Turn off the Meltdown and Specter fix in Windows
The Microsoft website contains information on how you can check whether the OS is subject to meltdown attacks. There is also information on how to disable the latest fix.
Considering that rumors about a catastrophic performance drop do not subside on the Internet and even comparative tests “before” and “after” appear, information on disabling this patch may be useful.
Immediately to the point: you can disable by entering or adjusting two parameters in the registry.
From the Microsoft website:
')
It is assumed that the ExecutionPolicy in powershell is configured to the desired level (Bypass or Unrestricted).
Install PowerShell module:
For both questions answer "Y".
Further:
Running a scan:
The result in the case of full "security" PC:
After applying the settings change and reboot:
But the questions need to do it or not, whether it makes sense or not, and remain open.
Source Protect against speculative execution side-channel vulnerabilities in Windows client
Official update to disable CVE 2017-5715 patch for all supported windows
www.catalog.update.microsoft.com/Search.aspx?q=KB4078130
PPS: If anyone has the opportunity to test whether there are any changes in terms of performance, it would be very nice.

Considering that rumors about a catastrophic performance drop do not subside on the Internet and even comparative tests “before” and “after” appear, information on disabling this patch may be useful.
Immediately to the point: you can disable by entering or adjusting two parameters in the registry.
From the Microsoft website:
')
Enabling or disabling fix separately for CVE-2017-5715 and CVE-2017-5754 (Specter and Meltdown)
How to enable the fix CVE-2017-5715 and CVE-2017-5754reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
How to disable the fix CVE-2017-5715 and CVE-2017-5754reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 3 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
Enabling or disabling fix separately for CVE 2017-5715 (Specter)
How to enable fix CVE-2017-5715reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 1 /f
How to disable fix CVE-2017-5715reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 1 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 1 /f
Note * Setting the value 3 for FeatureSettingsOverrideMask is the same for both cases.
Note. * Disabling and enabling by changing registry settings will require restarting the computer and administrator rights.
Note. * There is no need to modify MinVmVersionForCpuBasedMitigations.
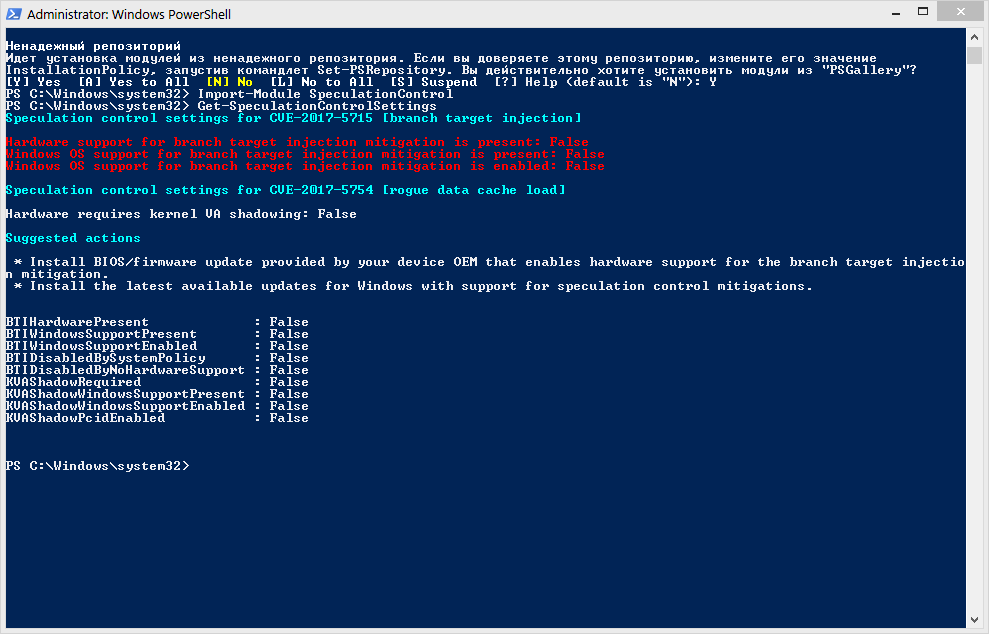
Check for vulnerabilities in the system using powershell module SpeculationControl
It is assumed that the ExecutionPolicy in powershell is configured to the desired level (Bypass or Unrestricted).
Install PowerShell module:
Install-Module SpeculationControl For both questions answer "Y".
Further:
Import-Module SpeculationControl Running a scan:
Get-SpeculationControlSettings The result in the case of full "security" PC:
BTIHardwarePresent : True BTIWindowsSupportPresent : True BTIWindowsSupportEnabled : True BTIDisabledBySystemPolicy : True BTIDisabledByNoHardwareSupport : True KVAShadowRequired : True KVAShadowWindowsSupportPresent : True KVAShadowWindowsSupportEnabled : True KVAShadowPcidEnabled : True After applying the settings change and reboot:
BTIHardwarePresent : False BTIWindowsSupportPresent : False BTIWindowsSupportEnabled : False BTIDisabledBySystemPolicy : False BTIDisabledByNoHardwareSupport : False KVAShadowRequired : False KVAShadowWindowsSupportPresent : False KVAShadowWindowsSupportEnabled : False KVAShadowPcidEnabled : False But the questions need to do it or not, whether it makes sense or not, and remain open.
Source Protect against speculative execution side-channel vulnerabilities in Windows client
Official update to disable CVE 2017-5715 patch for all supported windows
www.catalog.update.microsoft.com/Search.aspx?q=KB4078130
PPS: If anyone has the opportunity to test whether there are any changes in terms of performance, it would be very nice.
Source: https://habr.com/ru/post/357452/
All Articles