The guy accidentally stopped the global spread of cryptographer WannaCrypt
These days everyone is talking about the WannaCry / Wcry / WannaCrypt cryptogenerator , which hit tens of thousands of computers all over the world on Friday, but then its distribution suddenly stopped.
Microsoft promptly released patches to fix the vulnerability (a patch can tear down pirated Windows):
The vulnerability can also be closed in Windows 8.1 and higher versions by completely disabling SMBv1 support:
')
According to the latest information, the cryptographer managed to hit more than 75,000 Windows computers in at least 99 countries around the world. But the scale of the spread of WannaCrypt could have been an order of magnitude greater if it were not for the actions of one security specialist, the author of the blog MalwareTech Blog . He tells how everything was.
This hero is a 22-year-old hacker and blogger from the UK, whose name has not yet become public. He writes that on Friday he had a day off. He woke up around 10:00 and logged into the national cyber threat tracking system to watch the spread of banking malware Emotet, the most significant event of recent days. I did not notice anything unusual and went to breakfast. When I returned home around 2:30 pm, I found a bunch of reports about the infection of various hospitals and medical systems with cryptographer. Such infections occurred before , but here, as if the scale was larger than before.
With the help of his friend, a hacker under the nickname Kafeine, the guy quickly took out a sample of the malware, launched it in a virtual machine and saw that it was sending requests to an unregistered domain. It was interesting.
Cisco Umbrella statistics showed that requests to this domain began on Friday at 8:00 am and grew like an avalanche.
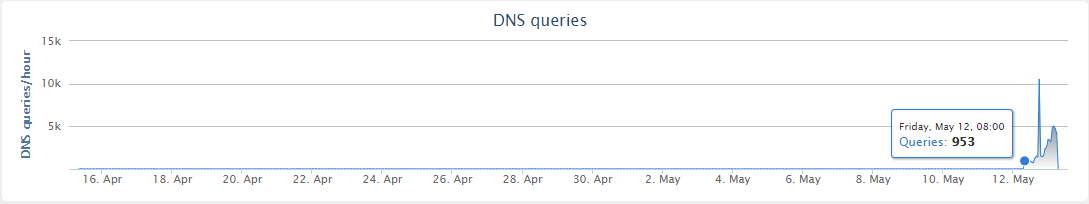
The blogger registered the domain on himself for 8 pounds ($ 10.69). This is standard practice, he says. Botnets often generate domain names for command servers (C2C) each according to their own algorithm. The algorithm is known to intruders, so they can register this domain in advance. Sometimes, researchers and antivirus companies manage to get ahead of them, and then they have the opportunity from the inside to study the work of the botnet command center, collect data on the geographical distribution of bots, and reverse engineer the software. So registration of these domains is a normal thing. The author of the blog MalwareTech Blog says that over the past year he has registered several thousand domains.
While after registration records were updated in the DNS systems, the guy studied the behavior of the malware in the virtual machine. It turned out that after encrypting files, he starts scanning random IP addresses on port 445 (using SMB). Already this suggested that WannaCrypt could somehow be connected with the NSA exploit for SMB, which just a month ago appeared in the public domain due to hacking of NSA servers by the hacker group ShadowBrokers .
Since all infected people knocked on this domain, after gaining control over it, the researcher was able to compile a list of IP addresses and an infection map using log files.
Yesterday at about 18:23 BST, a hacker asked an employee to study the malware code for generating new domain names — it was necessary to check that the domain for communication would not change. Five minutes later, the employee appeared in a panicked state. He said that domain registration is related to file encryption - that is, the guys are responsible for encrypting files on all computers (it later turned out that this was not the case). They quickly got in touch with the hacker Kafeine, and he showed a fresh tweet from ProofPoint’s company Diren Huss (Darien Huss), who analyzed the malware code more thoroughly after reverse engineering. It turned out that the opposite is true - it was the registration of the domain that stopped the further spread of the cryptographer.
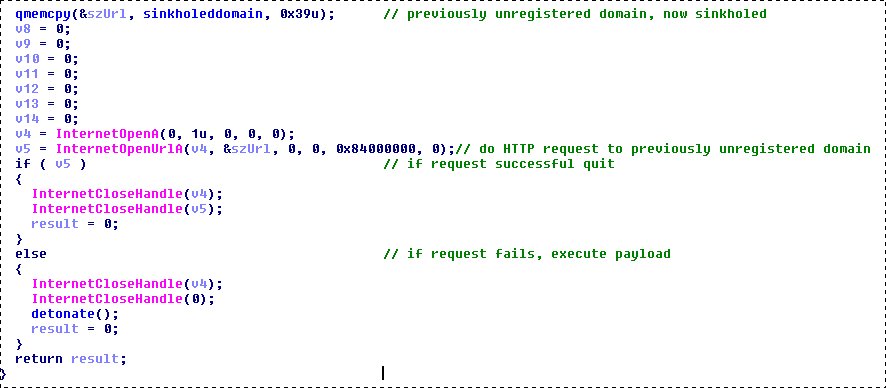
As can be seen in the screenshot of the code, the malware performs an HTTP request to an unregistered domain. If the request is successful, then it stops working . If the request fails, the program code is executed and file encryption begins.
Tweet posted May 12 at 8:29 pm.
Armed with this information, the guy again uploaded his virtual environment, launched the malware - and nothing happened, he no longer worked.
The first thought was that the request to this domain was used as a kind of “emergency stop-crane”, which should work if something went wrong. But it is more likely that the authors of the malware simply incorrectly implemented protection against the analysis of their program (protection against the virtual environment). Probably, when running in a virtual environment, a request to such a domain should have given a positive answer - emulators are trying to convince the malware that the virtual environment is normal and everything works as it should. Therefore, they intercept all such requests and return the IP address of the sandbox. A similar technique to protect against virtual environment uses the Necurs Trojan.
Accordingly, if the request to the domain returns a successful response, the malware thinks that it is in the sandbox and crashes.
It was so completely by chance that one researcher managed to stop the spread of a global viral infection, which is now spoken of in all the news.
But you should not relax. This time, people were just lucky that the attacker made a mistake with one function in the code, but the next time there will be no error - and the “cyberacalypse” may turn out to be real. We assume that it was a test check. New versions for sure will appear in the coming days.
UPD. Discovered the second and third variants of WannaCry, including those without a stop-tap
Microsoft promptly released patches to fix the vulnerability (a patch can tear down pirated Windows):
- Microsoft Security Bulletin MS17-010
- Patch, for older systems (Windows XP, Winows Server 2003R2)
The vulnerability can also be closed in Windows 8.1 and higher versions by completely disabling SMBv1 support:
')
dism /online /norestart /disable-feature /featurename:SMB1Protocol According to the latest information, the cryptographer managed to hit more than 75,000 Windows computers in at least 99 countries around the world. But the scale of the spread of WannaCrypt could have been an order of magnitude greater if it were not for the actions of one security specialist, the author of the blog MalwareTech Blog . He tells how everything was.
This hero is a 22-year-old hacker and blogger from the UK, whose name has not yet become public. He writes that on Friday he had a day off. He woke up around 10:00 and logged into the national cyber threat tracking system to watch the spread of banking malware Emotet, the most significant event of recent days. I did not notice anything unusual and went to breakfast. When I returned home around 2:30 pm, I found a bunch of reports about the infection of various hospitals and medical systems with cryptographer. Such infections occurred before , but here, as if the scale was larger than before.
With the help of his friend, a hacker under the nickname Kafeine, the guy quickly took out a sample of the malware, launched it in a virtual machine and saw that it was sending requests to an unregistered domain. It was interesting.
Cisco Umbrella statistics showed that requests to this domain began on Friday at 8:00 am and grew like an avalanche.

The blogger registered the domain on himself for 8 pounds ($ 10.69). This is standard practice, he says. Botnets often generate domain names for command servers (C2C) each according to their own algorithm. The algorithm is known to intruders, so they can register this domain in advance. Sometimes, researchers and antivirus companies manage to get ahead of them, and then they have the opportunity from the inside to study the work of the botnet command center, collect data on the geographical distribution of bots, and reverse engineer the software. So registration of these domains is a normal thing. The author of the blog MalwareTech Blog says that over the past year he has registered several thousand domains.
While after registration records were updated in the DNS systems, the guy studied the behavior of the malware in the virtual machine. It turned out that after encrypting files, he starts scanning random IP addresses on port 445 (using SMB). Already this suggested that WannaCrypt could somehow be connected with the NSA exploit for SMB, which just a month ago appeared in the public domain due to hacking of NSA servers by the hacker group ShadowBrokers .
Since all infected people knocked on this domain, after gaining control over it, the researcher was able to compile a list of IP addresses and an infection map using log files.
Yesterday at about 18:23 BST, a hacker asked an employee to study the malware code for generating new domain names — it was necessary to check that the domain for communication would not change. Five minutes later, the employee appeared in a panicked state. He said that domain registration is related to file encryption - that is, the guys are responsible for encrypting files on all computers (it later turned out that this was not the case). They quickly got in touch with the hacker Kafeine, and he showed a fresh tweet from ProofPoint’s company Diren Huss (Darien Huss), who analyzed the malware code more thoroughly after reverse engineering. It turned out that the opposite is true - it was the registration of the domain that stopped the further spread of the cryptographer.

As can be seen in the screenshot of the code, the malware performs an HTTP request to an unregistered domain. If the request is successful, then it stops working . If the request fails, the program code is executed and file encryption begins.
Tweet posted May 12 at 8:29 pm.
Armed with this information, the guy again uploaded his virtual environment, launched the malware - and nothing happened, he no longer worked.
The first thought was that the request to this domain was used as a kind of “emergency stop-crane”, which should work if something went wrong. But it is more likely that the authors of the malware simply incorrectly implemented protection against the analysis of their program (protection against the virtual environment). Probably, when running in a virtual environment, a request to such a domain should have given a positive answer - emulators are trying to convince the malware that the virtual environment is normal and everything works as it should. Therefore, they intercept all such requests and return the IP address of the sandbox. A similar technique to protect against virtual environment uses the Necurs Trojan.
Accordingly, if the request to the domain returns a successful response, the malware thinks that it is in the sandbox and crashes.
It was so completely by chance that one researcher managed to stop the spread of a global viral infection, which is now spoken of in all the news.
But you should not relax. This time, people were just lucky that the attacker made a mistake with one function in the code, but the next time there will be no error - and the “cyberacalypse” may turn out to be real. We assume that it was a test check. New versions for sure will appear in the coming days.
UPD. Discovered the second and third variants of WannaCry, including those without a stop-tap
Source: https://habr.com/ru/post/357342/
All Articles