Kaspersky Lab: WannaCry malware was actively spreading through the network due to a vulnerability in Windows 7

A little more than a week ago, articles began to appear on the network about a new virus that attacks computers in various networks. On Geektimes, an article about WannaCry / Wcry / WannaCrypt appeared on May 12th. Since then, the situation has not been fully managed, although the attack has been suspended. In order to reduce the danger of malware, Microsoft has promptly released patches to fix a vulnerability that WCry has been exploiting. In Windows 8.1 and higher, you can solve the problem by disabling SMBv1 support.
Minor OS versions are not well protected. All this led to the fact that the unexpected attack WannaCry hit more than 200,000 personal computers in approximately 150 countries. Unfortunately, the full picture of what is happening is still unknown, experts are working on clarifying all the details of the attack. Already published some interesting details. For example, Kaspersky Lab found out that more than 97% of infected computers work on Windows 7. Almost nothing is heard about infected PCs and laptops running Windows XP - usually such systems are infected by the users themselves, who are learning a new malware. The above data was provided by Kostin Rayu, head of the Global Research and Analysis Team at Kaspersky Lab.
In fairness, it is worth noting that Kaspersky Lab can monitor infections only on PCs with Kaspersky Anti-Virus installed. So, 97% of infected Windows 7 PCs are statistics on machines with Kaspersky Anti-Virus, and not statistics on all PCs connected to the network. Nevertheless, the bias in the direction of Windows 7 is so strong that it is hardly possible to doubt that Windows 7 is more vulnerable to WannaCry than other versions of the Microsoft operating system.
')
And earlier, some experts said that the virus had spread so quickly due to users who refused to leave Windows XP for newer and, therefore, more secure versions of the Microsoft operating system. The author of the article in the New York Times, referred to above, is one of the first to make just this assumption. In his opinion, users who did not want to update the OS on their computers with Windows XP, greatly contributed to the spread of the malware.
As it turned out, systems running Windows XP that tried to infect the malware “fall” before ransomware manages to penetrate the OS. But Windows 7 is infected with malware without any problems. This is, first of all, about computers with Windows 7, on which the patch, released by Microsoft in March, is not installed.
According to representatives of the "Laboratory", the virus most often infects Windows 7 x64 Edition, since it is this version of the OS that rests on the vast majority of corporate PCs running Windows.
In addition, it was previously reported that a phishing e-mail attack played a major role in the spread of the virus. In fact, it is not. Yes, of course, some fractions of the percentage of infection are associated with careless users who do not pay attention to what applications in their mailer they open. In fact, the user’s computers penetrate malicious computers into Server Message Block ports. To do this, the malware uses a kind of SMB exploit, called "Eternal Blue". It was developed by NDA experts and then made public by the Shadow Brokers group.
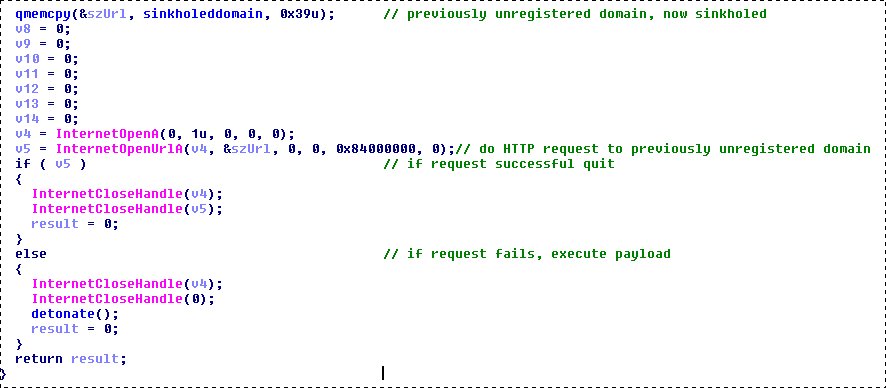
The screenshot shows a section of the virus code where there is an instruction for making an HTTP request to an unregistered domain. If the request is successful, the virus stops working.
Now the attackers who developed the malware decided to increase the scale and effectiveness of the attack. To do this, they use the powerful Mirai botnet to attack two servers that are now holding back the spread of WCry. We are talking about servers where domains are registered to which a virus is accessed. The developers of the virus are currently trying to disable these servers, so that the virus can continue to spread throughout the world.
As it turned out, if you register the domain accessed by the virus when it is loaded into the victim's computer, then the spread of WannaCry stops - this malware goes into hibernation. Experts called this method of neutralization of the virus "switch". But, unfortunately, now the attackers continue their work, releasing new versions of the virus. So there are already “descendants” of the first version without a “switch”, which was the appeal to a non-existent domain. Accordingly, the modified WCry continues to spread without any interference, although the power of this attack is much lower than that of its predecessor.
MalwareTech , an information security specialist who registered a domain associated with a virus, stopped the main attack and believes that the main danger has passed. He argues that now there are several versions of the virus that can spread without a domain, which was discussed above. Perhaps this is true, to find out, you have to wait a week or two.
Source: https://habr.com/ru/post/357344/
All Articles