Partial recovery after Petya (ExPetr)
06.27.2017, for those who do not back up to removable media, it became the blackest day when the Petya virus-viper destroyed someone for a half hour of their work, and someone 10-25 years of experience, archive valuable files, databases and other things. Making start life with a clean slate. However, there is a chance to save at least the Outlook archives and photos. Details under the cut.
The virus worked in two stages: it encrypted files (and not everything and not completely), then initiated a reboot and, after rebooting, encrypted the bootloader (MBR) of the hard disk. As a result, the hard disk turned into a conditional “pumpkin”, from which nothing could be pulled out.
If the PC has gone through only the first stage, then after the MBR has been restored, you can continue to work fully on the PC and observe the consequences of the file encryption program and look for those that survived. If the PC has gone through two stages, then everything is much worse and even just pulling out the files is much more difficult.
There is practically no information search in RuNet using methods of saving information from such a hard disk, so I had to experimentally select the optimal strategy for finding and recovering what could have survived. About a dozen information recovery programs were tried, but most of the information was pulled out using the R-Studio program, we’ll talk about it later, with a description of the sequence of actions for saving (all actions will be carried out under Windows 7, but I think no matter what version of windows you just have to run R-studio).
I will say right away that almost all files can be pulled out, but they will be encrypted, except for files that were not encrypted, usually photos and videos. It will be possible to recover some files if you have the utilities that the developers of the respective file format provided. In the example below, we will look at the process of saving an archive file from Outlook.
')
So the sequence of actions:
1. We connect an unformatted encrypted disk (this is a key requirement if the disk was formatted or the OS was reinstalled, then the chances of recovering at least something tend to zero), which went through 2 stages of encryption with the loss of the file system, to a Windows PC (connect You can either directly to the motherboard through the sata / ide ports or via USB adapters, for whom it is more convenient). And after loading the PC, we get a message about the need to format the newly connected drive (in my case, this is drive G).
Click cancel. We are convinced that our disk is really damaged, in the disk manager it will be determined with the RAW file system:
2. Run the R-Studio program (I used version 8.2) and watch the disks found. Our experimental 320 GB hard drive was connected via a USB 3.0 docking station and was identified as JMicron Tech 023 under the letter “G”.
Next, double-click on the line with the “G” disk, as in the figure above, and wait for the end of the disk scan.
3. The R-Studio window will open to us with the scan results (see figure below):
As a rule, there are very few folders with a clear name, all the most valuable is in the "Additional Found Files" section. Therefore, we proceed to the next step.
4. Use the mouse to select the line “Additionally found files” and click the “Find / Mark” button on the program's control panel.
5. In the window that opens, select the search by file extension and specify the pst extension (file format of Outlook archive folders) and click the "Yes" button.
6. Search will find archive files, there may be many of them in different folders. Therefore, we focus on the way in which you have stored archive files. The example below shows that the files you were looking for were in the Outlook Files folder.
Please note that if you look at the left menu and go up through the folder hierarchy, you can see that this folder is located in the user account folder and there are Desktop, Documents, etc. folders. Thus, you can pull out photos and other files that were stored in the user in these folders.
7. Next, we tick the required files with the pst extension and click the Restore Marked button, indicate the place to save the saved files (in my case this is the Recover folder on drive C). We are waiting for the end of the process of copying files.
8. The recovered archive file is usually damaged and is not detected by Outlook. Fortunately, for large files, the virus encrypted only the first megabyte, leaving the rest intact. Therefore, we need to try to restore the structure of the archive, for this there are several ways:
A) Use the SCANPST utility included in the standard MS Office suite. For example, in MS Office 2010 this utility is located in the folder C: \ Program Files (x86) \ Microsoft Office \ Office14 \ if you have 64-bit Windows and the path C: \ Program Files \ Microsoft Office \ Office14 when using the 32-bit version of Windows .
B) Use third-party utilities. Which you can find a lot in the open spaces of Google.
I used the first option and, in principle, it worked on all the PCs that were brought to me for recovery.
I also attach to the post a link to step-by-step instructions for working with the SCANPST utility.
That's all, other files are restored by the same algorithm, you only need to substitute the desired file extension, or manually scroll through all the folders in the "Additional found files" section and select what needs to be restored.
If someone post my "captain", please do not criticize strongly, not everyone has data recovery experience and proven tools. If you still have questions you can write in the LAN or here in the comments.
The virus worked in two stages: it encrypted files (and not everything and not completely), then initiated a reboot and, after rebooting, encrypted the bootloader (MBR) of the hard disk. As a result, the hard disk turned into a conditional “pumpkin”, from which nothing could be pulled out.
If the PC has gone through only the first stage, then after the MBR has been restored, you can continue to work fully on the PC and observe the consequences of the file encryption program and look for those that survived. If the PC has gone through two stages, then everything is much worse and even just pulling out the files is much more difficult.
There is practically no information search in RuNet using methods of saving information from such a hard disk, so I had to experimentally select the optimal strategy for finding and recovering what could have survived. About a dozen information recovery programs were tried, but most of the information was pulled out using the R-Studio program, we’ll talk about it later, with a description of the sequence of actions for saving (all actions will be carried out under Windows 7, but I think no matter what version of windows you just have to run R-studio).
I will say right away that almost all files can be pulled out, but they will be encrypted, except for files that were not encrypted, usually photos and videos. It will be possible to recover some files if you have the utilities that the developers of the respective file format provided. In the example below, we will look at the process of saving an archive file from Outlook.
')
So the sequence of actions:
1. We connect an unformatted encrypted disk (this is a key requirement if the disk was formatted or the OS was reinstalled, then the chances of recovering at least something tend to zero), which went through 2 stages of encryption with the loss of the file system, to a Windows PC (connect You can either directly to the motherboard through the sata / ide ports or via USB adapters, for whom it is more convenient). And after loading the PC, we get a message about the need to format the newly connected drive (in my case, this is drive G).
Screenshot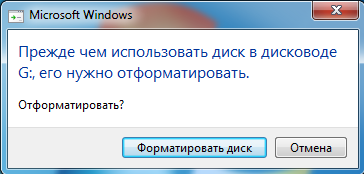

Click cancel. We are convinced that our disk is really damaged, in the disk manager it will be determined with the RAW file system:
Screenshot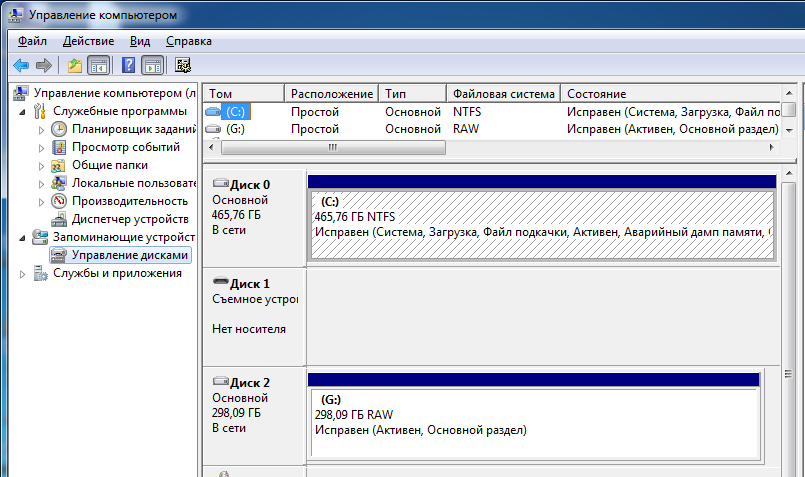

2. Run the R-Studio program (I used version 8.2) and watch the disks found. Our experimental 320 GB hard drive was connected via a USB 3.0 docking station and was identified as JMicron Tech 023 under the letter “G”.
Screenshot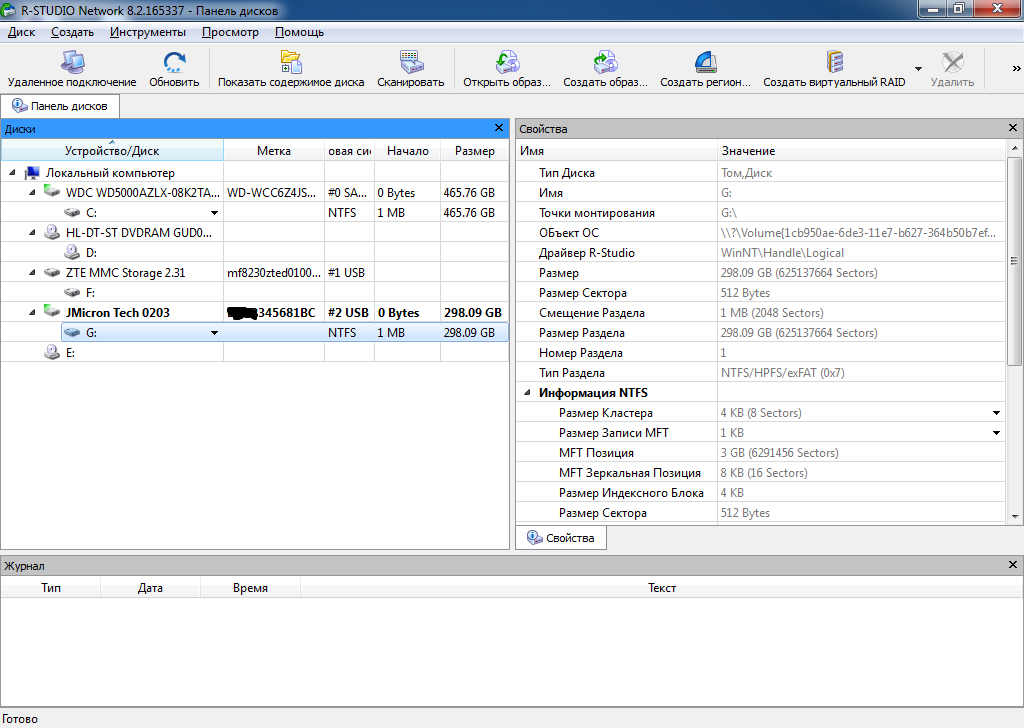

Next, double-click on the line with the “G” disk, as in the figure above, and wait for the end of the disk scan.
3. The R-Studio window will open to us with the scan results (see figure below):
Screenshot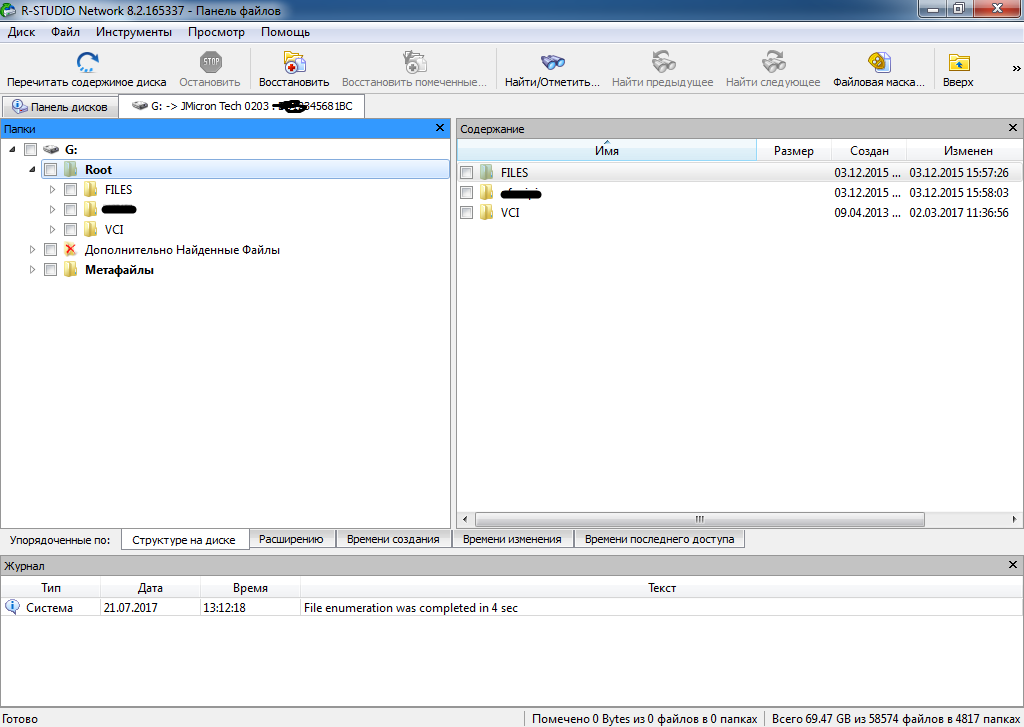

As a rule, there are very few folders with a clear name, all the most valuable is in the "Additional Found Files" section. Therefore, we proceed to the next step.
4. Use the mouse to select the line “Additionally found files” and click the “Find / Mark” button on the program's control panel.
5. In the window that opens, select the search by file extension and specify the pst extension (file format of Outlook archive folders) and click the "Yes" button.
Screenshot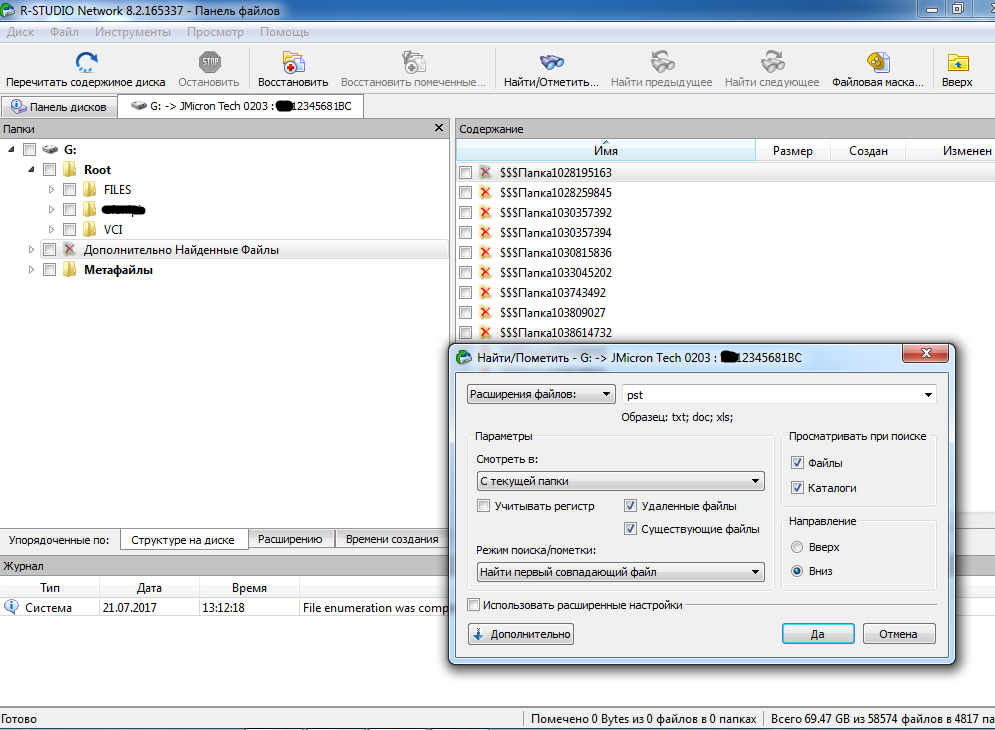

6. Search will find archive files, there may be many of them in different folders. Therefore, we focus on the way in which you have stored archive files. The example below shows that the files you were looking for were in the Outlook Files folder.
Screenshot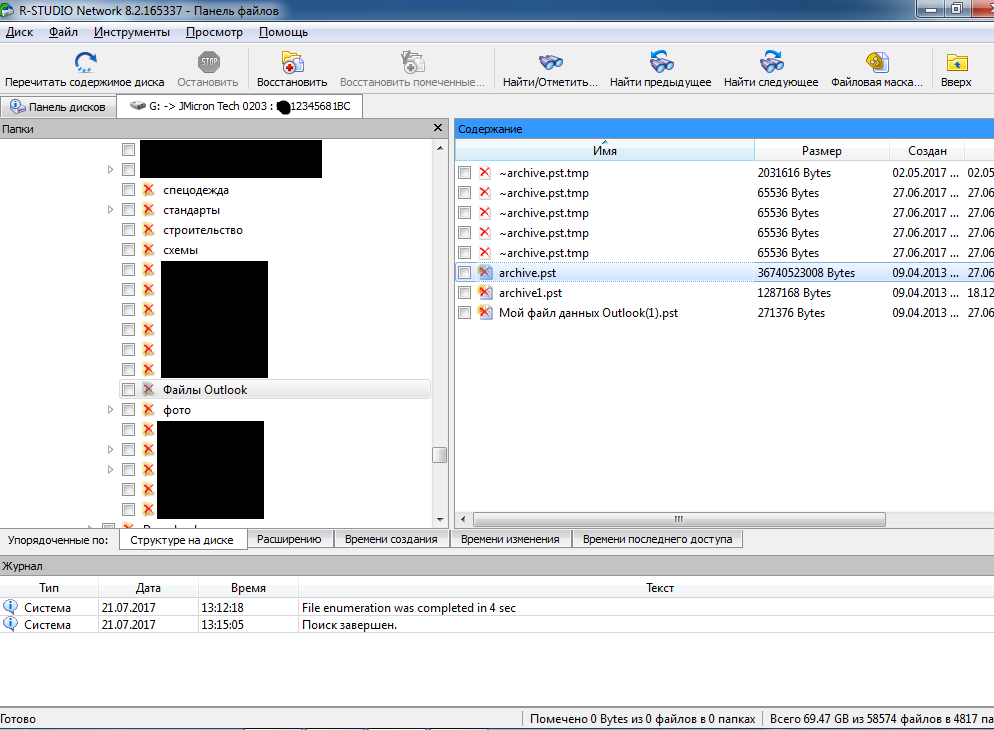

Please note that if you look at the left menu and go up through the folder hierarchy, you can see that this folder is located in the user account folder and there are Desktop, Documents, etc. folders. Thus, you can pull out photos and other files that were stored in the user in these folders.
Screenshot

7. Next, we tick the required files with the pst extension and click the Restore Marked button, indicate the place to save the saved files (in my case this is the Recover folder on drive C). We are waiting for the end of the process of copying files.
Screenshot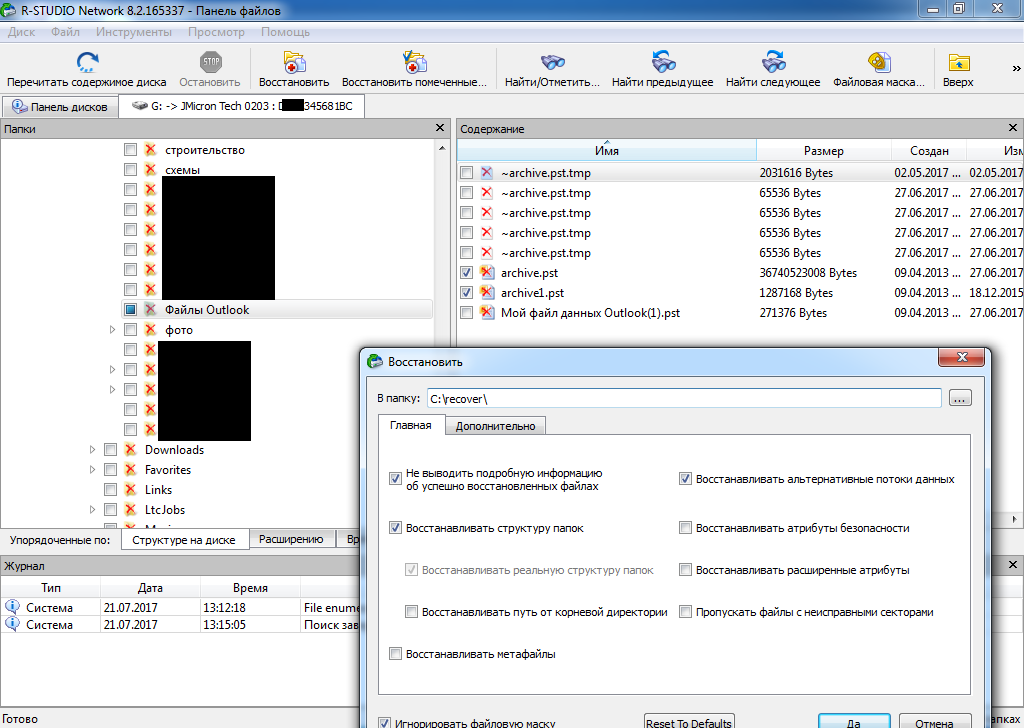

8. The recovered archive file is usually damaged and is not detected by Outlook. Fortunately, for large files, the virus encrypted only the first megabyte, leaving the rest intact. Therefore, we need to try to restore the structure of the archive, for this there are several ways:
A) Use the SCANPST utility included in the standard MS Office suite. For example, in MS Office 2010 this utility is located in the folder C: \ Program Files (x86) \ Microsoft Office \ Office14 \ if you have 64-bit Windows and the path C: \ Program Files \ Microsoft Office \ Office14 when using the 32-bit version of Windows .
B) Use third-party utilities. Which you can find a lot in the open spaces of Google.
I used the first option and, in principle, it worked on all the PCs that were brought to me for recovery.
I also attach to the post a link to step-by-step instructions for working with the SCANPST utility.
That's all, other files are restored by the same algorithm, you only need to substitute the desired file extension, or manually scroll through all the folders in the "Additional found files" section and select what needs to be restored.
If someone post my "captain", please do not criticize strongly, not everyone has data recovery experience and proven tools. If you still have questions you can write in the LAN or here in the comments.
Source: https://habr.com/ru/post/357390/
All Articles