-generating private keys at the first suspicion of data leakage. Or you could use keys with limited privileges.
Source: https://habr.com/ru/post/357602/
All Articles