Miners and antivirus
I personally encountered the theme of miners after the statement of German Klimenko that a huge number of Moscow servers are struck by the miners. Before that, the miners were for me personally only one of the types of malware. There is not so much time since then, but the number of people who want to make money on other people's computers is growing and I think it's time to talk about this phenomenon.
Who cares how many miners are created per day, how they are distributed and (most importantly) how antiviruses treat them - please under the cat!
Let's start with the last stated topic - about the attitude of antiviruses and miners. To answer this question, you need to understand that there is a malicious program from an anti-virus point of view.
A malicious program is a program that is installed on a computer without the user's knowledge or performs unauthorized actions on the user's computer. The definition is not perfect, but very close to the truth.
')
Two quotes from the article :
Definitely harmful behavior that makes miners legal booty of antivirus (and other protection systems, because they are not the only antivirus).
But can antivirus catch a miner?
Not certainly in that way. In the above quote, we are talking about a behavioral analyzer (or its variants - cloud antivirus). These anti-virus components really track behavior. And if the malicious program were engaged in pure mining, then it would be impossible to really decide that this is a malicious program or not. Therefore, I propose to see what are the miners.
Roughly speaking, two varieties. The first implements the mining self-written component. And here everything is clear - the anti-virus database signatures will not even allow miners to start, no matter how it penetrates the machine. The above article claims that “attackers on the network are infecting, exploiting a vulnerability such as EternalBlue”. Similarly, spread Wanna Cry. But at the same time, it could not always start. So one of the antiviruses caught it with a heuristic, the other with the included cloud - with its components.
An example of such a miner:
The second option is to use the usual miner.
Example
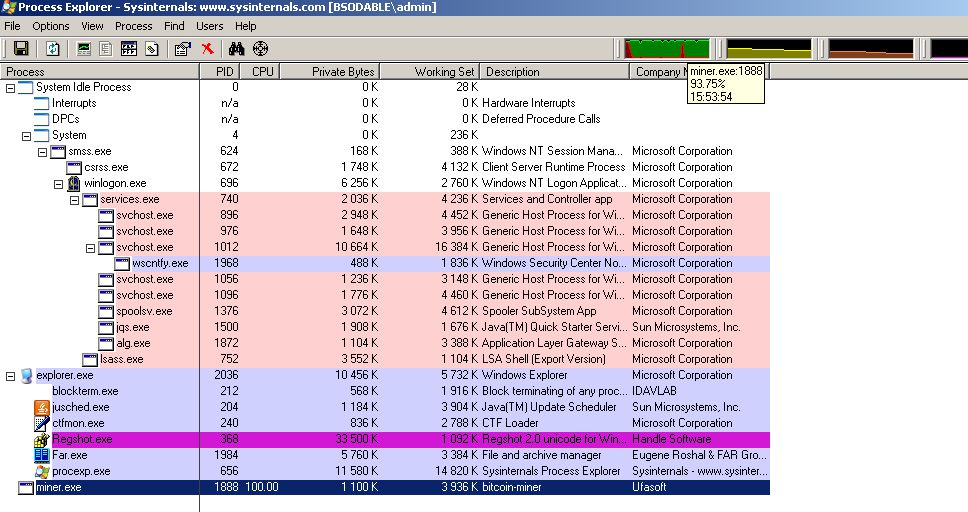
In this case, to start a legitimate miner, you must first deliver it to the machine, start it and preferably hide the presence of the process in the system / icon in the tray. So there are malicious components that can again be detected either by signature or by behavior.
In general - there will be a signature - the miner will not pass. There will be no signature, the miner will find out by the increased load of the machines and the signature will appear.
How many miners are created? We take a random date on updates.drweb.com
On the selected date, Android turned out to be ignored by the virus makers; let's take an example from the news


An example of a miner for Linux can be found here .
How are miners spread?
In all ways the spread of malware. A couple of examples
Through the hacked site
Network scan:
How widespread are miners?
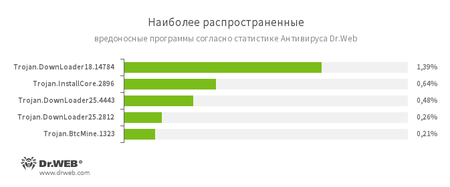
In total miners will be about 0.3 of all caught in a month. Not every month, but periodically miners get into the top of the most common malware.
Total:
I hope it was interesting, if you have questions - I will try to answer.
Update. Are there miners who are not greedy and do not take all the resources on themselves. And if so, is it possible to detect them? Yes, there are such miners, nevertheless, their appearance is accompanied by the appearance of brakes, though small, but brakes. Lags when starting programs at an unexpected moment. Therefore, if the computer started to glitch more than normal:
And I recommend to follow that you are trying to access the Internet
Update2. Are there miners whose processes are not visible? Little, but there is. ... Miner selects an existing system service in netsvcs, replaces the service file, restores the time attributes and starts the service ... But there is no perfection in the world - detected by the processor load
Here, apart from a behavioral analyzer, changes in protection measures can hardly be invented. Plus, of course, control of everything that starts new
Who cares how many miners are created per day, how they are distributed and (most importantly) how antiviruses treat them - please under the cat!
Let's start with the last stated topic - about the attitude of antiviruses and miners. To answer this question, you need to understand that there is a malicious program from an anti-virus point of view.
A malicious program is a program that is installed on a computer without the user's knowledge or performs unauthorized actions on the user's computer. The definition is not perfect, but very close to the truth.
')
Two quotes from the article :
The problem for the victim is that her computer infected with a crypto miner runs much slower than usual ...
... advanced malware stops working during the launch of "heavy" applications like games on the PC ...
Definitely harmful behavior that makes miners legal booty of antivirus (and other protection systems, because they are not the only antivirus).
But can antivirus catch a miner?
There are a lot of miners, and the difficulty of detecting them is that mining itself is a standard process. These are not attempts to erase or modify files, change the contents of the boot sector of a hard disk, etc. No, mining in the usual case will not be determined by antivirus. Therefore, antivirus developers have to look for new ways to determine the presence of such programs on victims' computers.
Not certainly in that way. In the above quote, we are talking about a behavioral analyzer (or its variants - cloud antivirus). These anti-virus components really track behavior. And if the malicious program were engaged in pure mining, then it would be impossible to really decide that this is a malicious program or not. Therefore, I propose to see what are the miners.
Roughly speaking, two varieties. The first implements the mining self-written component. And here everything is clear - the anti-virus database signatures will not even allow miners to start, no matter how it penetrates the machine. The above article claims that “attackers on the network are infecting, exploiting a vulnerability such as EternalBlue”. Similarly, spread Wanna Cry. But at the same time, it could not always start. So one of the antiviruses caught it with a heuristic, the other with the included cloud - with its components.
An example of such a miner:
Miner Trojan.BtcMine.1259 is downloaded to the computer by Trojan-loader Trojan.DownLoader24.64313, which, in turn, is distributed using the DoublePulsar backdoor. Immediately after launching, Trojan.BtcMine.1259 checks whether its copy is running on the infected computer. Then it determines the number of processor cores, and if it is greater than or equal to the number of threads specified in the Trojan’s configuration, it decrypts and loads the library stored in its body into memory. This library is a modified version of the open source remote administration system known as Gh0st RAT (it is detected by Dr.Web Anti-virus under the name BackDoor.Farfli.96). Then Trojan.BtcMine.1259 saves its copy to the disk and starts it as a system service. After a successful launch, the Trojan attempts to download its update from the management server whose address is specified in the configuration file.
The second option is to use the usual miner.
Example
Trojan.BtcMine.1, uses two legitimate mining programs, by which it uses the computing resources of the victim's computer in order to “extract” virtual coins. Being an unsuspecting user running on the system, Trojan.BtcMine.1 saves itself to a temporary folder under the name udpconmain.exe. Then he writes the path to the executable file in the registry key responsible for the application startup. Then the malware downloads from the Internet and places the second “miner” in the temporary folder under the name miner.exe in order to maximally load the computer with calculations. After that, the Trojans connect to one of the pools of the payment system and start making calculations, earning the corresponding reward for the intruders. In the illustration you can see the load on the processor that is created by the miner program launched by the Trojan.BtcMine.1 Trojan.

In this case, to start a legitimate miner, you must first deliver it to the machine, start it and preferably hide the presence of the process in the system / icon in the tray. So there are malicious components that can again be detected either by signature or by behavior.
In general - there will be a signature - the miner will not pass. There will be no signature, the miner will find out by the increased load of the machines and the signature will appear.
How many miners are created? We take a random date on updates.drweb.com
Trojan.BtcMine.1065 (2) Trojan.BtcMine.1084 Trojan.BtcMine.1177 Trojan.BtcMine.1247 Trojan.BtcMine.1336 Trojan.BtcMine.1421 (3) Trojan.BtcMine.1440 Trojan.BtcMine.1447 (2) Trojan .BtcMine.1448 (10) Trojan.BtcMine.1449 Trojan.BtcMine.1500 Trojan.BtcMine.1501 Trojan.BtcMine.1502 (2) Trojan.BtcMine.1503 Trojan.BtcMine.1506 Trojan.BtcMine.1507 Trojan.BtcMine.1508
Tool.BtcMine.1000 Tool.BtcMine.1001 Tool.BtcMine.1002 Tool.BtcMine.1003 (2) Tool.BtcMine.1004 Tool.BtcMine.1005 Tool.BtcMine.1006 Tool.BtcMine.1007 Tool.BtcMine.1008 (2 ) Tool.BtcMine.1009 (2) Tool.BtcMine.1010 (2) Tool.BtcMine.1011 (4) Tool.BtcMine.1012 Tool.BtcMine.1013 Tool.BtcMine.1014 Tool.BtcMine.1015 Tool.BtcMine.1016 (2) Tool.BtcMine.1021 (2) Tool.BtcMine.1022 Tool.BtcMine.1023 (2) Tool.BtcMine.1024 Tool.BtcMine.1025 Tool.BtcMine.1026 Tool.BtcMine.1027 (3) Tool.BtcMine .1028 (2) Tool.BtcMine.1029 (2) Tool.BtcMine.1030 (2) Tool.BtcMine.230 Tool.BtcMine.278 Tool.BtcMine.288 (7) Tool.BtcMine.390 (2) Tool.BtcMine .433 Tool.BtcMine.483 (2) Tool.BtcMine.573 (3) Tool.BtcMine.800 Tool.BtcMine.810 (11) Tool.BtcMine.916 (2) Tool.BtcMine.917 Tool.BtcMine.943 Tool .BtcMine.944 (7) Tool.BtcMine.948 (2) Tool.BtcMine.958 (3) Tool.BtcMine.968 Tool.BtcMine.970 (4) Tool.BtcMine.973 (4) Tool.BtcMine.974 Tool .BtcMine.975 Tool.BtcMine.976 Tool.BtcMine.977 (4) Tool.BtcMine.978 (6) Tool.BtcMine.979 Tool.BtcMine.980 Tool.BtcMine. 981 (3) Tool.BtcMine.982 Tool.BtcMine.983 Tool.BtcMine.984 Tool.BtcMine.985 Tool.BtcMine.986 Tool.BtcMine.987 (2) Tool.BtcMine.988 Tool.BtcMine.989 Tool.BtcMine .990 Tool.BtcMine.991 (4) Tool.BtcMine.992 Tool.BtcMine.993 Tool.BtcMine.994 Tool.BtcMine.995 Tool.BtcMine.996 (2) Tool.BtcMine.997 Tool.BtcMine.998 Tool. BtcMine.999 Tool.Linux.BtcMine.163 Tool.Linux.BtcMine.164 Tool.Linux.BtcMine.165 Tool.Linux.BtcMine.166 Tool.Linux.BtcMine.167 Tool.Linux.BtcMine.168 Tool.Linux.BtcMine .169 Tool.Linux.BtcMine.170 Tool.Linux.BtcMine.171 Tool.Linux.BtcMine.172 Tool.Linux.BtcMine.173 Tool.Linux.BtcMine.174 Tool.Linux.BtcMine.175 Tool.Linux.BtcMine. 176 Tool.Linux.BtcMine.178 Tool.Linux.BtcMine.179 Tool.Linux.BtcMine.180 Tool.Linux.BtcMine.181 Tool.Linux.BtcMine.182 Tool.Linux.BtcMine.183 Tool.Linux.BtcMine.184 Tool.Linux.BtcMine.186 Tool.Linux.BtcMine.187 Tool.Linux.BtcMine.188 Tool.Linux.BtcMine.189 Tool.Linux.BtcMine.190 Tool.Linux.BtcMine.191 Tool .Linux.BtcMine.194 Tool.Linux. BtcMine.195 Tool.Linux.BtcMine.196 Tool.Linux.BtcMine.197 Tool.Linux.BtcMine.198 Tool.Linux.BtcMine.199 Tool.Linux.BtcMine.201 Tool.Linux.BtcMine.202 Tool.Linux.BtcMine .203 Tool.Linux.BtcMine.204 Tool.Linux.BtcMine.205 Tool.Linux.BtcMine.206 Tool.Linux.BtcMine.207 Tool.Linux.BtcMine.208 Tool.Linux.BtcMine.209 Tool.Linux.BtcMine. 210 Tool.Linux.BtcMine.211 Tool.Linux.BtcMine.212 Tool.Linux.BtcMine.213 Tool.Linux.BtcMine.214 Tool.Linux.BtcMine.215 Tool.Linux.BtcMine.216 Tool.Linux.BtcMine.219 Tool.Linux.BtcMine.220 Tool.Linux.BtcMine.221 Tool.Linux.BtcMine.222 Tool.Linux.BtcMine.223 Tool.Linux.BtcMine.224 Tool.Linux.BtcMine.225 Tool.Linux.BtcMine.226 Tool .Linux.BtcMine.227 Tool.Linux.BtcMine.228 Tool.Linux.BtcMine.229 Tool.Mac.BtcMine.35 Tool.Mac.BtcMine.36 Tool.Mac.BtcMine.37 Tool.Mac.BtcMine.38 Tool. Mac.BtcMine.39 Tool.Mac.BtcMine.40 Tool.Mac.BtcMine.41 Tool.Mac.BtcMine.42 Tool.Mac.BtcMine.43 Tool.Mac.BtcMine.44 Tool.Mac.BtcMine.45 Tool.Mac .BtcMine.46 Tool.Mac.BtcMine.47 Tool.Mac.BtcMin e.48 Tool.Mac.BtcMine.50 Tool.Mac.BtcMine.51 Tool.Mac.BtcMine.52 Tool.Mac.BtcMine.53 Tool.Mac.BtcMine.54 Tool.Mac.BtcMine.55 Tool.Mac.BtcMine .56 Tool.Mac.BtcMine.57
On the selected date, Android turned out to be ignored by the virus makers; let's take an example from the news
Android-miners Android.CoinMine.1.origin and Android.CoinMine.2.origin, designed for the extraction of virtual currencies Litecoin, Dogecoin and Casinocoin were distributed by attackers in the popular applications they modified and activated in those periods of time when the mobile device was not used by its owner . Since these malicious programs actively used the hardware resources of infected smartphones and tablets, this could cause them to overheat, accelerate battery drain and even result in financial losses for users due to excessive consumption of Internet traffic by Trojans. And in April 2014, new versions of these Trojans appeared, which were discovered in the Google Play catalog and intended for the extraction of Bitcoin cryptocurrency. These malicious applications were hidden in harmless "live wallpaper" and also began their illegal activities if the infected mobile device was not used for a certain time.


An example of a miner for Linux can be found here .
How are miners spread?
In all ways the spread of malware. A couple of examples
Through the hacked site
The attackers placed on the VCIOM server web pages from which visitors were offered to download the malware under the guise of various “useful” files.
Both the Russian-language (wciom.ru) and the English-language (wciom.com) versions of the VTsIOM official web site have been cracked. Cybercriminals created a special section on the compromised server that hosted web pages with headlines that are highly popular according to search engine statistics: for example, “new-commands-chl-2015-2016”, “download-book-metro-2035-in- format-fb2 "," catalogs-avon-12-2015-view-online-free-russia-flipping "," traffic jams-on-the-route-m4-dong-today-online "," download-adblock ", etc. When you try to open such a link in a browser window, the user was shown a fake webpage of a popular file storage service. “Yandex.Disk” or a web page with the title WCIOM.RU, where a potential victim was offered to download the archive allegedly with some “useful” content, for example, the popular book “Metro 2035” or the latest Avon catalog.
Network scan:
Trojan.BtcMine.737 lists the computers available in the network environment and tries to connect to them, sorting through logins and passwords using the special list at its disposal. In addition, the malware is trying to find the password to the local Windows user account. If this succeeds, Trojan.BtcMine.737, if it has the appropriate equipment, launches an open WiFi access point on the infected computer. If the malware was able to access one of the computers on the local network, an attempt is made to save and run a copy of the Trojan on it either using the Windows Management Instrumentation (WMI) toolkit or using the Task Scheduler
How widespread are miners?

In total miners will be about 0.3 of all caught in a month. Not every month, but periodically miners get into the top of the most common malware.
Total:
- Miners are the legitimate goal of antiviruses and, if signatures and rules are present, they can be removed and deleted.
- Any malware is found and removed by the antivirus only if there are rules / signatures. Since miners like to create botnets, they fall into the hands of analysts guaranteed
- Antivirus is not a panacea or a golden bullet. Therefore, you should not neglect other methods of protection, the same restriction of rights
I hope it was interesting, if you have questions - I will try to answer.
Update. Are there miners who are not greedy and do not take all the resources on themselves. And if so, is it possible to detect them? Yes, there are such miners, nevertheless, their appearance is accompanied by the appearance of brakes, though small, but brakes. Lags when starting programs at an unexpected moment. Therefore, if the computer started to glitch more than normal:
- Update antivirus and check the system. It seems ridiculous, but a huge number of people have outdated bases
- If the databases are fresh, download a different antivirus and check them
- Check for unknown processes for system services. As a rule, the miner does not make it difficult to disguise itself and the services / processes are visible. Example
And I recommend to follow that you are trying to access the Internet
Update2. Are there miners whose processes are not visible? Little, but there is. ... Miner selects an existing system service in netsvcs, replaces the service file, restores the time attributes and starts the service ... But there is no perfection in the world - detected by the processor load
Here, apart from a behavioral analyzer, changes in protection measures can hardly be invented. Plus, of course, control of everything that starts new
Source: https://habr.com/ru/post/357424/
All Articles